BeEF utilizes YAML files in order to configure the core functionality, as well as the extensions. Most of the core BeEF configurations are in the main configuration file: config.yaml, found in the BeEF directory.
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
BeEF hooks one or more web browsers to the application for the launching of directed command modules. Each browser is likely to be within a different security context, and each context may provide a set of unique attack vectors.
https://github.com/beefproject/beef
https://github.com/beefproject/beef/wiki
Installation
1. Download the package
- git clone https://github.com/beefproject/beef
2. access the new directory created when the download completes
- cd beef
- ls
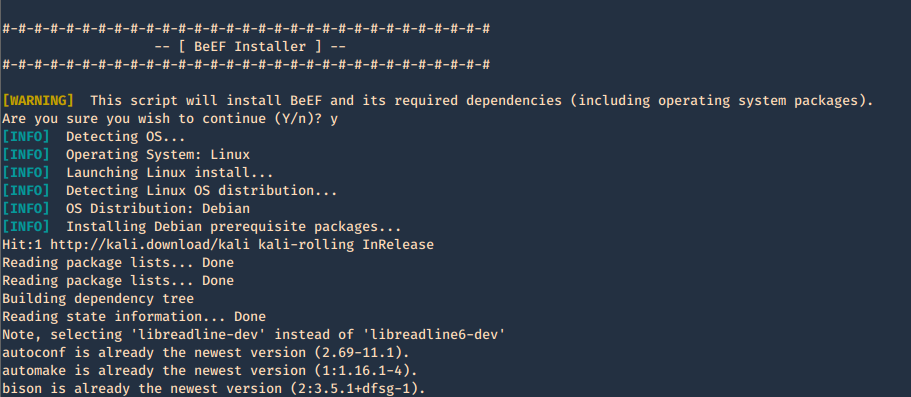
3. Run the installer with elevated privileges
- sudo ./install
Getting started
1. run the beef program, the executable is within the same location as the script ran previously ./install. Since we are running this the first time, we need to configure the credentials in config.yaml
- ls
- ./beef
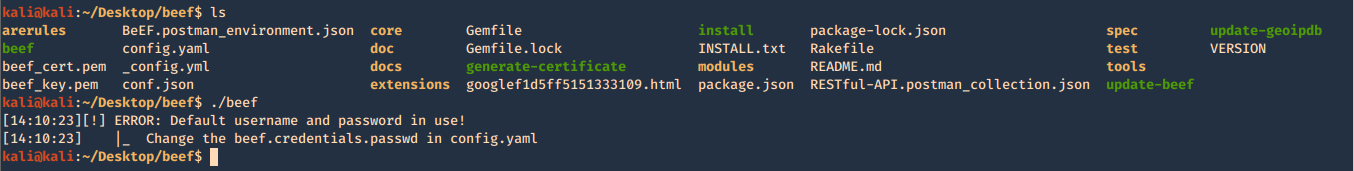
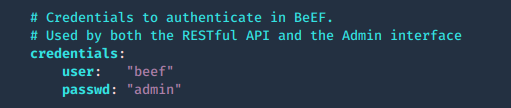
2. Create Username & Password in config.yaml, change the current values
- vi config.yaml
3. Try to run again the application
- ./beef
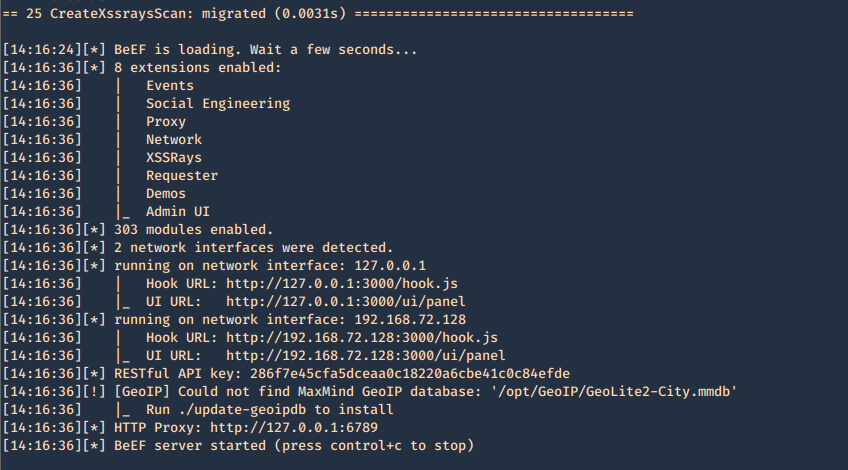
4. When it finishes loading, we can find network access details
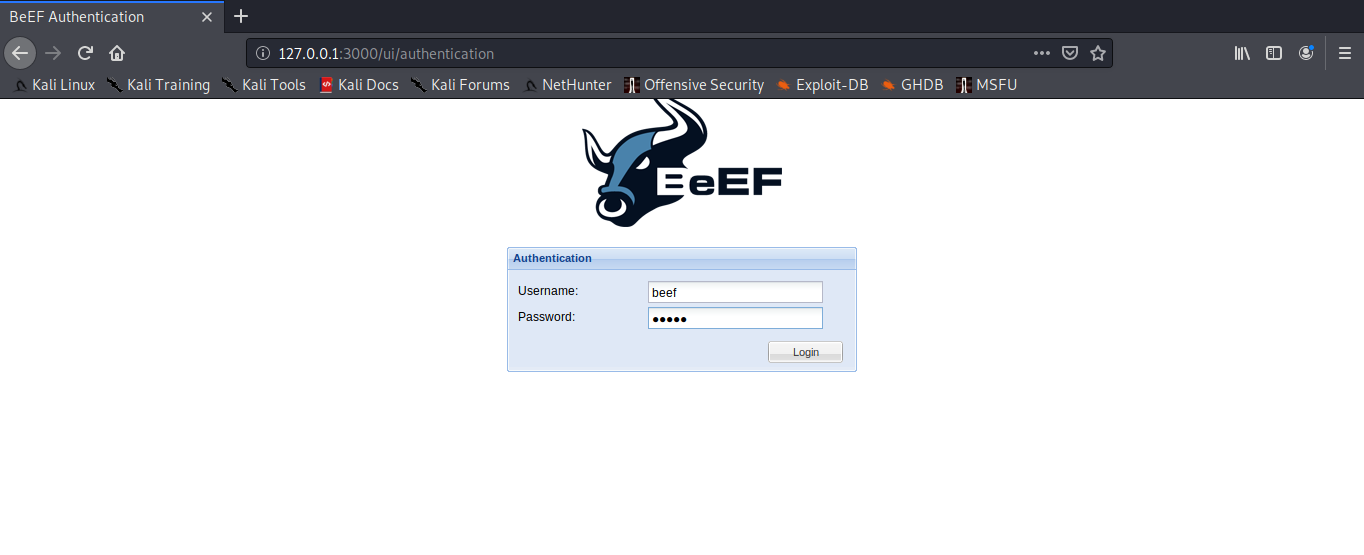
5. In order to access, open a web browser and type http://127.0.0.1:3000/ui/panel, enter the credentials we just modified in config.yaml
- beef
- admin
6. You then get the main page
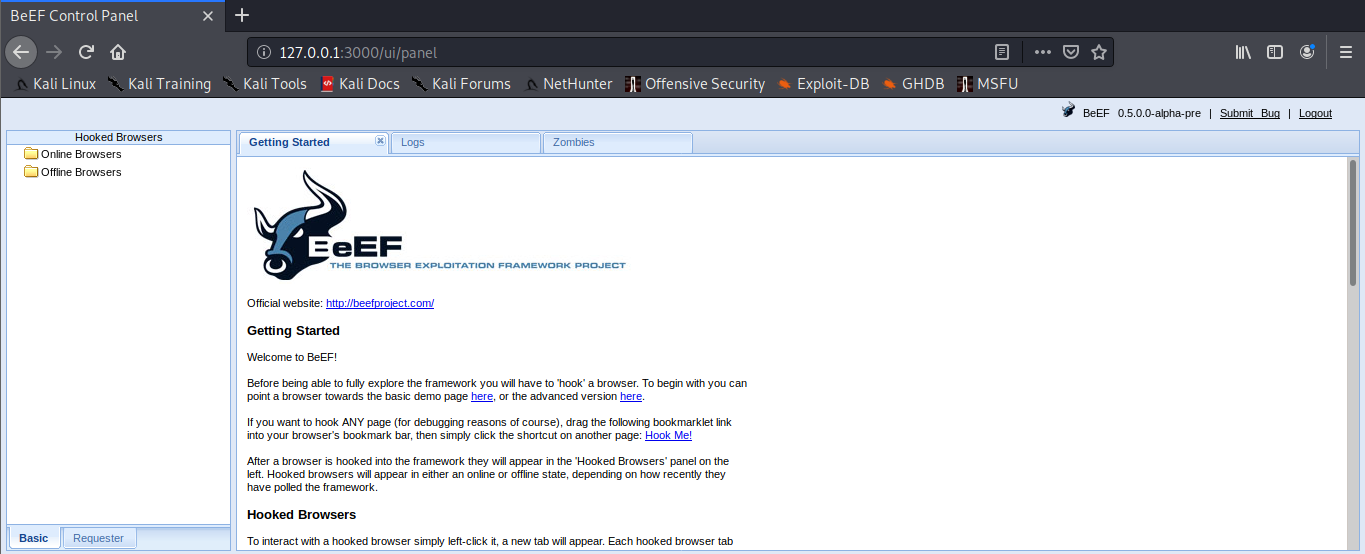
Configuring access control
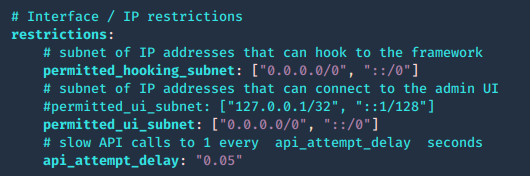
The web interface for hooking or for managing BeEF can be limited by subnet. Modify config.yaml
1. Permit who can get hooked
- permitted_hooking_subnet: [“10.1.0.0/16”]
2. Permit who can access the management interface, in this case loopback only
- permitted_ui_subnet: [“127.0.0.1/32”]
0.0.0.0/0, ::/0 mean any
- vi config.yaml
Web server configuration
The web server can be fully configured, this is done in the HTTP subsection of the config.yaml file
- vi config.yaml
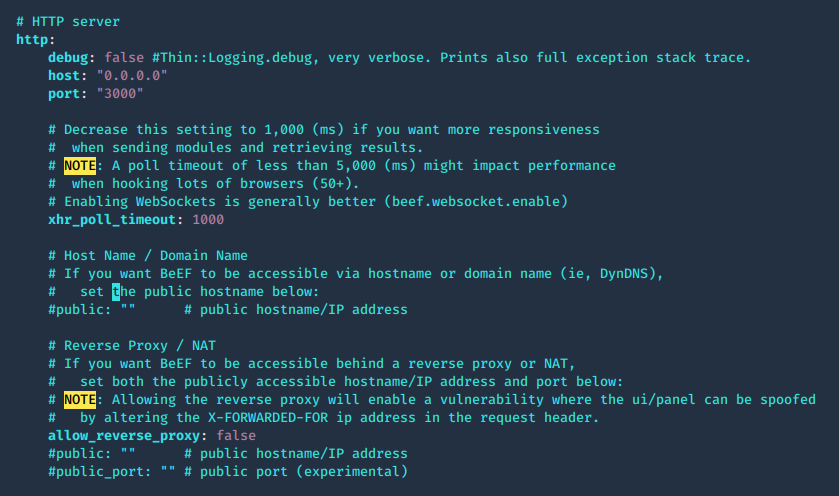
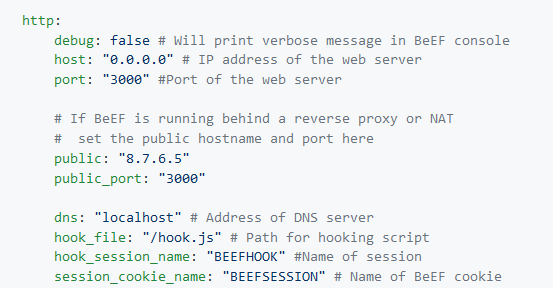
The root page and HTTP 404 error pages can be changed to reflect one of several popular web servers (Apache, IIS, NGINX) using the beef.http.web_server_imitation directive.
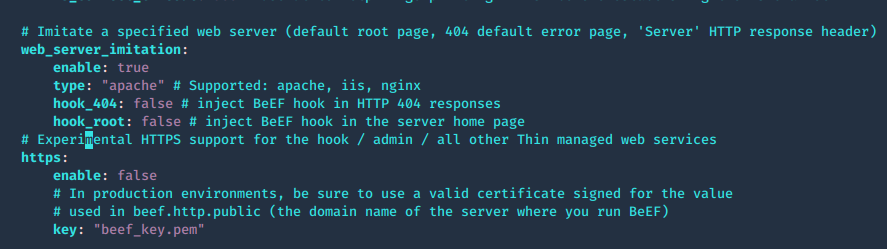
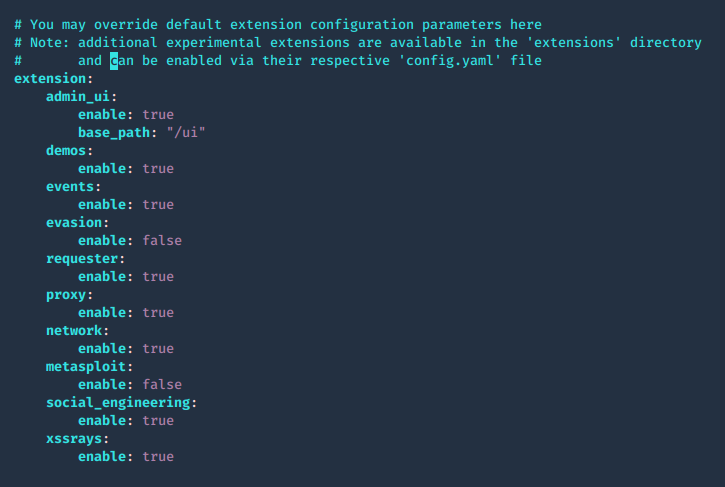
Admin UI, enable extensions
1. The panel path should also be changed using the beef.extension.admin_ui.base_path configuration option, this is used to enable extensions, change false to true
- vi config.yaml
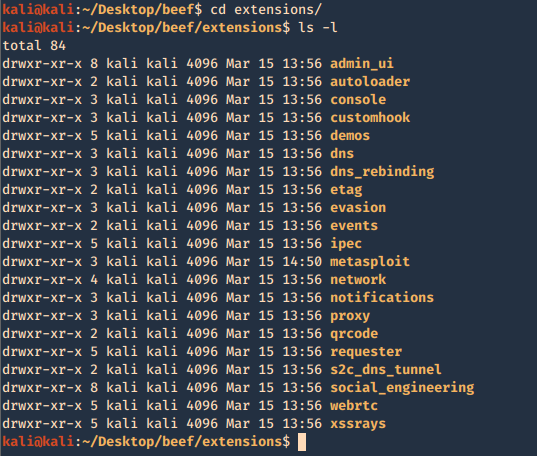
2. The extensions are located in ./beef/extensions, each one has its own config.yaml
- cd extensions
- ls -l
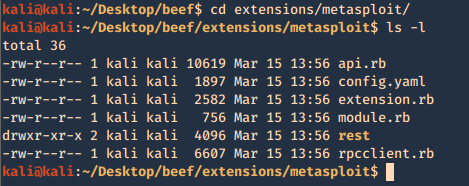
Integrating BeEF with Metasploit
1. Enable Metasploit extension ./beef/config.yaml
- enable: true
![]()
2. Now access the extension configuration file
- cd extensions/Metasploit
- ls -l
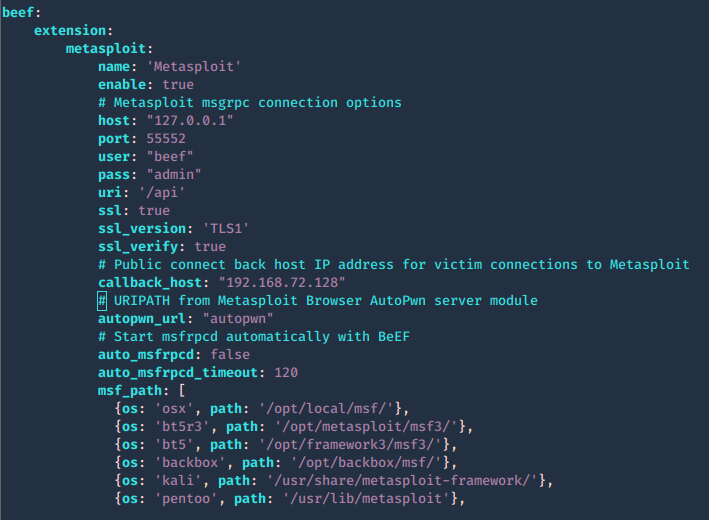
3. modify the contents of config.yaml, the following are important fields. Most of the configuration can be left with default value, except the host and callback_host parameters which should have the IP address of the host on which Metasploit is accessible.
- name: Name of module
- enable: status (true or false)
- # Metasploit msgrpc connection options
- host: host to connect
- port: port to connect
- user: log in name
- pass: password to log in
- uri: API dir
- ssl: status (true or false)
- ssl_version: ‘TLS1’
- ssl_verify: status (true or false)
- # Public connect back host IP address for victim connections to Metasploit
- callback_host: local IP for reverse connections
- # URIPATH from Metasploit Browser AutoPwn server module
- autopwn_url: “autopwn”
- # Start msfrpcd automatically with BeEF
- auto_msfrpcd: false
- auto_msfrpcd_timeout: 120
- msf_path: make sure the path to Metasploit is correct
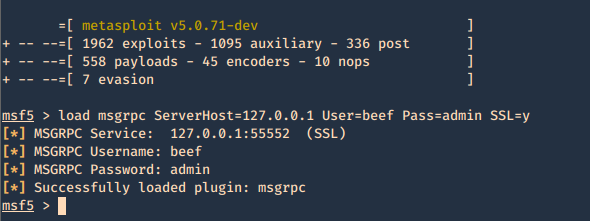
4. Now that the configuration is completed. Run Metasploit and link the module to beef
- sudo msfdb init
- msfconsole
- load msgrpc ServerHost=127.0.0.1 User=beef Pass=admin SSL=y
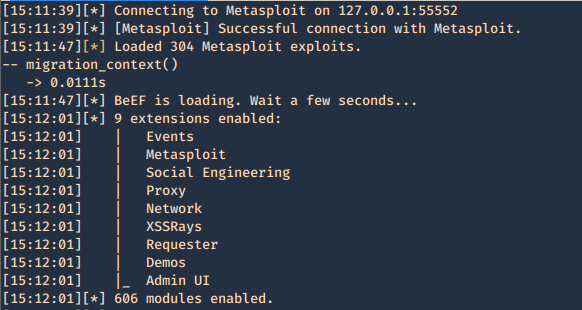
5. Reload the beef application
- ./beef
6. Additional beef options
Usage: beef [options]
- -x, –reset Reset the database
- -v, –verbose Display debug information
- -a, –ascii_art Prints BeEF ascii art
- -c, –config FILE load a different configuration file: if it’s called custom-config.yaml, git automatically ignores it.
- -p, –port PORT Change the default BeEF listening port
- -w, –wsport WS_PORT Change the default BeEF WebSocket listening port
7. Now log in again to beef and you will see that the “Commands” tab appears, and it includes the Metasploit Module, it loaded 304 exploits
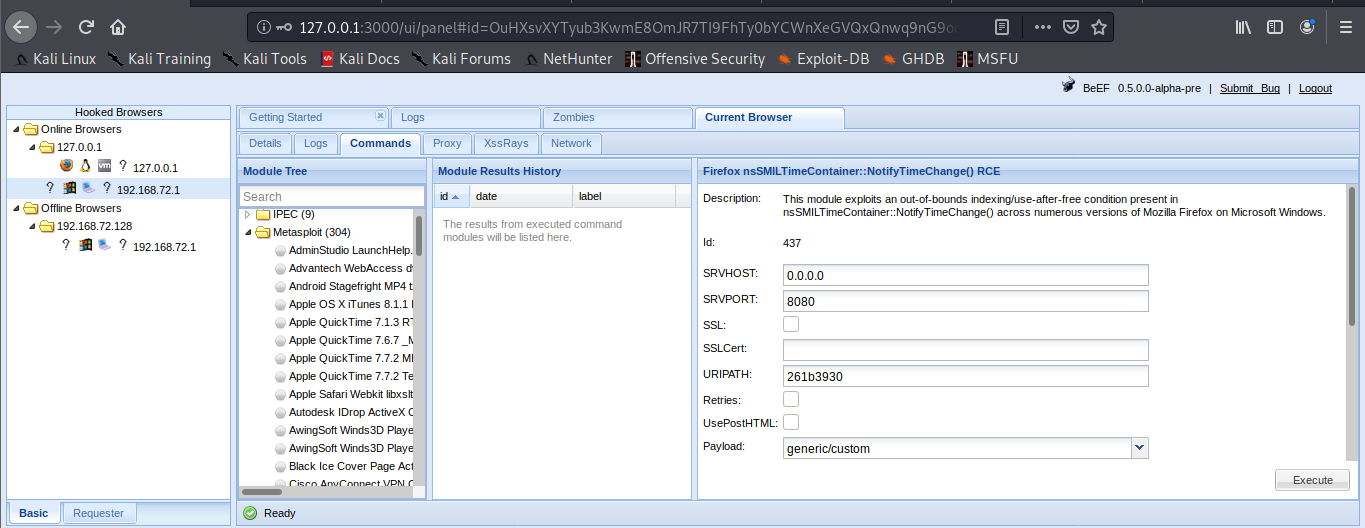
The set up has been completed successfully. Now it is time to hook a browser. In order to do that just have someone access BeEF hook site.
http://127.0.0.1:3000/demos/butcher/index.html
http://127.0.0.1:3000/demos/basic.html
Basic interface layout
1. Main page
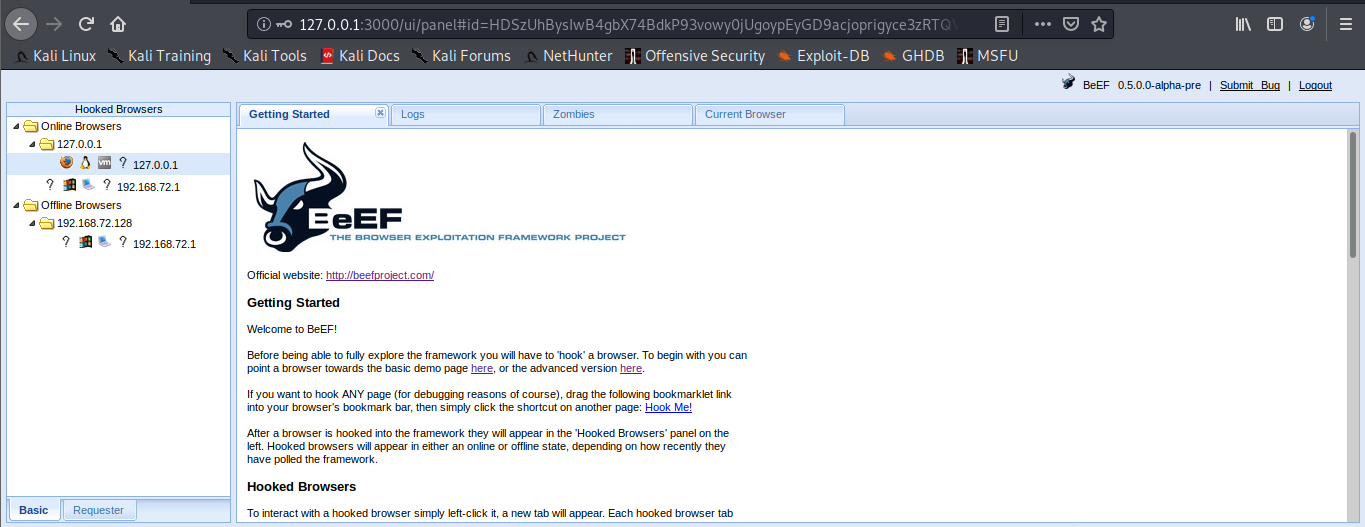
Online Browsers = Active connection
Offline Browsers = Closed connections
2. Clicking on active browsers, opens automatically, “Current Browser”
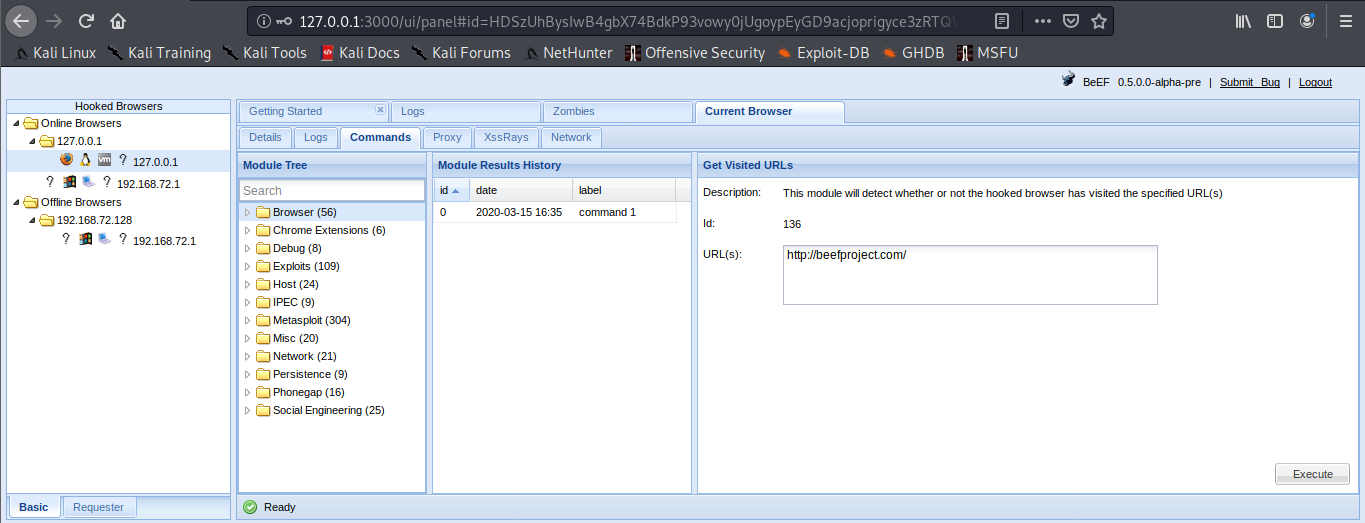
There we have
- Details = Info of the Browser
- Logs = Activity records
- Proxy = Proxy utility
- Commands = Main interface to run Modules
https://github.com/beefproject/beef/wiki/BeEF-modules
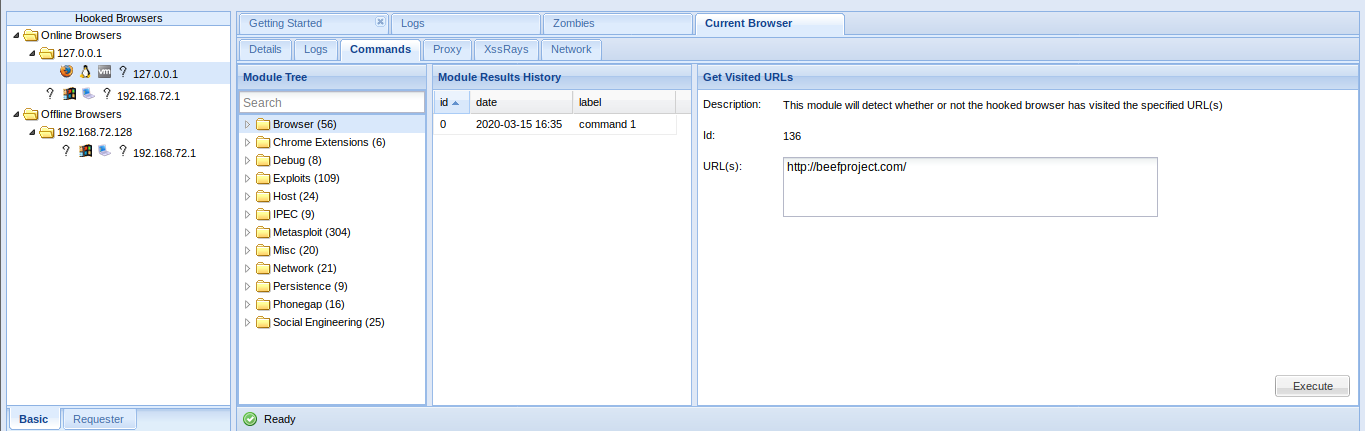
You will see bullets with different colors before each module. Internally, BeEF detects which browser you hooked and knows which modules are working on each browser :
- Green: The command module works against the target and should be invisible to the user
- Orange: The command module works against the target, but may be visible to the user
- Grey: The command module is yet to be verified against this target
- Red: The command module does not work against this target
XSSRays
- XSSRays = Cross site domain records
- Network = Network info that can be captured
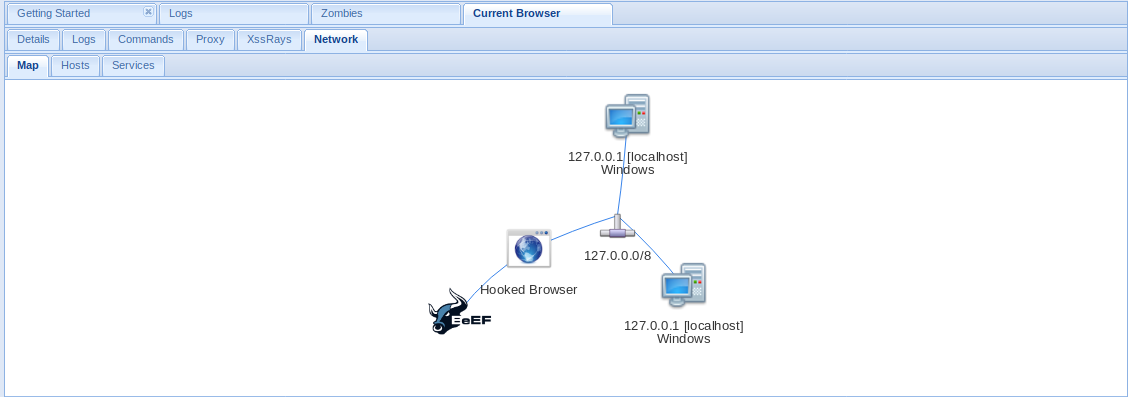
DEMO
Information Gathering
Your first step will often be to perform reconnaissance on the remote host. Which browser and plugins do they have running? Which website have you hooked?
When a browser is hooked, BeEF will automatically gather several pieces of information, including:
- Browser Name and Version
- Browser User Agent
- Plugins (including Java, ActiveX, VBS, Flash etc)
- If Adobe Flash Player is installed
You can then use different plugins to gather more specific information on the browsers
Under Browser module you can find most Information Gathering about the browser
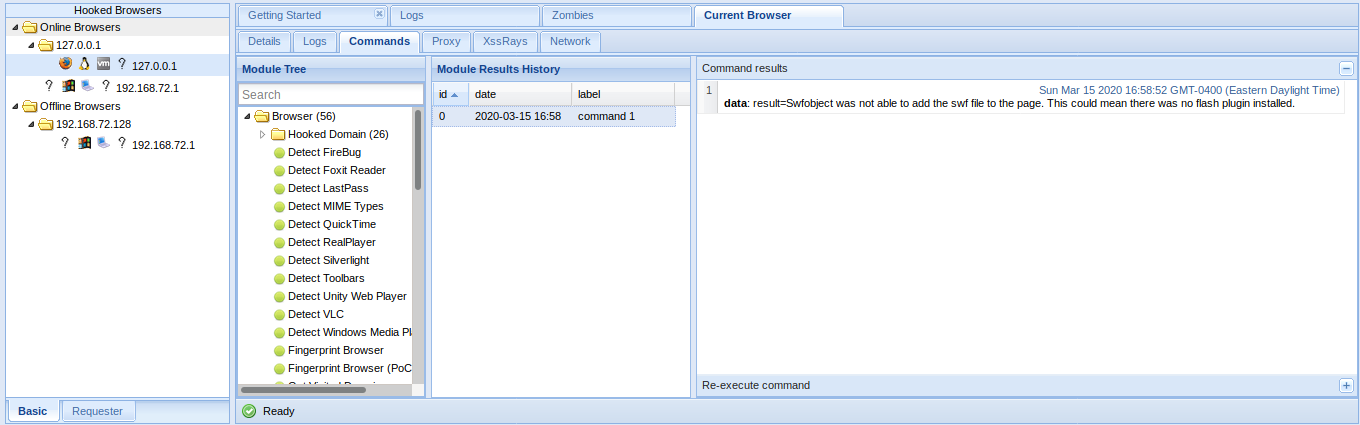
Information Gathering about the operating system
BeEF enables you to gather information on the system of the hooked browser:
- Get Internal IP module allows BeEF to detect the IP address of the system (don’t worry, more fun network tricks will be described later). If the browser authorizes Java
- Get System Info module can gather additional information on the system from a Java Applet including: Operating System details, Java JVM info, IP addresses, Processor/Memory specs, and more.
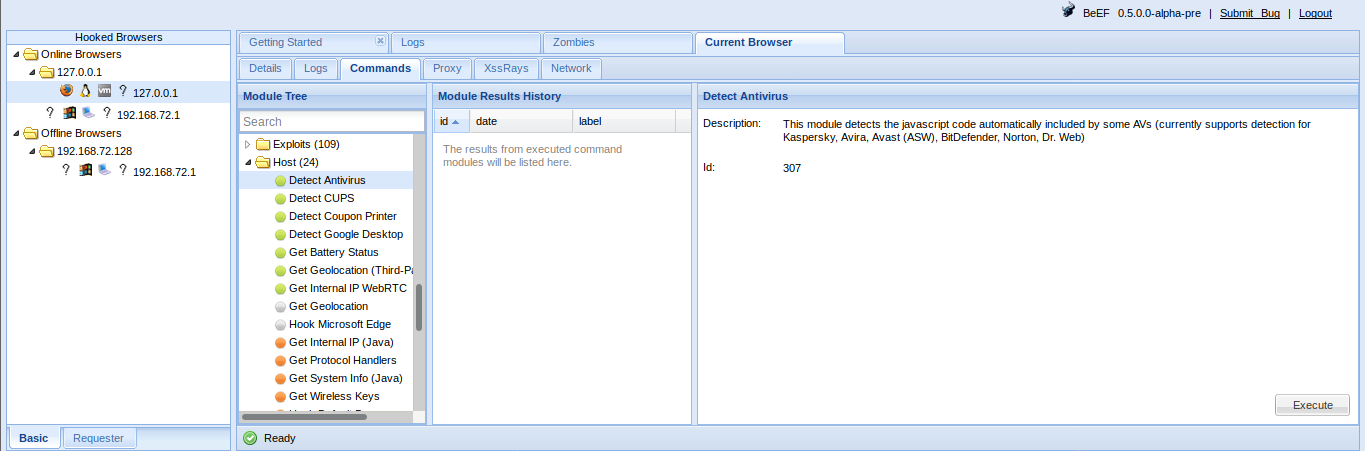
A hooked browser allows BeEF to discover information on the behavior of the user:
- Detect Social Networks module can identify if the user of the hooked browser has a current session on Facebook, Twitter, or Gmail.
- Detect TOR module can identify if the user of the hooked browser is currently using TOR.
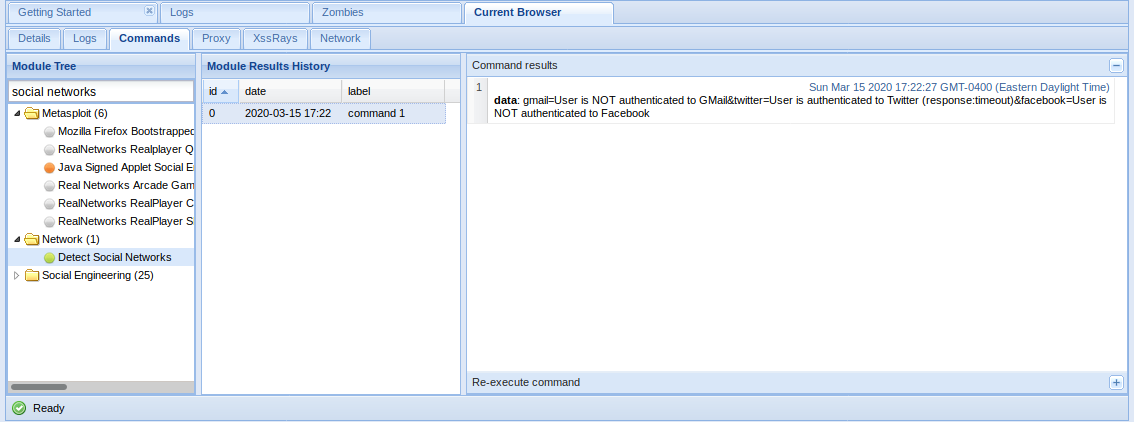
You can search for module names in the search bar at the top of the list.
Social Engineering
BeEF includes a suite of modules to try to gather passwords and usernames
Simple attacks are often the most efficient ones. BeEF comes with several command modules that present the target with familiar interfaces requesting credentials:
- Pretty Theft module prints a simple message to the user requiring login and password, explaining that the session has timed out. It has a number of presets that imitate popular social network/marketplace themes.
- Simple Hijacker module allows you to load a number of common pop-ups when a user clicks any link on their current page. Pop-up templates include certificate warnings, standard alert style prompts, and credit card payment forms.
- Clippy is a module that create a small browser assistant which propose browser updates.
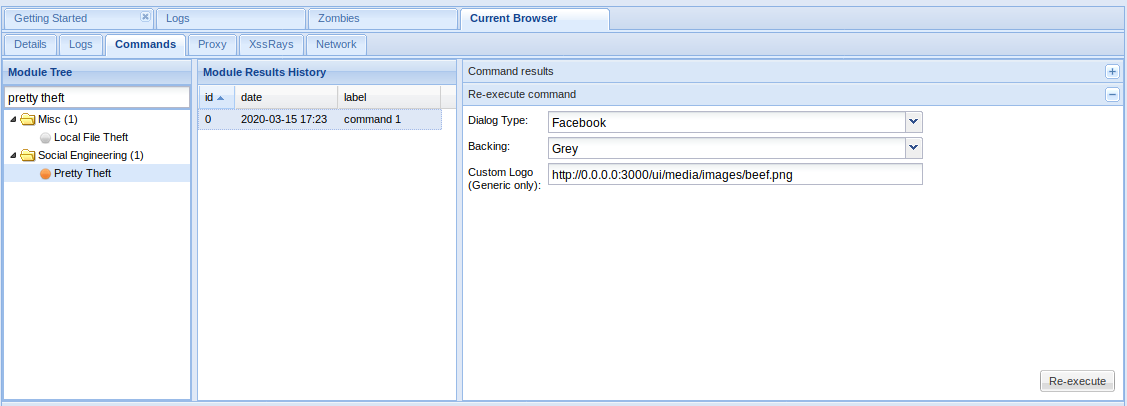
In the Browser
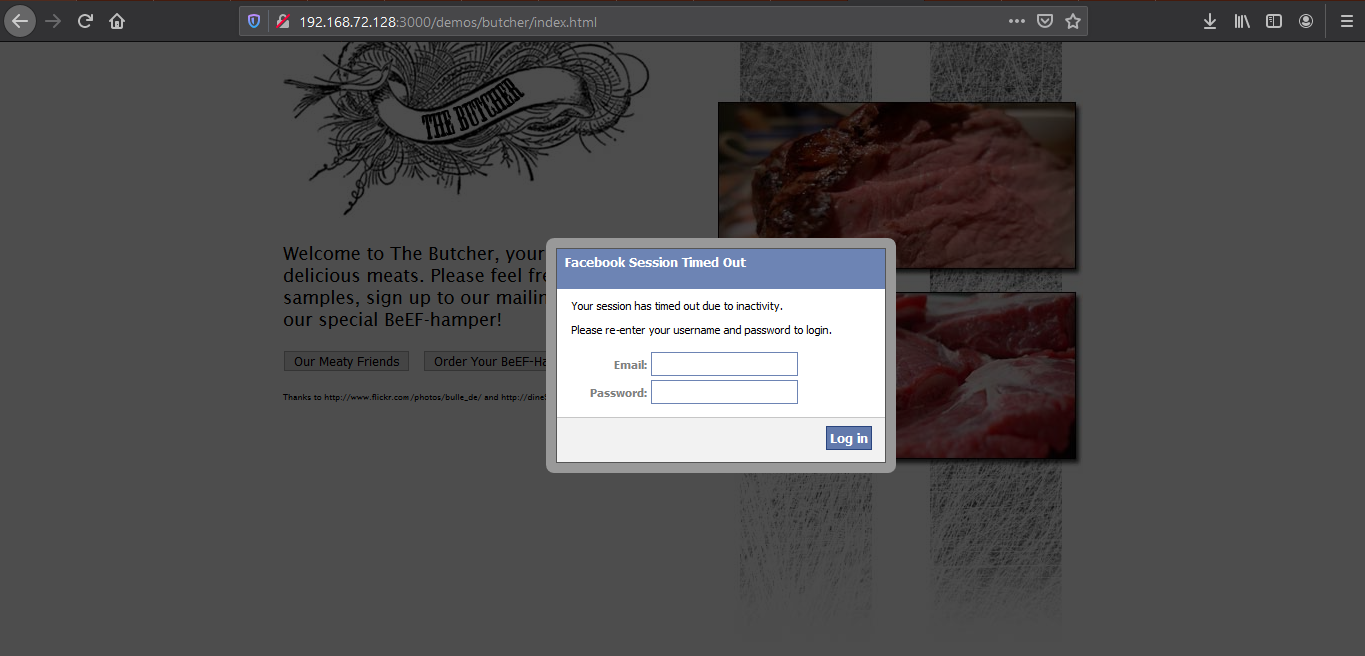
Type something in and then return to BeEF to see if it captured the user input
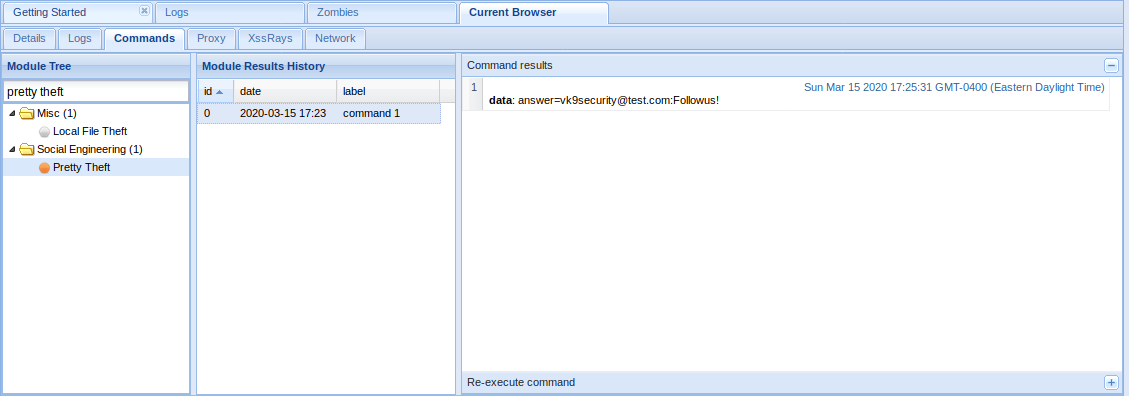
Redirect to Another Page
A number BeEF modules exist that allow you to redirect to external pages:
- Redirect Browser module can redirect the hooked page to any other page.
- Redirect Browser (iFrame) sub-module will create a full viewport iFrame which redirects to the specified URL.
- TabNabbing module will detect when the user loses focus on the current tab and modify it in the background. When the user comes back to the tab, they will be viewing a full viewport iFrame containing the contents of the specified URL.
Redirect Browser
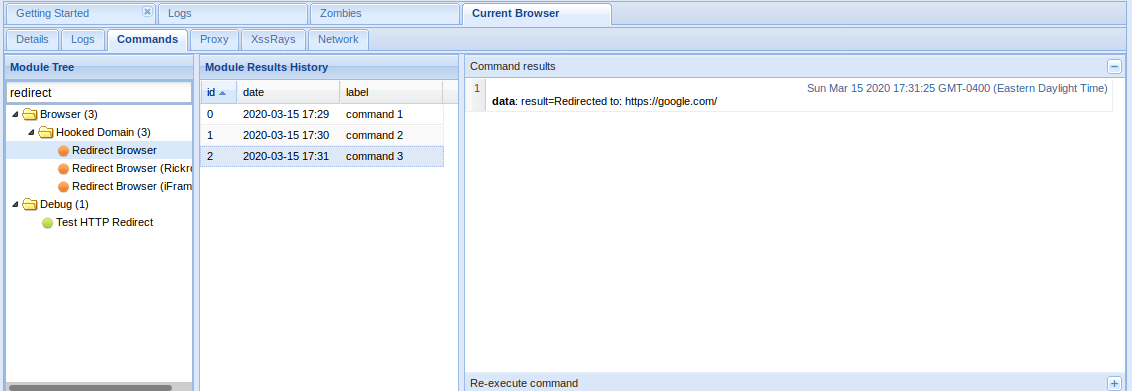
The window got redirected to google.com

Chrome/Firefox Extensions
Using BeEF it is possible to get a user to install a malicious browser extension:
Fake Flash Update module prompts the hooked browser’s user to install a flash update. Instead of installing a Flash update, a browser extension will be installed that can communicate with BeEF and provide access to far more information than is available by default. If the extension were installed in Chrome, for example, BeEF could run the following modules:
- Get All Cookies
- List Chrome Extensions
- Grab Google Contacts from Logged in User
- Inject BeEF in All Tabs
- Execute Arbitrary Javascript Code
- Taking Screenshots
- Send Gvoice SMS
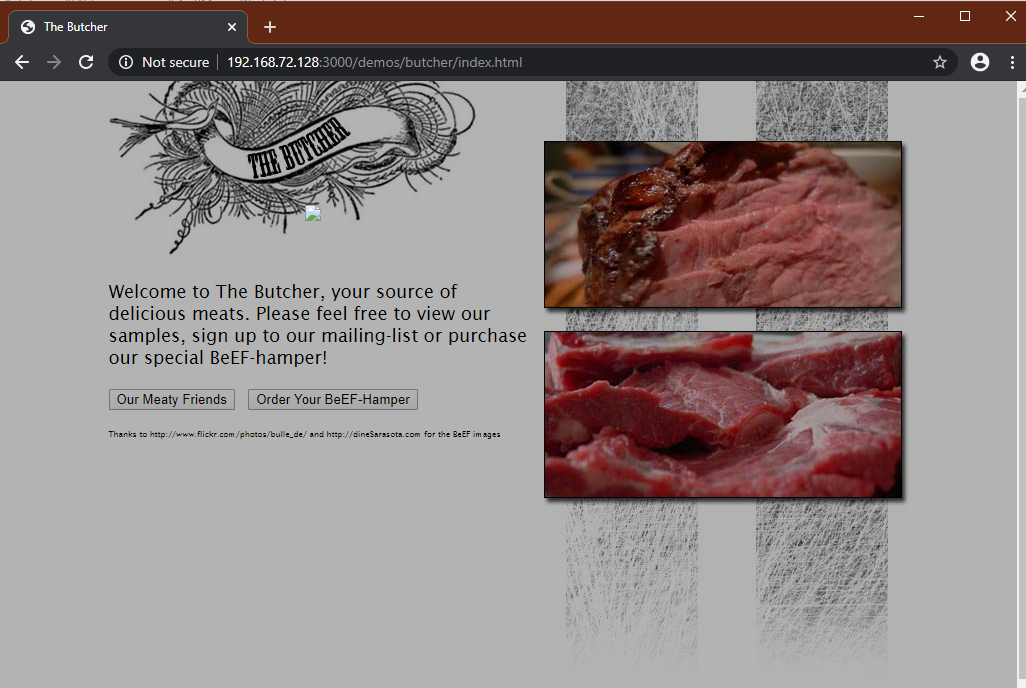
Fake Flash Update
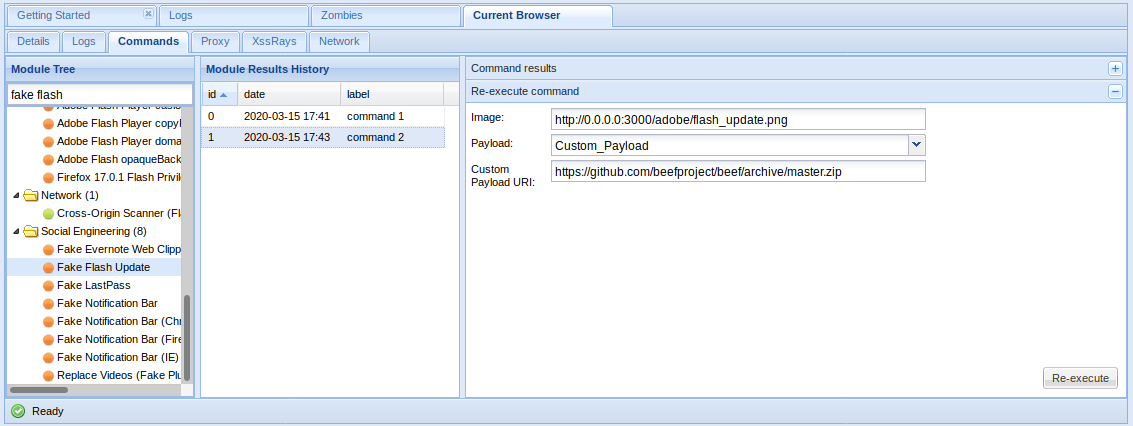
If the user click on it. The payload URI is downloaded
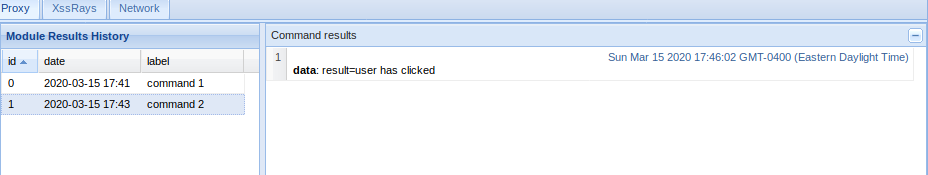
The result is shown in the logs
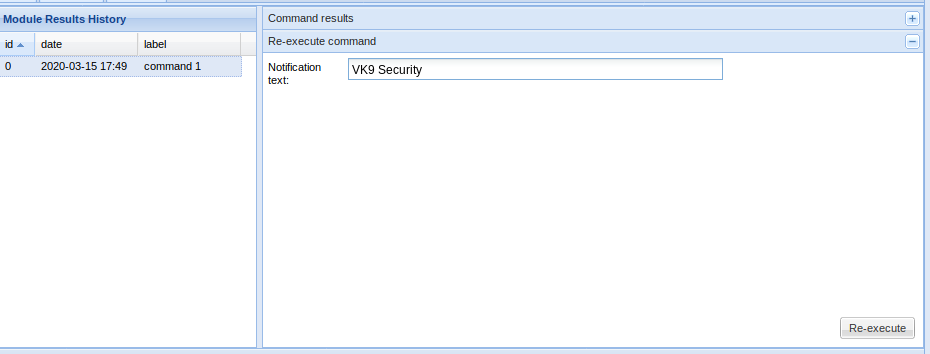
Fake notification Bar
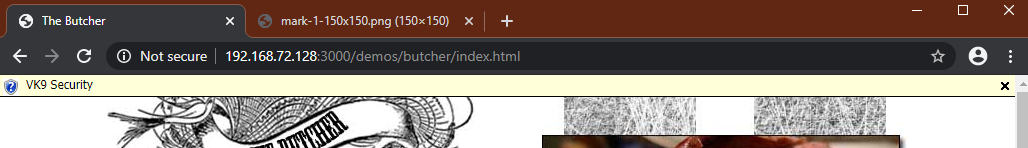
Results
Clickjacking
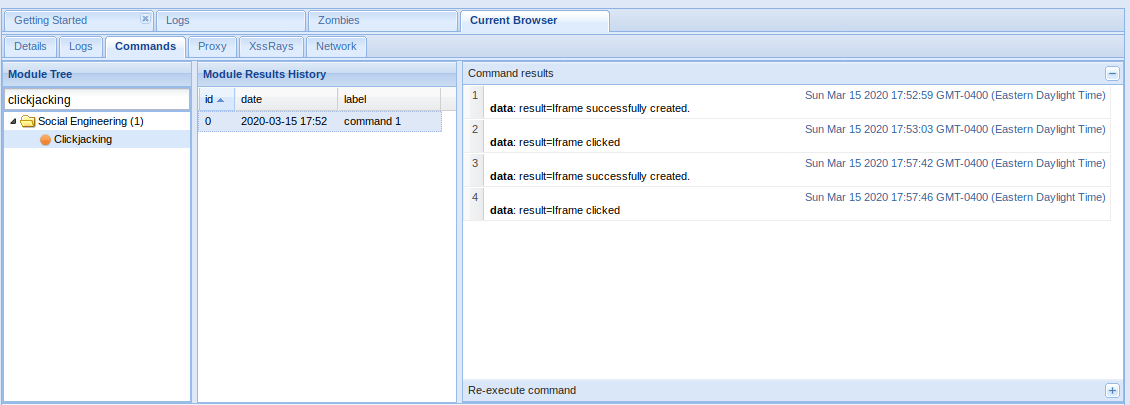
BeEF contains a module that enables clickjacking attacks in a hooked browser:
- Clickjacking module will create an iFrame which follows the users cursor around the page, displaying the content at the specified URL.
Clickjacking
List of Modules
https://github.com/beefproject/beef/wiki/BeEF-modules
Browser
- Browser Fingerprinting
- Detect Firebug
- Detect Popup block
- Detect Unsafe ActiveX
- Get Visited Domains
- Detect Visited URL
- Play Sound
- Unhook
- Webcam
- Get Firefox/Chrome Extensions
- Detect MS Office Version
Hooked Domain
- AJAX Fingerprint
- Alert Dialog
- Deface Web Page
- Get Cookie
- Get Local Storage
- Get Page HTML
- Get Page Links
- Get Session Storage
- Get Stored Credentials
- Link Rewrite
- Link Rewrite (HTTPS)
- Link Rewrite (TEL)
- Link Rewrite (Clicked Event)
- Create Alert Dialog
- Create Prompt Dialog
- Redirect Browser
- Redirect Browser (Rickroll)
- Redirect Browser (iFrame)
- Replace Component (Deface)
- Replace Videos
- iOS Address Bar Spoofing
Chrome Extensions
- Execute On Tab
- Get All Cookies
- Grab Google Contacts
- Inject BeEF
- Screenshot
- Send Gvoice SMS
Debug
- Return Ascii Chars
- Test Network Request
- Test Returning Results
Exploits
- ColdFusion Directory Traversal Exploit
- GlassFish WAR Upload XSRF
- Jboss 6.0.0M1 JMX Deploy Exploit
- Spring Framework Malicious Jar Exploit
- VTiger CRM Upload Exploit
- Zenoss 3.2.1 Add User CSRF
- Zenoss 3.2.1 Daemon CSRF
- boastMachine 3.1 Add User CSRF
Camera
- Dlink DCS series CSRF
- Linksys WVC series CSRF
Local Host
- Windows Mail Client DoS
- ActiveX Command Execution
- Java Payload
- Safari Launch App
Router
- 3COM OfficeConnect Command Execution
- Asmax AR-804gu Command Execution
- BT Home Hub CSRF
- Cisco E2400 CSRF
- Comtrend CT-5367 CSRF
- Comtrend CT 5624 CSRF
- D-Link DIR-615 Password Wipe
- D-Link DSL500T CSRF
- Huawei SmartAX MT880 CSRF
- Linksys BEFSR41 CSRF
- Linksys WRT54G CSRF
- Linksys WRT54G2 CSRF
- Virgin Superhub CSRF
Switch
- Netgear GS108T CSRF
XSS
- AlienVault OSSIM 3.1 XSS
- Cisco Collaboration Server 5 XSS
- Serendipity <= 1.1.1 Add User CSRF
Host
- Detect Google Desktop
- Detect Softwares
- Get Clipboard
- Get Internal IP Java
- Get Internal IP WebRTC
- Get Physical Location
- Get Protocol Handlers
- Get System Info Java
- Hook Default Browser
- Get Geolocation
- Get Registry Keys
- Get Wireless Keys
- Detect CUPS
- Make Telephone Call
- Detect Bit Defender 2012
IPEC
- Bindshell (POSIX)
- Bindshell (Windows)
- Cross Site Printing (XSP)
- DNS Tunnel
- IMAP
- IRC
Miscellaneous
- Create Invisible Iframe
- Google Search
- iFrame Event Key Logger
- iFrame Sniffer
- Local File Theft
- Raw Javascript
Network
- Detect Social Networks
- Detect TOR
- Ping Sweep
- IRC NAT Pinning
- Fingerprint Network
- DNS Enumeration
- Ping Sweep (Java)
- Port Scanner
Persistence
- Man-In-The-Browser
- Confirm Close Tab
- Create Foreground iFrame
- Create Pop Under
Phonegap
- Beep
- Check connection
- Detect PhoneGap
- Geolocation
- List Files
- Persist resume
- Persistence
- Start Recording Audio
- Stop Recording Audio
- Upload File
Social Engineering
- Autocomplete Theft
- Clickjacking
- Clippy
- Fake Evernote Web Clipper Login
- Fake Flash Update
- Fake LastPass
- Google Phishing
- Lcamtuf Download
- Fake Notification Bar
- Fake Notification Bar (Chrome)
- Fake Notification Bar (FF)
- Fake Notification Bar (IE)
- Pretty Theft
- Simple Hijacker
- TabNabbing
My assumption is that Beef will only hook browsers on the LAN? Whenever I try to
http to the hook.js from another network, nothing happens …? Do you recommend
Ngrok for this?
Thanks
YOu must have connectivity from point to point to test from another network. Ngrok could be an option
Thanks for the good writeup. It if truth be told used to be a enjoyment account it. Glance complicated to more introduced agreeable from you! However, how can we be in contact?
nice, hope you learn a lot, in the main page there is my linked in account
Hey very cool website!! Man .. Beautiful .. Amazing .. I’ll bookmark your web site and take the feeds also…I’m happy to find so many useful info here in the post, we need work out more techniques in this regard, thanks for sharing. . . . . .
you won’t regret. be sure, I’ll post more content stay tuned!!
This is the right web site for everyone who really wants to find out about this topic.
You understand so much its almost hard to argue with you (not that I personally would
want to…HaHa). You definitely put a brand new spin on a subject that has been written about for years.
Excellent stuff, just excellent!
I am sure this piece of writing has touched all the internet viewers, its really really fastidious piece of writing on building up new
website.
This site certainly has all of the information and facts I
needed about this subject and didn’t know who to ask.
You could definitely see your expertise in the article you write.
The world hopes for even more passionate writers such as you who are not afraid to mention how they
believe. At all times follow your heart.
Hello, all is going fine here and ofcourse every one is sharing facts, that’s truly good, keep up
writing.
Hey there I am so delighted I found your web site, I really found
you by accident, while I was browsing on Askjeeve for something else,
Nonetheless I am here now and would just like to say many thanks for a incredible post and a
all round enjoyable blog (I also love the theme/design), I don’t have time to read through
it all at the minute but I have book-marked it and also added your RSS feeds, so when I have time I
will be back to read a great deal more, Please do keep up
the great work.
welcome, enjoy the time you stay in the site
Hi, I do believe this is a great blog. I stumbledupon it 😉 I may come back yet again since I book marked it.
Money and freedom is the best way to change, may you be rich
and continue to guide other people.
hope you learn lots here
What’s up, for all time i used to check weblog posts here early in the daylight,
since i love to find out more and more.
we want you all to always learn more
Wonderful blog you have here but I was wanting to know if you knew of any user discussion forums that cover the same topics discussed here?
I’d really love to be a part of online community where I can get suggestions from other knowledgeable individuals that share the same interest.
If you have any suggestions, please let me know. Many thanks!
Wow, incredible weblog structure! How long have you ever been blogging for?
you made blogging look easy. The full look of your site is
excellent, let alone the content material!
Hi there are using WordPress for your blog platform?
I’m new to the blog world but I’m trying to get started
and set up my own. Do you need any html coding knowledge to make your own blog?
Any help would be really appreciated!
Hi there are using WordPress for your site platform?
I’m new to the blog world but I’m trying to get started and set up my own. Do
you require any coding expertise to make your own blog? Any help would be really appreciated!
you can use templates or write your own code
I’m really loving the theme/design of your web site.
Do you ever run into any browser compatibility
issues? A handful of my blog readers have complained
about my blog not working correctly in Explorer but looks
great in Chrome. Do you have any advice to help fix this issue?
Great site you have here.. It’s difficult to find excellent writing
like yours nowadays. I seriously appreciate individuals like you!
Take care!!
Hello! I simply want to offer you a huge thumbs up
for your excellent info you have got here on this post. I’ll be coming back to your site
for more soon.
hello there and thank you for your information – I’ve certainly picked up anything new from right here.
I did however expertise several technical issues using this web site, as I experienced
to reload the web site a lot of times previous to I could get it to load correctly.
I had been wondering if your web host is OK? Not that I am complaining, but sluggish
loading instances times will very frequently affect your placement in google and can damage your quality score if advertising and marketing with Adwords.
Well I’m adding this RSS to my e-mail and could look out for a lot more of your respective fascinating content.
Make sure you update this again soon.
Hello, i think that i noticed you visited my weblog so i came to return the desire?.I’m trying to to find issues
to enhance my web site!I suppose its good enough to make use of some
of your concepts!!
Hey there would you mind sharing which blog platform you’re
using? I’m looking to start my own blog in the near future but I’m having a difficult
time making a decision between BlogEngine/Wordpress/B2evolution and Drupal.
The reason I ask is because your layout seems different then most blogs and I’m looking
for something completely unique. P.S Apologies for being off-topic but I had to
ask!
Use anything you feel conforble with, investigate about the hosting, and the website temple has been altered by me to look like this. Hope this helps
Hey very interesting blog!
I am in fact delighted to read this webpage posts which consists of plenty of valuable facts, thanks for providing these information.
Wow that was unusual. I just wrote an incredibly long comment
but after I clicked submit my comment didn’t show up.
Grrrr… well I’m not writing all that over again. Regardless,
just wanted to say superb blog!
For most recent news you have to pay a quick visit internet
and on the web I found this web page as a best web site for newest updates.
I seriously love your site.. Pleasant colors & theme.
Did you develop this amazing site yourself? Please reply back as I’m attempting to create my own personal website and want to know where you got this from or just what the theme is called.
Kudos!
Thank you, I did alter some code from a site template to make it look like this.
Really enjoyed this article.Really looking forward to read more.
It is perfect time to make some plans for the future and it’s time to be happy. I have read this post and if I could I want to suggest you few interesting things or tips. Maybe you can write next articles referring to this article. I desire to read even more things about it!
Great post.
Having read this I thought it was extremely enlightening.
I appreciate you finding the time and energy to put this
article together. I once again find myself spending
a significant amount of time both reading and leaving comments.
But so what, it was still worthwhile!
Hey I am so delighted I found your blog page, I really found you by mistake, while I was browsing
on Bing for something else, Anyhow I am here now and would
just like to say thanks for a remarkable post and a all round
enjoyable blog (I also love the theme/design), I
don’t have time to browse it all at the moment but I have saved it and also included your RSS feeds, so
when I have time I will be back to read a lot more, Please do keep up the excellent
job.
This is really interesting, You’re a very skilled blogger. I have joined your feed and look forward to seeking more of your great post. Also, I’ve shared your site in my social networks!
Hello to every single one, it’s really a good for me to pay a visit this site,
it consists of important Information.
Excellent article. I’m going through a few of these issues as well..