DNS is a naming system for computers that converts human readable domain names e.g. (infosecinstitute.com) into computer readable IP-addresses.
However, some security vulnerabilities exist due to misconfigured DNS name servers that can lead to information disclosure about the domain. This forms an important step of the Information Gathering stage during a Penetration test or Vulnerability assessment.
https://www.varonis.com/blog/what-is-dns/
DNS basics
Let’s say the user opens up the browser and types in infosecinstitute.com. It is now the responsibility of the DNS resolver in the user’s operating system to fetch the IP address. It first checks its local cache to see if it can find a record for the queried domain name. A cache usually contains a mapping of IP-addresses to hostnames which are saved during recent lookups so that the resolver does not have to fetch the IP address again and again. If it can’t find the IP address in its cache it queries the DNS server to see if it has a record for it. A DNS server is usually given to you by the ISP or you can manually set up a DNS server for yourself. If it still can’t find the IP Address then it goes through a process or recursive DNS query in which it queries different name servers to get the IP-address of the domain. As soon as it finds the IP-address it returns the IP-address back to the user and also caches it for its future use.
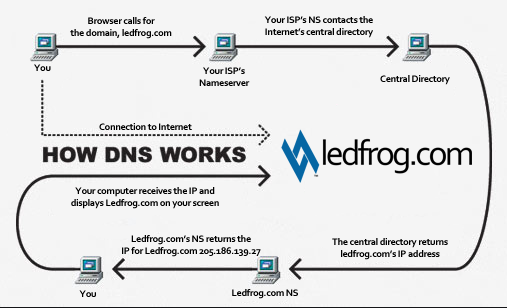
Basic DNS query
- nslookup
- set type=a
- google.com
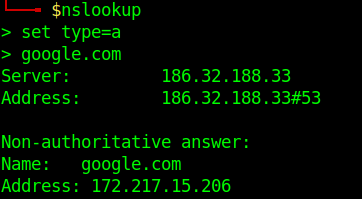
Network view of the request.
![]()
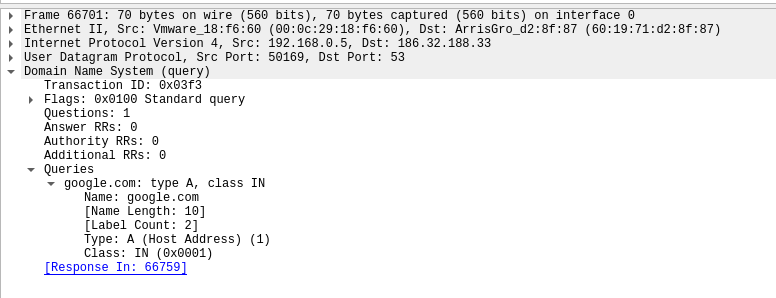
Request:
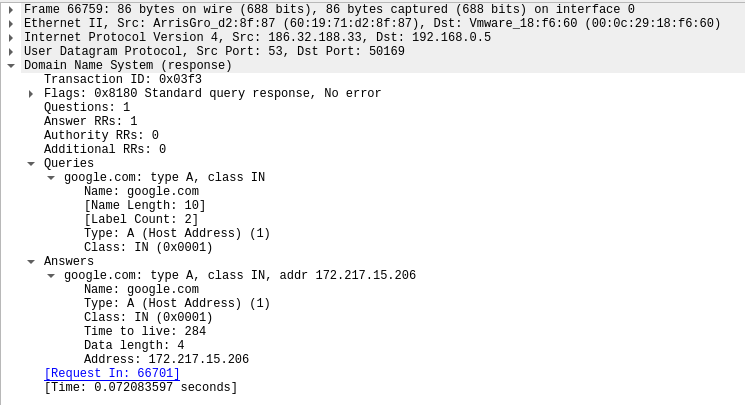
Response:
Running queries with dig
- dig google.com
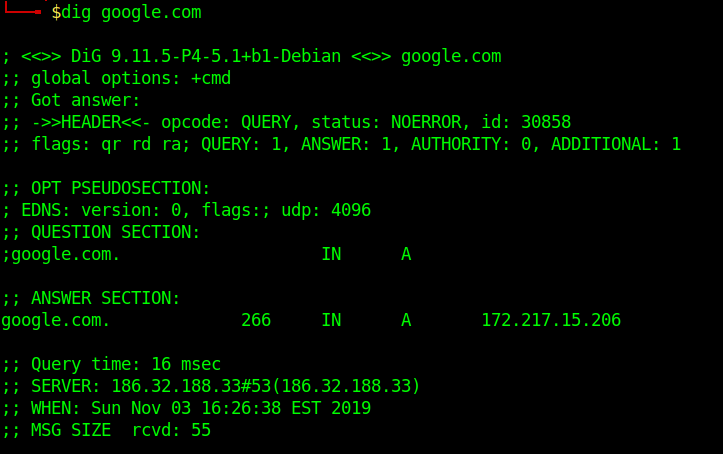
To simplify the output, we will be using those extra parameters on the following commands:
+nocmd – Removes the +cmd options output
+noall – Removes extra headers, flags, time information, message size, etc.
+answer – Tells dig to return the answer section (the “juicy” part of the output).
To specify the record we would like to query, we just have to add the record type right after the domain specification. Here is a basic syntax we will use:
- dig +nocmd google.com <record> +noall +answer
![]()
DNS Types: 10 Top DNS Record Types
DNS servers create a DNS record to provide important information about a domain or hostname, particularly its current IP address. The most common DNS record types are:
Address Mapping record (A Record)—also known as a DNS host record, stores a hostname and its corresponding IPv4 address.
IP Version 6 Address record (AAAA Record)—stores a hostname and its corresponding IPv6 address.
Canonical Name record (CNAME Record)—can be used to alias a hostname to another hostname. When a DNS client requests a record that contains a CNAME, which points to another hostname, the DNS resolution process is repeated with the new hostname.
Mail exchanger record (MX Record)—specifies an SMTP email server for the domain, used to route outgoing emails to an email server.
Name Server records (NS Record)—specifies that a DNS Zone, such as “example.com” is delegated to a specific Authoritative Name Server, and provides the address of the name server.
Reverse-lookup Pointer records (PTR Record)—allows a DNS resolver to provide an IP address and receive a hostname (reverse DNS lookup).
Certificate record (CERT Record)—stores encryption certificates—PKIX, SPKI, PGP, and so on.
Service Location (SRV Record)—a service location record, like MX but for other communication protocols.
Text Record (TXT Record)—typically carries machine-readable data such as opportunistic encryption, sender policy framework, DKIM, DMARC, etc.
Start of Authority (SOA Record)—this record appears at the beginning of a DNS zone file, and indicates the Authoritative Name Server for the current DNS zone, contact details for the domain administrator, domain serial number, and information on how frequently DNS information for this zone should be refreshed.
DNS Types: 3 DNS Query Types
There are three types of queries in the DNS system:
Recursive Query
In a recursive query, a DNS client provides a hostname, and the DNS Resolver “must” provide an answer—it responds with either a relevant resource record, or an error message if it can’t be found. The resolver starts a recursive query process, starting from the DNS Root Server, until it finds the Authoritative Name Server (for more on Authoritative Name Servers see DNS Server Types below) that holds the IP address and other information for the requested hostname.
Iterative Query
In an iterative query, a DNS client provides a hostname, and the DNS Resolver returns the best answer it can. If the DNS resolver has the relevant DNS records in its cache, it returns them. If not, it refers the DNS client to the Root Server, or another Authoritative Name Server which is nearest to the required DNS zone. The DNS client must then repeat the query directly against the DNS server it was referred to.
Non-Recursive Query
A non-recursive query is a query in which the DNS Resolver already knows the answer. It either immediately returns a DNS record because it already stores it in local cache, or queries a DNS Name Server which is authoritative for the record, meaning it definitely holds the correct IP for that hostname. In both cases, there is no need for additional rounds of queries (like in recursive or iterative queries). Rather, a response is immediately returned to the client.
Zone file
A Zone file is basically a text file present on the server hosting the domain that contains entries for different resource records. Each line is represented by a different record.
Each zone file must start with a Start of Authority (SOA) record containing an authoritative name server for the domain (for e.g. ns1.google.com for google.com) and an email address of someone responsible for the management of the name server.
Domains can be very large, so they are further organized into smaller books, called, “zones.” No single DNS server stores all the books – that would be impractical.
Different types of Resource Records exist within a Zone file. However we are going to discuss some of the important ones
- A Records– Maps an IP Address to a hostname.For e.g. 74.125.236.80 for google.com.
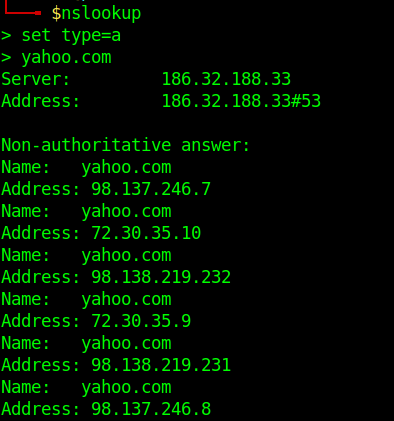
- nslookup
- set type=a
- yahoo.com
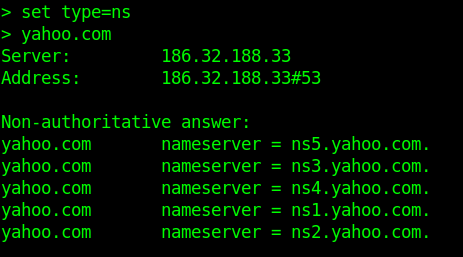
- NS Records-Delegates a given zone to use the given authoritative nameserver. For e.g. ns1.google.com is an authoritative nameserver for google.com
- set type=ns
- yahoo.com
-
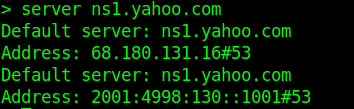
- server ns1.yahoo.com (set this as main server)
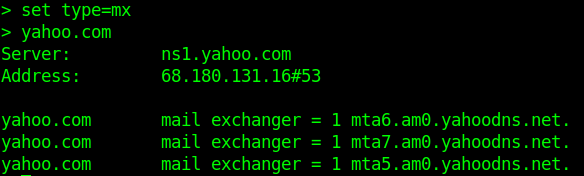
- MX Records-This basically tells us which server is responsible for receiving mails sent to that domain name.
- set type=mx
- yahoo.com
- TXT Records-This consists of arbitrarily human readable text in a record.
- CNAME Records– Gives an alias of one name to another.
Enumeration
Nmap
- nmap –script=broadcast-dns-service-discovery google.com
- nmap -T4 -p 53 –script dns-brute google.com
- nmap -Pn -sU -p 53 –script=dns-recursion google.com
DNSEnum
Multithreaded Perl script to enumerate DNS information of a domain and to discover non-contiguous IP blocks.
OPERATIONS:
- Get the host’s address (A record).
- Get the nameservers (threaded).
- Get the MX record (threaded).
- Perform axfr queries on nameservers and get BIND VERSION (threaded).
- Get extra names and subdomains via google scraping (google query = “allinurl: -www site:domain”).
- Brute force subdomains from a file can also perform recursion on a subdomain that has NS records (all threaded).
- Calculate C class domain network ranges and perform whois queries on them (threaded).
- Perform reverse lookups on netranges ( C class or/and whois netranges) (threaded).
- Write to domain_ips.txt file IP-blocks.
Execution
- dnsenum –noreverse google.com

DNSRecon
DNSRecon provides the ability to perform:
- Check all NS Records for Zone Transfers
- Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT)
- Perform common SRV Record Enumeration. Top Level Domain (TLD) Expansion
- Check for Wildcard Resolution
- Brute Force subdomain and host A and AAAA records are given a domain and a wordlist
- Perform a PTR Record lookup for a given IP Range or CIDR
- Check a DNS Server Cached records for A, AAAA and CNAME Records provided a list of host records in a text file to check
- Enumerate Common DNS records in the Local Network Enumerate Hosts and Subdomains using Google
Execution
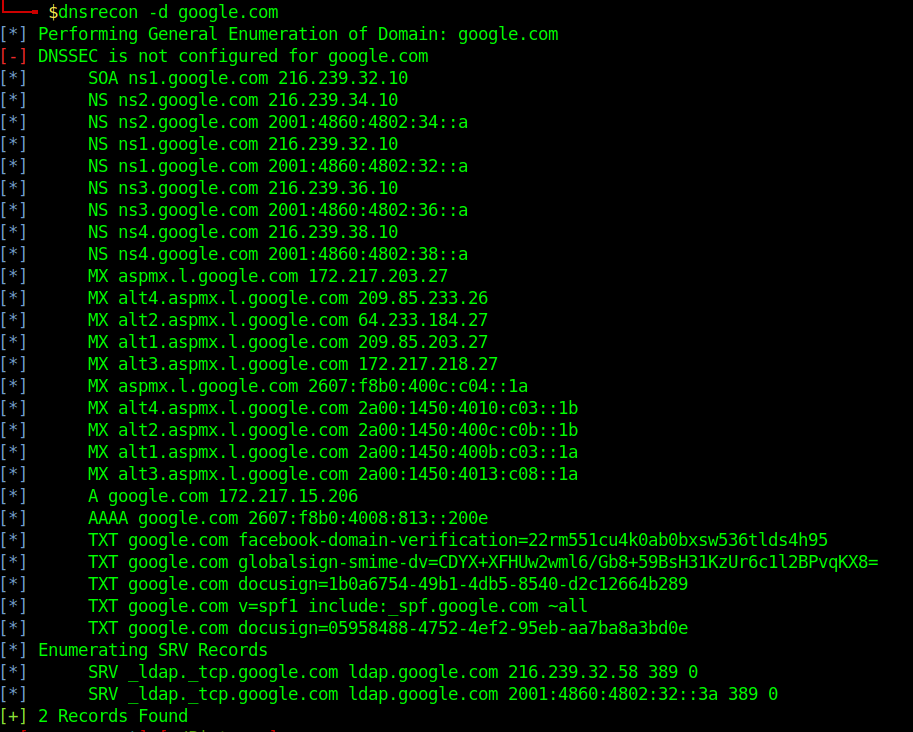
- dnsrecon -d google.com
Fierce
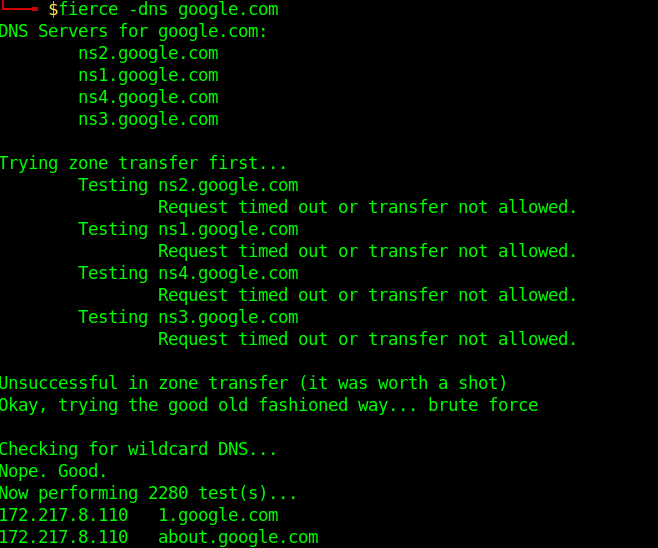
Fierce is a reconnaissance tool. Fierce is a PERL script that quickly scans domains (usually in just a few minutes, assuming no network lag) using several tactics
Execution
- fierce –dns google.com
Know the DNS server name
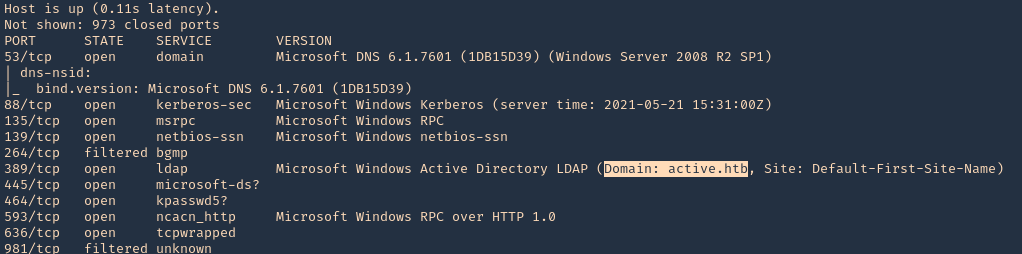
1. Scanning a host with nmap we can sometimes find a domain name, in this case LDAP
- nmap -sV -sC -A -T5 10.10.10.100
2. This server also has DNS (port 53) service opened. We can consult it
- nslookup
- server 10.10.10.100
- 127.0.0.1
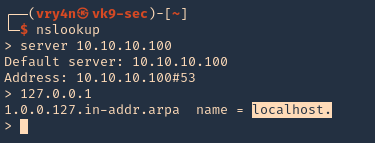
3. We now know this server is localhost, so, the FQDN would be localhost.active.htb