Covenant is a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.
Covenant is an ASP.NET Core, cross-platform application that includes a web-based interface that allows for multi-user collaboration.

Developers’ documentation
Wiki: https://github.com/cobbr/Covenant/wiki
Installation Guide: https://github.com/cobbr/Covenant/wiki/Installation-And-Startup
Features
- Intuitive Interface – Covenant provides an intuitive web application to easily run a collaborative red team operation.
- Multi-Platform – Covenant targets .NET Core, which is multi-platform. This allows Covenant to run natively on Linux, MacOS, and Windows platforms. Additionally, Covenant has docker support, allowing it to run within a container on any system that has docker installed.
- Multi-User – Covenant supports multi-user collaboration. The ability to collaborate has become crucial for effective red team operations. Many users can interact with the same Covenant server and operate independently or collaboratively.
- API Driven – Covenant is driven by an API that enables multi-user collaboration and is easily extendible. Additionally, Covenant includes a Swagger UI that makes development and debugging easier and more convenient.
- Listener Profiles – Covenant supports listener “profiles” that control how the network communication between Grunt implants and Covenant listeners look on the wire.
- Encrypted Key Exchange – Covenant implements an encrypted key exchange between Grunt implants and Covenant listeners that is largely based on a similar exchange in the Empire project, in addition to optional SSL encryption. This achieves the cryptographic property of forward secrecy between Grunt implants.
- Dynamic Compilation – Covenant uses the Roslyn API for dynamic C# compilation. Every time a new Grunt is generated or a new task is assigned, the relevant code is recompiled and obfuscated with ConfuserEx, avoiding totally static payloads. Covenant reuses much of the compilation code from the SharpGen project, which I described in much more detail in a previous post.
- Inline C# Execution – Covenant borrows code and ideas from both the SharpGen and SharpShell projects to allow operators to execute C# one-liners on Grunt implants. This allows for similar functionality to that described in the SharpShell post, but allows the one-liners to be executed on remote implants.
- Tracking Indicators – Covenant tracks “indicators” throughout an operation, and summarizes them in the Indicators menu. This allows an operator to conduct actions that are tracked throughout an operation and easily summarize those actions to the blue team during or at the end of an assessment for deconfliction and educational purposes. This feature is still in it’s infancy and still has room for improvement.
- Developed in C#
Installation
1. Download the repository in the server
- git clone –recurse-submodules https://github.com/cobbr/Covenant

2. Get Microsoft repositories in memory
- wget -qO- https://packages.microsoft.com/keys/microsoft.asc | gpg –dearmor > microsoft.asc.gpg
- sudo mv microsoft.asc.gpg /etc/apt/trusted.gpg.d/
- wget -q https://packages.microsoft.com/config/debian/10/prod.list
- sudo mv prod.list /etc/apt/sources.list.d/microsoft-prod.list
- sudo chown root:root /etc/apt/trusted.gpg.d/microsoft.asc.gpg
- sudo chown root:root /etc/apt/sources.list.d/microsoft-prod.list
3. update the database, and,install apt-transport-https and dotnet-sdk
- sudo apt-get update
- sudo apt-get install apt-transport-https
- sudo apt install dotnet-sdk-3.1
4. Navigate to Covenant folder and build the environment
- cd Covenant/Covenant
- sudo dotnet build
- sudo dotnet run

5. Once we have an instance running from the client machine, we will access https://<covenant server>:7443

6. Now we need to register the first user, once, we do that, we are redirected to the home index page

Alternative installation
1. Download the repository in the server
- git clone –recurse-submodules https://github.com/cobbr/Covenant

2. Run Covenant with Docker
- sudo docker build -t covenant .

3. Run a command to start Covenant
–name = is value is a random name to give to the docker instance
-it = parameter is a Docker parameter that indicates that we should begin Covenant in an interactive tty, and can be excluded if you would not like to attach to the tty.
-p = parameters expose ports to the Covenant Docker container. You must expose port 7443 and any other ports you would like to start listeners on.
-v = parameter creates a shared Data directory between the host and the container. Be sure to specify an absolute path to your data directory, a relative path will not work.
- sudo docker run -it -p 7443:7443 -p 8080:8080 -p 4433:4433 –name test_covenant -v /home/vry4n/Desktop/Covenant/Covenant/Data:/app/Data covenant –username AdminUser –computername 0.0.0.0
- <enter a password>

4. To manage the Docker instances you can use the following commands
List instances
- sudo docker ps -a
Stop a service
- sudo docker stop test_covenant
- sudo docker rm test_covenant
Restart a service
- sudo docker start test_covenant -ai
Start a service
- sudo docker start test_covenant

5. Once we have an instance running from the client machine, we will access https://<covenant server>:7443

6. Now we need to register the first user, once, we do that, we are redirected to the home index page

How to Use the Interface
Break down of the interface options
- Listeners: To get an operation started, you will want to start a new listener. Covenant supports native listeners and “bridge” listeners.
- Launchers: Launchers are used to generate, host, and download binaries, scripts, and one-liners to launch new Grunts. Once a listener has been started, you’ll want to generate a launcher to use in kicking off Grunts. To get started, navigate to the Launchers navigation page
- Grunt Interaction: Grunts are Covenant’s C# implant. Most of an operator’s time will be spent interacting with grunts to assign tasks and collect information.
- Templates: Grunt templates
- Tasks: are built-in functions that can be assigned to active grunts. Tasks should be written to complete common functionality to be run on grunts.
- Graph View: The Graph view provides a graphical interface for visualizing the peer-to-peer graph. The graph displays Listeners and Grunts in a graph that indicates the flow of network traffic.
- Data: The Data page displays certain types of information collected by Grunts during an operation, including credentials, indicators, and downloads.
- User Management: Covenant Users should be created for each operator to enable collaboration and so that actions can be tracked to operators.
1. First, we need to start a listener
- Navigate to listeners

2. Click on create

- Name: Name of the listener
- Bind Address: The IP associated to the listener 0.0.0.0 means all ports
- Connect Port: The port used by the listener
- Connect Address: The IP that will be listening
- UseSSL: if you want to encrypt traffic
- Http Profile: A profile for the listener
Fill out the information as you need
Name: test_listener
Bind Address: 0.0.0.0
Connect Port: 443
Connect Address: 192.168.0.21

3. We need to create a Launcher, these are used to generate payloads. Once, we create a listener we need to generate the launchers to initiate the grunts. In this case I’d use Binary

4. Modify the stager at will, I will choose the listener and I leave the rest as default, then click on Generate

5. Click on Download, and have the .exe file delivered to the target. Once executed we should see the session under Grunts

6. Clicking on the session name under Grunts. First you can see info about the host and session
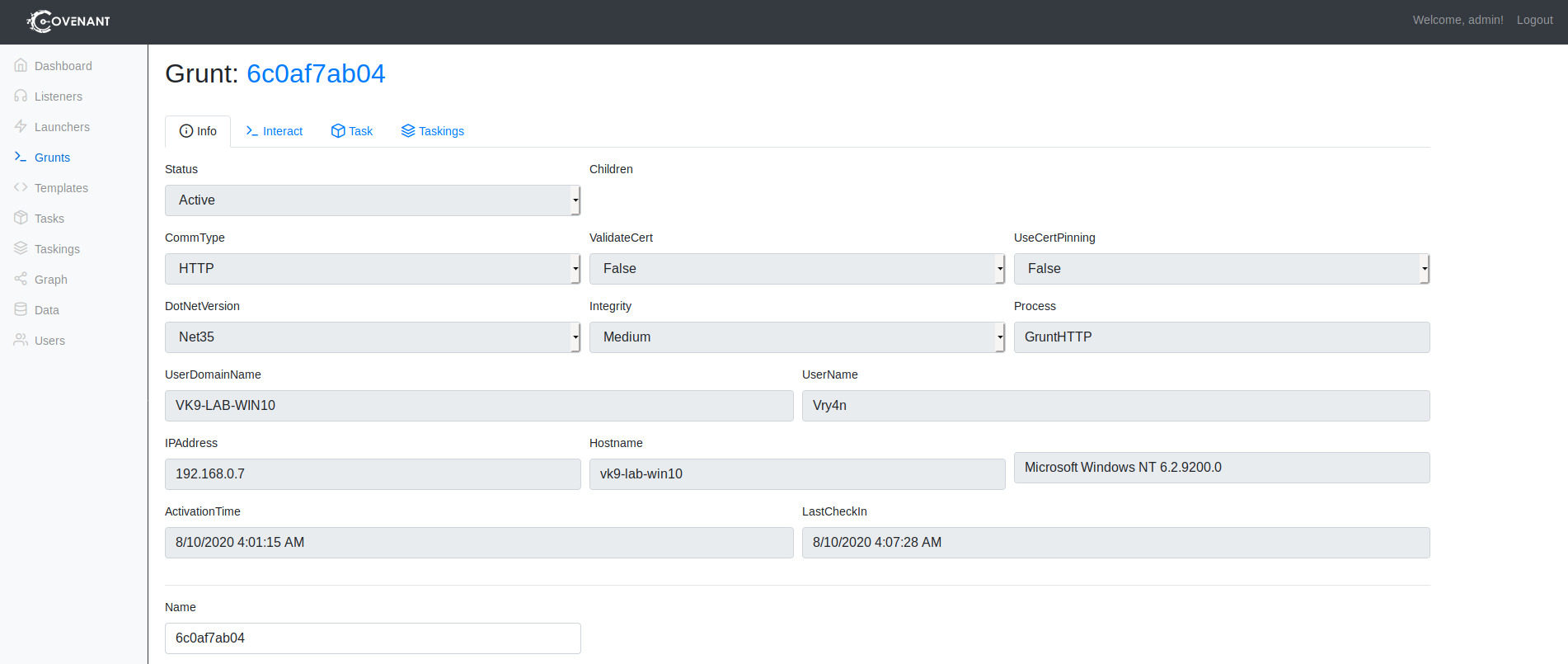
7. If you click on “Interact, there you can run command on the system
- ProcessList

8. If you go to “Taskings” You will see the status of the commands run in “Interact” tab
