Gobuster is a tool used to brute-force on URLs (directories and files) in websites and DNS subdomains. Gobuster can be downloaded through the apt- repository and thus execute the following command for installing it.
https://github.com/OJ/gobuster
Gobuster is a tool used to brute-force:
- URIs (directories and files) in web sites.
- DNS subdomains (with wildcard support).
- Virtual Host names on target web servers.
Installation
apt-get install gobuster
See the available options
gobuster –help

Common Parameters
-fw – force processing of a domain with wildcard results.
-np – hide the progress output.
-m <mode> – which mode to use, either dir or dns (default: dir).
-q – disables banner/underline output.
-t <threads> – number of threads to run (default: 10).
-u <url/domain> – full URL (including scheme), or base domain name.
-v – verbose output (show all results).
-w <wordlist> – path to the wordlist used for brute forcing (use – for stdin).
Dir mode Parameter
-a <user agent string> – specify a user agent string to send in the request header.
-c – use this to specify any cookies that you might need (simulating auth).
-e – specify the extended mode that renders the full URL.
-f – append / for directory brute forces.
-k – Skip verification of SSL certificates.
-l – show the length of the response.
-n – “no status” mode, disables the output of the result’s status code.
-o <file> – specify a file name to write the output to.
-p <proxy url> – specify a proxy to use for all requests (scheme much match the URL scheme).
-r – follow redirects.
-s <status codes> – comma-separated set of the list of status codes to be deemed a “positive” (default: 200,204,301,302,307).
-x <extensions> – list of extensions to check for, if any.
-P – HTTP Authorization password (Basic Auth only, prompted if missing).
-U – HTTP Authorization username (Basic Auth only).
-to – HTTP timeout. Examples: 10s, 100ms, 1m (default: 10s).
DNS mode Parameters
-cn – show CNAME records (cannot be used with ‘-i’ option).
-i – show all IP addresses for the result.
How to use
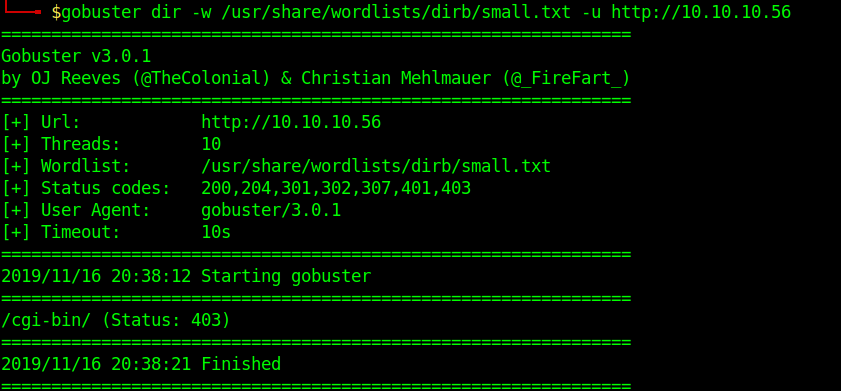
1. Basic dir scan
- gobuster dir -u http://10.10.10.40 -w /usr/share/wordlists/dirb/small.txt
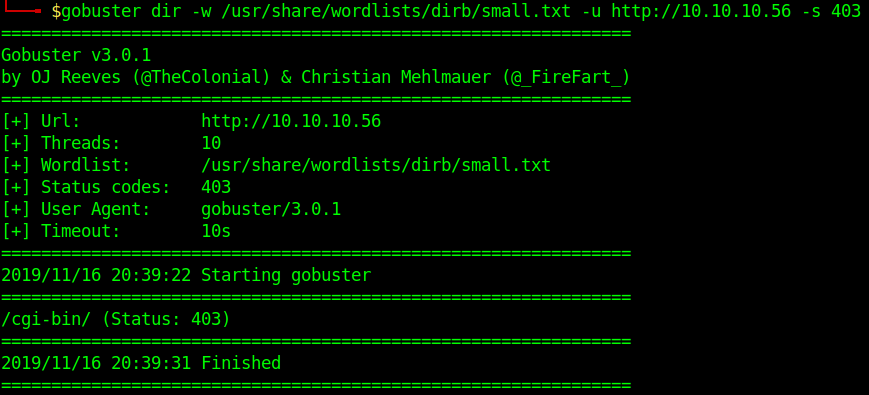
2. To select only specific types of responses use “-s”
- gobuster dir -u http://10.10.10.40 -w /usr/share/wordlists/dirb/small.txt -s 403
3. Search for files with extention sh,pl within /cgi-bin/
- gobuster dir -u http://10.10.10.40/cgi-bin/ -w /usr/share/wordlists/dirb/small.txt -x sh,pl

4. Print verbose of what is going on
- gobuster dir -u http://10.10.10.40/cgi-bin/ -w /usr/share/wordlists/dirb/small.txt -v

5. Identify content length
- gobuster dir -u http://10.10.10.40/cgi-bin/ -w /usr/share/wordlists/dirb/small.txt -l

6. Writing results to a file
-
- gobuster dir -u http://10.10.10.40 -w /usr/share/wordlists/dirb/small.txt -o results.txt
- ls -l results.txt
