pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute. Great for enumeration of Linux systems in CTFs. Also great to demonstrate your colleagues why passing secrets as arguments on the command line is a bad idea.
https://github.com/DominicBreuker/pspy
Installation
1. Download the package to your computer
- git clone https://github.com/DominicBreuker/pspy.git

2. Install Golang
- cd pspy
- go build
- apt install golangapt # I already had it installed
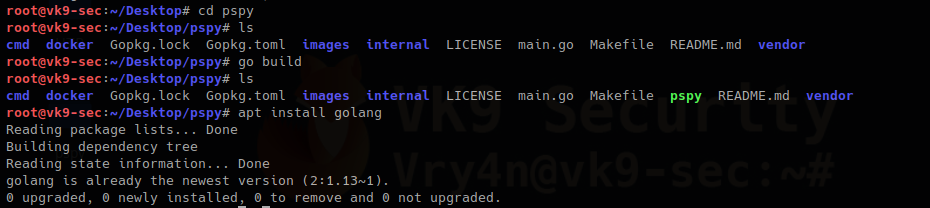
In case, you run go build and you face a “github.com/dominicbreuker/pspy/cmd” unable to locate the package, just install it
- go get github.com/dominicbreuker/pspy/cmd
Once compiled you can run it.
Execution
1. Running the script, first check what options are available, this script checks for systemevents, UID, PID, path of execution
- ./pspy –help

Options
-c doesn’t do much, the option is always true “(colored=true)”
- ./pspy -c

–debug: This one prints error messages
- ./pspy –debug

-d : this one print current processes but watches a specific directory “Watching directories: [/usr /tmp /etc /home /var /opt] (recursive)” and “[/tmp] (non-recursive)”
- ./pspy -d /tmp

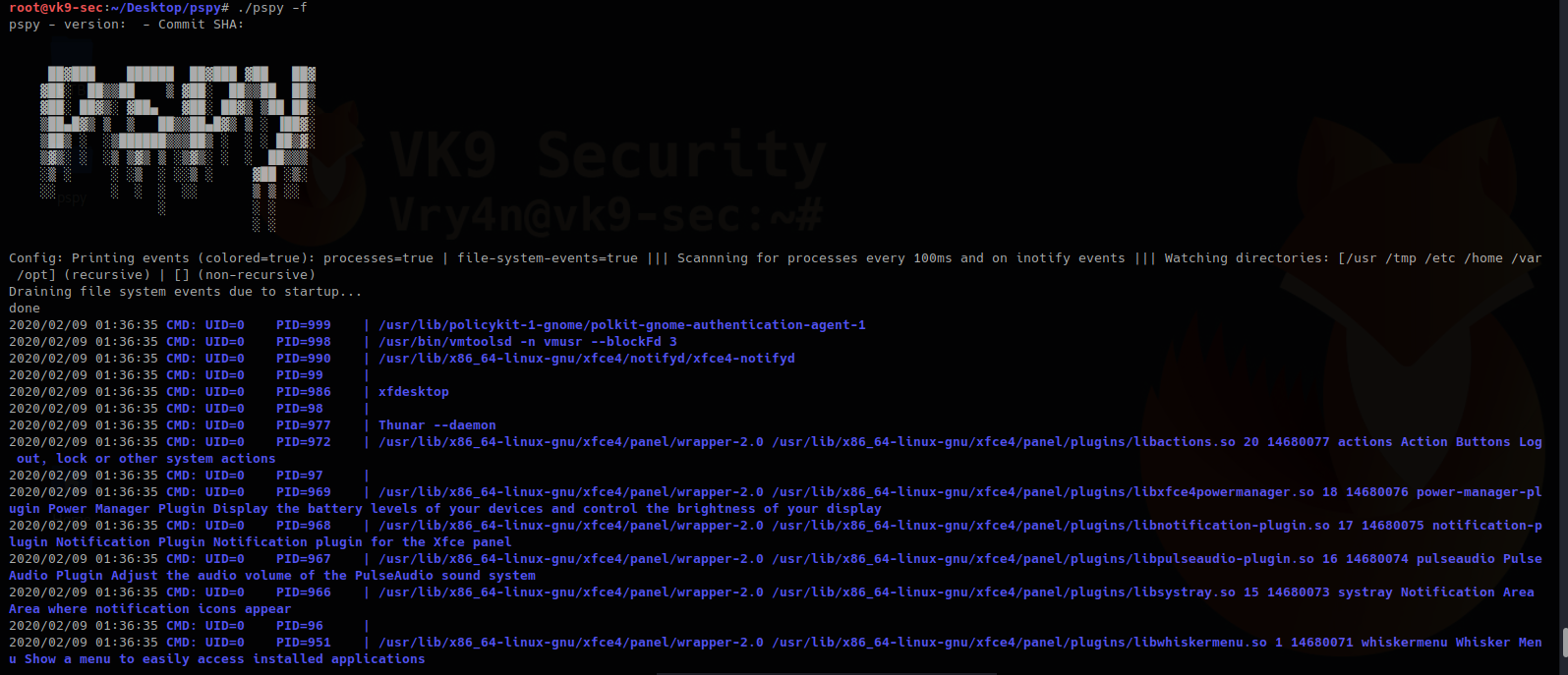
-f : print file system events to STDOUT
- ./pspy –f
-h : the help menu, we’ve just seen

-i : scan every ‘interval’ milliseconds for new processes (default 100)
- ./pspy -i 10

-p : print new processes to stdout (default true), “processes=true”
- ./pspy -p

-r : recursive “ Watching directories: [/home] (recursive)”
- ./pspy -r /home

Disabling features
1. Using “-p=false” tells the script to omit printing processes, combining it with “-f” can help only printing system events
- ./pspy -p=false -f
