Log in to DVWA admin/password, Session IDs have 4 levels (low, medium, high, impossible)
We will first inspect the low one. So, set the level to low

Low
This script is very basic and unsecure, due to the session ID is created in plaintext and uses the most common sequences.
Click on view source to open the window below
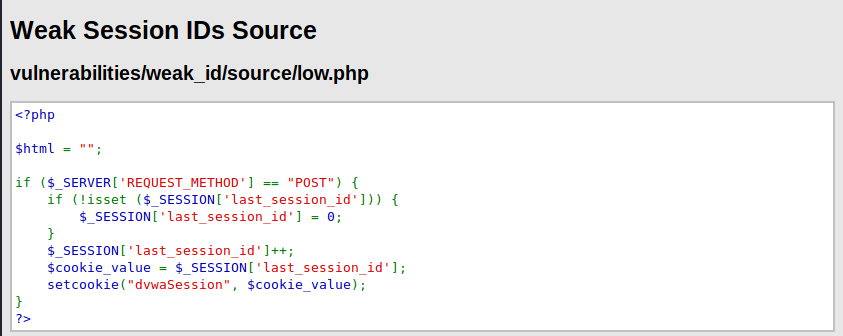
This code does the following:
- If the method is “POST” and if there is no “last_session_id” set it to 0 to start.
- If there is already a “last_session_id” start increasing by one
- Then, set the cookie with the value and set it as “dvwaSession”

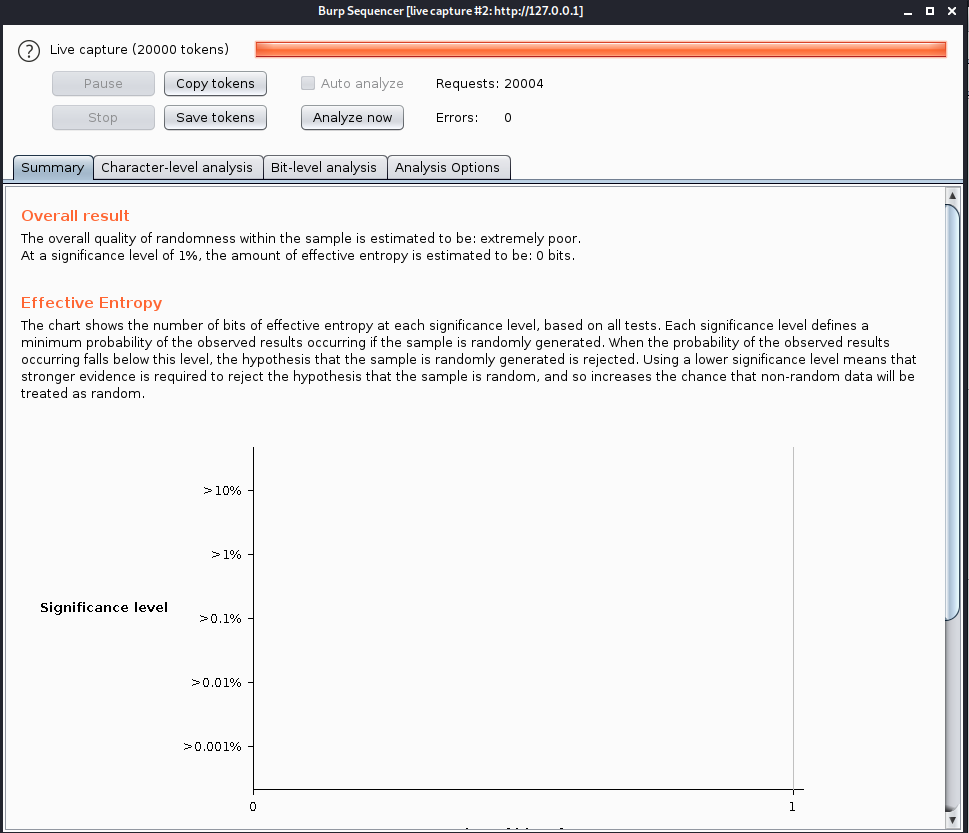
If we test against sequencer it shows this is weak
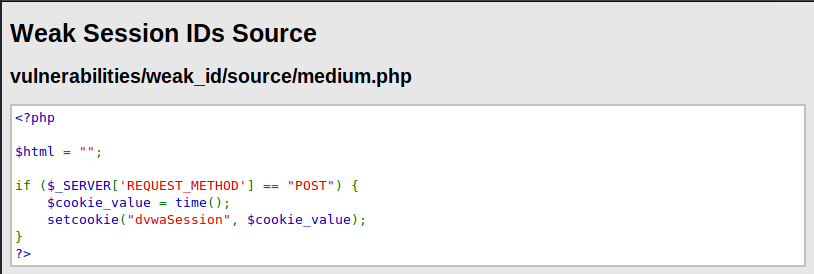
Medium
This is still weak, instead of a fix number increment, this implements the value based on time
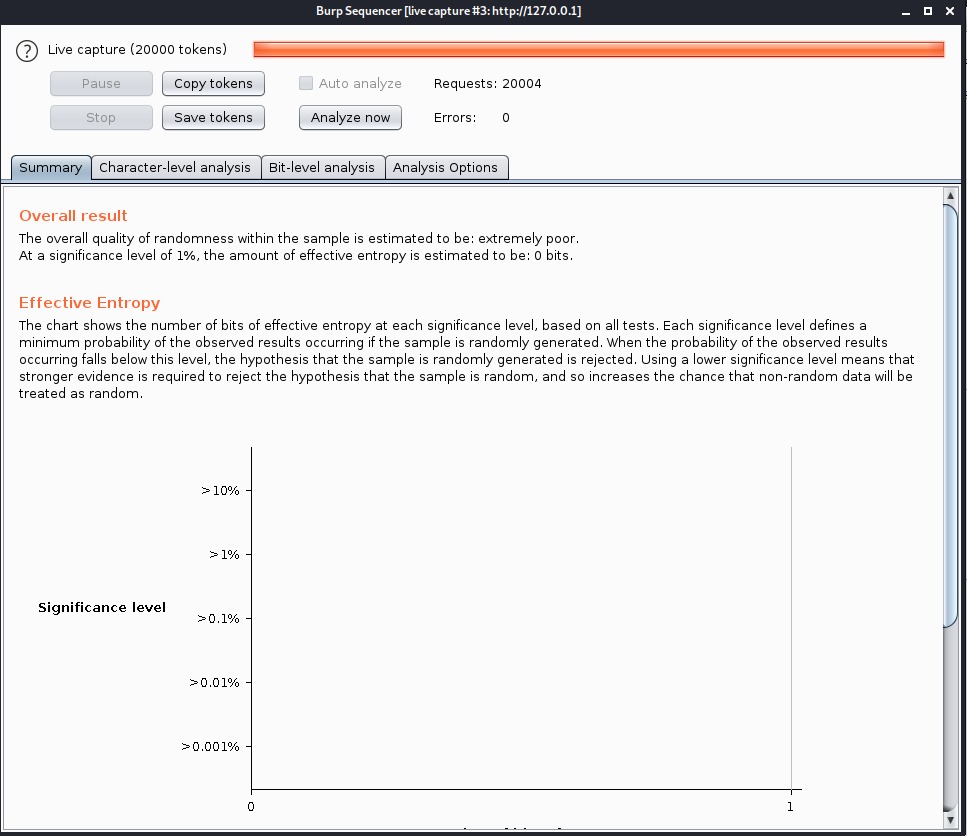
Sending it to sequencer shows it is still poor

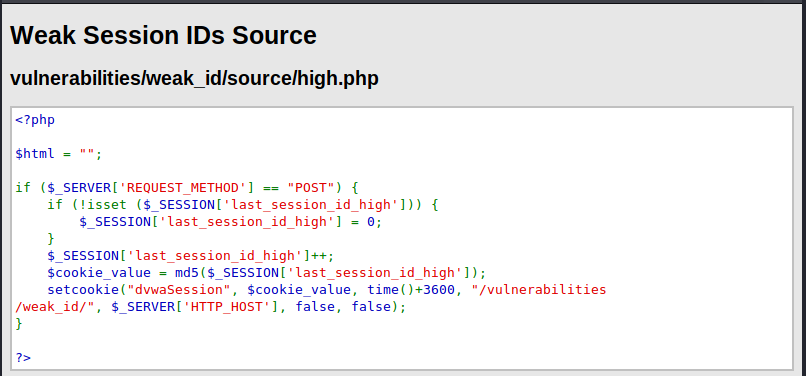
High
These time things get a little more serious. This request first checks for the type of request it should be “POST”, if isset has not been declared set the variable ‘last_session_id_high” = 0, once, the session has been created increment “last_session_id_high”, set the session id value as MD5 of the “last_session_id_high”, then, set the cookie values:
- Value name: dvwaSession
- Set the cookie value : the md5 hash
- Set the time to expire
- The path in which this session is allowed: /vulnerabilities/weak_id
- IP address
- False might indicate some values omitted
It seems more complicated even sending this to sequencer it showed positive results: excellent

In reality this is not a secure practice, as the MD5 hash was transmitted in the response set-cookie. I captured that traffic
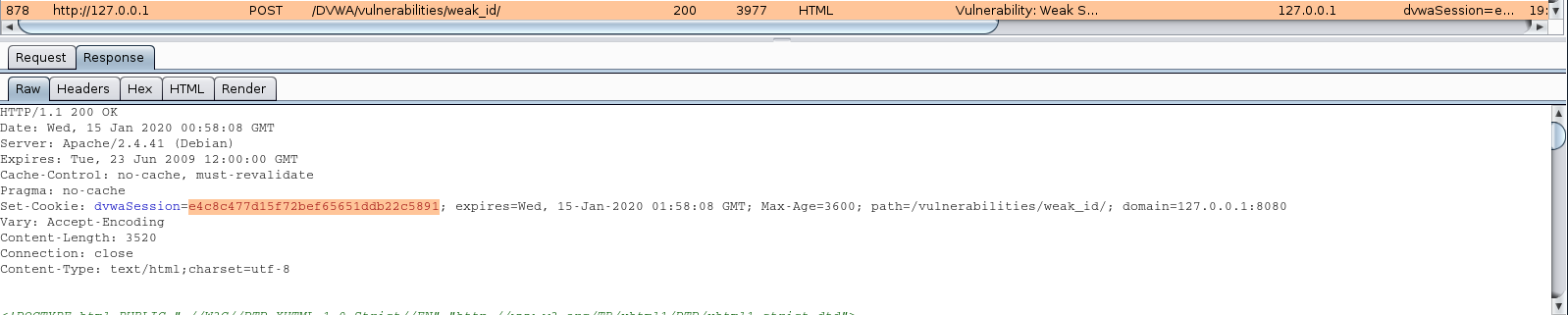
Set-Cookie: dvwaSession=e4c8c477d15f72bef65651ddb22c5891; expires=Wed, 15-Jan-2020 01:58:08 GMT; Max-Age=3600; path=/vulnerabilities/weak_id/; domain=127.0.0.1:8080
Now using any md5 tool, in this case I’m using https://www.md5online.org/md5-decrypt.html
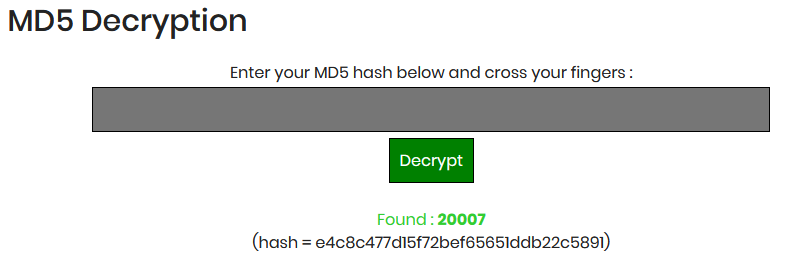
So we got the Session ID.
Impossible
This time the code got more robust. If the request is “POST”, set the session ID as a hash value SHA1 of a random number, concatenate the time and concatenate the work “Impossible”

