
Description
OneDrive users have a file share URL with a known location:
https://acmecomputercompany-my.sharepoint.com/personal/lightmand_acmecomputercompany_com/_layouts/15/onedrive.aspx
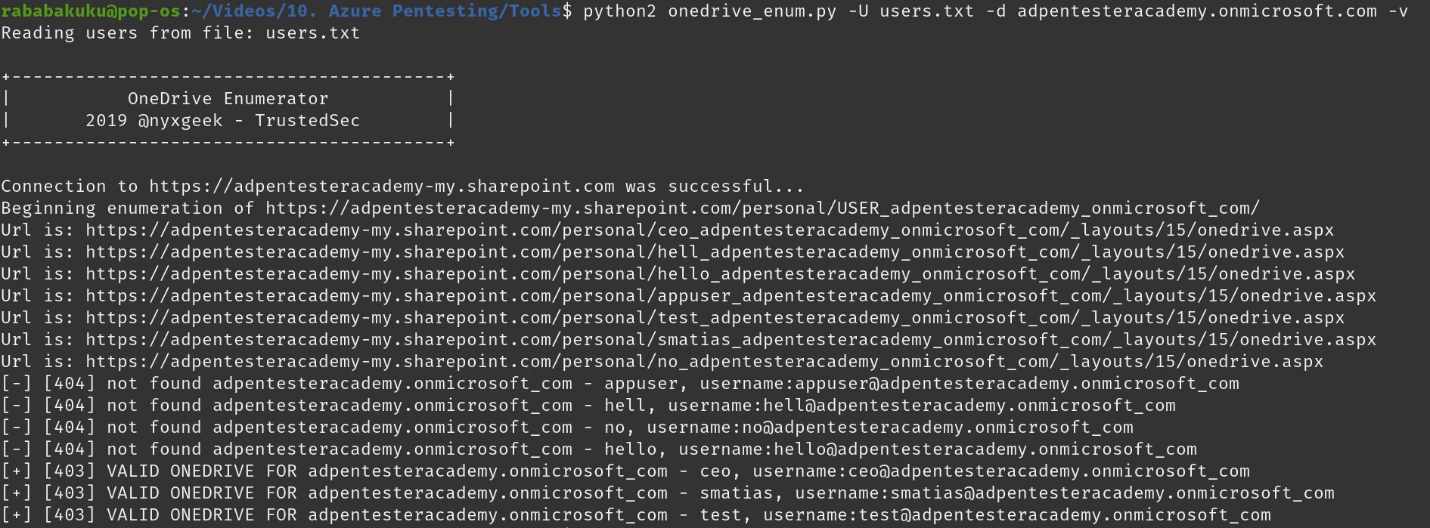
In this instance, the username is ‘lightmand’ and the domain is ‘acmecomputercompany.com’. If a user has logged into OneDrive, this path will exist and return a 403 status code. If they have not, or the user is invalid, it will return a 404.
The results may vary depending on how widely used OneDrive is within an org. Currently it is the most reliable user-enumeration method that I’m aware of (office365userenum no longer works, and the others like UhOh365 are unreliable). Further, it does not attempt a login and is much more passive, and should be undetectable to the target org. Microsoft will see the hits, but the target org won’t.
Requirements
- Tenant name
- Username or user list <found usernames>
- Domain name
How to Use
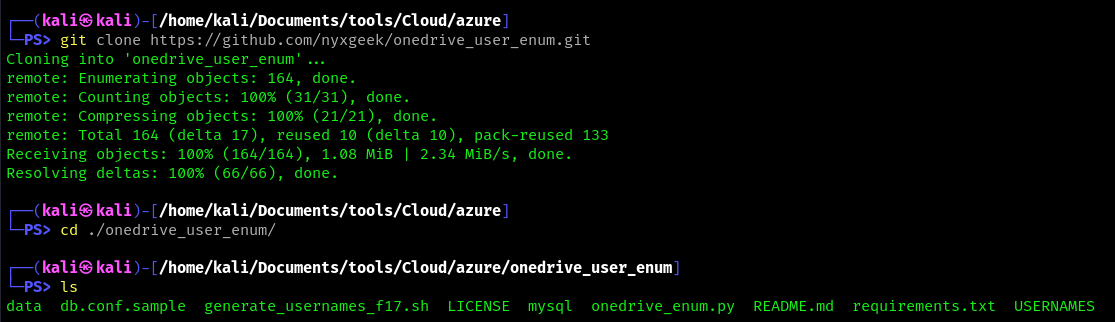
1. Download the tool
- git clone https://github.com/nyxgeek/onedrive_user_enum.git
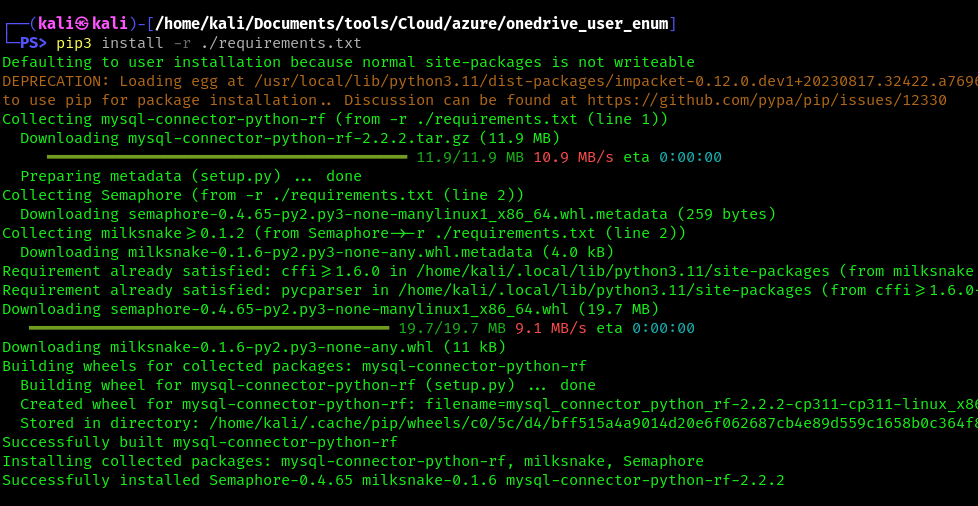
2. Install requirements
- pip3 install -r requirements.txt
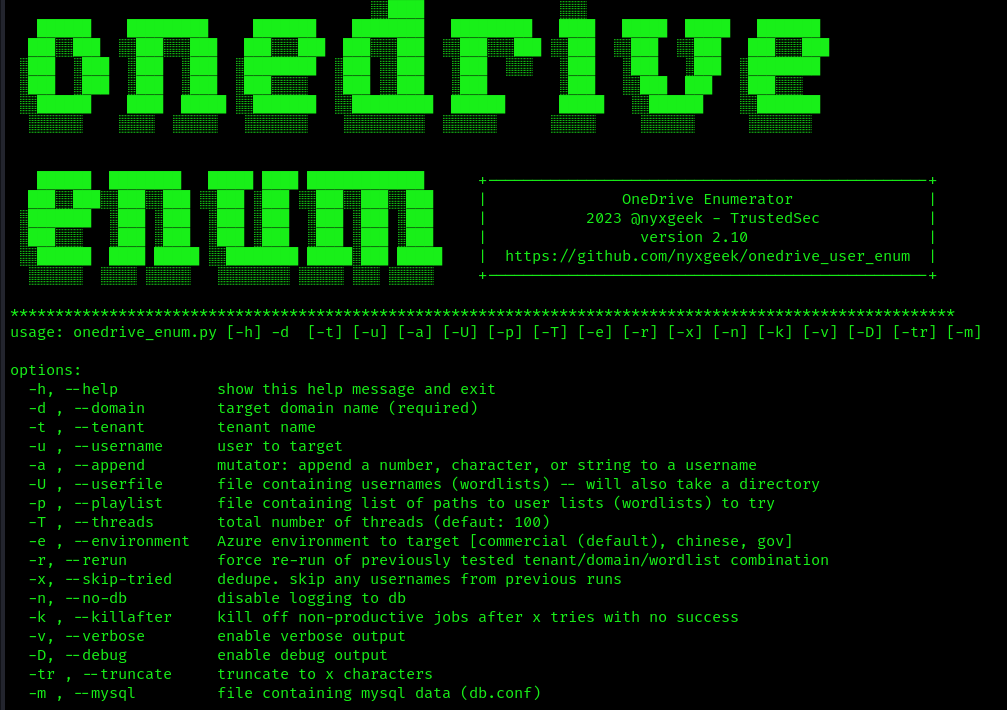
3. Display menu
- python3 ./onedrive_enum.py -h
Exploitation
1. Run basic OneDrive user enumeration
- python3 onedrive_enum.py -U <user_list> -d <domain.onmicrosoft.com> -v
2. example – basic usage
- ./onedrive_enum.py -t microsoft -d microsoft.com -U USERNAMES/statistically-likely/jsmith.txt
3. example – mysql db logging
- ./onedrive_enum.py -t microsoft -d microsoft.com -U USERNAMES/statistically-likely/jsmith.txt -m db.conf
4. Set Threads
- python3 onedrive_enum.py -U <user_list> -d <domain.onmicrosoft.com> -v -T100