Apache is an open-source and free web server software
How to use the services (System V)
Start
- /etc/init.d/apache2 start
- Or
- sudo service apache2 start
![]()
View Status
- service apache2 status

Restart the service
- service apache2 restart
Stop the service
- service apache2 stop
- service apache2 status
Steps for RHEL 4.x/5.x/6.x or older
Start
- service httpd start
Stop
- service httpd stop
Restart
- service httpd restart
How to use the services (Systemd)
RHEL 7.x or newer
Start
- systemctl start httpd.service
Stop
- systemctl stop httpd.service
Restart command
- systemctl restart httpd.service
Basic Info
- Document root Directory: /var/www/html or /var/www
- Main Configuration file: /etc/httpd/conf/httpd.conf (RHEL/CentOS/Fedora) and /etc/apache2/apache2.conf (Debian/Ubuntu).
- Default HTTP Port: 80 TCP
- Default HTTPS Port: 443 TCP
- Test your Configuration file settings and syntax: httpd -t
- Access Log files of Web Server: /var/log/apache2/access_log
- Error Log files of Web Server: /var/log/apache2/error_log
Best Practices
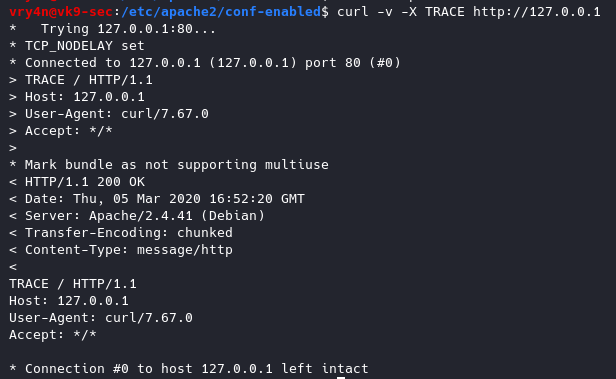
1. Disable TRACE HTTP Request
Having this feature on can lead to Cross Site Tracing attack (XST). (See, https://owasp.org/www-community/attacks/Cross_Site_Tracing )
TraceEnable on allows for Cross Site Tracing Issue and potentially giving the option to a hacker to steal your cookie information.
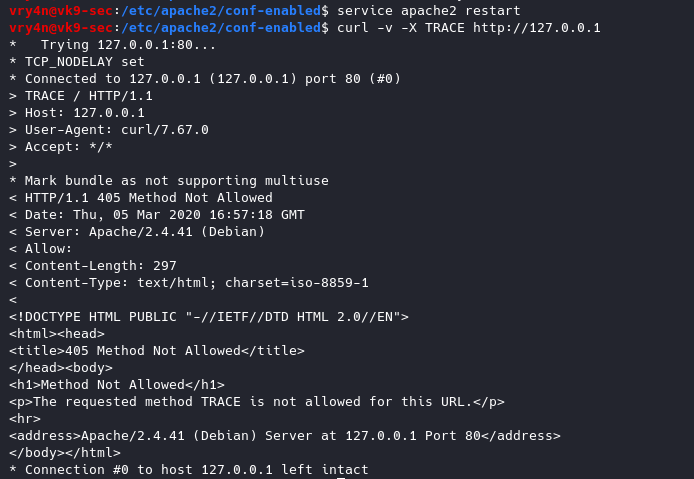
- curl -v -X TRACE http://127.0.0.1
Solution
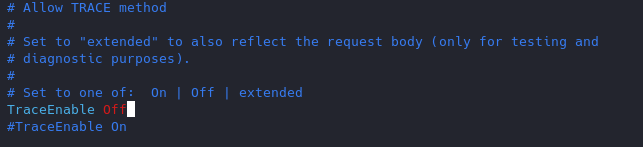
Set the TraceEnable directive to “off” in the main configuration file and then restart Apache. (the directory may vary depending on apache installation, see user guide for more information)
- sudo vi /etc/apache2/conf-enabled/security.conf
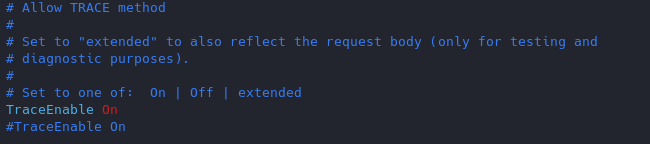
- TraceEnable off
Restart apache service and try to run again curl command
- service apache2 restart
- curl -v -X TRACE http://127.0.0.1
2. Set User & Group
Never run as root, You can set a default user with minimal rights and accesses to exclusively run apache it can be set as follows
- vi /etc/apache2/envvars
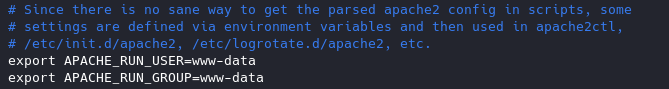
www-data is used by default by most administrators we can leave it as it is or modify the values at will.
3. Disable Signatures
By default apache displays the version of the web service install as an error, can also show the information about Apache modules installed in your server.
Solution
Turn Off “ServerSignature”
- vi /etc/apache2/conf-enabled/security.conf
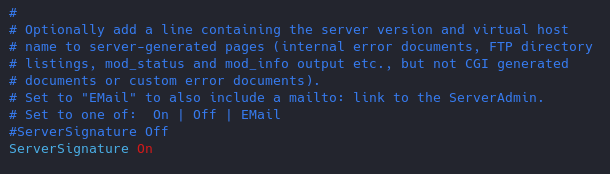
- ServerSignature Off
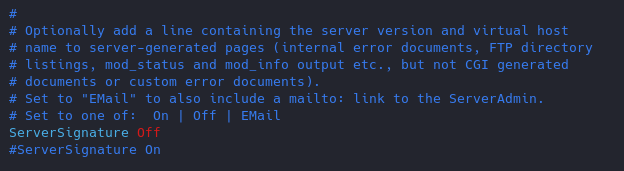
Results
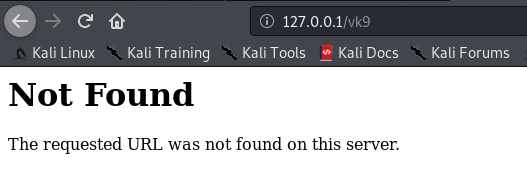
(Optional)
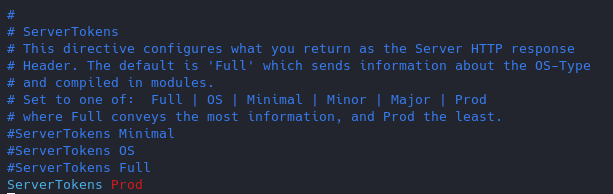
Change the “serverTokens” value to hide OS-Type and modules disclosure. This also disables Banner
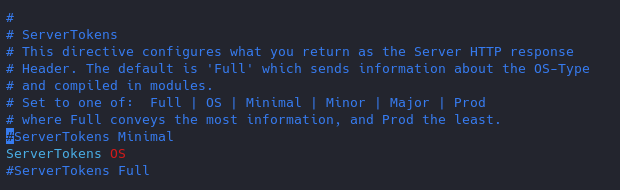
Having this feature on it displays in the response that the OS is Debian
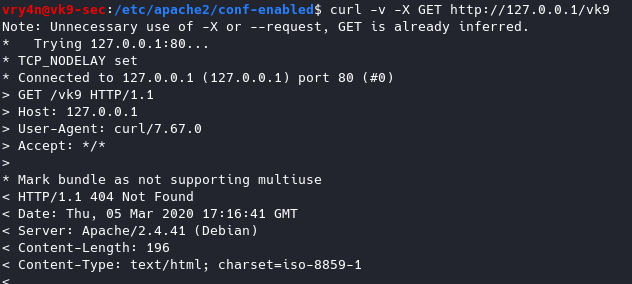
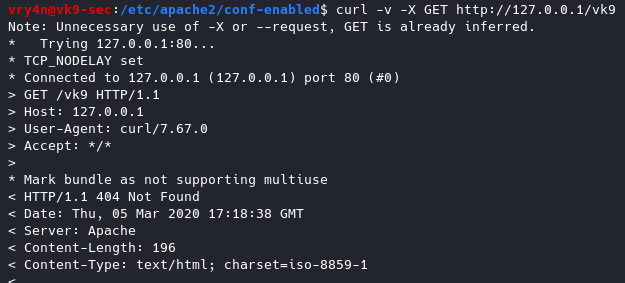
- ServerTokens Prod
Now the OS info is not disclosed
4. Restrict access to some network/file type
if the files are sensitive for example. Config file /etc/apache2/apache2.conf
File access control
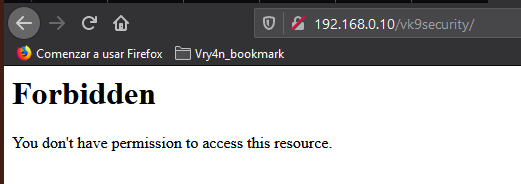
As of now, we can access 127.0.0.1/vk9security/
- Restrict index.php from anyone
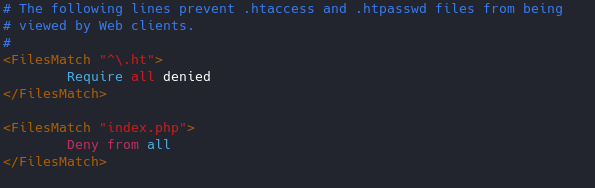
Result
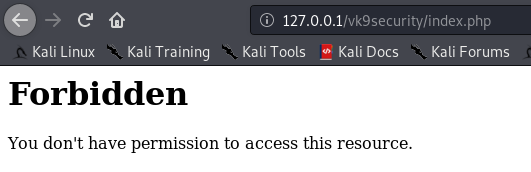
Note: I can still access other resources that are not index.php, like, index.html

Network access control
You can control which networks access which resources, in this case we are only allowing loopback 127.0.0.1.
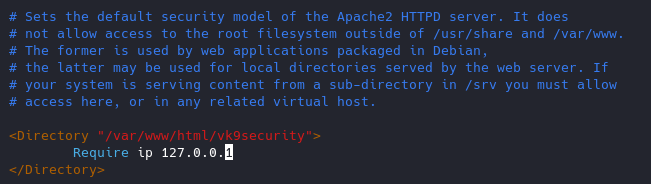
- From 192.168.0.2
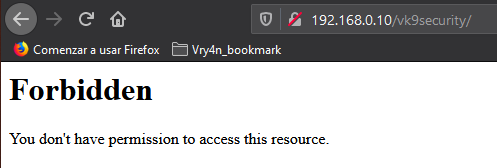
- From 127.0.0.1
5. Use strong encryption HTTPS
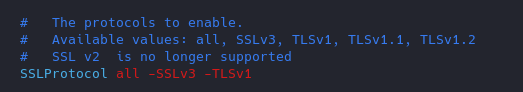
Use TLS 1.2, disable SSL v2 & v3
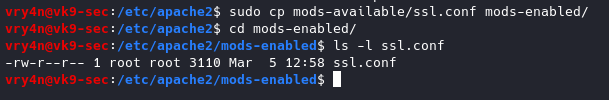
1. Copy the module ssl.conf from mods-available to mods-enabled
- sudo cp mods-available/ssl.conf mods-enabled/ (or create a link to the original file)
- cd mods-enabled
- ls -l ssl.conf
Highlight
Better to use a2enmod to activate the module
2. Modify the ssl.conf file and negate some protocols
- vi ssl.conf
6. You can remove unused or unnecessary modules
https://haydenjames.io/strip-apache-improve-performance-memory-efficiency/
Disable modules
- a2dismod dnssd
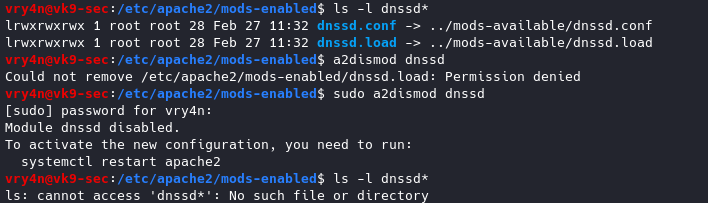
To enable a module
sudo a2enmod <module_name>
7. Control Ciphers
You can choose what ciphers are allowed
- vi ssl.conf
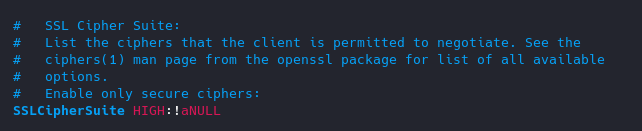
List of Ciphers
https://curl.haxx.se/docs/ssl-ciphers.html
8. Keep it updated!
Always use the latest software version.
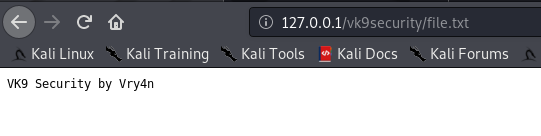
9. Void directory listing
This works almost like “ls” linux & dir “windows”
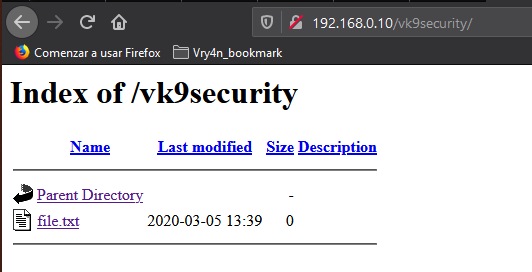
- vi /etc/apache2/apache2.conf
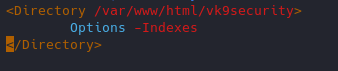
Result
We still have access to the file
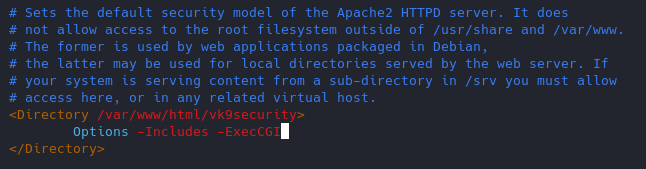
10. Turn off Server side Includes and CGI execution
If not in use turn off SSI and CGI
Server Side Includes: SSI are inserted into HTML code that allows us insert dynamic content in our web sites.
CGI: The Common Gateway Interface (CGI) is a set of rules for running scripts and programs on a Web server. Most Web servers include a cgi-bin directory in the root folder of each website on the server. Any scripts placed in this directory must follow the rules of the Common Gateway Interface.
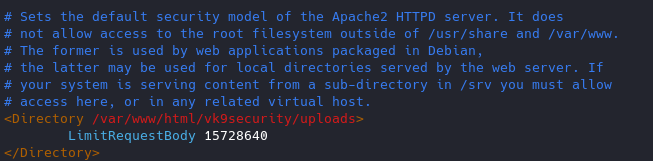
11. Limit the Request size
By default, Apache has no limit on the total size of the HTTP request (it’s possible that you could be a victim of Denial of service attacks)
You can set the value in bytes from 0 (unlimited) to 2147483647 (2GB) that are allowed in a request body.
If you upload files, and, you want to limit the upload size for a particular directory. (in Bytes)
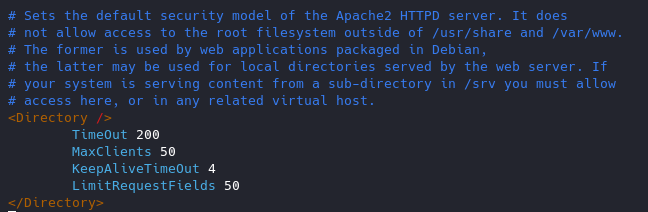
12. Protect against DDoS
it’s true that you cannot completely protect your web site from DDos attacks. Here are some directives which can help you to have a control on it.
- TimeOut : This directive allows you to set the amount of time the server will wait for certain events to complete before it fails. Its default value is 300 secs. It’s good to keep this value low on those sites which are subject to DDOS attacks.
- MaxClients : This directive allows you to set the limit on connections that will be served simultaneously. Every new connection will be queued up after this limit. The default value of it is 256.
- KeepAliveTimeout : Its the amount of time the server will wait for a subsequent request before closing the connection. Default value is 5 secs.
- LimitRequestFields : It helps us to set a limit on the number of HTTP request’s header fields that will be accepted from the clients. Its default value is 100. It is recommended to lower this value if DDos attacks are occurring as a result of so many http request headers.
- LimitRequestFieldSize : It helps us to set a size limit on the HTTP Request header.
13. Enable apache Logging
Apache allows you to logging independently of your OS logging. It is wise to enable Apache logging, because it provides more information, such as the commands entered by users that have interacted with your Web server.
To do so you need to include the mod_log_config module. There are three main logging-related directives available with Apache.
- TransferLog: Creating a log file.
- LogFormat : Specifying a custom format.
- CustomLog : Creating and formatting a log file.
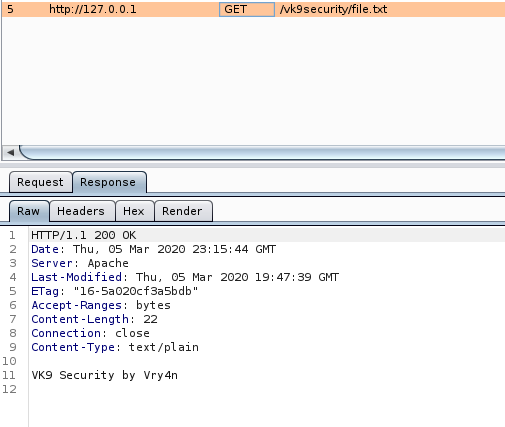
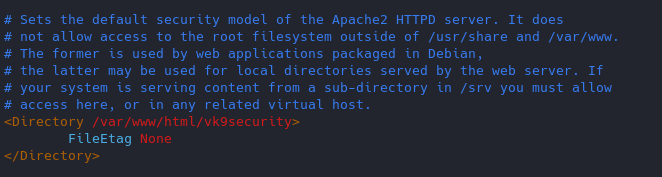
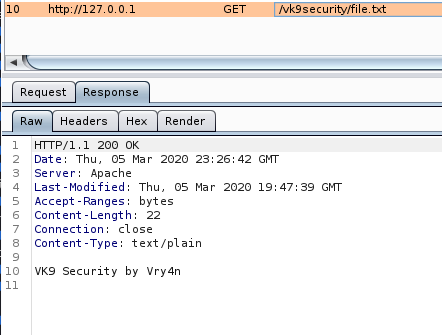
14. Disable Etag
It allows remote attackers to obtain sensitive information like inode number, multipart MIME boundary, and child process through Etag header.
ETag (entity tag) response header provides a mechanism to cache unchanged resources. Its value is an identifier which represents a specific version of the resource. Here’s an example ETag header:
Disabling ETag
Response
15. change config files permission
- chmod -R 750 <filename>
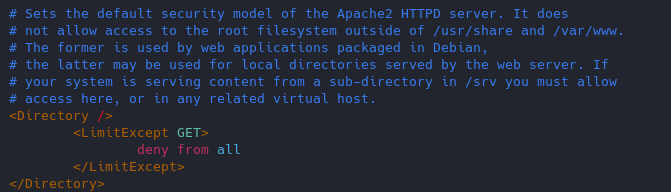
16. Restict HTTP methods in use
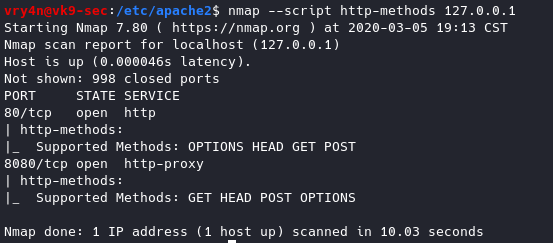
Using nmap we can query for the methods allowed
- nmap –script http-methods 127.0.0.1
Enabling methods
Results of nmap
- nmap –script http-methods 127.0.0.1
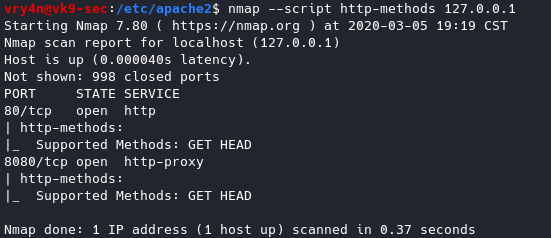
17. Set cookies (HttpOnly & Secure flag)
You can mitigate most of the common Cross Site Scripting attack using HttpOnly and Secure flag in a cookie. Without having HttpOnly and Secure, it is possible to steal or manipulate web application session and cookies, and it’s dangerous.
- Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
You can set up cookies using PHP or the config files of apache2.
18. Prevent Clickjacking
Clickjacking is a well-known web application vulnerabilities.
- Header always append X-Frame-Options SAMEORIGIN
19. Protection against Cross Site Scripting
Cross Site Scripting (XSS) protection can be bypassed in many browsers. You could apply this protection for a web application if it was disabled by the user. This is used by a majority of giant web companies like Facebook, Twitter, Google, etc.
- Header set X-XSS-Protection “1; mode=block”