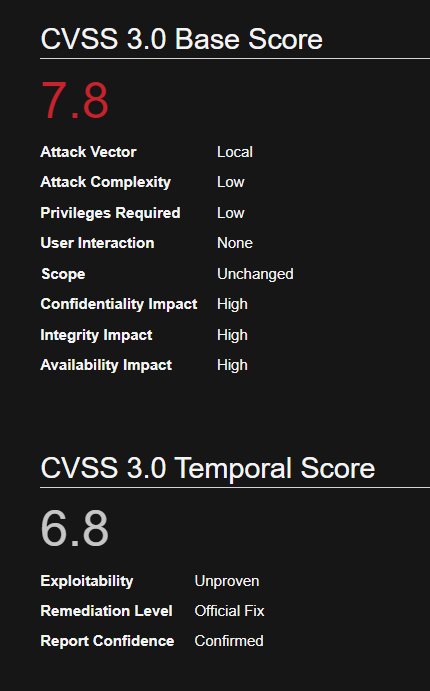
Microsoft Windows could allow a local authenticated attacker to gain elevated privileges on the system, caused by improper enforcement of user privileges in the Certificate Dialog. By executing a specially-crafted program, an authenticated attacker could exploit this vulnerability to execute arbitrary code with higher privileges.
To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.
This CVE exploit tend to abuse the UAC windows Certificate Dialog to execute the certificate issuer link as an NT Authority User and open a browser that is under NT Authority User. Then we can use that to prompt a shell as a NT Authority User.
What is Certificate Dialog?
The UAC (User Account Control) Windows Certificate Dialog is a component of the UAC system in Microsoft Windows. UAC is a security feature implemented in Windows Vista and later versions to mitigate the risks of unauthorized or malicious actions by prompting users for confirmation before allowing certain operations that require administrative privileges.
How UAC Windows Certificate Dialog Works:
- User Initiates Action: When a user or an application attempts to perform an action that requires administrative privileges, such as installing or modifying certificates, a UAC prompt is triggered.
- UAC Prompt: The UAC Windows Certificate Dialog appears, notifying the user that the action requires administrative rights. The dialog presents information about the application and the action being requested.
- User Confirmation: The user must confirm the action by providing administrative credentials, typically an administrator’s username and password.
- Privilege Elevation: Upon confirmation, Windows grants the application or process the necessary elevated privileges to carry out the requested action. This might involve launching a separate process with administrative rights.
- Action Execution: With the elevated privileges, the application can now perform the certificate-related operation that requires administrative access.
The prompts themselves are produced by an executable named consent.exe, running as NT AUTHORITY\SYSTEM and having an integrity level of System. Since the user can interact with this UI, it is necessary for the UI to be very tightly constrained. Otherwise, a low privileged user might be able to perform actions as SYSTEM via a circuitous route of UI operations. Even a solitary UI feature that appears harmless in isolation could potentially be the first step in a chain of actions leading to arbitrary control.
There is an obscure Microsoft-specific object identifier (OID) defined, having the numeric value 1.3.6.1.4.1.311.2.1.22.

The WinTrust.h header defines this as SPC_SP_AGENCY_INFO_OBJID, and, if present, it will be displayed in the Details tab as SpcSpAgencyInfo.

Affected Systems
SERVER
Windows 2008r2 7601
Windows 2012r2 9600
Windows 2016 14393
Windows 2019 1773
WORKSTATION
Windows 7 SP1 7601
Windows 8 9200
Windows 8.1 9600
Windows 10 1511 10240
Windows 10 1607 14393
Windows 10 1703 15063
Windows 10 1709 16299
Steps to abuse this vulnerability
1) Verify the current user you are, using cmd
- whoami

2) find a program that can trigger the UAC prompt screen, run it as administrator. (In this demo I used: https://github.com/jas502n/CVE-2019-1388, HHUPD.exe)

3) select “Show more details”
4) select “Show information about the publisher’s certificate”
5) click on the “Issued by” URL link it will prompt a browser interface. Then click OK to close this “Certificate” window and exit the UAC prompt

6) wait for the site to be fully loaded & select “save as” to prompt a explorer window for “save as”.
Note: In my case, the webpage didn’t actually fully load so if that happens to you it is no worry, just verify within the address bar that it has a CA issuer address, in my case, Verisign.
7) This warning may appear just click OK and ignore it
- When attempting to save the webpage you will get a pop up that states Location is not available. This verifies that escalation is working good. Simply hit OK and proceed on
8) on the explorer window address path, enter the cmd.exe full path:
C:\WINDOWS\system32\cmd.exe, use the enter key

Note: You will now go and save the webpage. This will vary on how it’s done depending on the browser.
- (Alternatively way to open CMD): Within the System32 directory navigate down until you find the cmd executable. Right click on it and hit Open. A command prompt should open and to verify, type whoami and hit enter. whoami should display the current user as nt authority\system.
9) now you’ll have an escalated privileges command prompt.

Remedy
Use Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
Securing UAC Windows Certificate Dialog:
- Keep UAC Enabled: UAC should be enabled to ensure that administrative actions are confirmed by the user. Disabling UAC removes this layer of security.
- Use Strong User Accounts: Ensure that the accounts with administrative privileges have strong passwords to prevent unauthorized access.
- Regular Updates: Keep your Windows operating system and security software up to date to address any known vulnerabilities.
- Beware of Malicious Prompts: Be cautious when prompted by UAC dialogs, especially if you didn’t initiate any action. Malware can attempt to trick users into granting elevated privileges.
- Use Standard User Accounts: Whenever possible, use a standard user account for regular activities. Use an administrative account only when necessary.
- Verify the Source: Before providing administrative credentials, verify the source of the UAC prompt and the legitimacy of the action.
- Application Whitelisting: Consider using application whitelisting solutions to restrict the execution of only trusted applications.
Sources
https://exchange.xforce.ibmcloud.com/vulnerabilities/170556
https://msrc.microsoft.com/update-guide/en-us/vulnerability/CVE-2019-1388
https://www.zerodayinitiative.com/advisories/ZDI-19-975/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-1388
https://github.com/nobodyatall648/CVE-2019-1388
https://sotharo-meas.medium.com/cve-2019-1388-windows-privilege-escalation-through-uac-22693fa23f5f